WinDbg_Scripts/symbolBuilderLogIoctls.js at master · yardenshafir/WinDbg_Scripts · GitHub
https://github.com/yardenshafir/WinDbg_Scripts/blob/master/symbolBuilderLogIoctls.js
GitHub - yoryio/CVE-2024-20767: Exploit for CVE-2024-20767 - Adobe ColdFusion
https://github.com/yoryio/CVE-2024-20767
APT37 그룹의 RoKRAT 파일리스 공격 증가
https://www.genians.co.kr/blog/threat_intelligence/rokrat
A review of zero-day in-the-wild exploits in 2023
https://blog.google/technology/safety-security/a-review-of-zero-day-in-the-wild-exploits-in-2023/
CISA Warns: Hackers Actively Attacking Microsoft SharePoint Vulnerability
https://thehackernews.com/2024/03/cisa-warns-hackers-actively-attacking.html
Critical Unpatched Ray AI Platform Vulnerability Exploited for Cryptocurrency Mining
https://thehackernews.com/2024/03/critical-unpatched-ray-ai-platform.html
Alert: New Phishing Attack Delivers Keylogger Disguised as Bank Payment Notice
https://thehackernews.com/2024/03/alert-new-phishing-attack-delivers.html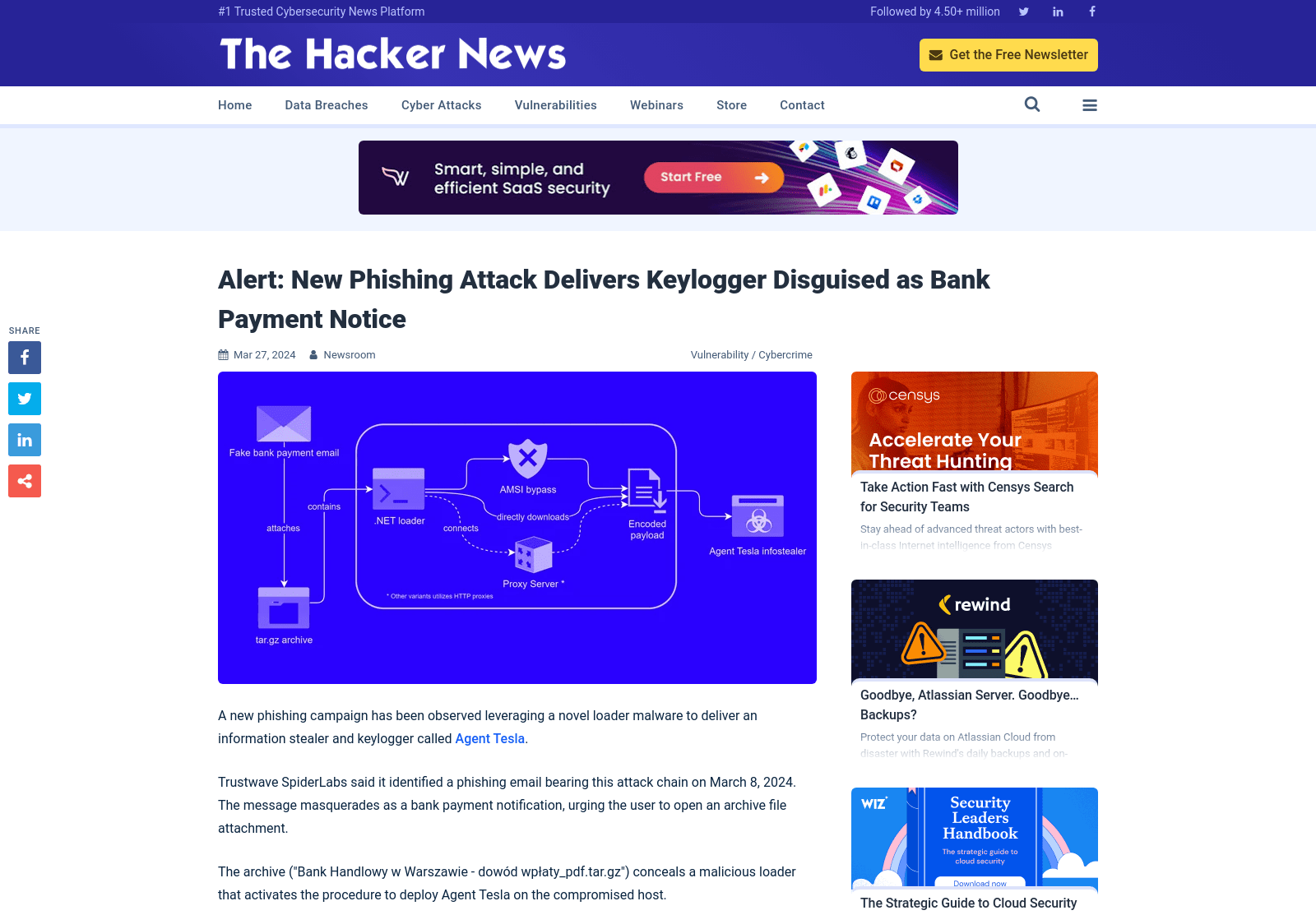
