1 little known secret of explorer.exe | Hexacorn
https://www.hexacorn.com/blog/2024/03/03/1-little-known-secret-of-explorer-exe/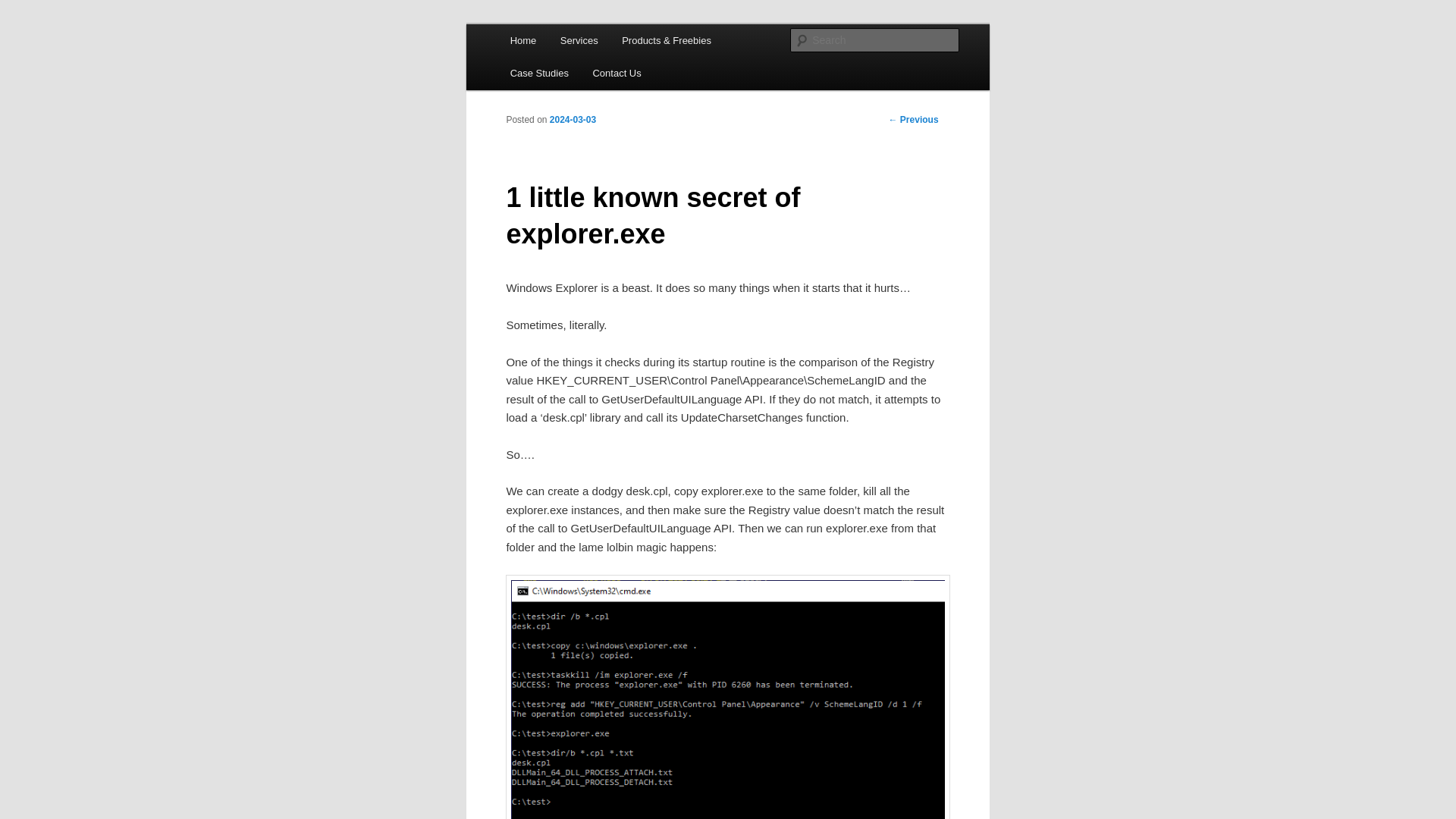
Introducing APT-Hunter : Threat Hunting Tool via Windows Event Log - Shells.Systems
https://shells.systems/introducing-apt-hunter-threat-hunting-tool-via-windows-event-log/
A Guide to ARM64 / AArch64 Assembly on Linux with Shellcodes and Cryptography | modexp
https://modexp.wordpress.com/2018/10/30/arm64-assembly/
Hackers target FCC, crypto firms in advanced Okta phishing attacks
https://www.bleepingcomputer.com/news/security/hackers-target-fcc-crypto-firms-in-advanced-okta-phishing-attacks/
