Project Zero: The Windows Registry Adventure #1: Introduction and research results
https://googleprojectzero.blogspot.com/2024/04/the-windows-registry-adventure-1.html
Hackers Exploit OpenMetadata Flaws to Mine Crypto on Kubernetes
https://thehackernews.com/2024/04/hackers-exploit-openmetadata-flaws-to.html
LabHost phishing service with 40,000 domains disrupted, 37 arrested
https://www.bleepingcomputer.com/news/security/labhost-phishing-service-with-40-000-domains-disrupted-37-arrested/
XAgent Spyware Targeting iOS Devices in Western Europe: Analysis of Capabilities
https://www.linkedin.com/pulse/xagent-spyware-targeting-ios-devices-western-europe-dmitry-bestuzhev-xunle
Agenda — SLEUTHCON
https://www.sleuthcon.com/agenda2024
Global Police Operation Disrupts 'LabHost' Phishing Service, Over 30 Arrested Worldwide
https://thehackernews.com/2024/04/global-police-operation-disrupts.html
New Android Trojan 'SoumniBot' Evades Detection with Clever Tricks
https://thehackernews.com/2024/04/new-android-trojan-soumnibot-evades.html
Exploiting the libwebp Vulnerability, Part 1: Playing with Huffman Code | DARKNAVY