Microsoft Edge Bug Could Have Allowed Attackers to Silently Install Malicious Extensions
https://thehackernews.com/2024/03/microsoft-edge-bug-could-have-allowed.html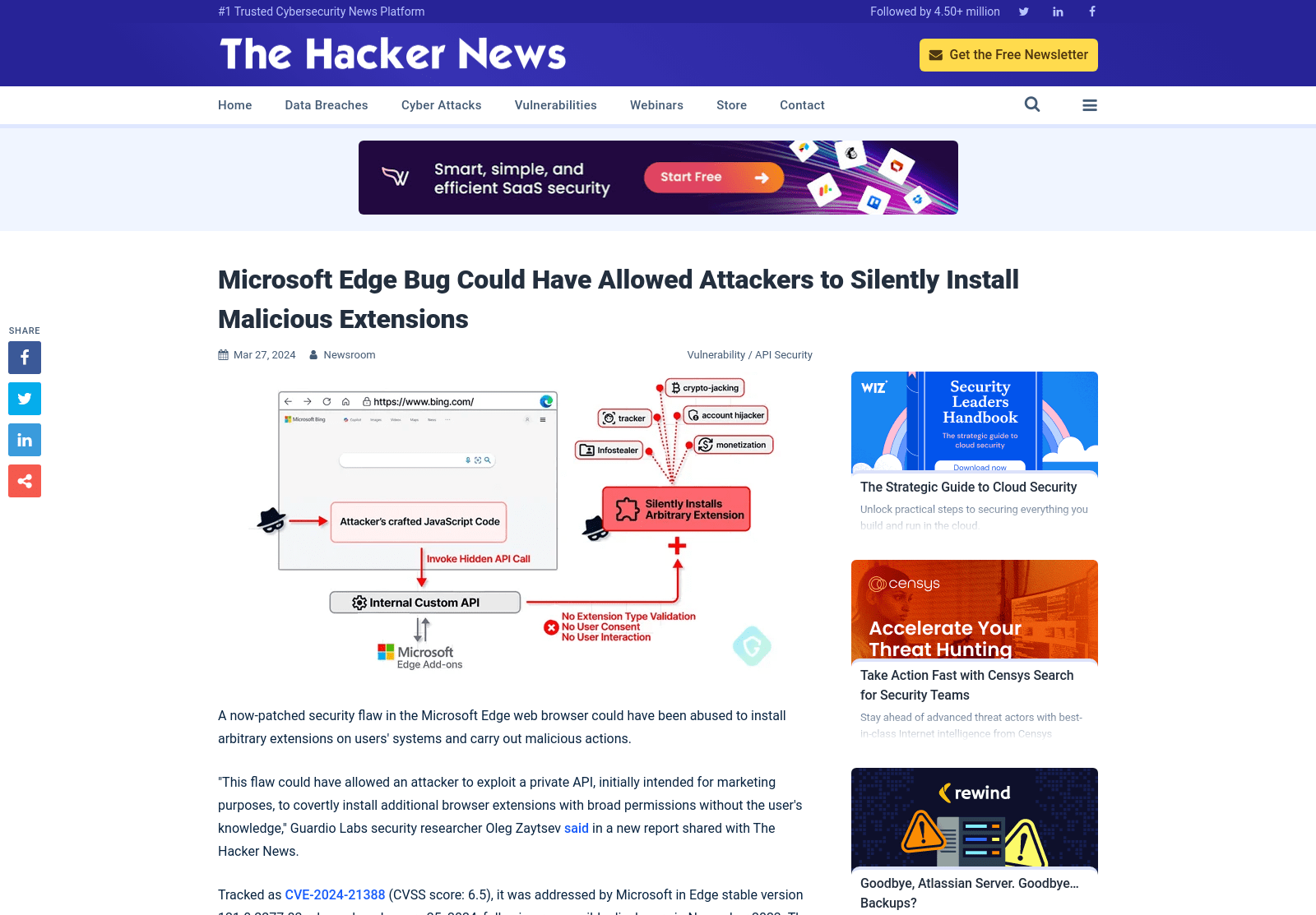
Abusing MiniFilter Altitude to blind EDR
https://tierzerosecurity.co.nz/2024/03/27/blind-edr.html
Two Chinese APT Groups Ramp Up Cyber Espionage Against ASEAN Countries
https://thehackernews.com/2024/03/two-chinese-apt-groups-ramp-up-cyber.html
KuCoin charged with AML violations that let cybercriminals launder billions
https://www.bleepingcomputer.com/news/cryptocurrency/kucoin-charged-with-aml-violations-that-let-cybercriminals-launder-billions/
ShadowRay: First Known Attack Campaign Targeting AI Workloads Exploited In The Wild
https://www.oligo.security/blog/shadowray-attack-ai-workloads-actively-exploited-in-the-wild
Organizations Informed of 10 Vulnerabilities in Rockwell Automation Products - SecurityWeek
