Security mitigation for the Common Log Filesystem (CLFS) - Microsoft Community Hub
https://techcommunity.microsoft.com/t5/security-compliance-and-identity/security-mitigation-for-the-common-log-filesystem-clfs/ba-p/4224041
YubiKeys are vulnerable to cloning attacks thanks to newly discovered side channel | Ars Technica
https://arstechnica.com/security/2024/09/yubikeys-are-vulnerable-to-cloning-attacks-thanks-to-newly-discovered-side-channel/
Hackers inject malicious JS in Cisco store to steal credit cards, credentials
https://www.bleepingcomputer.com/news/security/hackers-inject-malicious-js-in-cisco-store-to-steal-credit-cards-credentials/
Revisiting the UDRL Part 3: Beacon User Data | Cobalt Strike
https://www.cobaltstrike.com/blog/revisiting-the-udrl-part-3-beacon-user-data
Rundll32 and Phantom DLL lolbins | Hexacorn
https://www.hexacorn.com/blog/2024/09/03/rundll32-and-phantom-dll-lolbins/
[HackerNotes Ep.86] The X-Correlation between Frans & RCE - Research Drop
https://blog.criticalthinkingpodcast.io/p/hackernotes-ep86-xcorrelation-frans-rce-research-drop![[HackerNotes Ep.86] The X-Correlation between Frans & RCE - Research Drop](/image/screenshot/de6e05c24e1c4168f2a2d04409eeaf3b.png)
epf.atc23.pdf
https://cs.brown.edu/~vpk/papers/epf.atc23.pdf