https://www.darknavy.org/blog/exploiting_the_libwebp_vulnerability_part_1/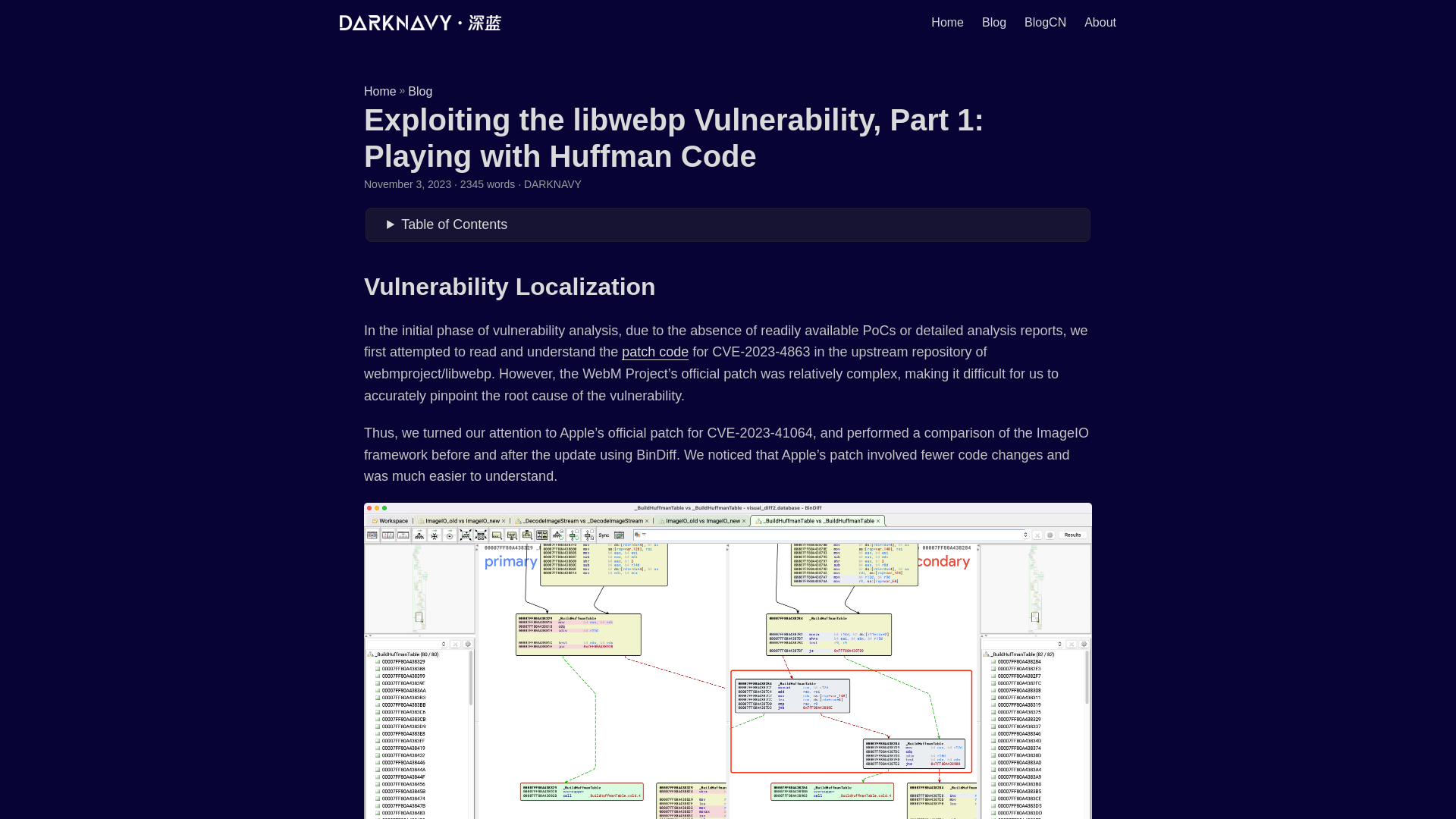
Hello: I’m your ADCS server and I want to authenticate against you – Decoder's Blog
https://decoder.cloud/2024/02/26/hello-im-your-adcs-server-and-i-want-to-authenticate-against-you/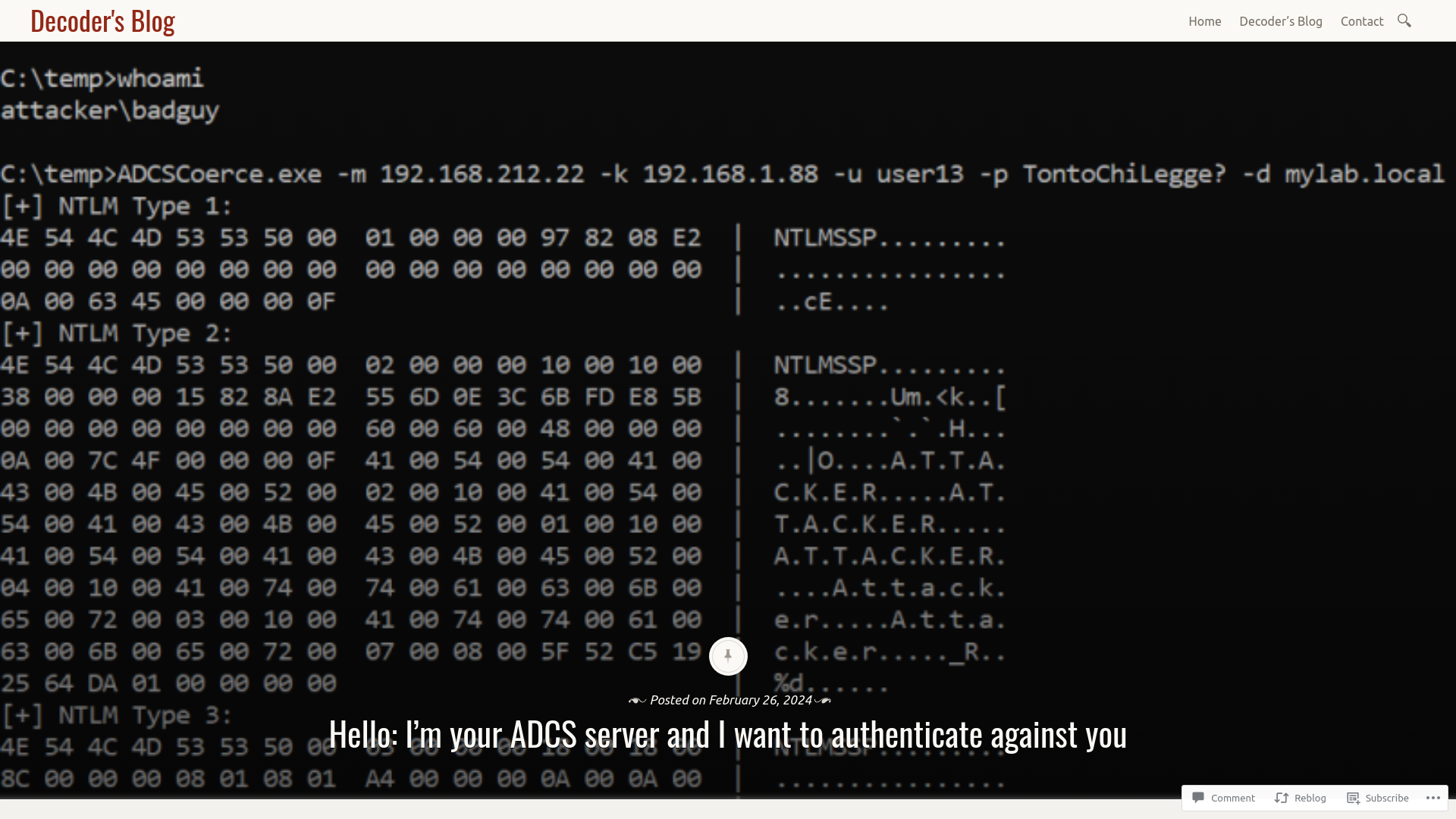
Cisco warns of a command injection escalation flaw in its IMC
https://securityaffairs.com/161975/hacking/cisco-integrated-management-controller-bug.html
Cybercriminals pose as LastPass staff to hack password vaults
https://www.bleepingcomputer.com/news/security/cybercriminals-pose-as-lastpass-staff-to-hack-password-vaults/
Malicious Google Ads Pushing Fake IP Scanner Software with Hidden Backdoor
https://thehackernews.com/2024/04/malicious-google-ads-pushing-fake-ip.html
Chaining N-days to Compromise All: Part 4 — VMware Workstation Information leakage | by Theori Vulnerability Research | Apr, 2024 | Theori BLOG
https://blog.theori.io/chaining-n-days-to-compromise-all-part-4-vmware-workstation-information-leakage-44476b05d410?source=social.tw
apt44-unearthing-sandworm.pdf
