Banks in Singapore to phase out one-time passwords in 3 months
https://www.bleepingcomputer.com/news/security/banks-in-singapore-to-phase-out-one-time-passwords-in-3-months/
Pwntools 101 - Pwndbg & Buffer Overflows · Arch Cloud Labs
https://archcloudlabs.com/projects/pwntools-bof/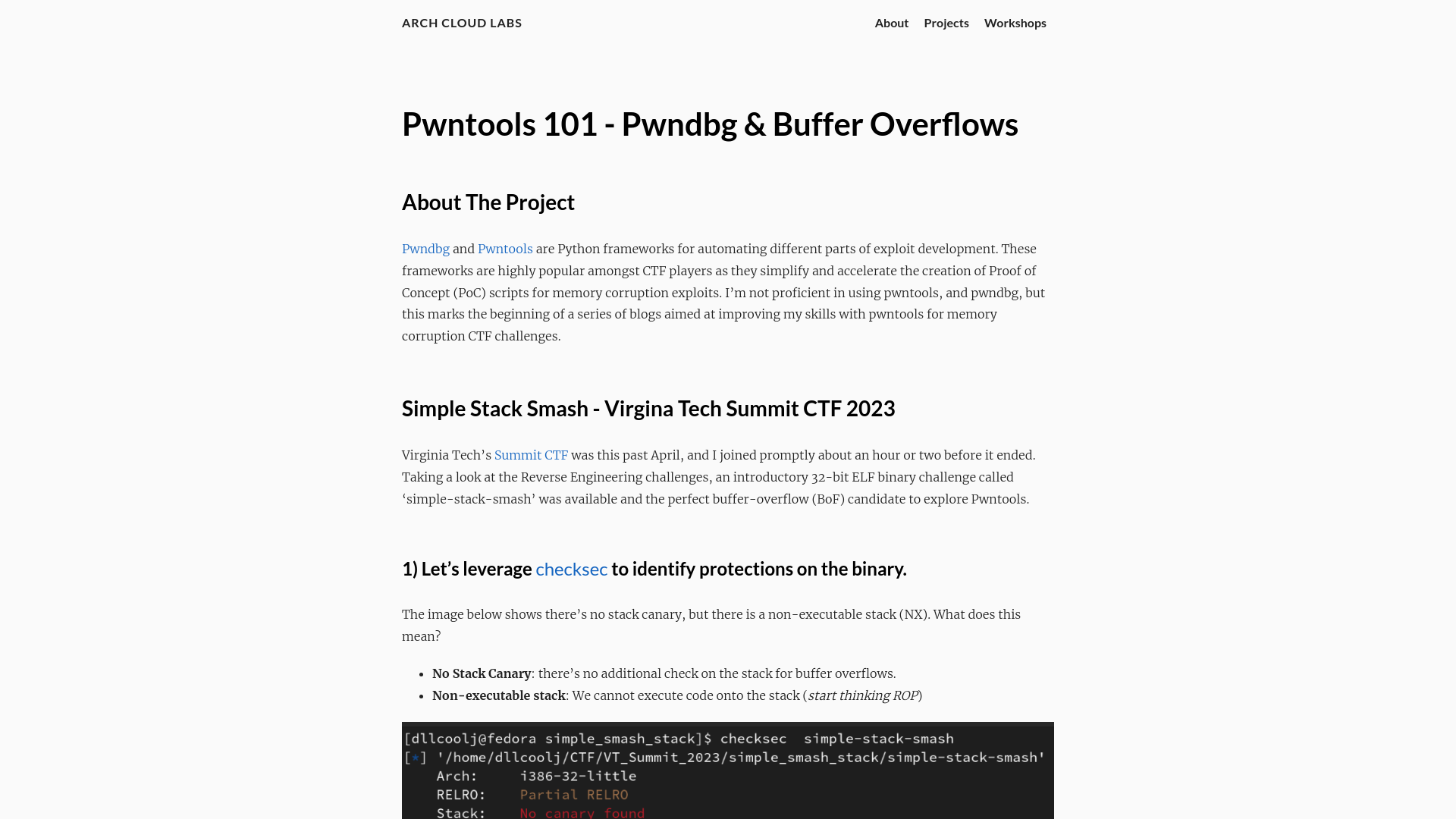
Z80%20CPU%20Instant%20Reference%20Card%20(Color).pdf
https://ballyalley.com/ml/z80_docs/Z80%20CPU%20Instant%20Reference%20Card%20(Color).pdf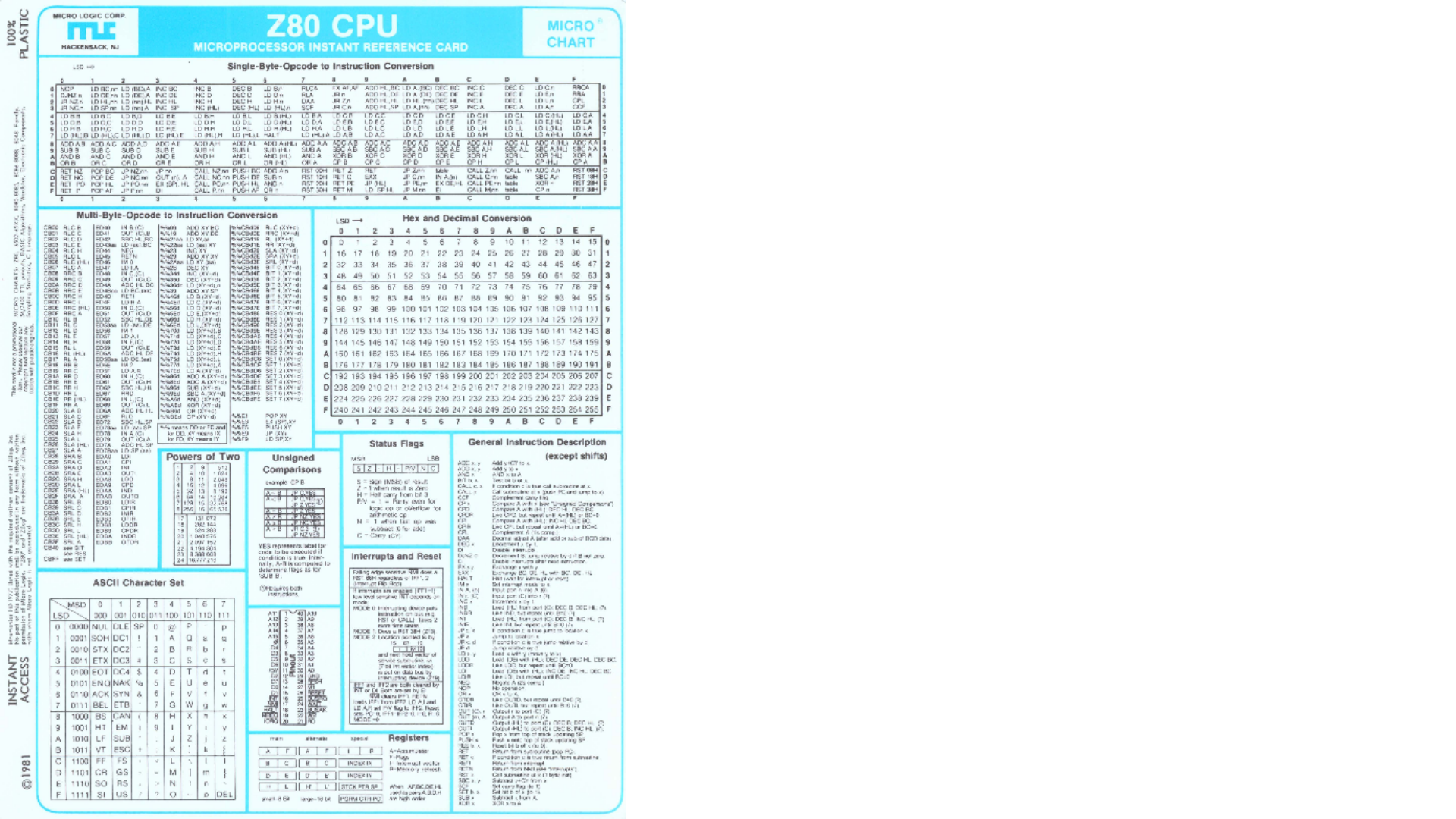
https://bsideslv.org/schedule
https://bsideslv.org/schedule
Fun with Exception Handlers | Ya boy Manny
https://mannyfreddy.gitbook.io/ya-boy-manny/
High Fidelity detections are Low Fidelity detections, until proven otherwise | Hexacorn
https://www.hexacorn.com/blog/2024/07/14/high-fidelity-detections-are-low-fidelity-detections-until-proven-otherwise/
GitHub - rzte/pdf-exploit: pdf exploit 集成
https://github.com/rzte/pdf-exploit
The Art of Malware C2 Scanning - How to Reverse and Emulate Protocol Obfuscated by Compiler - Speaker Deck
https://speakerdeck.com/takahiro_haruyama/the-art-of-malware-c2-scanning-how-to-reverse-and-emulate-protocol-obfuscated-by-compiler
GitHub - Proxmark/proxmark3: Proxmark 3
https://github.com/Proxmark/proxmark3
Reverse Engineering master0Fnone Class | Episode 1.2: x86 Assembly Demystified - YouTube
