JTAG Hacking with a Raspberry Pi - Introducing the PiFex
https://voidstarsec.com/blog/jtag-pifex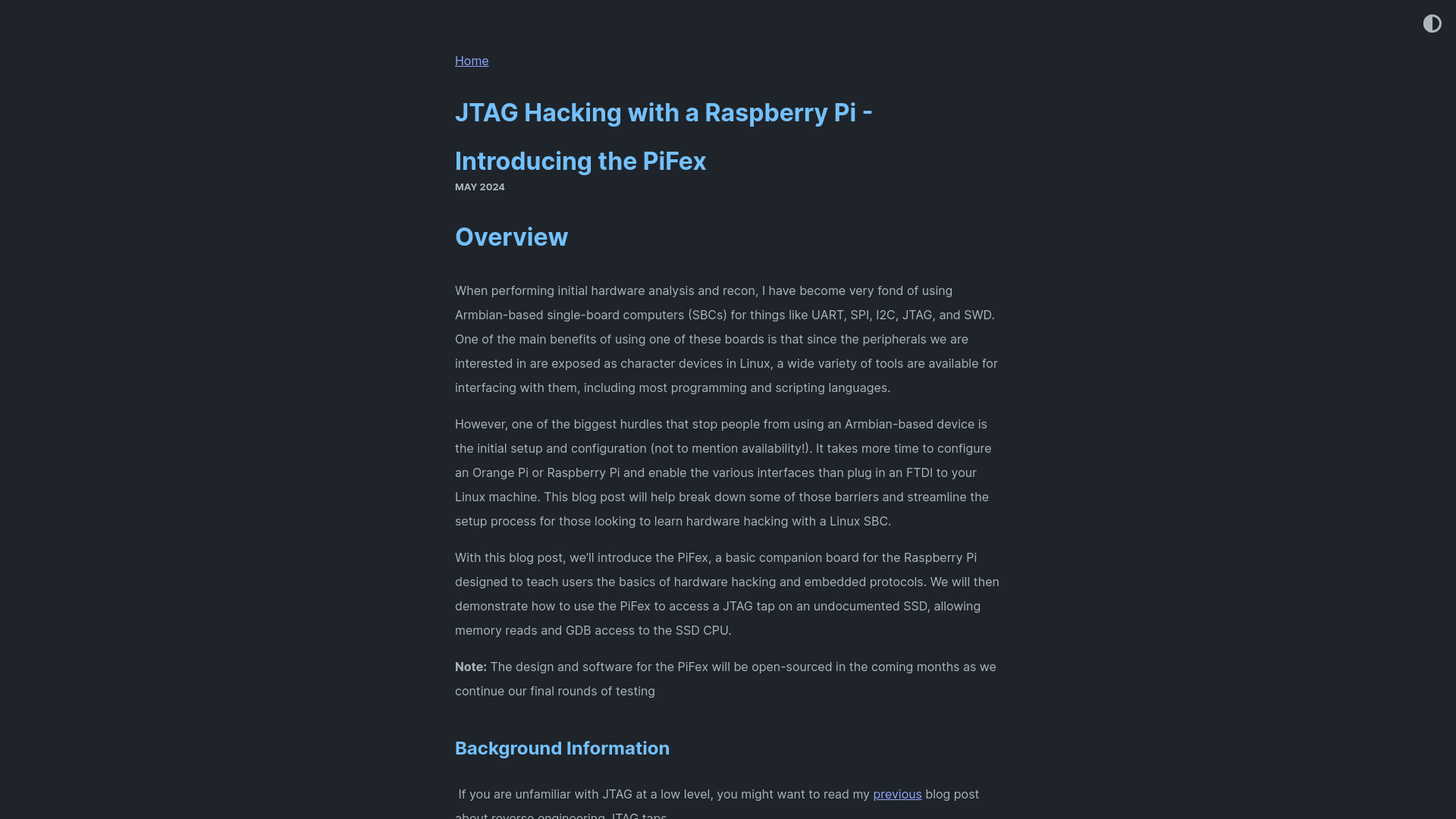
New 'Cuckoo' Persistent macOS Spyware Targeting Intel and Arm Macs
https://thehackernews.com/2024/05/new-cuckoo-persistent-macos-spyware.html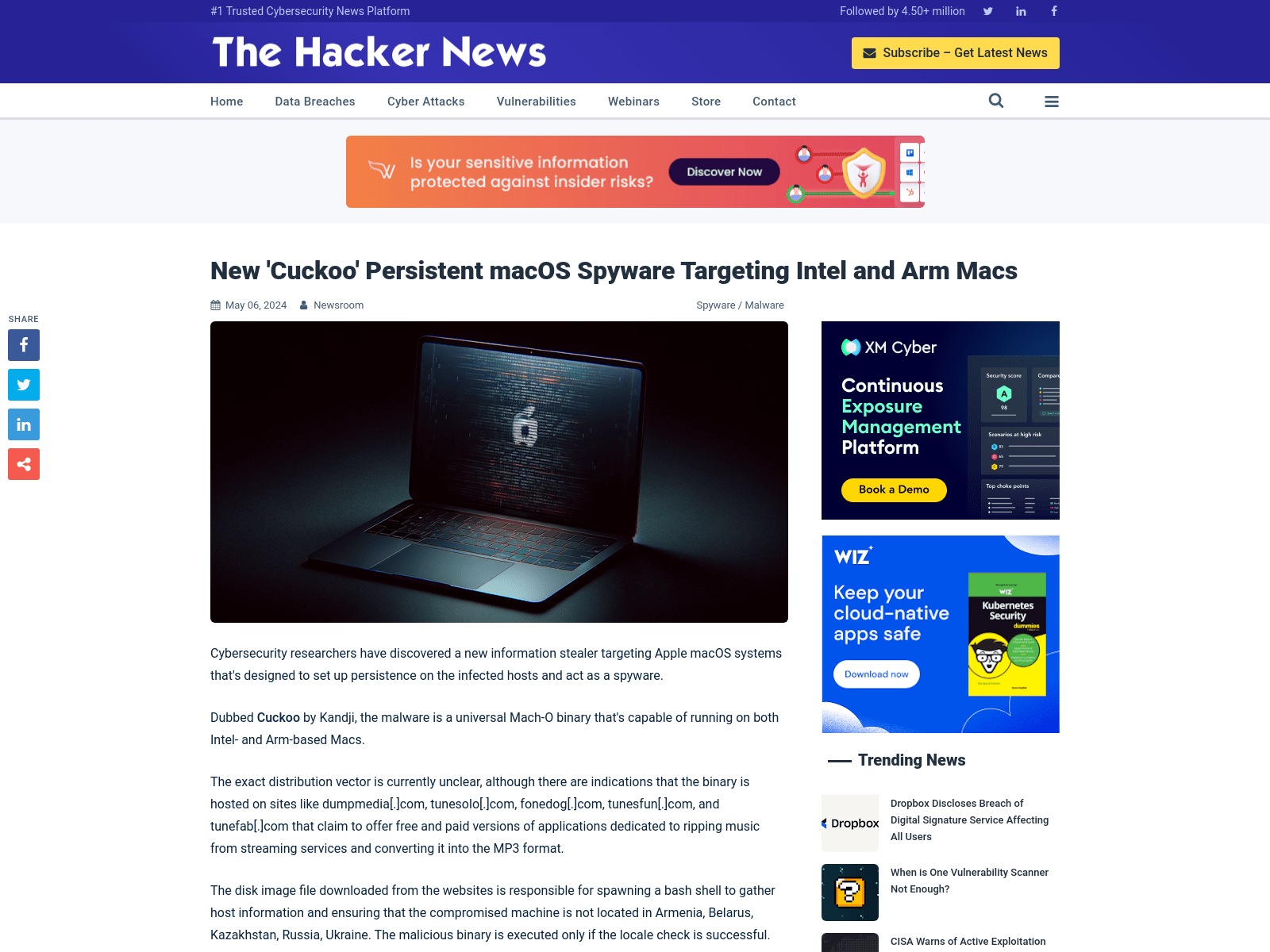
The toddler’s introduction to Heap exploitation (Part 1) | by +Ch0pin🕷️ | InfoSec Write-ups
https://infosecwriteups.com/the-toddlers-introduction-to-heap-exploitation-part-1-515b3621e0e8
APT_REPORT/Sandworm/Kapeka at master · blackorbird/APT_REPORT · GitHub
https://github.com/blackorbird/APT_REPORT/tree/master/Sandworm/Kapeka
GitHub - Squiblydoo/debloat: A GUI tool for removing bloat from executables
https://github.com/Squiblydoo/debloat
China-Linked Hackers Suspected in ArcaneDoor Cyberattacks Targeting Network Devices
https://thehackernews.com/2024/05/china-linked-hackers-suspected-in.html