https://www.securityweek.com/organizations-informed-of-10-vulnerabilities-in-rockwell-automation-products/
$700 cybercrime software turns Raspberry Pi into an evasive fraud tool
https://www.bleepingcomputer.com/news/security/700-cybercrime-software-turns-raspberry-pi-into-an-evasive-fraud-tool/
Weblogic/Weblogic_Serialization_Vulnerability_and_IIOP_Protocol_en_US.md at main · gobysec/Weblogic · GitHub
https://github.com/gobysec/Weblogic/blob/main/Weblogic_Serialization_Vulnerability_and_IIOP_Protocol_en_US.md
Untitled / X
https://twitter.com/i/broadcasts/1rmGPMPVQAEJN
Zero Day Engineering by Alisa Esage
http://zerodayengineering.com
Google fixes Chrome zero-days exploited at Pwn2Own 2024
https://www.bleepingcomputer.com/news/security/google-fixes-chrome-zero-days-exploited-at-pwn2own-2024/
curl | Report #2402845 - CVE-2024-2398: HTTP/2 push headers memory-leak | HackerOne
https://hackerone.com/reports/2402845
MalwareBazaar | SHA256 de29ff5d531e11ec17eaa1abfb75c3cdf7c2e3e37bfbae61711aee41f20118b0 (Latrodectus)
