Chaining N-days to Compromise All: Part 3 — Windows Driver LPE: Medium to System | by Theori Vulnerability Research | Apr, 2024 | Theori BLOG
https://blog.theori.io/chaining-n-days-to-compromise-all-part-3-windows-driver-lpe-medium-to-system-12f7821d97bb?source=social.tw
GMER - the art of exposing Windows rootkits in kernel mode | A blog about rootkits research and the Windows kernel
https://artemonsecurity.blogspot.com/2024/04/gmer-art-of-exposing-windows-rootkits.html
Speakers | OffensiveCon
https://www.offensivecon.org/speakers/
10-Year-Old 'RUBYCARP' Romanian Hacker Group Surfaces with Botnet
https://thehackernews.com/2024/04/10-year-old-rubycarp-romanian-hacker.html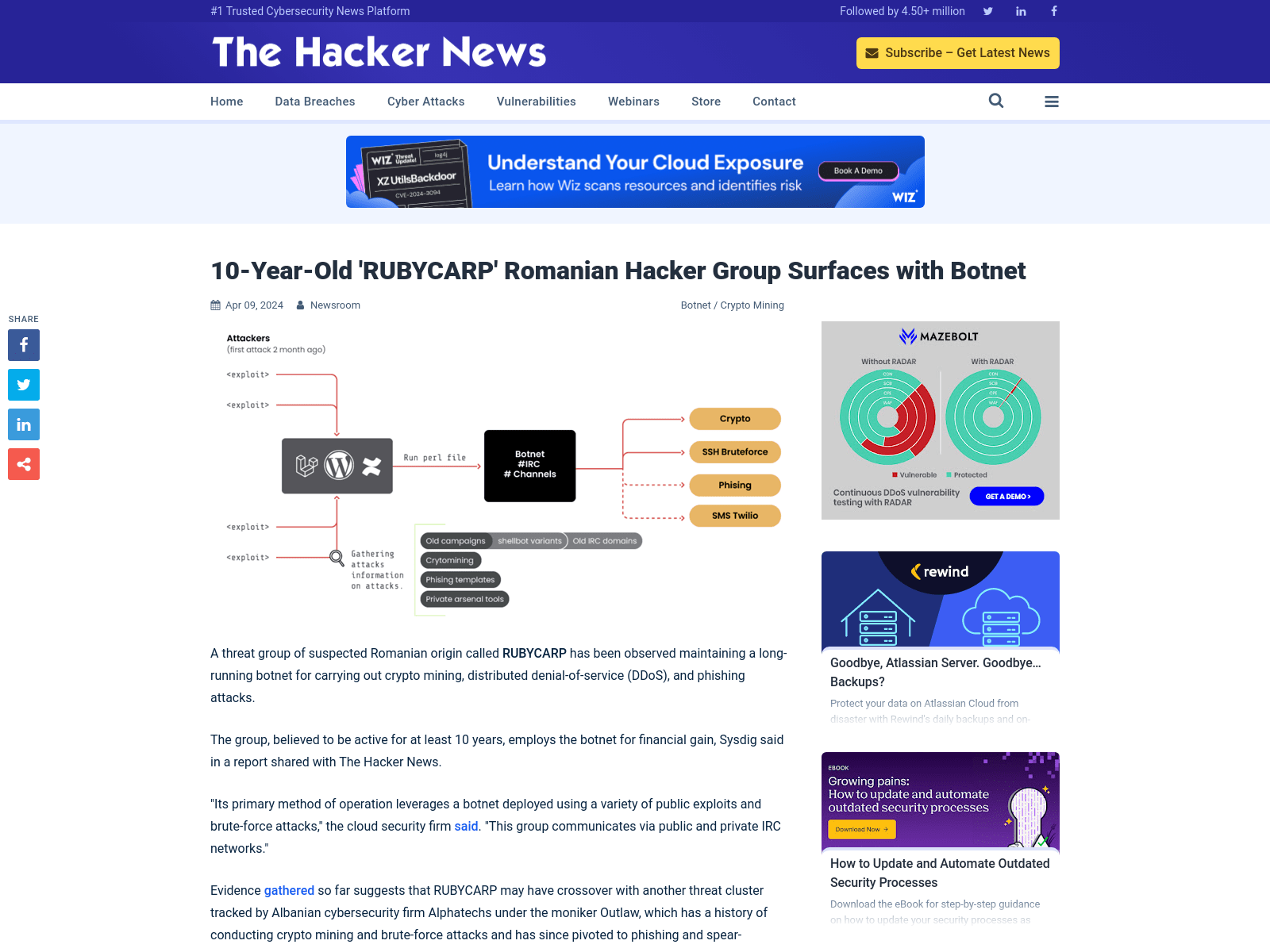
Over 90,000 LG Smart TVs may be exposed to remote attacks
https://www.bleepingcomputer.com/news/security/over-90-000-lg-smart-tvs-may-be-exposed-to-remote-attacks/
Microsoft April 2024 Patch Tuesday fixes 150 security flaws, 67 RCEs
https://www.bleepingcomputer.com/news/microsoft/microsoft-april-2024-patch-tuesday-fixes-150-security-flaws-67-rces/
Targus discloses cyberattack after hackers detected on file servers
https://www.bleepingcomputer.com/news/security/targus-discloses-cyberattack-after-hackers-detected-on-file-servers/
GHC-SCW: Ransomware gang stole health data of 533,000 people
https://www.bleepingcomputer.com/news/security/ghc-scw-ransomware-gang-stole-health-data-of-533-000-people/