Path Traversal Affecting Multiple CData Products - Research Advisory | Tenable®
https://www.tenable.com/security/research/tra-2024-09
Hunting M365 Invaders: Blue Team's Guide to Initial Access Vectors | Splunk
https://www.splunk.com/en_us/blog/security/hunting-m365-invaders-blue-team-s-guide-to-initial-access-vectors.html
Critical Tinyproxy Flaw Opens Over 50,000 Hosts to Remote Code Execution
https://thehackernews.com/2024/05/critical-tinyproxy-flaw-opens-over.html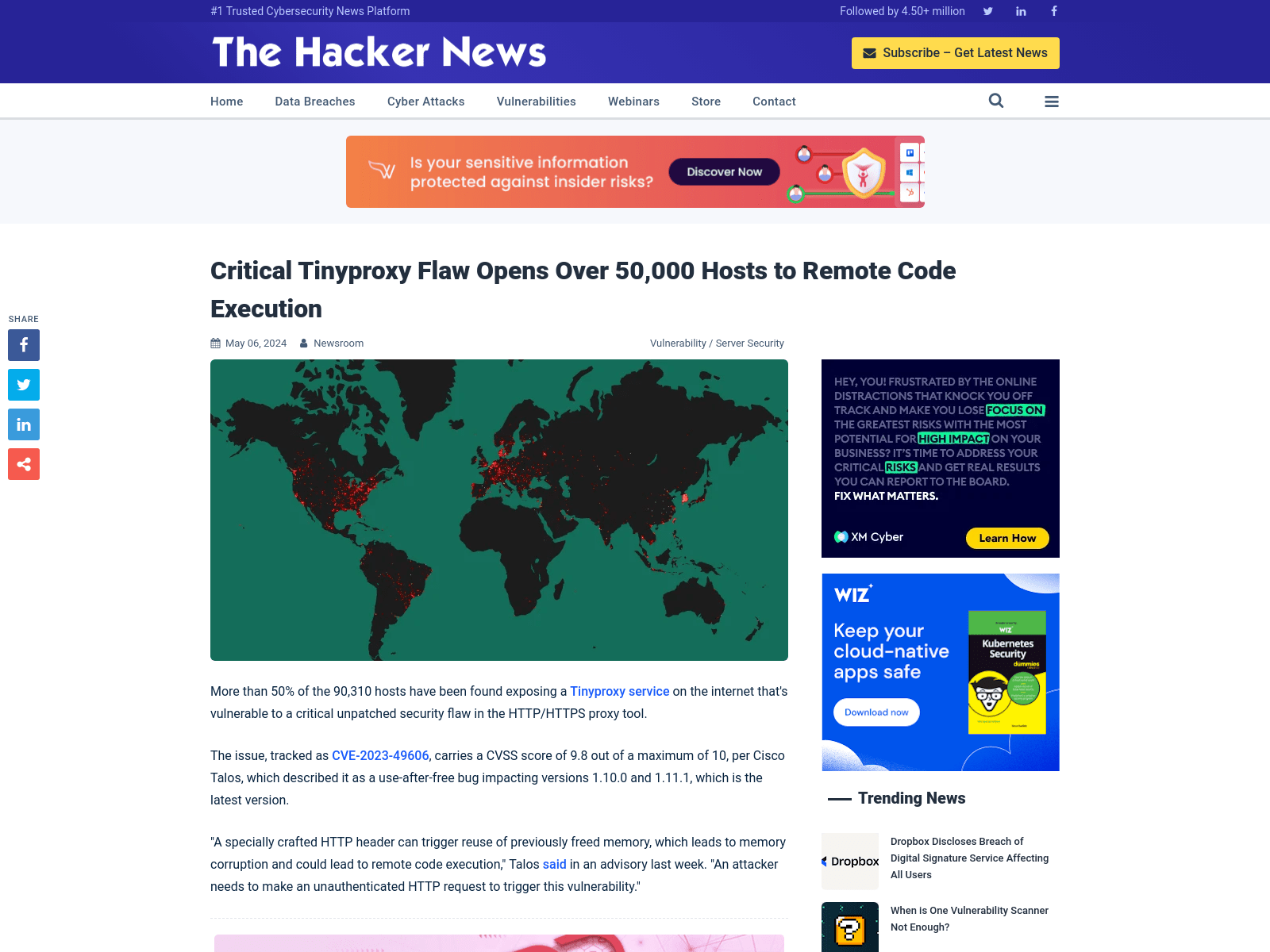
APT_REPORT/kimsuky/Exploit Weak DMARC.pdf at master · blackorbird/APT_REPORT · GitHub
https://github.com/blackorbird/APT_REPORT/blob/master/kimsuky/Exploit%20Weak%20DMARC.pdf
The toddler’s introduction to Heap exploitation (Part 2) | by +Ch0pin🕷️ | InfoSec Write-ups
https://infosecwriteups.com/the-toddlers-introduction-to-heap-exploitation-part-2-d1f325b74286
Lockbit's seized site comes alive to tease new police announcements
