Overview of GLIBC heap exploitation techniques
https://0x434b.dev/overview-of-glibc-heap-exploitation-techniques/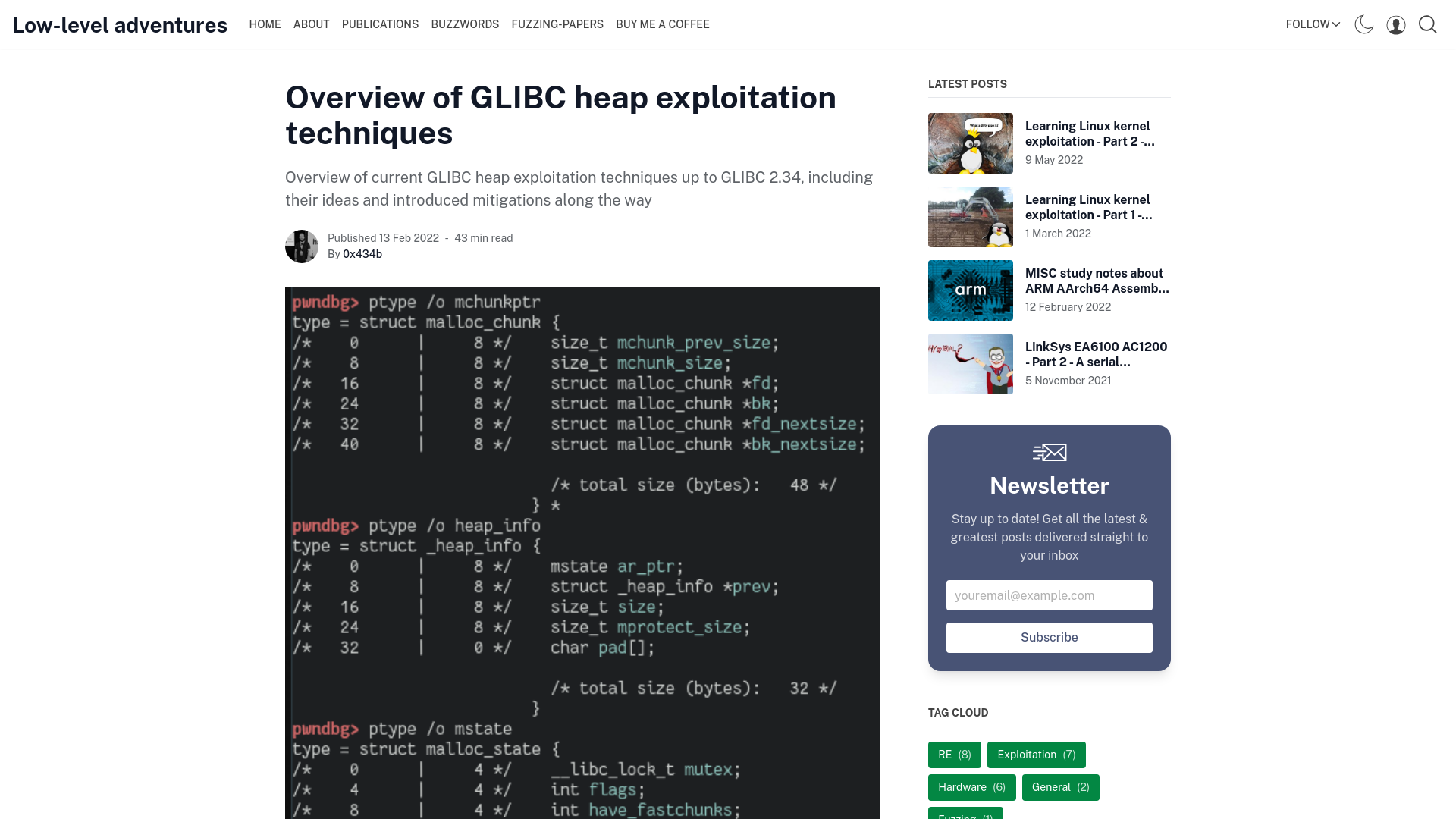
New Phishing Attack Uses Clever Microsoft Office Trick to Deploy NetSupport RAT
https://thehackernews.com/2024/03/new-phishing-attack-uses-clever.html
Bypassing EDRs With EDR-Preloading
https://malwaretech.com/2024/02/bypassing-edrs-with-edr-preload.html
Gaining kernel code execution on an MTE-enabled Pixel 8 - The GitHub Blog
https://github.blog/2024-03-18-gaining-kernel-code-execution-on-an-mte-enabled-pixel-8/
Hackers Exploiting Popular Document Publishing Sites for Phishing Attacks
https://thehackernews.com/2024/03/hackers-exploiting-popular-document.html
E-Root Marketplace Admin Sentenced to 42 Months for Selling 350K Stolen Credentials
https://thehackernews.com/2024/03/e-root-marketplace-admin-sentenced-to.html
Microsoft announces deprecation of 1024-bit RSA keys in Windows
https://www.bleepingcomputer.com/news/microsoft/microsoft-announces-deprecation-of-1024-bit-rsa-keys-in-windows/
Suspected Russian Data-Wiping 'AcidPour' Malware Targeting Linux x86 Devices
https://thehackernews.com/2024/03/suspected-russian-data-wiping-acidpour.html
Ukraine arrests hackers trying to sell 100 million stolen accounts
https://www.bleepingcomputer.com/news/security/ukraine-arrests-hackers-trying-to-sell-100-million-stolen-accounts/
Finding pastures new: An alternate approach for implant design | by Sapientflow | Mar, 2024 | Medium
https://medium.com/@sapientflow/finding-pastures-new-an-alternate-approach-for-implant-design-644611c526ca
PoC Releases for 0-day CVE-2024-21762 FortiGate SSLVPN Flaw, Over 133K Remain Vulnerable
https://securityonline.info/poc-releases-for-0-day-cve-2024-21762-fortigate-sslvpn-flaw-over-133k-remain-vulnerable/
SANS Security West San Diego 2024 | Cyber Security Training
https://www.sans.org/u/1uZO
Untitled / X
https://twitter.com/i/broadcasts/1ynKOyWQYZlJR
New AcidPour data wiper targets Linux x86 network devices
https://www.bleepingcomputer.com/news/security/new-acidpour-data-wiper-targets-linux-x86-network-devices/
White House and EPA warn of hackers breaching water systems
https://www.bleepingcomputer.com/news/security/white-house-and-epa-warn-of-hackers-breaching-water-systems/
AIS247: AI Security Essentials for Business Leaders | SANS Institute
https://www.sans.org/u/1ukG
