Why exploits prefer memory corruption | PACIBSP security
https://pacibsp.github.io/2024/why-exploits-prefer-memory-corruption.html
Microsoft Warns of Six Windows Zero-Days Being Actively Exploited - SecurityWeek
https://www.securityweek.com/microsoft-warns-of-six-windows-zero-days-being-actively-exploited/
GitHub - onhexgroup/Conferences: Conference presentation slides
https://github.com/onhexgroup/Conferences
Malware Development : Part 3. “Mastering Malware: A Journey Through… | by RED TEAM | Medium
https://sid4hack.medium.com/malware-development-part-3-669bebef79c4
Australian gold producer Evolution Mining hit by ransomware
https://www.bleepingcomputer.com/news/security/australian-gold-producer-evolution-mining-hit-by-ransomware/
X faces GDPR complaints for unauthorized use of data for AI training
https://www.bleepingcomputer.com/news/artificial-intelligence/x-faces-gdpr-complaints-for-unauthorized-use-of-data-for-ai-training/
Malware Development : Part-2. “Infected Innovation: The Malware… | by RED TEAM | Medium
https://sid4hack.medium.com/malware-development-part-2-459109c50126
Malware Development : Part 1. Where do I start, and what are all the… | by RED TEAM | Medium
https://sid4hack.medium.com/malware-development-part-1-ea9e26088662
Resurrecting Internet Explorer: Threat Actors Using Zero-day Tricks in Internet Shortcut File to Lure Victims (CVE-2024-38112) - Check Point Research
https://research.checkpoint.com/2024/resurrecting-internet-explorer-threat-actors-using-zero-day-tricks-in-internet-shortcut-file-to-lure-victims-cve-2024-38112/
3AM ransomware stole data of 464,000 Kootenai Health patients
https://www.bleepingcomputer.com/news/security/3am-ransomware-stole-data-of-464-000-kootenai-health-patients/
SAP Patches Critical Vulnerabilities in BusinessObjects, Build Apps - SecurityWeek
https://www.securityweek.com/sap-patches-critical-vulnerabilities-in-businessobjects-build-apps/
Ransomware Hits Australian Gold Mining Firm Evolution Mining - SecurityWeek