Breaking down CVE-2024–38063: remote exploitation of the Windows kernel | by BI.ZONE | Sep, 2024 | Medium
https://bi-zone.medium.com/breaking-down-cve-2024-38063-remote-exploitation-of-the-windows-kernel-bdae36f5f61d
Microsoft Tackling Windows Logfile Flaws With New HMAC-Based Security Mitigation - SecurityWeek
https://www.securityweek.com/microsoft-tackling-windows-logfile-flaws-with-new-hmac-based-security-mitigation/
North Korean Hackers Targets Job Seekers with Fake FreeConference App
https://thehackernews.com/2024/09/north-korean-hackers-targets-job.html
Android Users Urged to Install Latest Security Updates to Fix Actively Exploited Flaw
https://thehackernews.com/2024/09/google-confirms-cve-2024-32896.html
EDRmetry - Effective Linux EDR/SIEM Evaluation Testing Playbook
https://edu.defensive-security.com/edrmetry-effective-linux-edr-xdr-evaluation-testing-playbook
Where do Detections come from? | Wirespeed
https://wirespeed.co/posts/where-do-detections-come-from
MalwareBazaar | French Group
https://bazaar.abuse.ch/browse/tag/French%20Group/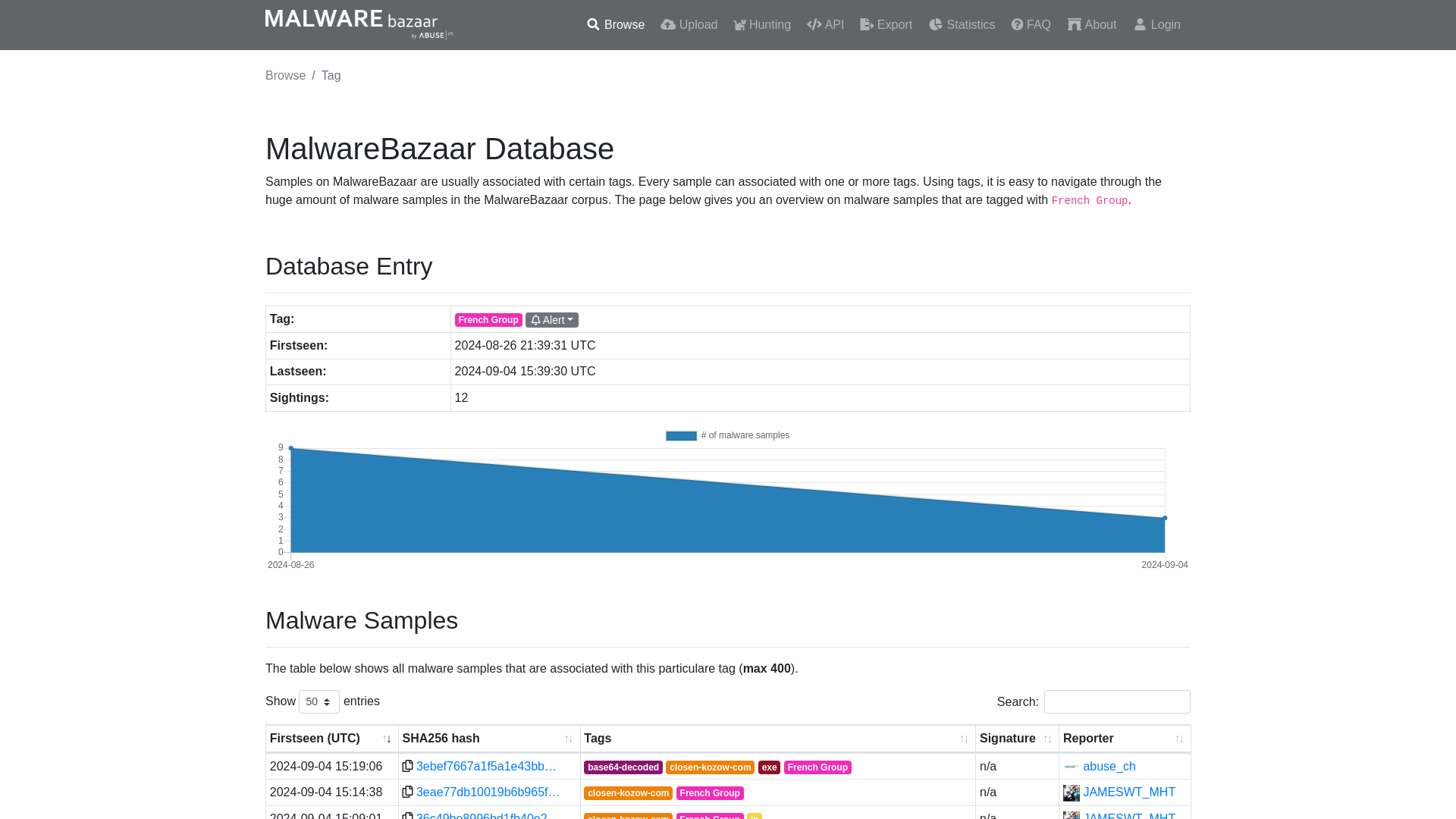
GitHub - stripe-samples/accept-a-payment: Learn how to accept a payment from customers around the world with a variety of payment methods.
https://github.com/stripe-samples/accept-a-payment