https://bazaar.abuse.ch/sample/de29ff5d531e11ec17eaa1abfb75c3cdf7c2e3e37bfbae61711aee41f20118b0/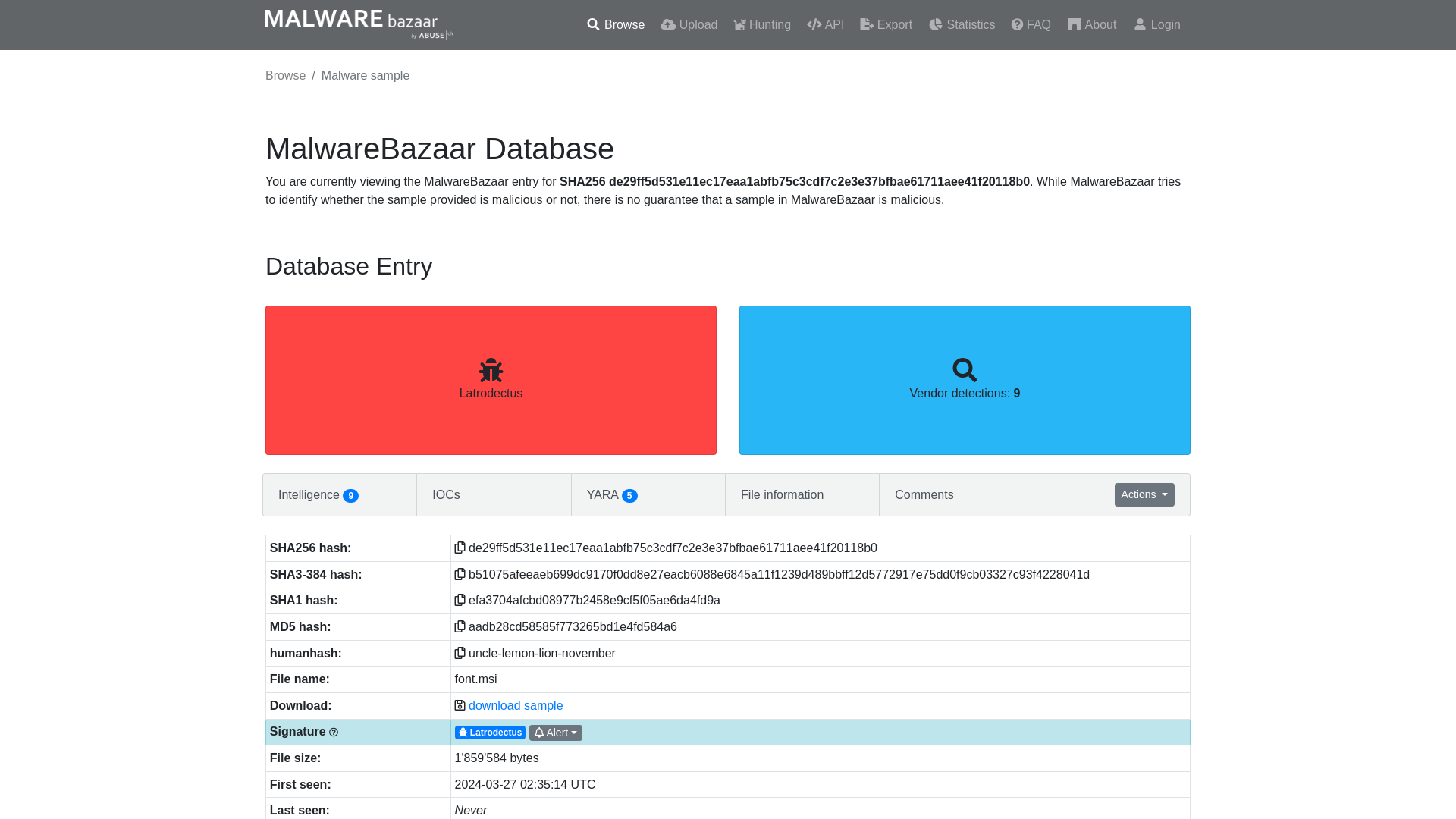
Dissecting a complex vulnerability and achieving arbitrary code execution in Ichitaro Word
https://blog.talosintelligence.com/exploiting-low-severity-vulnerability-using-a-frame-pointer-overwrite/
Unidentified 111 (Latrodectus) (Malware Family)
https://malpedia.caad.fkie.fraunhofer.de/details/win.unidentified_111
Flipping Pages: An analysis of a new Linux vulnerability in nf_tables and hardened exploitation techniques
https://pwning.tech/nftables/
“CVE-2024-21388”- Microsoft Edge’s Marketing API Exploited for Covert Extension Installation | by Guardio | Mar, 2024 | Medium
https://labs.guard.io/cve-2024-21388-microsoft-edges-marketing-api-exploited-for-covert-extension-installation-879fe5ad35ca
Meta to abandon social media tracking tool CrowdTangle | Malwarebytes
https://www.malwarebytes.com/blog/news/2024/03/meta-to-abandon-social-media-tracking-tool-crowdtangle