https://www.securityweek.com/ransomware-hits-australian-gold-mining-firm-evolution-mining/
Six ransomware gangs behind over 50% of 2024 attacks • The Register
http://dlvr.it/TBt67V
Post-Quantum Cryptography Standards Officially Announced by NIST – a History and Explanation - SecurityWeek
https://www.securityweek.com/post-quantum-cryptography-standards-officially-announced-by-nist-a-history-and-explanation/
Windows 11 KB5041585 cumulative update released with fixes, new features
https://www.bleepingcomputer.com/news/microsoft/windows-11-kb5041585-cumulative-update-released-with-fixes-new-features/
Mispadu Droppers + Downloaders (8/6/2024 - 8/13/2024) · GitHub
https://gist.github.com/kirk-sayre-work/a4a8c83481bbf0197375e3fd21914fc1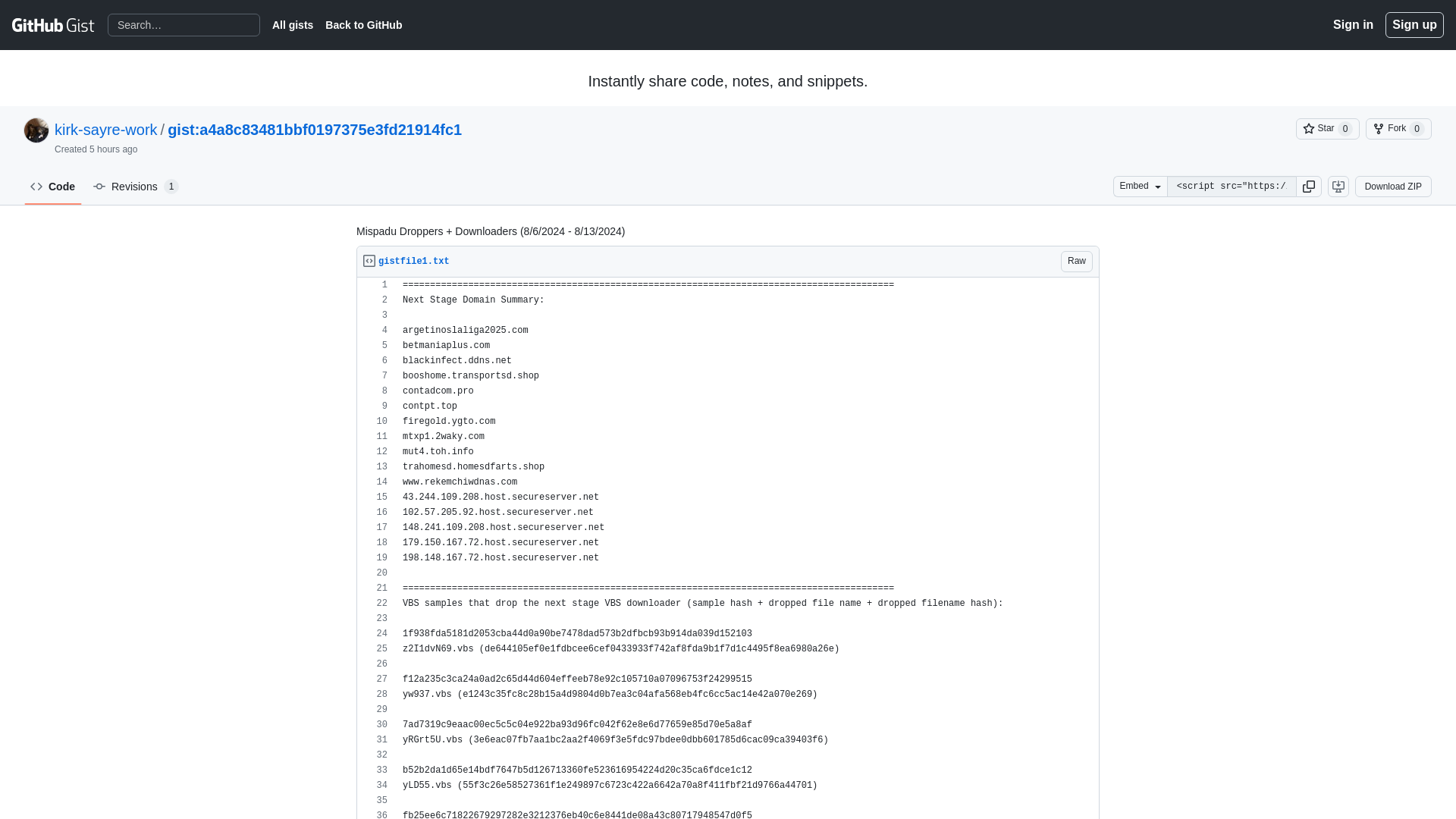
Critical SAP flaw allows remote attackers to bypass authentication
https://www.bleepingcomputer.com/news/security/critical-sap-flaw-allows-remote-attackers-to-bypass-authentication/
Radar/Dispossessor Ransomware Operation Disrupted by Authorities - SecurityWeek
https://www.securityweek.com/radar-dispossessor-ransomware-operation-disrupted-by-authorities/
Adobe Calls Attention to Massive Batch of Code Execution Flaws - SecurityWeek
https://www.securityweek.com/adobe-calls-attention-to-massive-batch-of-code-execution-flaws/
Justice Department Disrupts North Korean 'Laptop Farm' Operation - SecurityWeek
https://www.securityweek.com/justice-department-disrupts-north-korean-laptop-farm-operation/
Building a nation-scale evidence base for cyber deception - NCSC.GOV.UK
https://www.ncsc.gov.uk/blog-post/building-a-nation-scale-evidence-base-for-cyber-deception
Windows 10 KB5041580 update released with 14 fixes, security updates
https://www.bleepingcomputer.com/news/microsoft/windows-10-kb5041580-update-released-with-14-fixes-security-updates/
The DEF CON® Media Server - Archives of the conferences
https://media.defcon.org/DEF%20CON%2032
GitHub - hackerschoice/thc-tips-tricks-hacks-cheat-sheet: Various tips & tricks
https://github.com/hackerschoice/thc-tips-tricks-hacks-cheat-sheet#payload