Ransomware gang’s new extortion trick? Calling the front desk | TechCrunch
https://techcrunch.com/2024/04/09/ransomware-gang-fail-calling-front-desk-extortion/
New SharePoint flaws help hackers evade detection when stealing files
https://www.bleepingcomputer.com/news/security/new-sharepoint-flaws-help-hackers-evade-detection-when-stealing-files/
Tapping into the potential of Memory Dump Emulation
https://blahcat.github.io/posts/2024/01/27/tapping-into-the-potential-of-memory-dump-emulation.html
Emulate to Exploitate
https://exploitthis.ctfd.io
Security Update Guide - Microsoft
https://msft.it/60119yPTS
#100DaysofYARA 2024 – Day 100 – MAILSLOT – Cyber Poking
https://cyberpoking.com/2024/04/09/100daysofyara-2024-day-100-mailslot/
🔃 Security Update Guide - Loading - Microsoft
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-26228
CVS Group Restoring Systems Impacted by Cyberattack - SecurityWeek
https://www.securityweek.com/cvs-group-restoring-systems-impacted-by-cyberattack/
35-year long identity theft leads to imprisonment for victim | Malwarebytes
https://www.malwarebytes.com/blog/news/2024/04/35-year-long-identity-theft-leads-to-imprisonment-for-victim
Critical Rust flaw enables Windows command injection attacks
https://www.bleepingcomputer.com/news/security/critical-rust-flaw-enables-windows-command-injection-attacks/
Shazzer - Shared online fuzzing
