Researchers Uncover Windows Flaws Granting Hackers Rootkit-Like Powers
https://thehackernews.com/2024/04/researchers-uncover-windows-flaws.html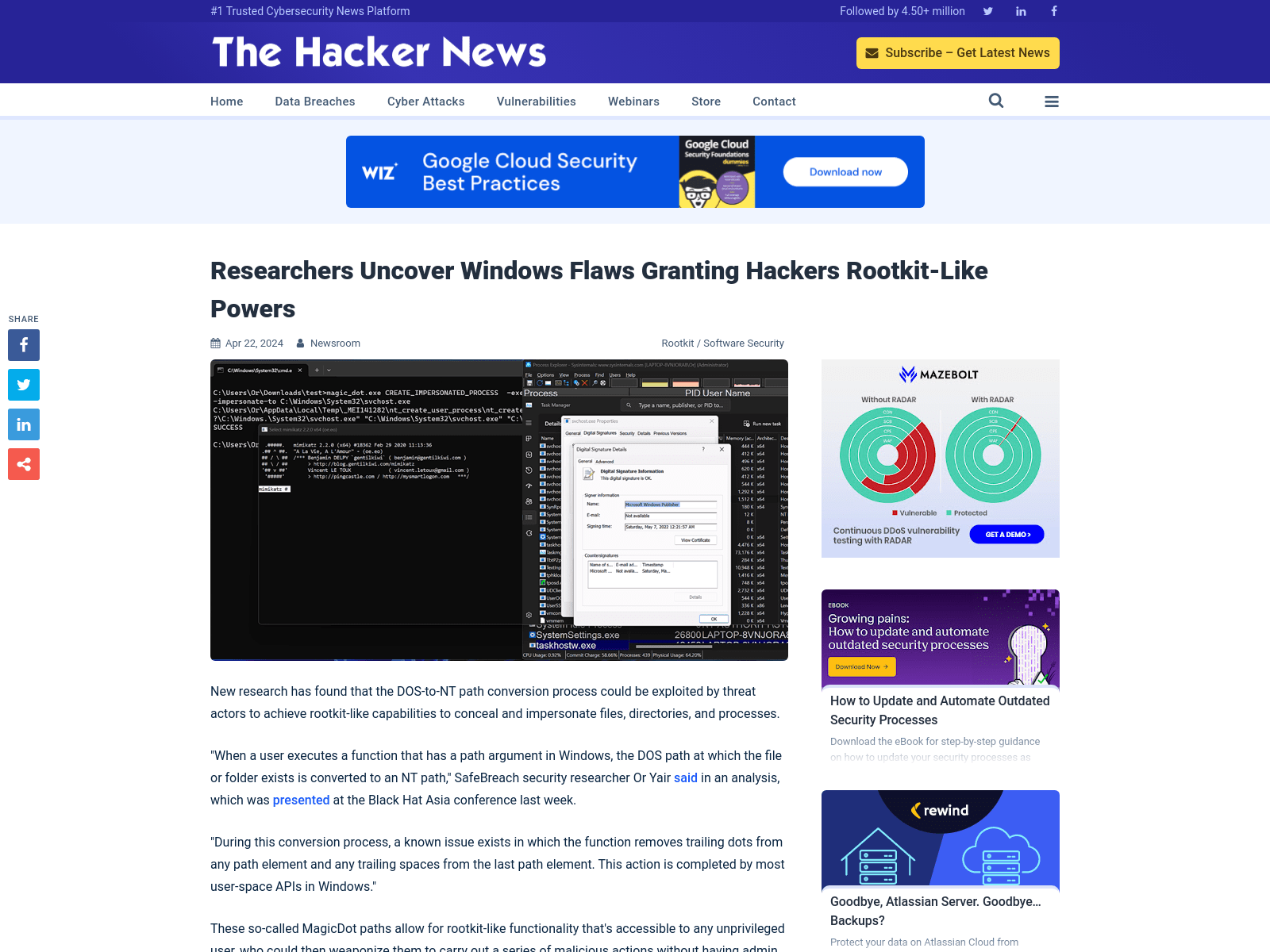
GitHub - mansk1es/CVE-2024-21111: Oracle VirtualBox Elevation of Privilege (Local Privilege Escalation) Vulnerability
https://github.com/mansk1es/CVE-2024-21111
Lord Of The Ring0 - Part 1 | Introduction - Ido Veltzman - Security Blog
https://idov31.github.io/2022/07/14/lord-of-the-ring0-p1.html
Microsoft: APT28 hackers exploit Windows flaw reported by NSA
https://www.bleepingcomputer.com/news/security/microsoft-apt28-hackers-exploit-windows-flaw-reported-by-nsa/
Malware dev lures child exploiters into honeytrap to extort them
https://www.bleepingcomputer.com/news/security/malware-dev-lures-child-exploiters-into-honeytrap-to-extort-them/
Microsoft Warns: North Korean Hackers Turn to AI-Fueled Cyber Espionage
https://thehackernews.com/2024/04/microsoft-warns-north-korean-hackers.html
GitLab affected by GitHub-style CDN flaw allowing malware hosting