https://www.bleepingcomputer.com/news/security/lockbits-seized-site-comes-alive-to-tease-new-police-announcements/
The toddler’s introduction to Heap exploitation, Overflows (Part 3) | by +Ch0pin🕷️ | InfoSec Write-ups
https://infosecwriteups.com/the-toddlers-introduction-to-heap-exploitation-overflows-part-3-d3d1aa042d1e
Xiaomi Android Devices Hit by Multiple Flaws Across Apps and System Components
https://thehackernews.com/2024/05/xiaomi-android-devices-hit-by-multiple.html
Google Debuts New Security Products, Hyping AI and Mandiant Expertise - SecurityWeek
https://www.securityweek.com/google-debuts-new-security-products-hyping-ai-and-mandiant-expertise/
El Salvador suffered a massive leak of biometric data
https://securityaffairs.com/162790/data-breach/el-salvador-massive-leak-biometric-data.html
Exploring hunting options for catching Impacket - Threat hunting with hints of incident response
https://threathunt.blog/impacket-psexec/
Introducing Google Threat Intelligence: Actionable threat intelligence at Google scale | Google Cloud Blog
https://cloud.google.com/blog/products/identity-security/introducing-google-threat-intelligence-actionable-threat-intelligence-at-google-scale-at-rsa/
Why Your VPN May Not Be As Secure As It Claims – Krebs on Security
https://krebsonsecurity.com/2024/05/why-your-vpn-may-not-be-as-secure-as-it-claims/
Impacket – Part 2 - Threat hunting with hints of incident response
https://threathunt.blog/impacket-part-2/
LLM Pentest: Leveraging Agent Integration For RCE
https://www.blazeinfosec.com/post/llm-pentest-agent-hacking/
Zeus WPI | Unveiling secrets of the ESP32 part 2: reverse engineering RX
https://zeus.ugent.be/blog/23-24/esp32-reverse-engineering-continued/
Analysis of an Info Stealer — Chapter 2: The iOS App | by Fr4 | Medium
https://medium.com/@icebre4ker/analysis-of-an-info-stealer-chapter-2-the-ios-app-0529e7b45405
Linksys Router Flaws Exposed, Poc Published, Patch Unavailable!