https://shazzer.co.uk/
Zyxel USG SSH Backdoor Attempt | GreyNoise Visualizer
https://viz.greynoise.io/tags/zyxel-usg-ssh-backdoor-attempt?days=10
Attackers Using Obfuscation Tools to Deliver Multi-Stage Malware via Invoice Phishing
https://thehackernews.com/2024/04/attackers-using-obfuscation-tools-to.html
bochscpu-python/examples/long_mode_emulate_windows_udump.py at main · hugsy/bochscpu-python · GitHub
https://github.com/hugsy/bochscpu-python/blob/main/examples/long_mode_emulate_windows_udump.py
ScrubCrypt used to drop VenomRAT along with many malicious plugins
https://securityaffairs.com/161639/cyber-crime/scrubcrypt-venomrat-plugins.html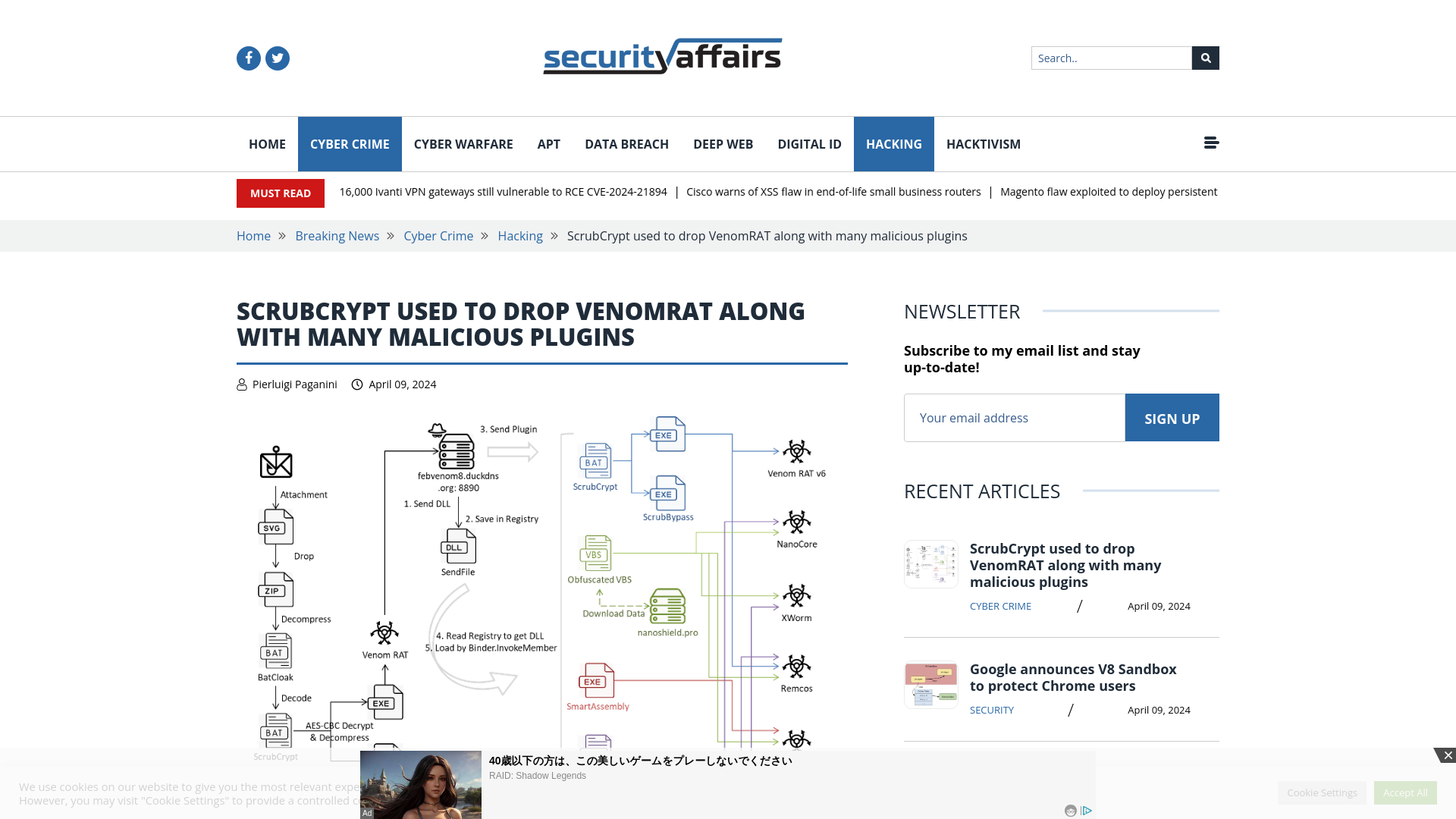
CVE-2024-24576 (CVSS 10): Rust Flaw Exposes Windows Systems to Command Injection Attacks
https://securityonline.info/cve-2024-24576-cvss-10-rust-flaw-exposes-windows-systems-to-command-injection-attacks/
Crowdfense is offering a larger $30M exploit acquisition program
https://securityaffairs.com/161584/hacking/crowdfense-30m-exploit-acquisition-program.html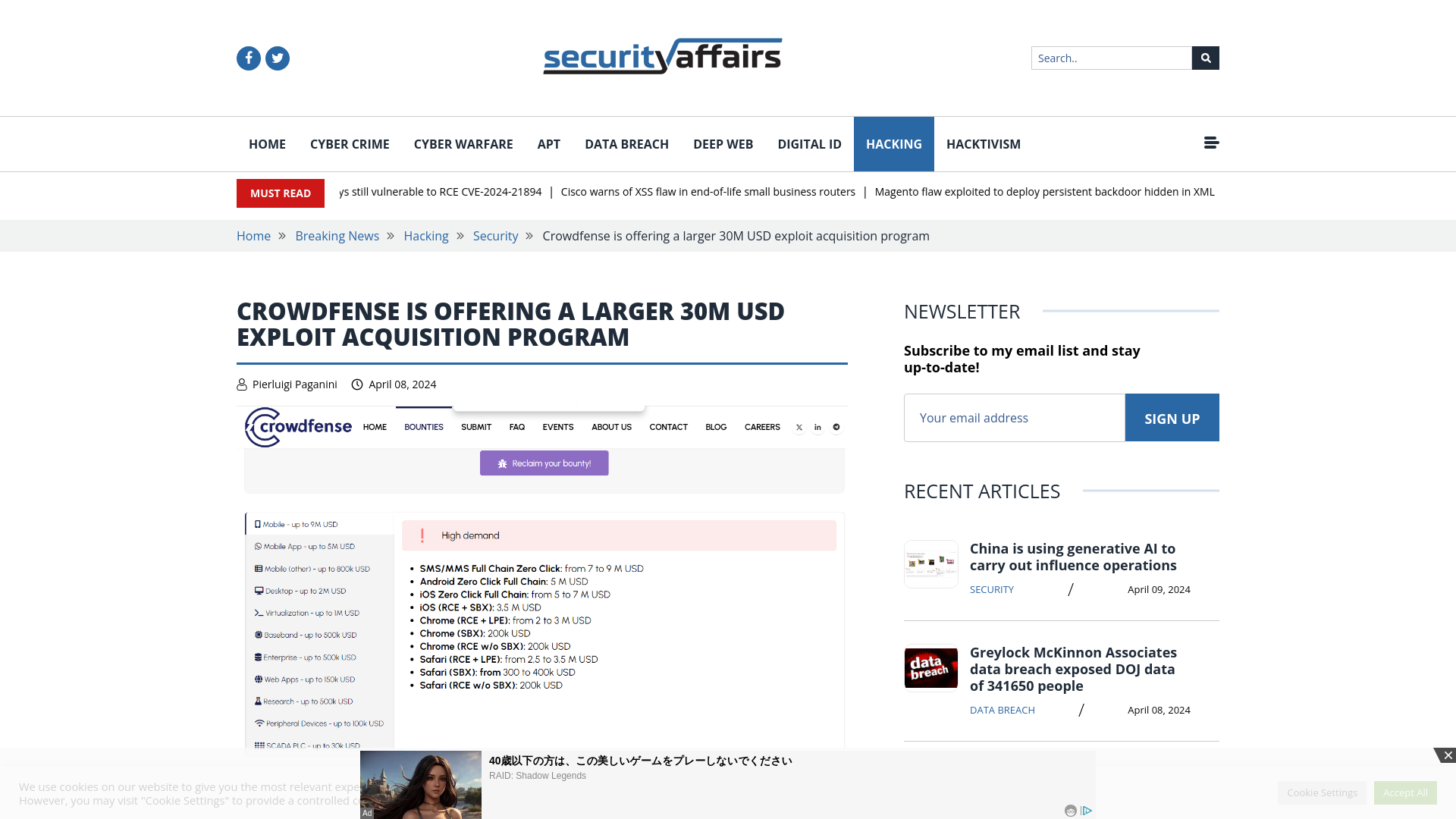
Microsoft patches actively exploited security feature bypass vulnerability (CVE-2024-29988) - Help Net Security
https://www.helpnetsecurity.com/2024/04/09/april-2024-patch-tuesday-cve-2024-29988/
Quick References | The Cyber Yeti
https://www.thecyberyeti.com/quick-references
