We Hacked Google A.I. for $50,000 - Lupin & Holmes
https://www.landh.tech/blog/20240304-google-hack-50000
GitHub Rolls Out Default Secret Scanning Push Protection for Public Repositories
https://thehackernews.com/2024/03/github-rolls-out-default-secret.html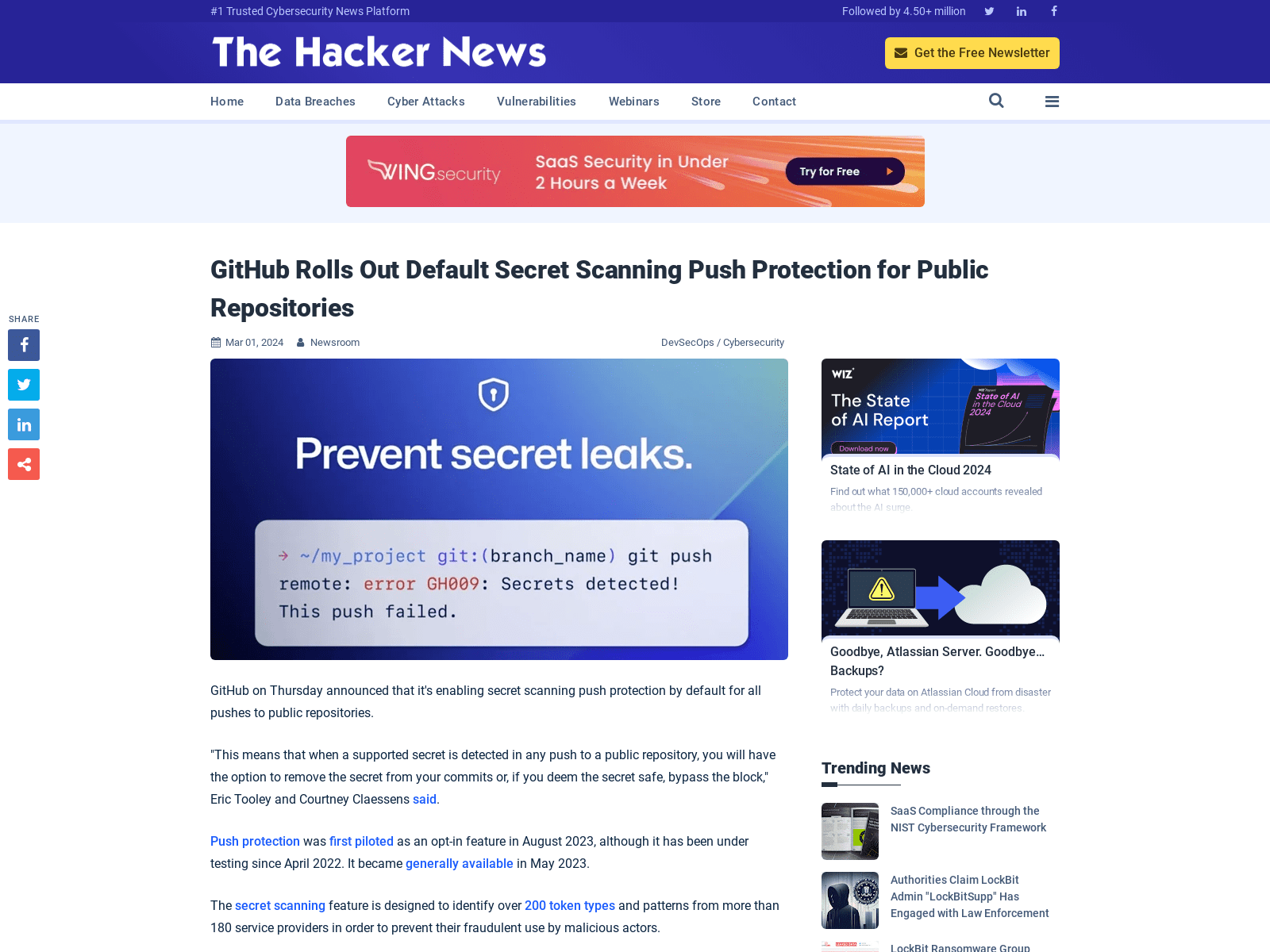
New Phishing Kit Leverages SMS, Voice Calls to Target Cryptocurrency Users
https://thehackernews.com/2024/03/new-phishing-kit-leverages-sms-voice.html
Whisky - Run Modern Windows Games on macOS
https://getwhisky.app
BlueHatIL - Call For Papers
https://www.microsoftrnd.co.il/bluehatil/conference/CFP
CISA cautions against using hacked Ivanti VPN gateways even after factory resets
https://www.bleepingcomputer.com/news/security/cisa-warns-against-using-hacked-ivanti-devices-even-after-factory-resets/
Germany takes down cybercrime market with over 180,000 users
