Clorox says cyberattack caused $49 million in expenses
https://www.bleepingcomputer.com/news/security/clorox-says-cyberattack-caused-49-million-in-expenses/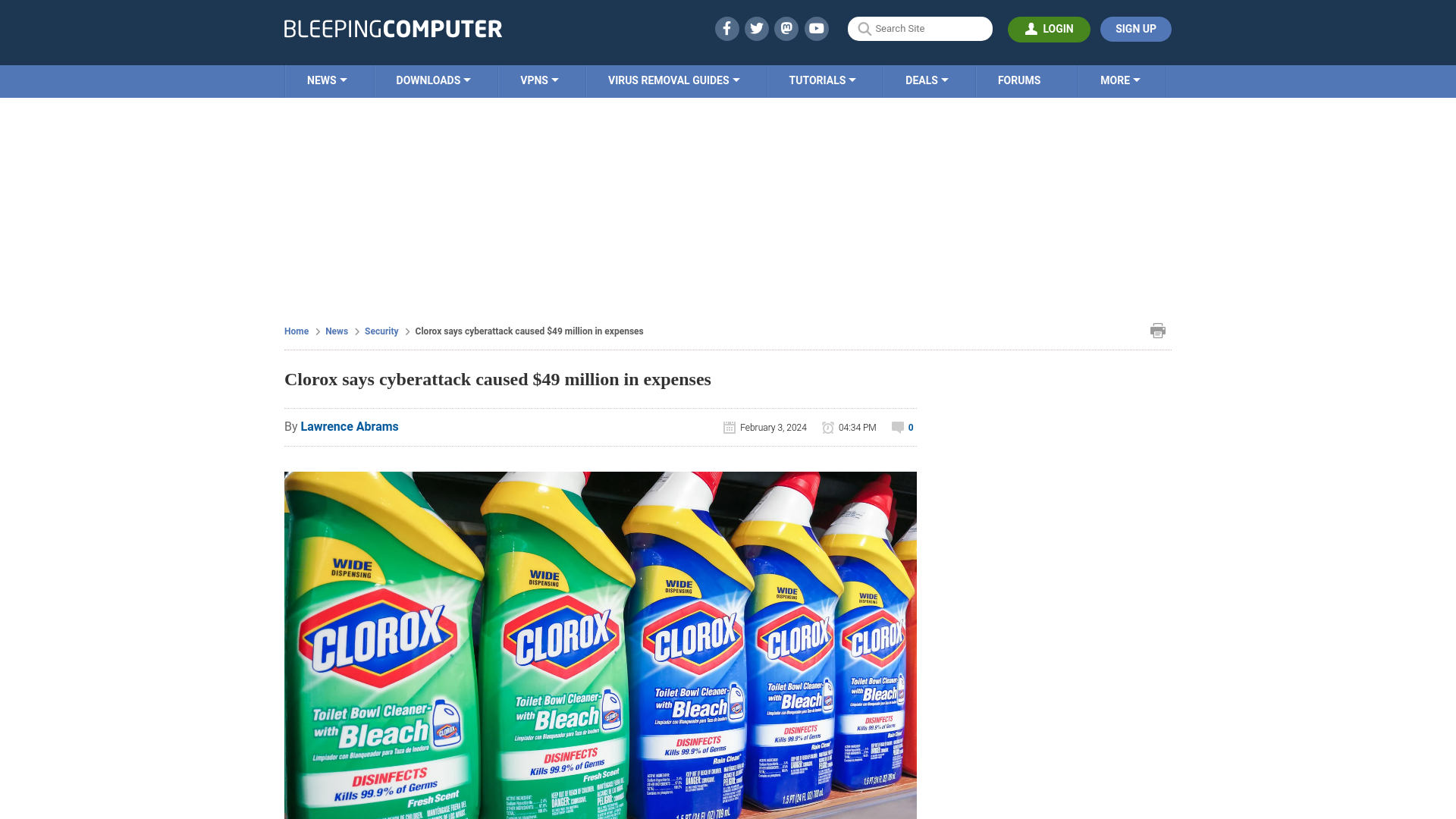
Nt Token Theft - Offensive Defence
https://offensivedefence.co.uk/posts/nt-token-theft/
Breaking Bitlocker - Bypassing the Windows Disk Encryption - YouTube
https://www.youtube.com/watch?v=wTl4vEednkQ
VajraSpy: A Patchwork of espionage apps
https://www.welivesecurity.com/en/eset-research/vajraspy-patchwork-espionage-apps/
SANS Dallas 2024 | Cyber Security Training
https://www.sans.org/u/1ukV
In-Memory-Only ELF Execution (Without tmpfs) Mrs Quis Will Think of a Better Title
https://magisterquis.github.io/2018/03/31/in-memory-only-elf-execution.html
Leaky Vessels flaws allow hackers to escape Docker, runc containers
https://www.bleepingcomputer.com/news/security/leaky-vessels-flaws-allow-hackers-to-escape-docker-runc-containers/
AnyDesk Breach 2024: Dark Web Sale of 18,317 Credentials
https://securityonline.info/anydesk-breach-2024-dark-web-sale-of-18317-credentials/
Microsoft is bringing the Linux sudo command to Windows Server
https://www.bleepingcomputer.com/news/microsoft/microsoft-is-bringing-the-linux-sudo-command-to-windows-server/
Hunting M365 Invaders: Blue Team's Guide to Initial Access Vectors | Splunk
https://www.splunk.com/en_us/blog/security/hunting-m365-invaders-blue-team-s-guide-to-initial-access-vectors.html
HackerOne | Report #815085 - Account creation with invalid email addresses / email is accepting % and %0d%0a line termination chars | HackerOne
https://hackerone.com/reports/815085