CISA Warns of Active CVE-2023-24955 Exploitation in Microsoft SharePoint Server
https://securityonline.info/cisa-warns-of-active-cve-2023-24955-exploitation-in-microsoft-sharepoint-server/
CISA tags Microsoft SharePoint RCE bug as actively exploited
https://www.bleepingcomputer.com/news/security/cisa-tags-microsoft-sharepoint-rce-bug-as-actively-exploited/
PwnAgent: A One-Click WAN-side RCE in Netgear RAX Routers with CVE-2023-24749
https://mahaloz.re/2023/02/25/pwnagent-netgear.html
Hackers Hit Indian Defense, Energy Sectors with Malware Posing as Air Force Invite
https://thehackernews.com/2024/03/hackers-target-indian-defense-and.html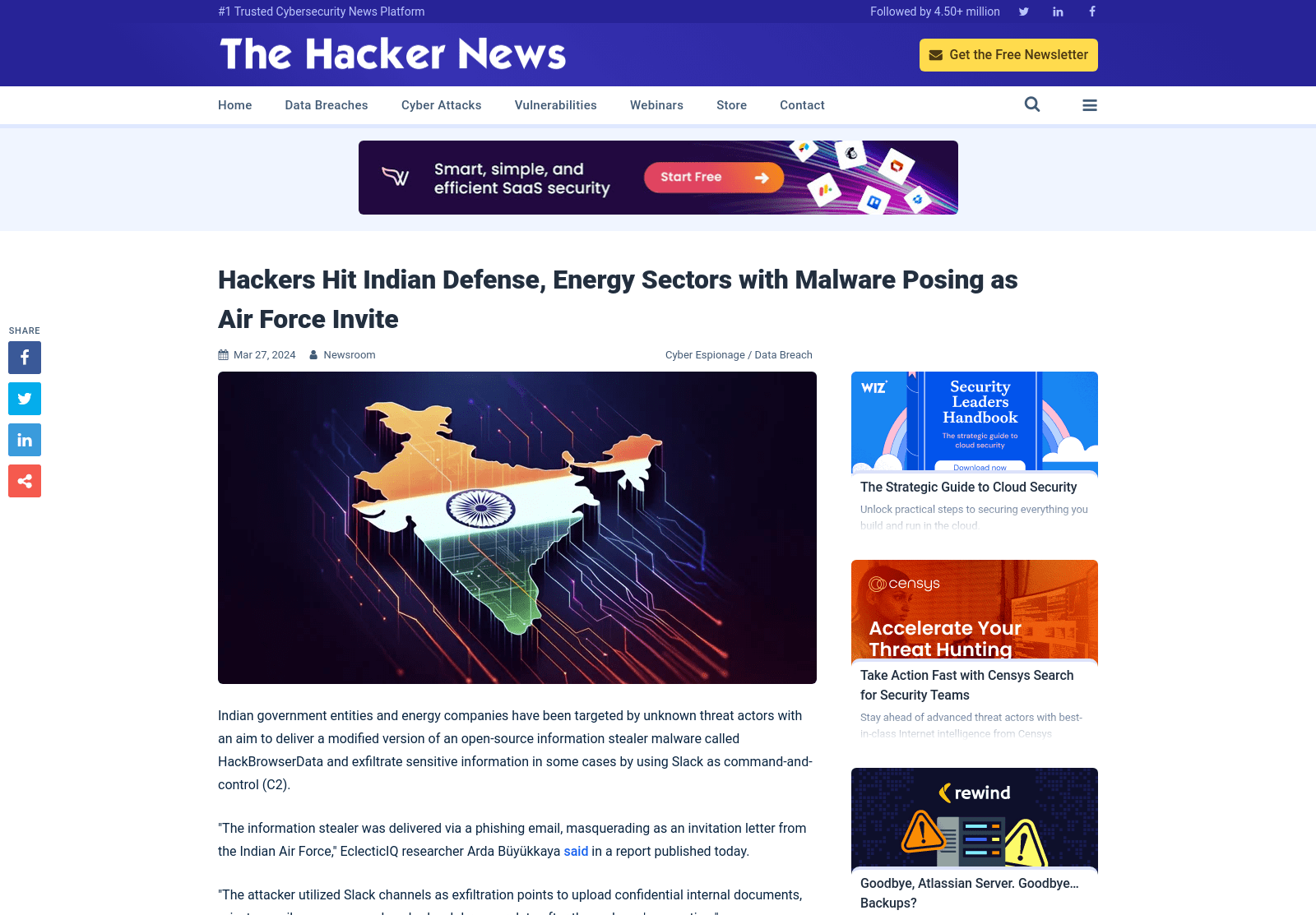
Google: Spyware vendors behind 50% of zero-days exploited in 2023
https://www.bleepingcomputer.com/news/security/google-spyware-vendors-behind-50-percent-of-zero-days-exploited-in-2023/
VPN Apps on Google Play Turn Android Devices Into Proxies - SecurityWeek