Zeus WPI | Unveiling secrets of the ESP32: creating an open-source MAC Layer
https://zeus.ugent.be/blog/23-24/open-source-esp32-wifi-mac/
ADCS ESC14 Abuse Technique. The altSecurityIdentities attribute of… | by Jonas Bülow Knudsen | Feb, 2024 | Posts By SpecterOps Team Members
https://posts.specterops.io/adcs-esc14-abuse-technique-333a004dc2b9
Eken camera doorbells allow ill-intentioned individuals to spy on you
https://securityaffairs.com/159883/hacking/eken-camera-doorbells-flaws.html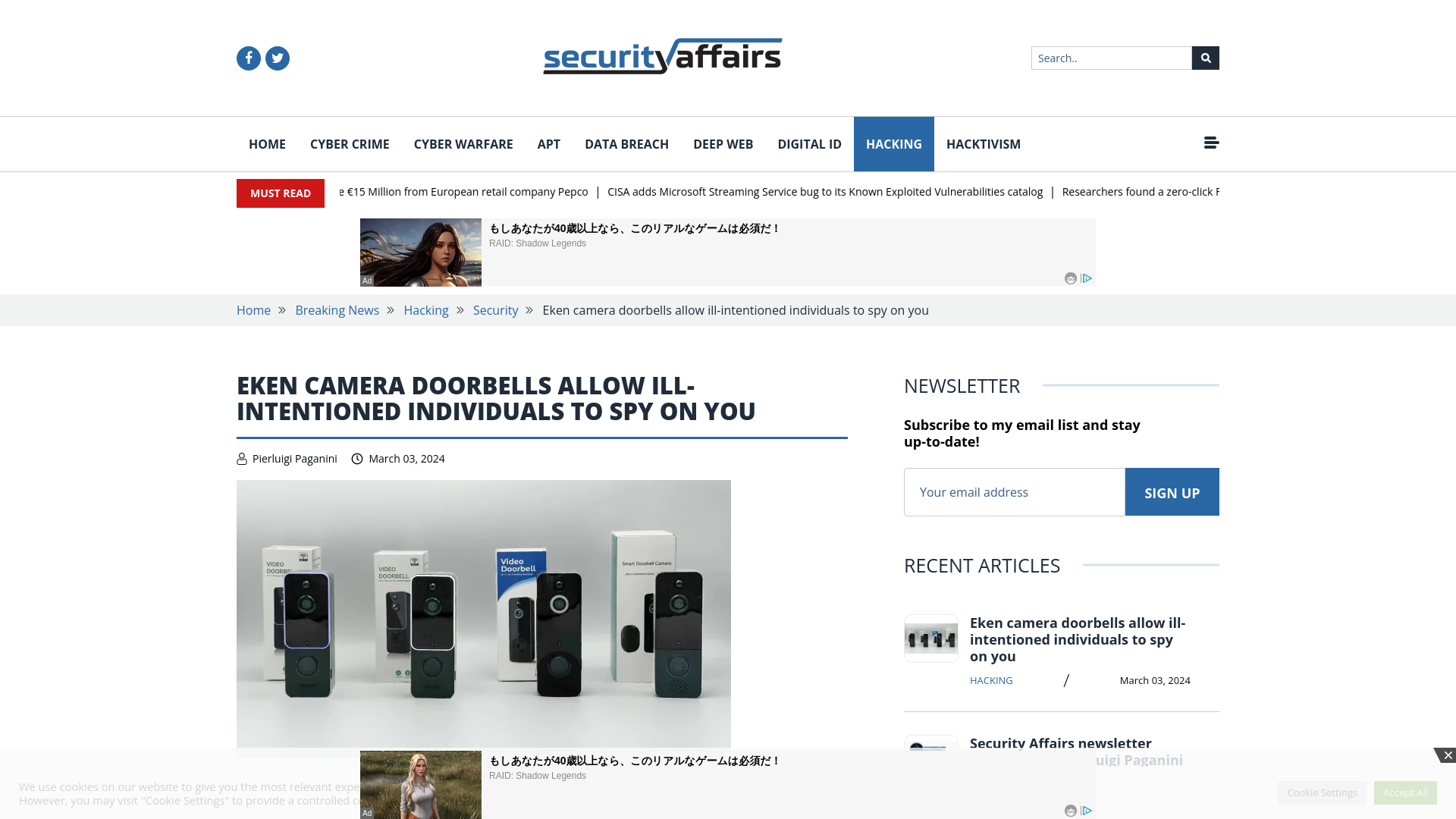
Practical Introduction to BLE GATT Reverse Engineering: Hacking the Domyos EL500 · Hack The World