https://securityonline.info/cve-2024-33788-cve-2024-33789-linksys-e5600-router/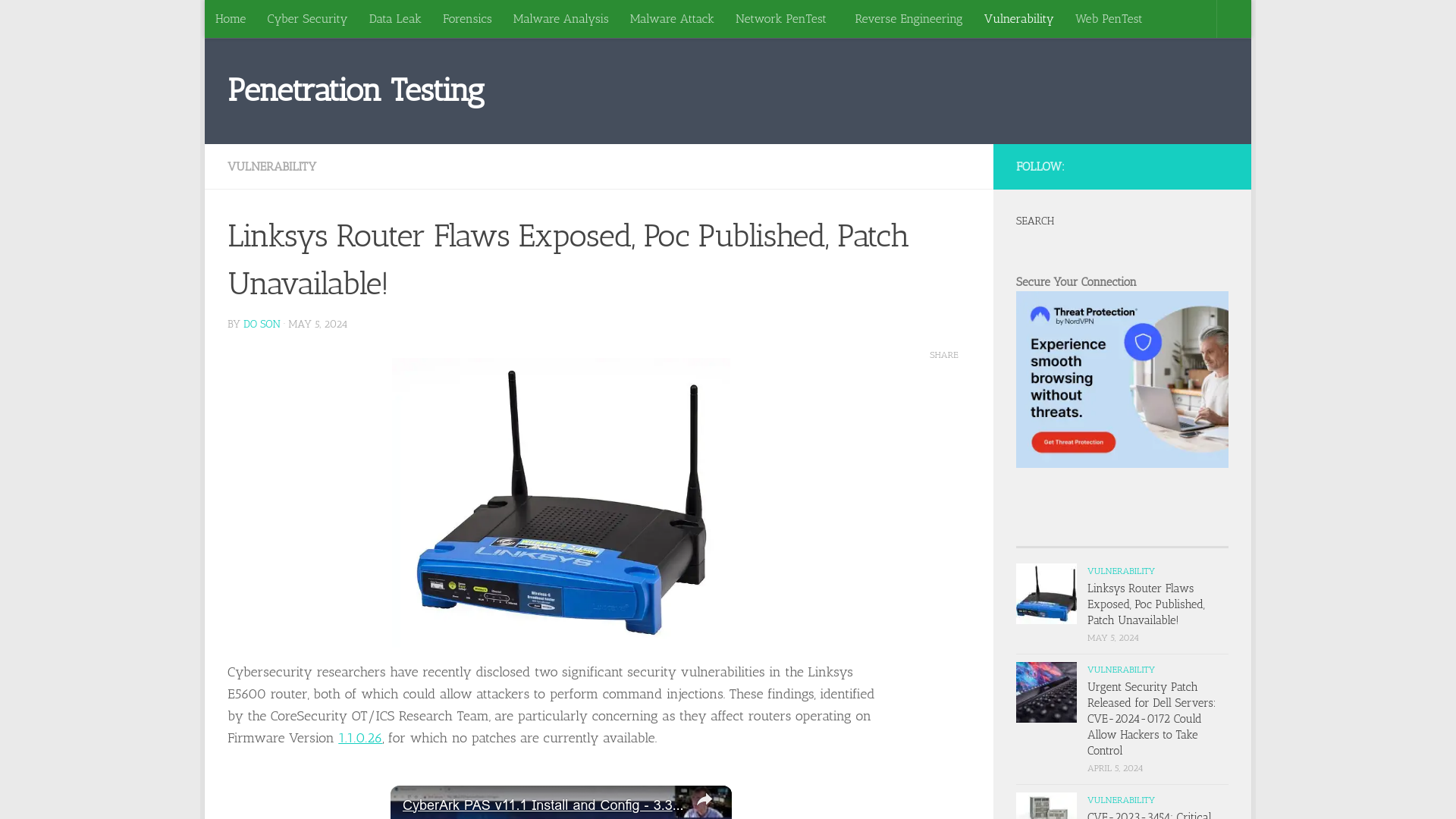
Uncharmed: Untangling Iran's APT42 Operations | Google Cloud Blog
https://cloud.google.com/blog/topics/threat-intelligence/untangling-iran-apt42-operations/
Apple’s iPhone Spyware Problem Is Getting Worse. Here’s What You Should Know | WIRED
https://www.wired.com/story/apple-iphone-spyware-101/
VirusTotal - Collections - ebb39ba4f340314ef4f69394f0793fc1e995ee22a3786b3d3c5fc67a05552fd7