CVE-2023-7102: A zero-day flaw affects Barracuda Email Security Gateway
https://securityonline.info/cve-2023-7101-cve-2023-7102-two-0-day-flaws-affect-barracuda-email-security-gateway/
Social media influencers targeted by identity thieves | Malwarebytes
https://www.malwarebytes.com/blog/news/2024/03/social-media-influencers-targeted-by-identity-thieves
Tsunami Network Scanner & AI Security - Google Bug Hunters
https://bughunters.google.com/blog/5691890239930368/tsunami-network-scanner-ai-security
Chinese APT Hacks 48 Government Organizations - SecurityWeek
https://www.securityweek.com/chinese-apt-hacks-48-government-organizations/
FTC warns scammers are impersonating its employees to steal money
https://www.bleepingcomputer.com/news/security/ftc-warns-scammers-are-impersonating-its-employees-to-steal-money/
APIs Drive the Majority of Internet Traffic and Cybercriminals are Taking Advantage
https://thehackernews.com/2024/03/apis-drive-majority-of-internet-traffic.html
Players hacked during the matches of Apex Legends Global Series
https://securityaffairs.com/160726/hacking/apex-legends-global-series-hack.html
Chinese Earth Krahang hackers breach 70 orgs in 23 countries
https://www.bleepingcomputer.com/news/security/chinese-earth-krahang-hackers-breach-70-orgs-in-23-countries/
Live Debugging Techniques for the Linux Kernel, Part 1 of 3
https://blogs.oracle.com/linux/post/live-kernel-debugging-1
Oracle warns that macOS 14.4 update breaks Java on Apple CPUs
https://www.bleepingcomputer.com/news/apple/oracle-warns-that-macos-144-update-breaks-java-on-apple-cpus/
Weaponizing Windows Thread Pool APIs: Proxying DLL Loads Using I/O Completion Callbacks - fin3ss3g0d's Blog
https://fin3ss3g0d.net/index.php/2024/03/18/weaponizing-windows-thread-pool-apis-proxying-dll-loads/
Store manager admits SIM swapping his customers | Malwarebytes
https://www.malwarebytes.com/blog/news/2024/03/store-manager-admits-sim-swapping-his-customers
Leveraging the Direct Pointer A Stealthy Maneuver in Evasion Tactics
https://lsecqt.github.io/Red-Teaming-Army/malware-development/leveraging-the-direct-pointer---a-stealthy-maneuver-in-evasion-tactics/
Subdomain Fuzzing worth 35k bounty! | by HX007 | Mar, 2024 | Medium
https://medium.com/@HX007/subdomain-fuzzing-worth-35k-bounty-daebcb56d9bc
Earth Krahang APT breached tens of government orgs worldwide
https://securityaffairs.com/160702/apt/earth-krahang-apt.html