https://services.google.com/fh/files/misc/apt44-unearthing-sandworm.pdf
Breaking Custom Encryption Using Frida (Mobile Application Pentesting) | Cognisys Labs
https://labs.cognisys.group/posts/Breaking-Custom-Ecryption-Using-Frida-Mobile-Application-pentesting/
Redline Stealer Malware Evolves with Sneaky New Tricks, Spreads Globally
https://securityonline.info/redline-stealer-malware-evolves-with-sneaky-new-tricks-spreads-globally/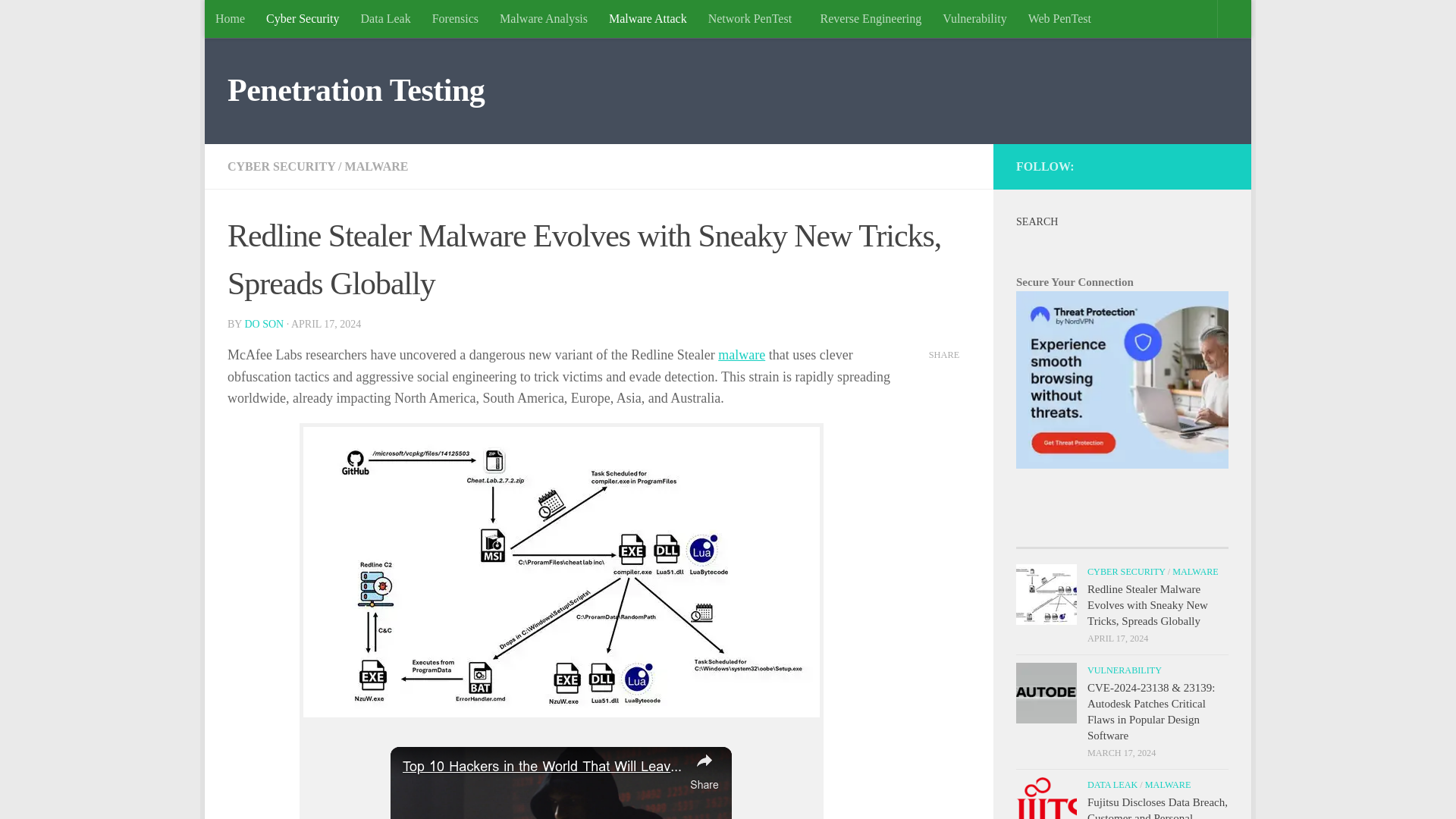
GitHub - cyrus-and/gdb-dashboard: Modular visual interface for GDB in Python
https://github.com/cyrus-and/gdb-dashboard
Cisco Says PoC Exploit Available for Newly Patched IMC Vulnerability - SecurityWeek
https://www.securityweek.com/cisco-says-poc-exploit-available-for-newly-patched-imc-vulnerability/
REKCAH - Black Hills Information Security
http://rekcahcomics.com
Google ad impersonates Whales Market to push wallet drainer malware
https://www.bleepingcomputer.com/news/security/google-ad-impersonates-whales-market-to-push-wallet-drainer-malware/
Deep Links & WebViews Exploitations Part II | by Just Mobile Security | Feb, 2024 | Medium
https://medium.com/@justmobilesec/deep-links-webviews-exploitations-part-ii-5c0b118ec6f1
Active Directory Hardening Series - Part 1 – Disabling NTLMv1 - Microsoft Community Hub
https://techcommunity.microsoft.com/t5/core-infrastructure-and-security/active-directory-hardening-series-part-1-disabling-ntlmv1/ba-p/3934787
Shielder - Element Android CVE-2024-26131, CVE-2024-26132 - Never Take Intents From Strangers
https://www.shielder.com/blog/2024/04/element-android-cve-2024-26131-cve-2024-26132-never-take-intents-from-strangers/
Mental health company Cerebral failed to protect sensitive personal data, must pay $7 million | Malwarebytes
https://www.malwarebytes.com/blog/news/2024/04/mental-health-company-cerebral-failed-to-protect-sensitive-personal-data-must-pay-7-million
Singapore infosec boss: splinternet hinders interoperability • The Register
https://go.theregister.com/feed/www.theregister.com/2024/04/18/blackhat_koh_splinternet/
Spearphish General Store
http://spearphishgeneralstore.com
Linux variant of Cerber ransomware targets Atlassian servers
https://securityaffairs.com/161962/cyber-crime/cerber-ransomware-cve-2023-22518-atlassian.html