https://www.virustotal.com/gui/collection/ebb39ba4f340314ef4f69394f0793fc1e995ee22a3786b3d3c5fc67a05552fd7/iocs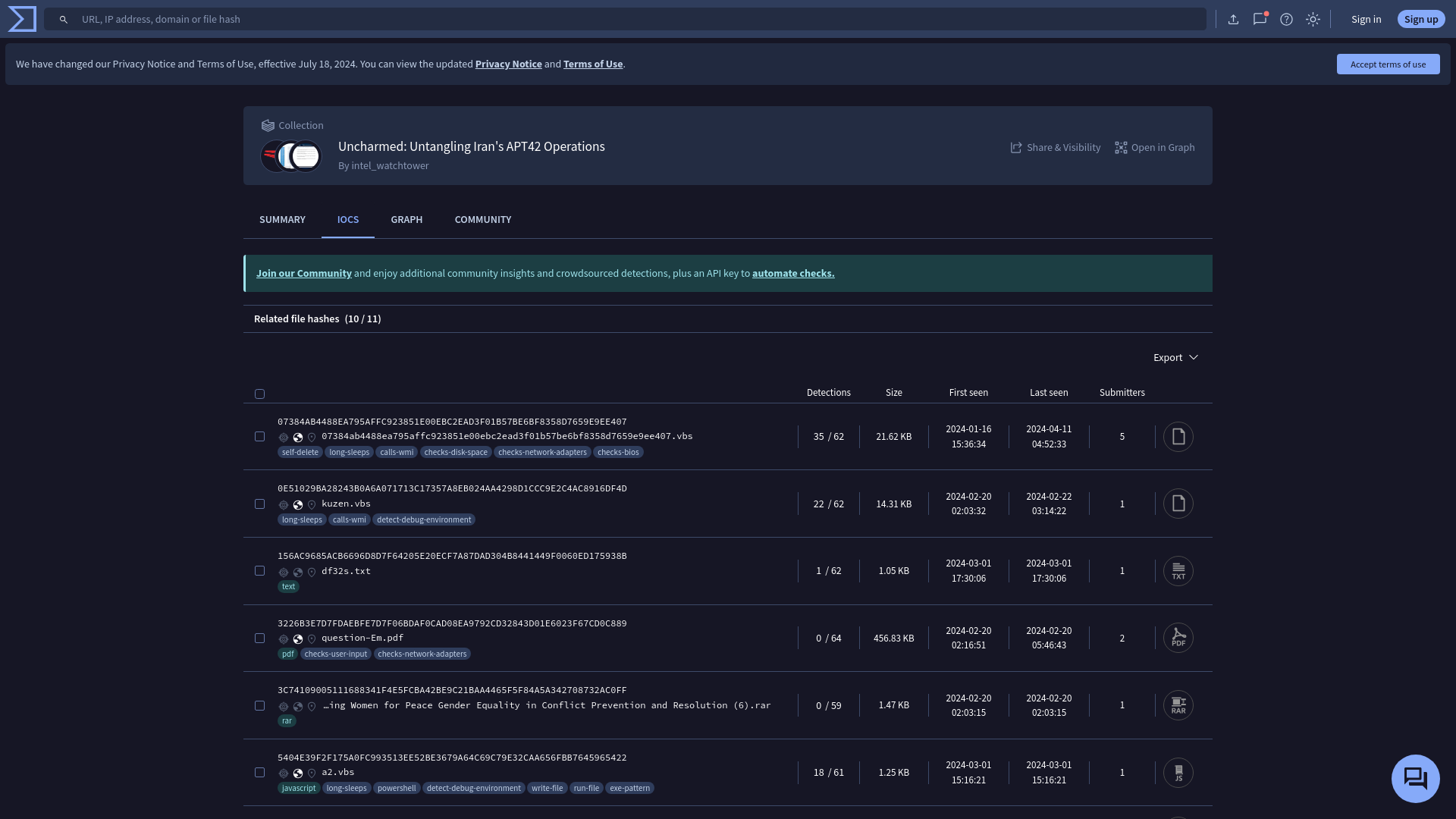
City of Wichita shuts down IT network after ransomware attack
https://www.bleepingcomputer.com/news/security/city-of-wichita-shuts-down-it-network-after-ransomware-attack/
Netscaler ADC and Gateway, Version 13.1-50.23 | Bishop Fox
https://bishopfox.com/blog/netscaler-adc-and-gateway-advisory
Lateral movement and on-prem NT hash dumping with Microsoft Entra Temporary Access Passes - dirkjanm.io