Microsoft BitLocker Bypasses are Practical – Compass Security Blog
https://blog.compass-security.com/2024/02/microsoft-bitlocker-bypasses-are-practical/
GitHub - RedByte1337/GraphSpy: Initial Access and Post-Exploitation Tool for AAD and O365 with a browser-based GUI
https://github.com/RedByte1337/GraphSpy
Hackers Targeting Human Rights Activists in Morocco and Western Sahara
https://thehackernews.com/2024/04/hackers-targeting-human-rights.html
Webinar Registration - Zoom
https://us06web.zoom.us/webinar/register/WN_GjWVolQiRDi7zdLA9gJgWg
Critical Flaws Leave 92,000 D-Link NAS Devices Vulnerable to Malware Attacks
https://thehackernews.com/2024/04/critical-flaws-leave-92000-d-link-nas.html
Samuel Groß | OffensiveCon
https://www.offensivecon.org/speakers/2024/samuel-gro%C3%9F.html
Zero Day Initiative — The April 2024 Security Updates Review
https://www.zerodayinitiative.com/blog/2024/4/9/the-april-2024-security-updates-review
Researchers Discover LG Smart TV Vulnerabilities Allowing Root Access
https://thehackernews.com/2024/04/researchers-discover-lg-smart-tv.html
ICS Patch Tuesday: Siemens Addresses Palo Alto Networks Product Vulnerabilities - SecurityWeek
https://www.securityweek.com/ics-patch-tuesday-siemens-addresses-palo-alto-networks-product-vulnerabilities/
Charles Fol | OffensiveCon
https://www.offensivecon.org/speakers/2024/charles-fol.html
#OBTS v7.0
https://objectivebythesea.org/v7/index.html