Revival Hijack supply-chain attack threatens 22,000 PyPI packages
https://www.bleepingcomputer.com/news/security/revival-hijack-supply-chain-attack-threatens-22-000-pypi-packages/
US cracks down on Russian disinformation before 2024 election
https://www.bleepingcomputer.com/news/security/us-cracks-down-on-russian-disinformation-before-2024-election/
Direct Syscalls: A journey from high to low - RedOps - English
https://redops.at/en/blog/direct-syscalls-a-journey-from-high-to-low
Evolution of Mallox: from private ransomware to RaaS | Securelist
https://securelist.com/mallox-ransomware/113529/
Protecting RDP passwords from Mimikatz with Remote Credential Guard - Devolutions Blog
https://blog.devolutions.net/2021/05/protecting-rdp-passwords-from-mimikatz-using-remote-credential-guard/
Crypto Vulnerability Allows Cloning of YubiKey Security Keys - SecurityWeek
https://www.securityweek.com/crypto-vulnerability-allows-cloning-of-yubikey-security-keys/
Researchers Find Over 22,000 Removed PyPI Packages at Risk of Revival Hijack
https://thehackernews.com/2024/09/hackers-hijack-22000-removed-pypi.html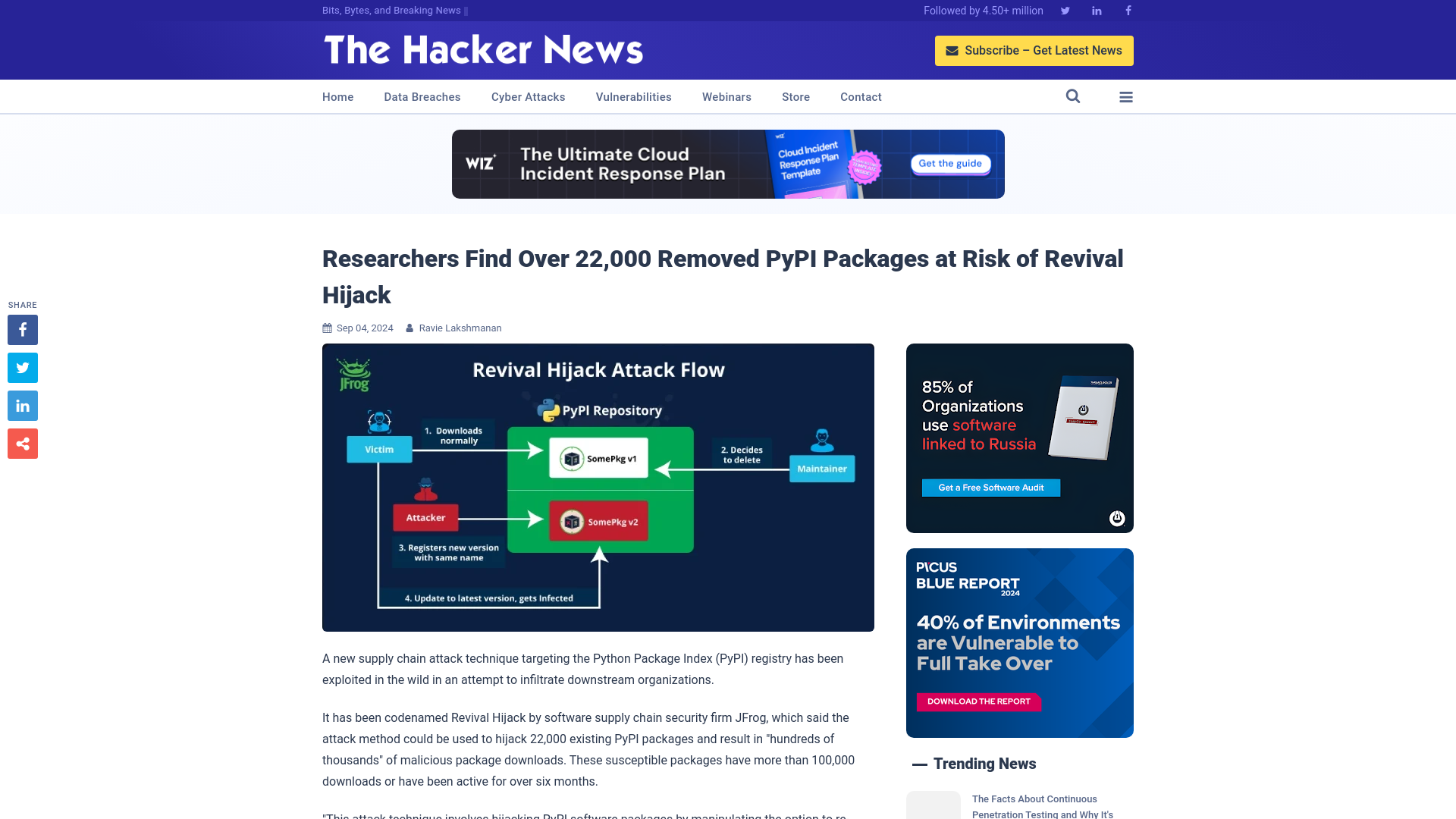
White House Addresses BGP Vulnerabilities in New Internet Routing Security Roadmap - SecurityWeek
https://www.securityweek.com/white-house-outlines-plan-for-addressing-bgp-vulnerabilities/