https://www.bleepingcomputer.com/news/legal/germany-takes-down-largest-cybercrime-market-in-the-country-arrests-6/
GitHub - vvmdx/Apache-Solr-RCE_CVE-2023-50386_POC: Apache Solr Backup/Restore APIs RCE Poc (CVE-2023-50386)
https://github.com/vvmdx/Apache-Solr-RCE_CVE-2023-50386_POC
MalwareBazaar | SHA256 744b9dea0d8f7fcb84cab5065ca9c398709e4f8c926af90c28c5a4531e61f335 (CobaltStrike)
https://bazaar.abuse.ch/sample/744b9dea0d8f7fcb84cab5065ca9c398709e4f8c926af90c28c5a4531e61f335
TrustedSec Impede
http://impede.ai
カスタムGPTsを悪用した攻撃と対策について | 調査研究/ブログ | 三井物産セキュアディレクション株式会社
https://www.mbsd.jp/research/20240301/gpts/
SANS 2024 in Orlando, FL | Cyber Security Training
https://www.sans.org/u/1uvE
U.S. charges Iranian for hacks on defense orgs, offers $10M for info
https://www.bleepingcomputer.com/news/security/us-charges-iranian-for-hacks-on-defense-orgs-offers-10m-for-info/
ARM64 Reversing And Exploitation Part 1 – ARM Instruction Set + Simple Heap Overflow | 8kSec Blogs
https://8ksec.io/arm64-reversing-and-exploitation-part-1-arm-instruction-set-simple-heap-overflow/
We Hacked Google A.I. for $50,000 - Lupin & Holmes
https://www.landh.tech/blog/20240304-google-hack-50000/
How This Professional Hacker Built Two Cybersecurity Firms In His 30s - YouTube
https://youtu.be/ixEJYoCcC-Y?si=m-roSDcOKssKrsNO&t=1875
US charges Iranian with attacks against defense contractors • The Register
https://go.theregister.com/feed/www.theregister.com/2024/03/01/iranian_cyberattack_charges/
Fulton County, Security Experts Call LockBit’s Bluff – Krebs on Security
https://krebsonsecurity.com/2024/02/fulton-county-security-experts-call-lockbits-bluff/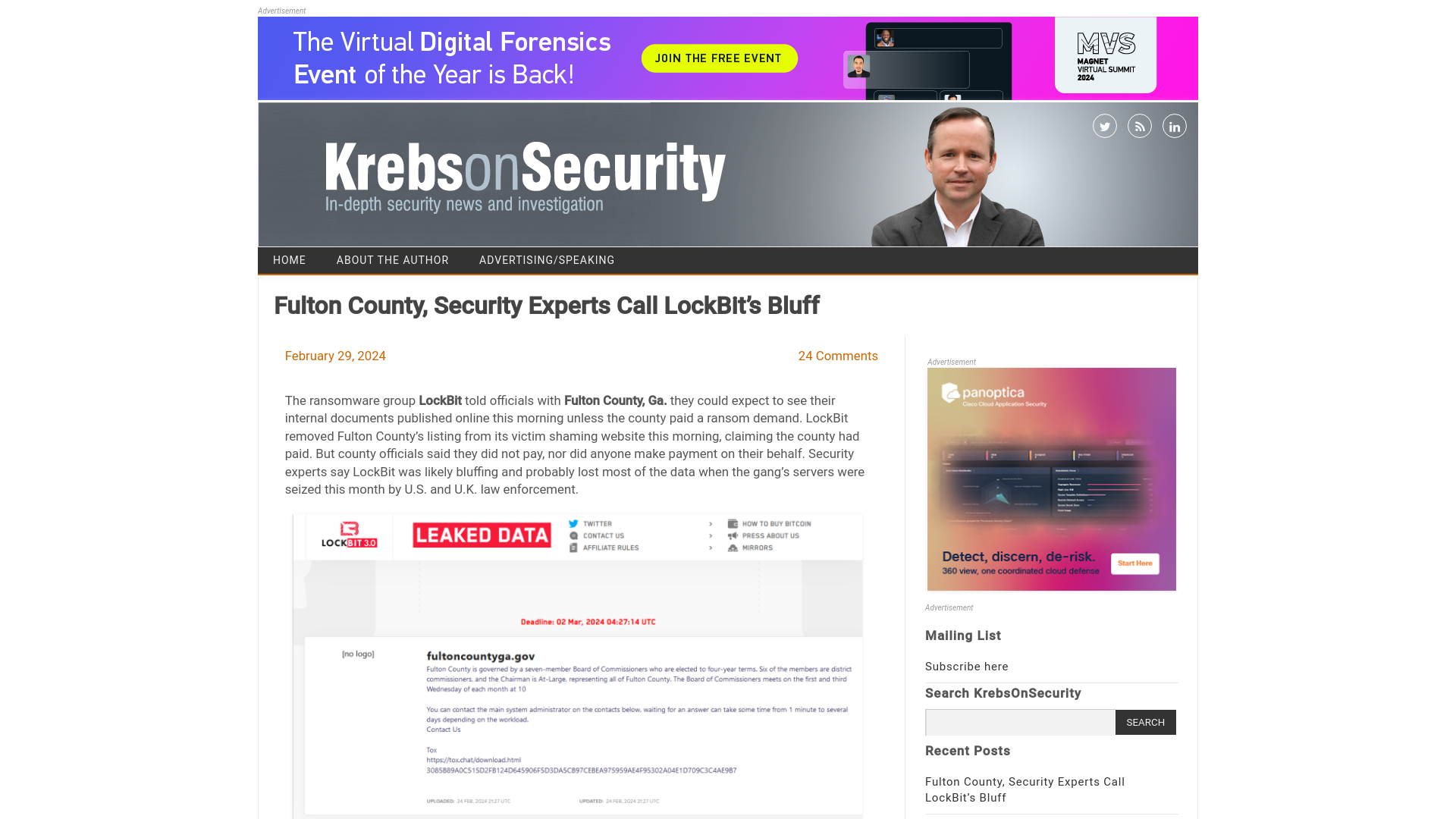
A reactionary take on memory safety - lcamtuf’s thing
https://lcamtuf.substack.com/p/a-reactionary-take-on-memory-safety