https://www.bleepingcomputer.com/news/security/gitlab-affected-by-github-style-cdn-flaw-allowing-malware-hosting/
ToddyCat’s traffic tunneling and data extraction tools | Securelist
https://securelist.com/toddycat-traffic-tunneling-data-extraction-tools/112443/
How to optimize your bug bounty programs - Help Net Security
https://www.helpnetsecurity.com/2024/04/22/roy-davis-zoom-bug-bounty-programs/
Search Jobs | Microsoft Careers
https://jobs.careers.microsoft.com/global/en/job/1710333/
CVE-2024-20356: Jailbreaking a Cisco appliance to run DOOM - LRQA Nettitude Labs
https://labs.nettitude.com/blog/cve-2024-20356-jailbreaking-a-cisco-appliance-to-run-doom/
Russian Sandworm hackers targeted 20 critical orgs in Ukraine
https://www.bleepingcomputer.com/news/security/russian-sandworm-hackers-targeted-20-critical-orgs-in-ukraine/
Project Zero: The Windows Registry Adventure #1: Introduction and research results
https://googleprojectzero.blogspot.com/2024/04/the-windows-registry-adventure-1.html
Bypassing EDRs With EDR-Preloading
https://malwaretech.com/2024/02/bypassing-edrs-with-edr-preload.html
The SNES Cartridge, Briefly Explained | Mouse Bite Labs
https://mousebitelabs.com/2019/05/18/custom-pcb-explanation/
Abusing WSUS with MITM to perform ADCS ESC8 attack | Belette Timorée’s blog post
https://j4s0nmo0n.github.io/belettetimoree.github.io/2023-12-01-WSUS-to-ESC8.html
MuddyWater campaign abusing Atera Agents - HarfangLab EDR | Block cyber attacks
https://harfanglab.io/en/insidethelab/muddywater-rmm-campaign/
Analysis of VirtualBox CVE-2023-21987 and CVE-2023-21991
https://qriousec.github.io/post/vbox-pwn2own-2023/
Billions of scraped Discord messages up for sale | Malwarebytes
https://www.malwarebytes.com/blog/news/2024/04/billions-of-scraped-discord-messages-up-for-sale
Researchers: Windows Defender attack can delete databases • The Register
https://go.theregister.com/feed/www.theregister.com/2024/04/22/edr_attack_remote_data_deletion/
Hackers threaten to leak a copy of the World-Check database used to assess potential risks associated with entities