CVE-2020-27786 ( Race Condition + Use-After-Free ) · ii4gsp
https://ii4gsp.github.io/cve-2020-27786/
EUCLEAK - NinjaLab
https://ninjalab.io/eucleak/
Hackers Use Fake GlobalProtect VPN Software in New WikiLoader Malware Attack
https://thehackernews.com/2024/09/hackers-use-fake-globalprotect-vpn.html
Active Directory Hardening Series - Part 5 – Enforcing LDAP Channel Binding - Microsoft Community Hub
https://techcommunity.microsoft.com/t5/core-infrastructure-and-security/active-directory-hardening-series-part-5-enforcing-ldap-channel/ba-p/4235497
D-Link Warns of Code Execution Flaws in Discontinued Router Model - SecurityWeek
https://www.securityweek.com/d-link-warns-of-code-execution-flaws-in-discontinued-router-model/
Head Mare hacktivist group targets Russia and Belarus
https://securityaffairs.com/168030/hacktivism/head-mare-hacktivist-group-winrar.html
Analysis https://payper99.store/?pub_id= Malicious activity - Interactive analysis ANY.RUN
https://app.any.run/tasks/51df83cb-1150-40f2-b4d3-53f04f1592bd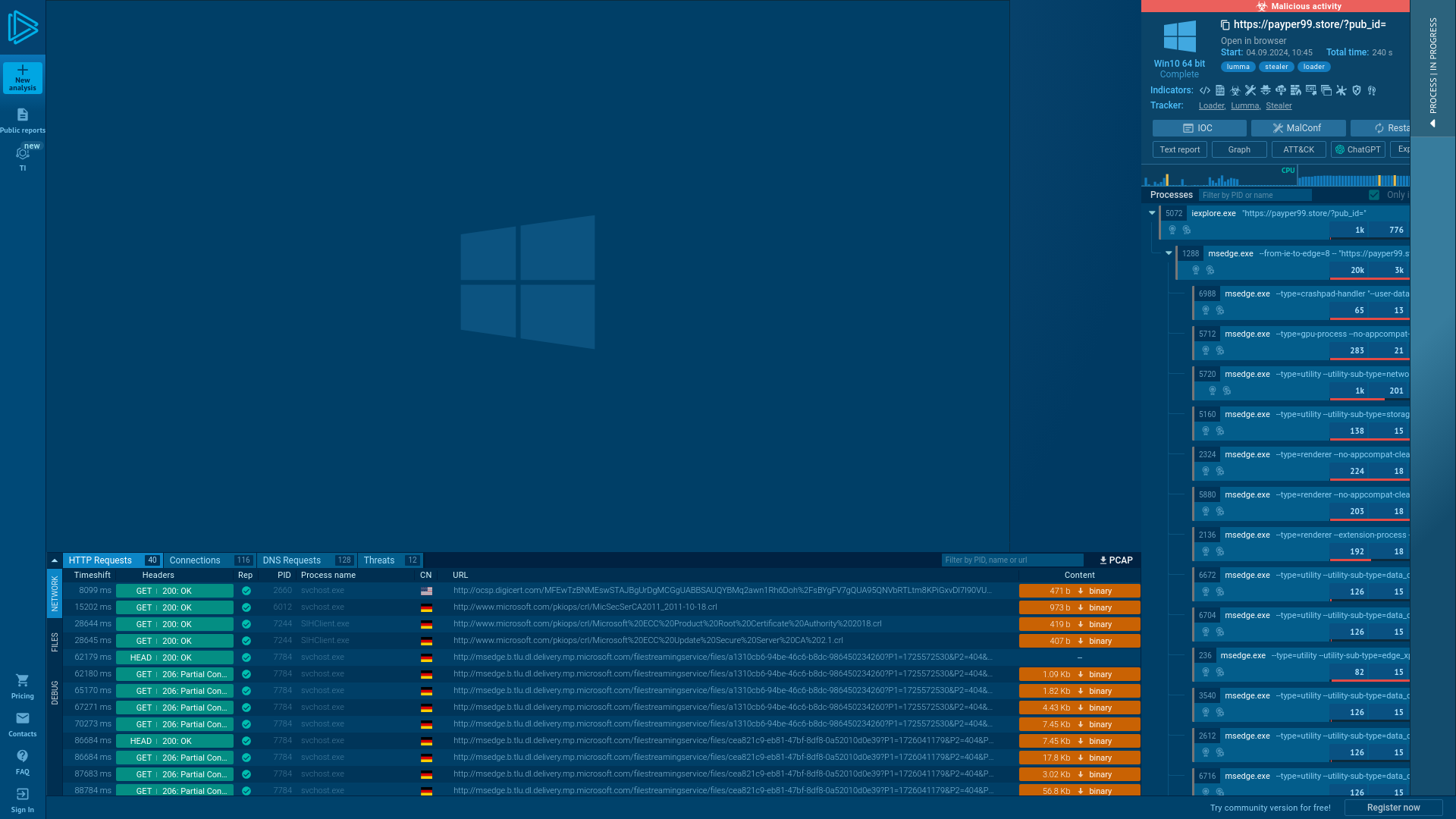
Revival Hijack - PyPI hijack technique exploited in the wild, puts 22K packages at risk | JFrog
https://jfrog.com/blog/revival-hijack-pypi-hijack-technique-exploited-22k-packages-at-risk/