https://dirkjanm.io/lateral-movement-and-hash-dumping-with-temporary-access-passes-microsoft-entra/
China hacked Ministry of Defence, Sky News learns | Politics News | Sky News
https://news.sky.com/story/china-hacked-ministry-of-defence-sky-news-learns-13130757
5 Big Cisco, Splunk Security Announcements At RSAC 2024
http://cs.co/6012j5Brw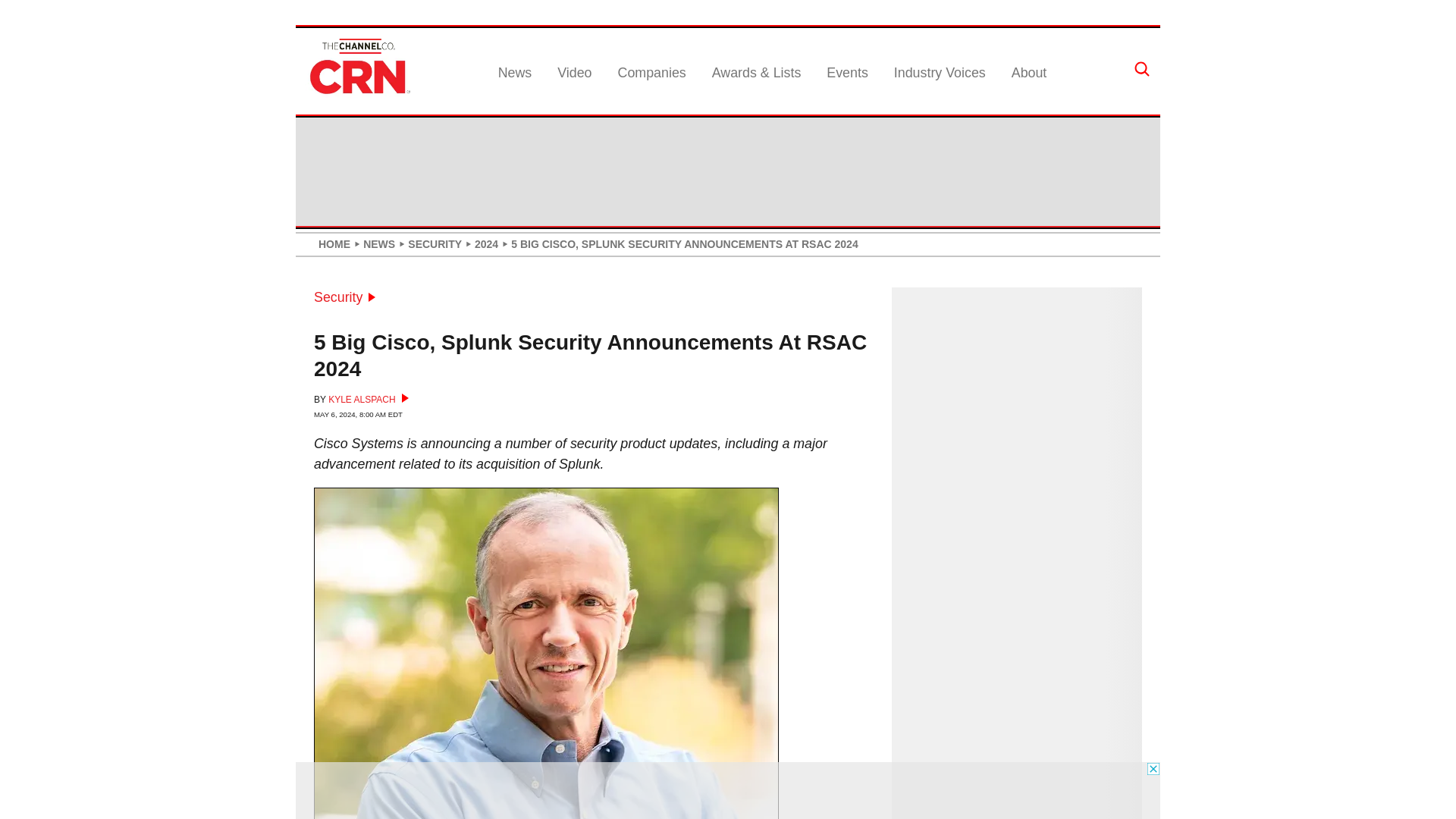
Finland authorities warn of Android malware campaign targeting bank users
https://securityaffairs.com/162768/malware/finland-android-malware-campaign-banks.html