https://securityaffairs.com/162136/cyber-crime/hackers-threaten-leak-world-check.html
LSA Whisperer. Thank you to SpecterOps for supporting… | by Evan McBroom | Apr, 2024 | Posts By SpecterOps Team Members
https://posts.specterops.io/lsa-whisperer-20874277ea3b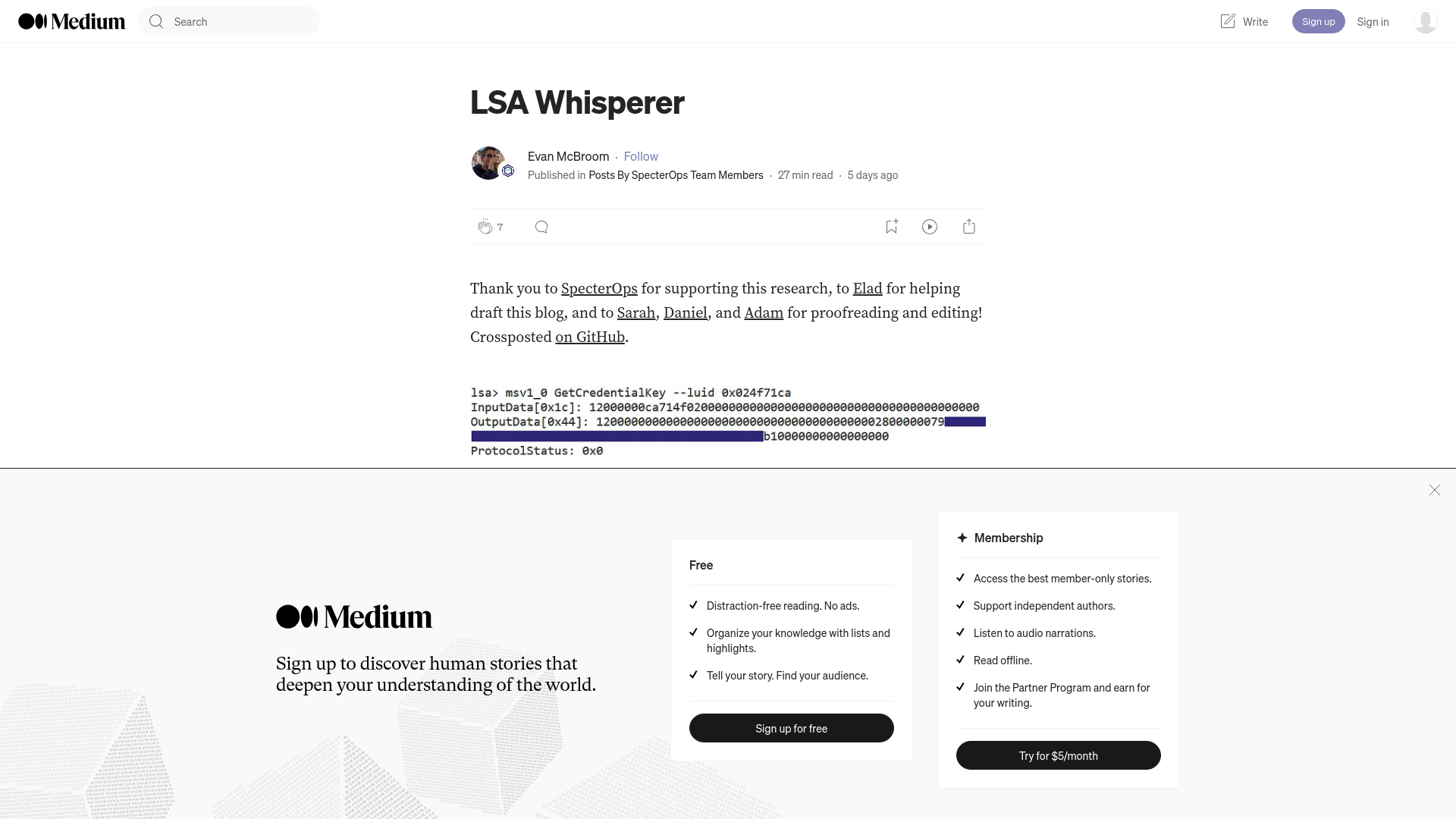
Research Shows How Attackers Can Abuse EDR Security Products - SecurityWeek
https://www.securityweek.com/research-shows-how-attackers-can-abuse-edr-security-products/
Creating Payloads with ScareCrow to Mimic Reputable Sources and Bypass Anti-Virus | by Cybertech Maven | Apr, 2024 | InfoSec Write-ups
https://infosecwriteups.com/creating-payloads-with-scarecrow-to-mimic-reputable-sources-and-bypass-anti-virus-01196cac741e
Cannes Hospital Cancels Medical Procedures Following Cyberattack - SecurityWeek
https://www.securityweek.com/cannes-hospital-cancels-medical-procedures-following-cyberattack/
New Code Threat Targets Discord Users, Steals Data with Clever Disguise