Industry Reactions to NIST Cybersecurity Framework 2.0: Feedback Friday - SecurityWeek
https://www.securityweek.com/industry-reactions-to-nist-cybersecurity-framework-2-0-feedback-friday/
Microsoft pulls Edge update causing 'Out of Memory' crashes
https://www.bleepingcomputer.com/news/microsoft/microsoft-pulls-edge-update-causing-out-of-memory-crashes/
CVE-2024-21762 Vulnerability Scanner for FortiGate… | Bishop Fox
https://bishopfox.com/blog/cve-2024-21762-vulnerability-scanner-for-fortigate-firewalls
ARM64 Reversing And Exploitation Part 2 – Use After Free | 8kSec Blogs
https://8ksec.io/arm64-reversing-and-exploitation-part-2-use-after-free/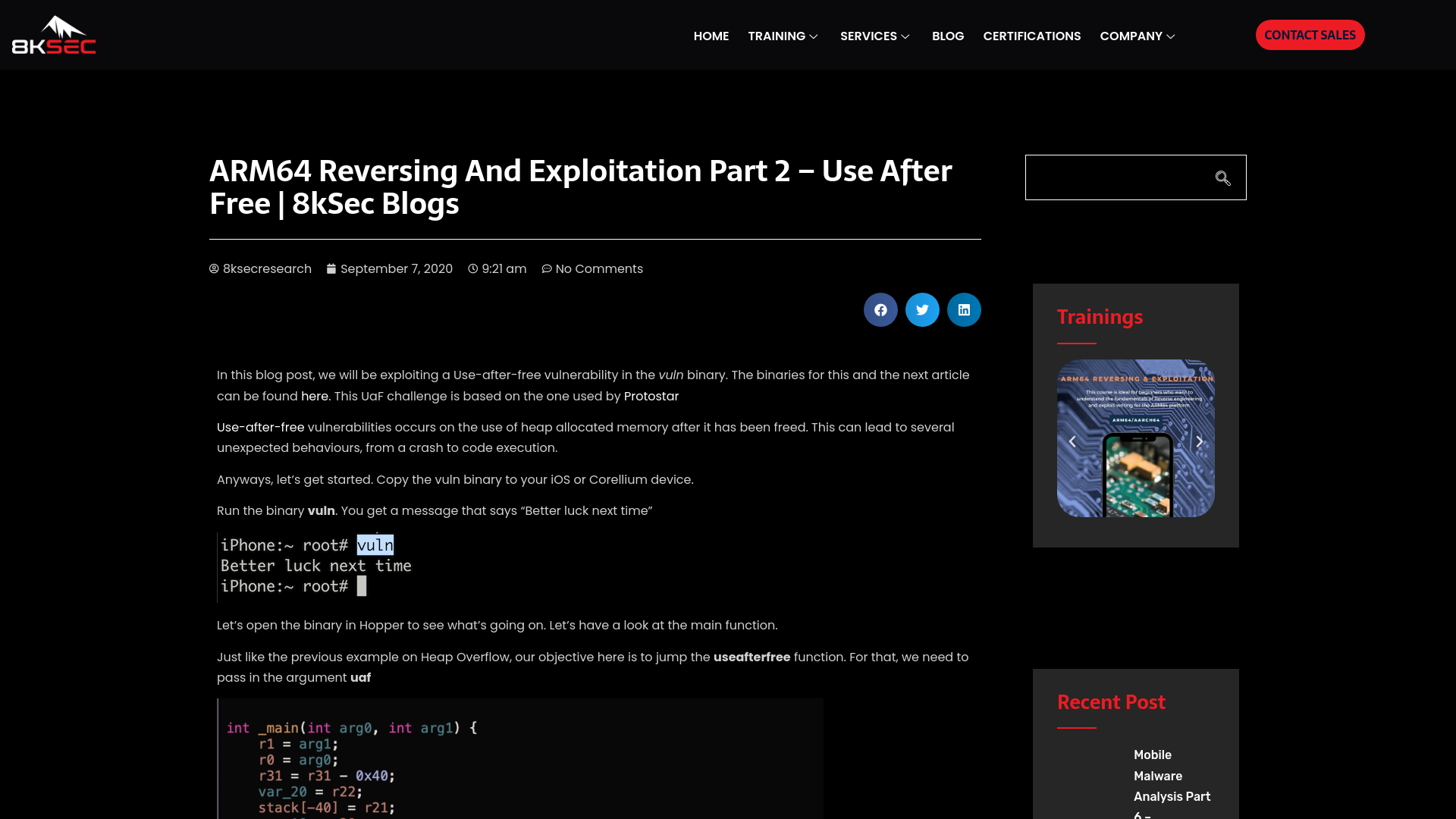
New BIFROSE Linux Malware Variant Using Deceptive VMware Domain for Evasion
https://thehackernews.com/2024/03/new-bifrose-linux-malware-variant-using.html