https://jcjc-dev.com/2023/03/19/reversing-domyos-el500-elliptical/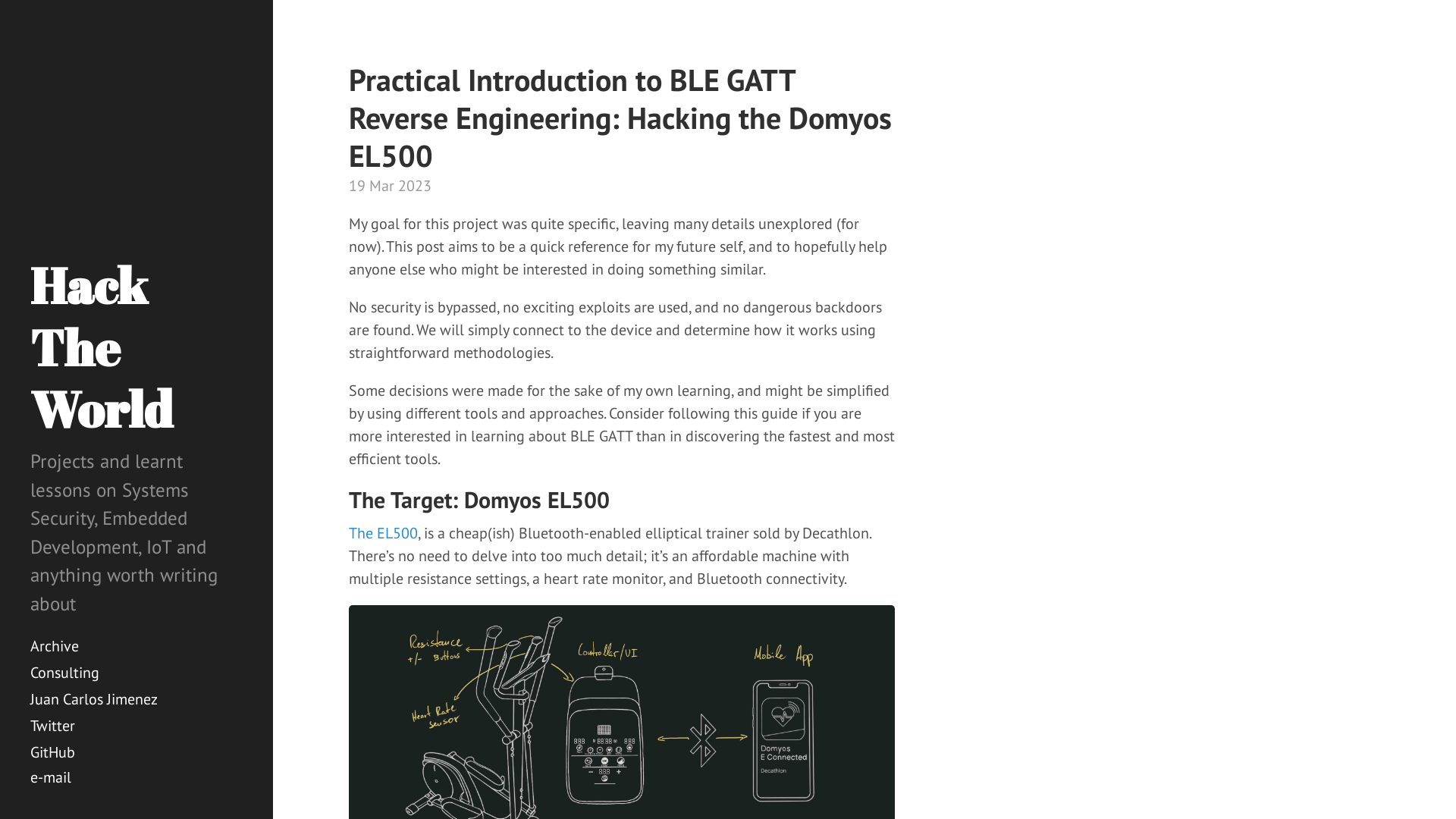
GitHub - BishopFox/cve-2024-21762-check: Safely detect whether a FortiGate SSL VPN is vulnerable to CVE-2024-21762
https://github.com/BishopFox/cve-2024-21762-check
We Hacked Google A.I. for $50,000 - Lupin & Holmes
https://www.landh.tech/blog/20240304-google-hack-50000
U.S. Judge ordered NSO Group to hand over the Pegasus spyware code to WhatsApp
https://securityaffairs.com/159847/security/nso-group-vs-meta-pegasus-hand-over.html
Rust-for-Malware-Development/dll_injection at main · Whitecat18/Rust-for-Malware-Development · GitHub