https://securityonline.info/new-code-threat-targets-discord-users-steals-data-with-clever-disguise/
Rural Texas Towns Report Cyberattacks That Caused One Water System to Overflow - SecurityWeek
https://www.securityweek.com/rural-texas-towns-report-cyberattacks-that-caused-one-water-system-to-overflow/
Oracle VirtualBox Elevation of Privilege Vulnerability (CVE-2024-21111): PoC Published
https://securityonline.info/oracle-virtualbox-elevation-of-privilege-vulnerability-cve-2024-21111-poc-published/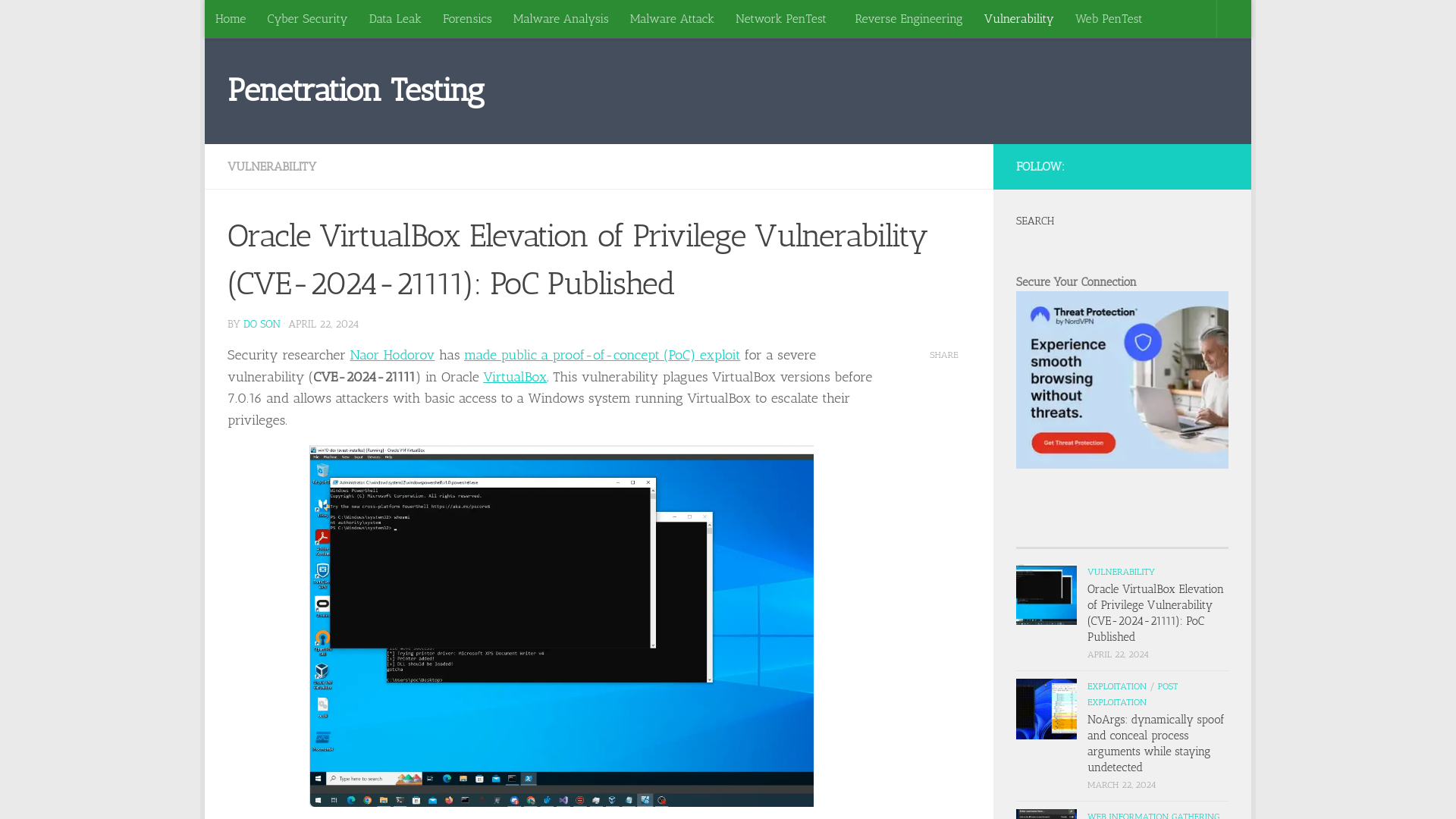
North Korean Internet | Monitoring the North Korea Public IP Space
https://nkinternet.wordpress.com/
Synlab Italia suspends operations following ransomware attack
https://www.bleepingcomputer.com/news/security/synlab-italia-suspends-operations-following-ransomware-attack/
CrushFTP Patches Exploited Zero-Day Vulnerability - SecurityWeek
https://www.securityweek.com/crushftp-patches-exploited-zero-day-vulnerability/
Analyzing Forest Blizzard’s custom post-compromise tool for exploiting CVE-2022-38028 to obtain credentials | Microsoft Security Blog