https://www.youtube.com/watch?v=d-zxyLQlaYw
Flatlined: Analyzing Pulse Secure Firmware and Bypassing Integrity Checking - Eclypsium | Supply Chain Security for the Modern Enterprise
https://eclypsium.com/blog/flatlined-analyzing-pulse-secure-firmware-and-bypassing-integrity-checking/
Reverse Engineering master0Fnone Class | Episode 1.1: x86 Assembly Demystified - YouTube
https://www.youtube.com/watch?v=ZXoW5iqbFJE
Hardware Hacking with a Raspberry Pi - Configuring the PiFex
https://voidstarsec.com/blog/pifex-config
DIY Malware Analysis Lab for Free (with CrackMe Challenge!) | master0Fnone Ep. 2.1: Sandbox in a Box - YouTube
https://www.youtube.com/watch?v=ELPWeRXxnSE
GitHub - otsmr/blackbox-fuzzing: Fuzzing IoT Devices Using the Router TL-WR902AC as Example
https://github.com/otsmr/blackbox-fuzzing
Flangvik - Twitch
https://www.twitch.tv/flangvik/
🔍 Looking for Remote Code Execution bugs in the Linux kernel | Andrey Konovalov
https://xairy.io/articles/syzkaller-external-network
Critical Exim bug bypasses security filters on 1.5 million mail servers
https://www.bleepingcomputer.com/news/security/critical-exim-bug-bypasses-security-filters-on-15-million-mail-servers/
GitHub Actions exploitation: untrusted input
https://www.synacktiv.com/publications/github-actions-exploitation-untrusted-input.html