South Korea says DPRK hackers stole spy plane technical data
https://www.bleepingcomputer.com/news/security/south-korea-says-dprk-hackers-stole-spy-plane-technical-data/
Reverse Engineering Dark Souls 3 Networking (#1 - Connection) - Tim Leonard's Website
https://timleonard.uk/2022/05/29/reverse-engineering-dark-souls-3-networking
AMD Says New Sinkclose CPU Vulnerability Only Affects 'Seriously Breached Systems' - SecurityWeek
https://www.securityweek.com/amd-says-new-sinkclose-cpu-vulnerability-only-affects-seriously-breached-systems/
US DoJ dismantled remote IT worker fraud schemes run by North Korea
https://securityaffairs.com/166951/intelligence/north-korea-t-worker-fraud-schemes.html
Data theft forum admins busted after flashing their cash in a life of luxury | Malwarebytes
https://www.malwarebytes.com/blog/news/2024/08/data-theft-forum-admins-busted-after-flashing-their-cash-in-a-life-of-luxury
Reverse Engineering Dark Souls 3 Networking (#2 - Packets) - Tim Leonard's Website
https://timleonard.uk/2022/06/02/reverse-engineering-dark-souls-3-networking-part-2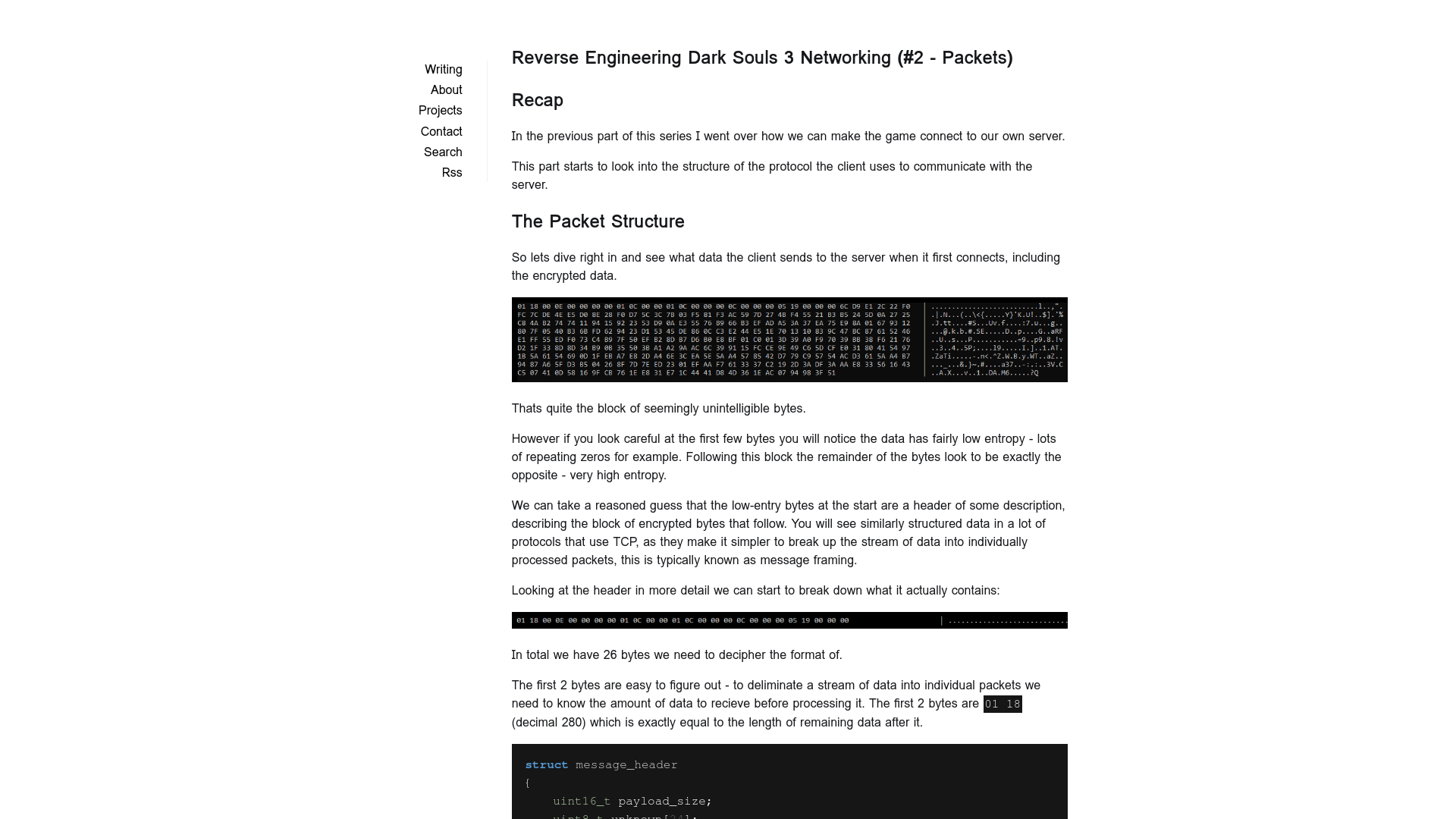
Microsoft fixes issue that sent PCs into BitLocker recovery
https://www.bleepingcomputer.com/news/microsoft/microsoft-fixes-issue-that-sent-pcs-into-bitlocker-recovery/
Microsoft August 2024 Patch Tuesday fixes 9 zero-days, 6 exploited
https://www.bleepingcomputer.com/news/microsoft/microsoft-august-2024-patch-tuesday-fixes-9-zero-days-6-exploited/
Ransom Cartel, Reveton ransomware owner arrested, charged in US
https://www.bleepingcomputer.com/news/security/ransom-cartel-reveton-ransomware-owner-arrested-charged-in-us/
us-20-Chen-You-Have-No-Idea-Who-Sent-That-Email-18-Attacks-On-Email-Sender-Authentication.pdf
https://i.blackhat.com/USA-20/Thursday/us-20-Chen-You-Have-No-Idea-Who-Sent-That-Email-18-Attacks-On-Email-Sender-Authentication.pdf
Ivanti warns of critical vTM auth bypass with public exploit
https://www.bleepingcomputer.com/news/security/ivanti-warns-of-critical-vtm-auth-bypass-with-public-exploit/