https://www.microsoft.com/en-us/security/blog/2024/04/22/analyzing-forest-blizzards-custom-post-compromise-tool-for-exploiting-cve-2022-38028-to-obtain-credentials/
Mitre says 'nation state' attackers touched its NERVE • The Register
https://go.theregister.com/feed/www.theregister.com/2024/04/22/in_brief_security/
Belarusian hackers claim to breach fertilizer plant in retaliation for support of Lukashenko regime
https://therecord.media/belarus-cyber-partisans-fertilizer-hack-lukashenko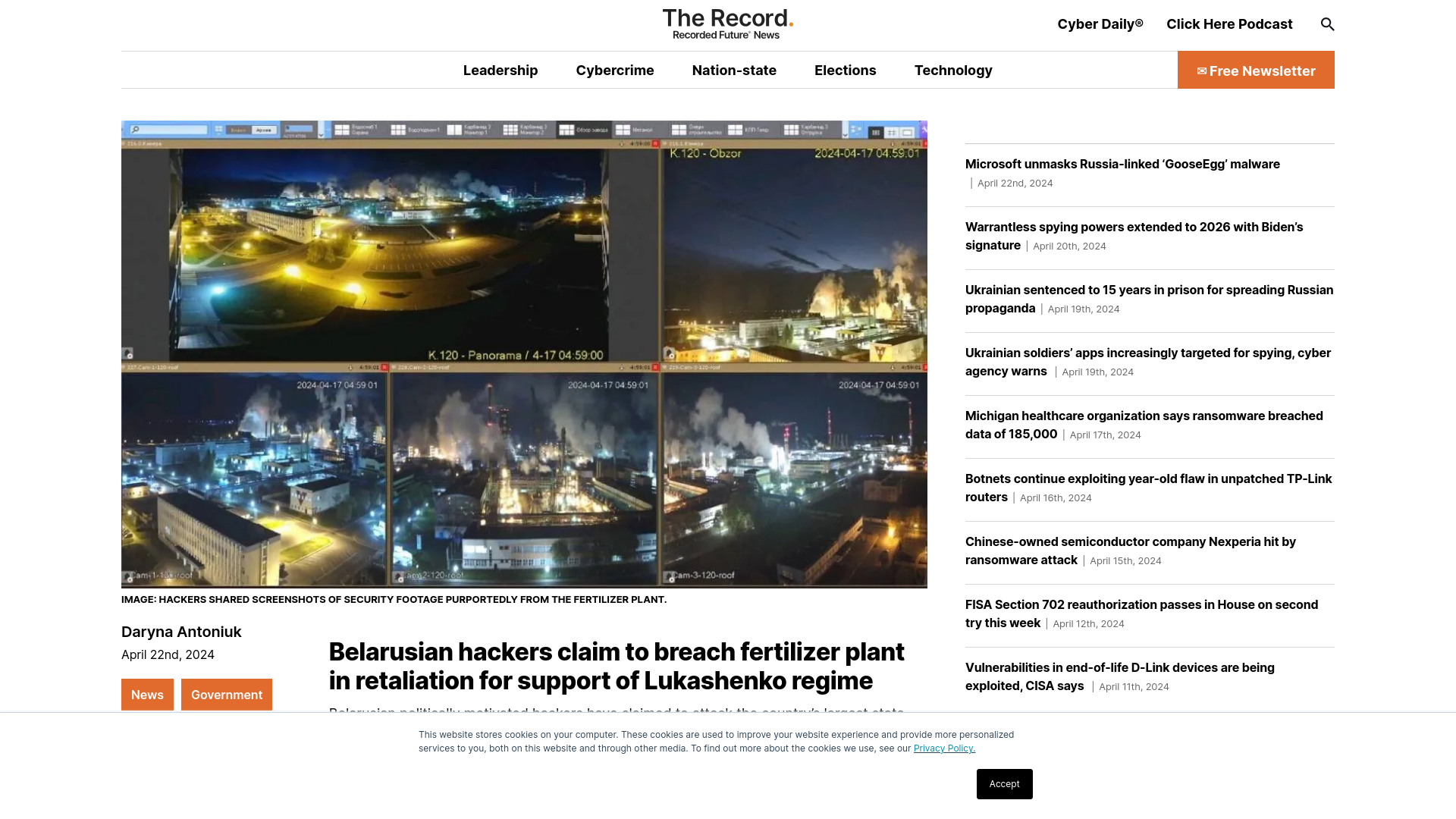
Inside the Super Nintendo cartridges
https://fabiensanglard.net/snes_carts/index.html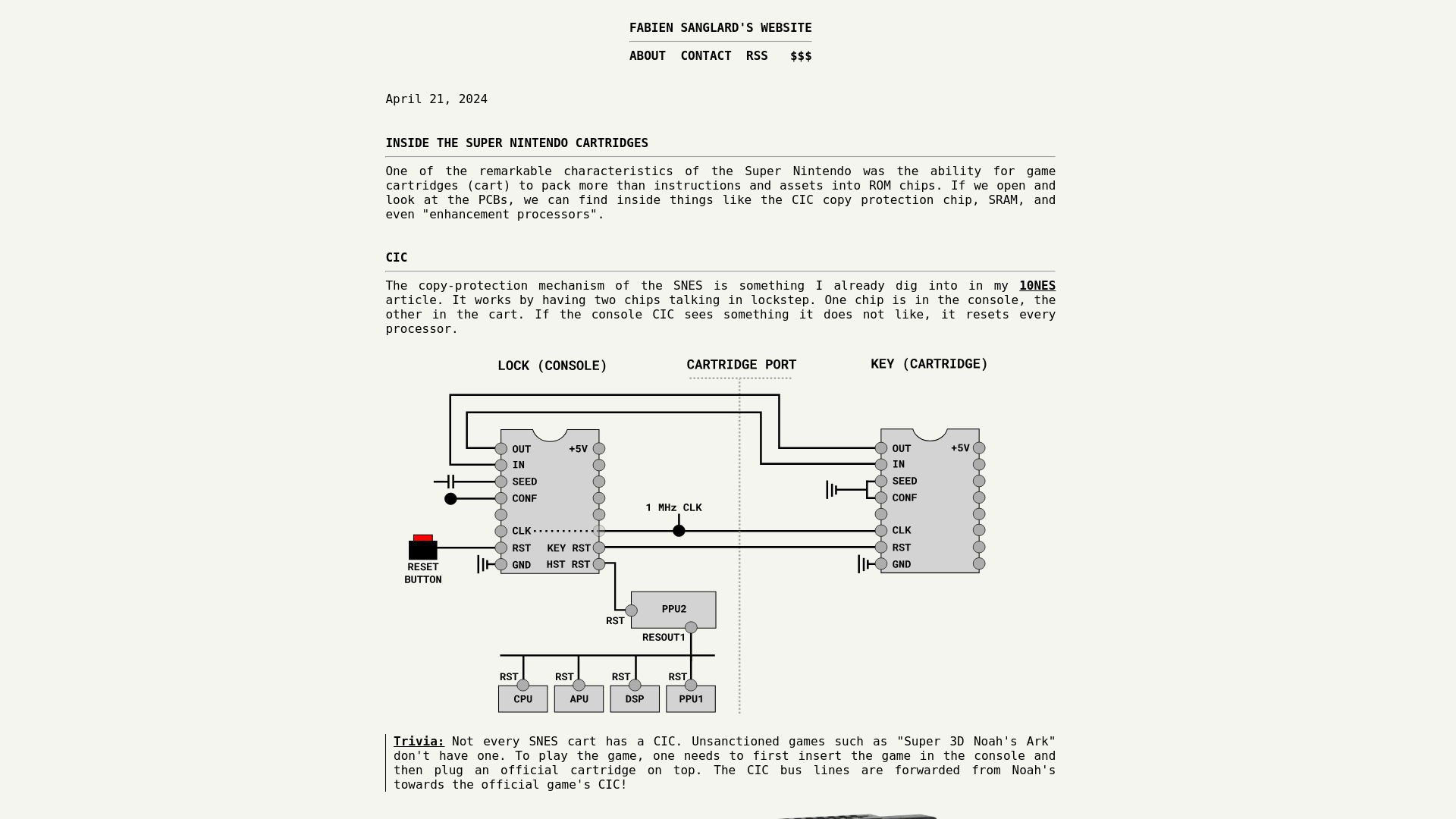
GitHub - badkeys/badkeys: Tool to find common vulnerabilities in cryptographic public keys
https://github.com/badkeys/badkeys
Thousands of Palo Alto Firewalls Potentially Impacted by Exploited Vulnerability - SecurityWeek
https://www.securityweek.com/thousands-of-palo-alto-firewalls-potentially-impacted-by-exploited-vulnerability/