https://www.securityweek.com/vpn-apps-on-google-play-turn-android-devices-into-proxies/
Drozer: Open-source Android security assessment framework - Help Net Security
https://www.helpnetsecurity.com/2024/03/27/drozer-open-source-android-security-assessment-framework/
Roles Allowing To Abuse Entra ID Federation for Persistence and Privilege Escalation | Tenable TechBlog
https://medium.com/tenable-techblog/roles-allowing-to-abuse-entra-id-federation-for-persistence-and-privilege-escalation-df9ca6e58360
Code Execution Flaws Haunt NVIDIA ChatRTX for Windows - SecurityWeek
https://www.securityweek.com/code-execution-flaws-haunt-nvidia-chatrtx-for-windows/
ASEAN Entities in the Spotlight: Chinese APT Group Targeting
https://unit42.paloaltonetworks.com/chinese-apts-target-asean-entities/
curl | Report #2410774 - CVE-2024-2379: QUIC certificate check bypass with wolfSSL | HackerOne
https://hackerone.com/reports/2410774
ホーム | マイナポータル
https://myna.go.jp/
INC Ransom threatens to leak 3TB of NHS Scotland stolen data
https://www.bleepingcomputer.com/news/security/inc-ransom-threatens-to-leak-3tb-of-nhs-scotland-stolen-data/
Zero-days exploited in the wild jumped 50% in 2023, fueled by spyware vendors
https://therecord.media/zero-day-exploits-jumped-in-2023-spyware
Analysis lnvoice-1445766252.pdf.js (MD5: 258B1E8DE4924787FB4032649A9ACD49) Malicious activity - Interactive analysis ANY.RUN
https://app.any.run/tasks/d7fe276d-82e2-421c-92c5-8b0e4a9a65e5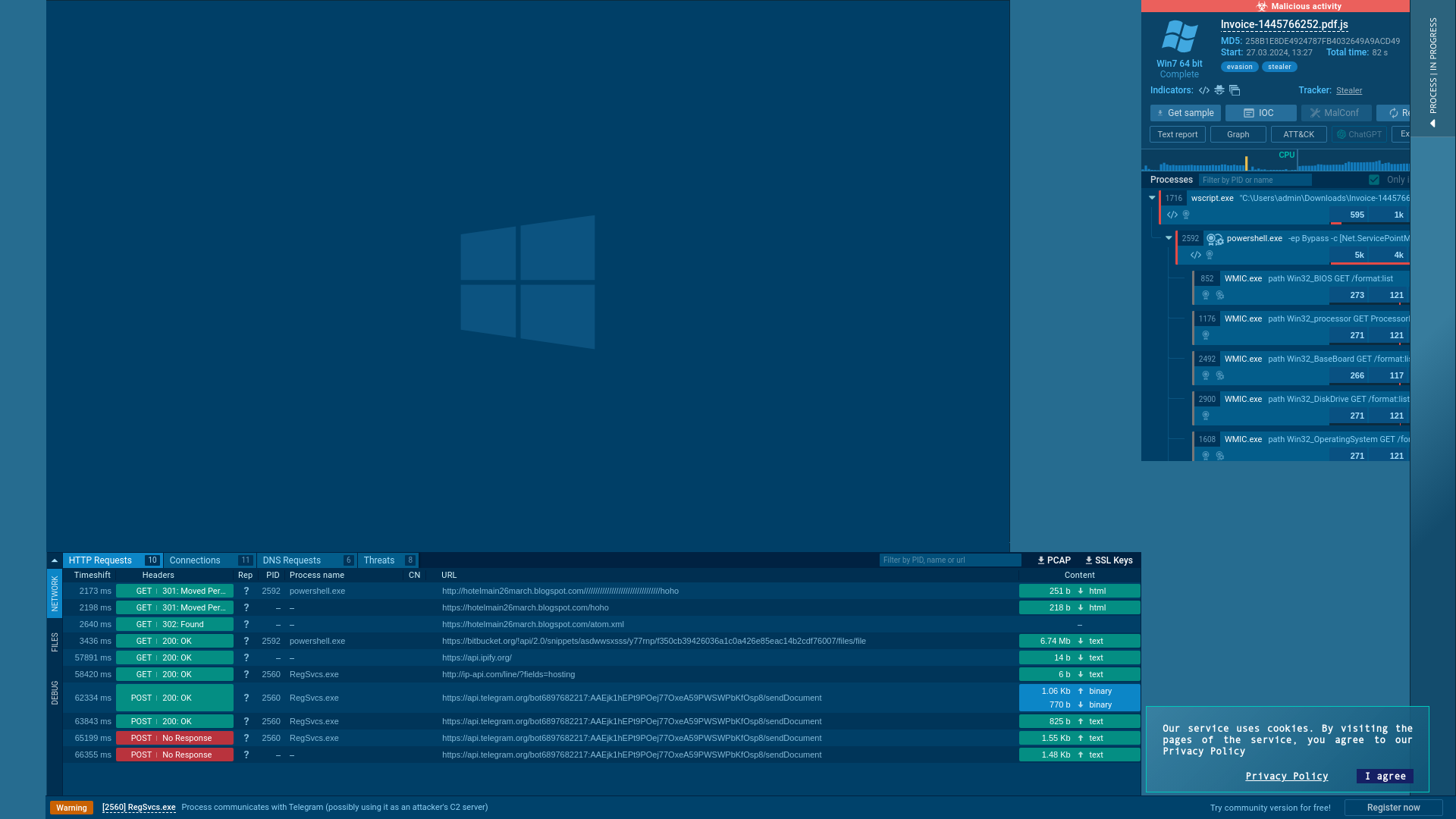
Disturbing robocaller fined $9.9 million | Malwarebytes
https://www.malwarebytes.com/blog/news/2024/03/disturbing-robocaller-fined-9-9-million
Finland confirms APT31 hackers behind 2021 parliament breach
https://www.bleepingcomputer.com/news/security/finland-confirms-apt31-hackers-behind-2021-parliament-breach/
Agent Customization in Mythic: Tailoring Tools for Red Team Needs | by Cody Thomas | Mar, 2024 | Medium
https://medium.com/@its_a_feature_/agent-customization-in-mythic-tailoring-tools-for-red-team-needs-1746fd02177f