https://github.com/Whitecat18/Rust-for-Malware-Development/tree/main/dll_injection#dll-injection-using-rust
MultiDump - Xre0uS
https://xre0us.io/posts/multidump/
Extracting Secure Onboard Communication (SecOC) keys from a 2021 Toyota RAV4 Prime Power | I CAN Hack
https://icanhack.nl/blog/secoc-key-extraction/
DUALITY - Part 1
https://www.aon.com/en/insights/cyber-labs/duality-part-1
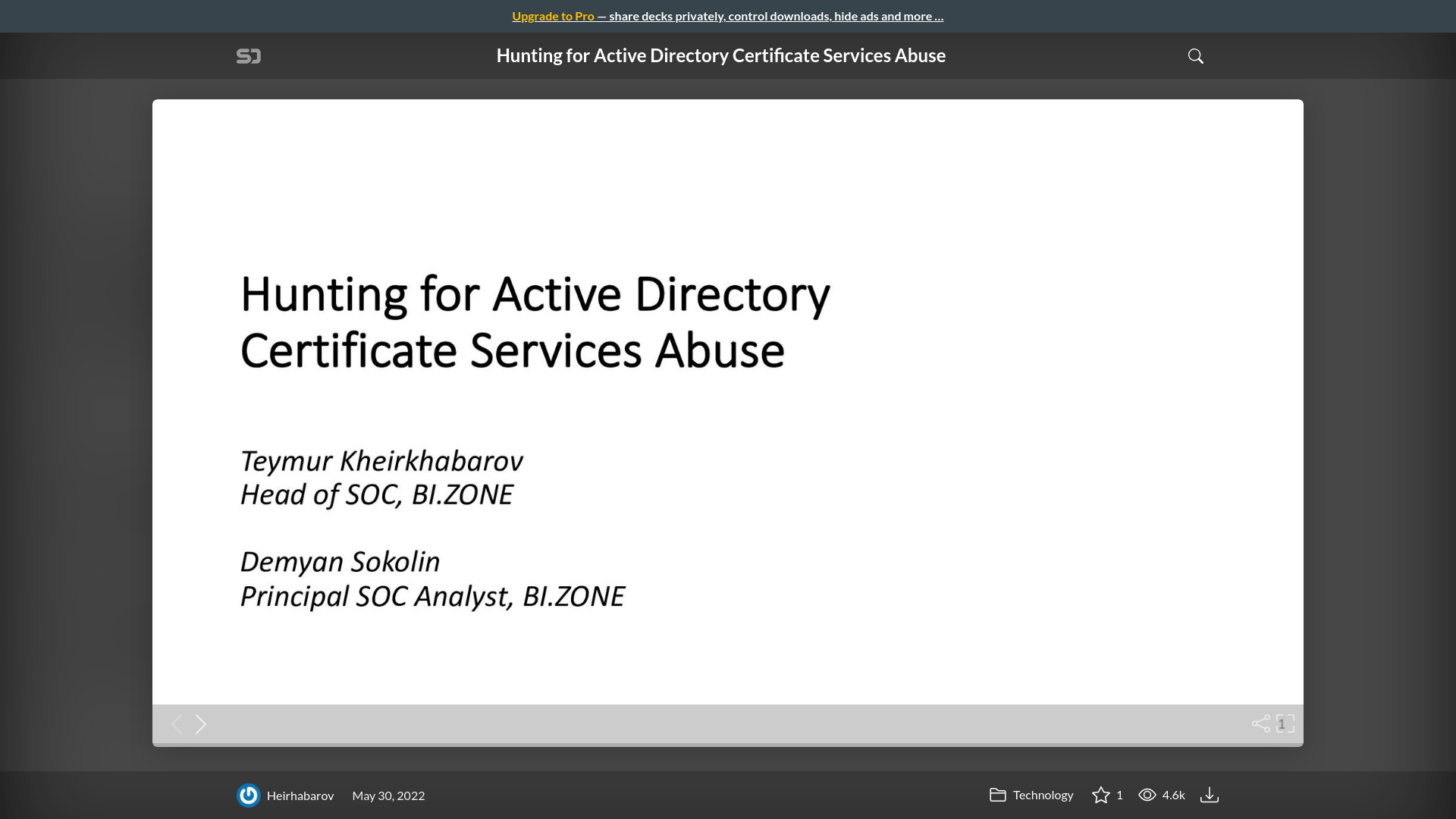
Hunting for Active Directory Certificate Services Abuse - Speaker Deck
https://speakerdeck.com/heirhabarov/hunting-for-active-directory-certificate-services-abuse