.:: Phrack Magazine ::.
http://phrack.org/
CISA orders federal agencies to disconnect Ivanti VPN appliances by Saturday
https://www.bleepingcomputer.com/news/security/cisa-orders-federal-agencies-to-disconnect-ivanti-vpn-appliances-by-saturday/
Cloudflare hacked using auth tokens stolen in Okta attack
https://www.bleepingcomputer.com/news/security/cloudflare-hacked-using-auth-tokens-stolen-in-okta-attack/
FBI disrupts Chinese botnet by wiping malware from infected routers
https://www.bleepingcomputer.com/news/security/fbi-disrupts-chinese-botnet-by-wiping-malware-from-infected-routers/
GitHub - google/oss-fuzz-gen: LLM powered fuzzing via OSS-Fuzz.
https://github.com/google/oss-fuzz-gen
Exposed Docker APIs Under Attack in 'Commando Cat' Cryptojacking Campaign
https://thehackernews.com/2024/02/exposed-docker-apis-under-attack-in.html
Cutting Edge, Part 2: Investigating Ivanti Connect Secure VPN Zero-Day Exploitation | Mandiant
https://www.mandiant.com/resources/blog/investigating-ivanti-zero-day-exploitation
CISA Warns of Active Exploitation of Critical Flaws in Apple iOS and macOS
https://thehackernews.com/2024/02/cisa-warns-of-active-exploitation-of.html
Special Offer for Asia Pacific Students | SANS Online Training
https://www.sans.org/u/1usZ
2024年サイバーセキュリティ月間 - NISC
https://security-portal.nisc.go.jp/cybersecuritymonth/2024/
Outlook Vulnerability Discovery and New Ways to Leak NTLM Hashes
https://www.varonis.com/blog/outlook-vulnerability-new-ways-to-leak-ntlm-hashes
Multiple malware used in attacks exploiting Ivanti VPN flaws
https://securityaffairs.com/158440/apt/malware-ivanti-vpn-flaws-attacks.html
CVEMap: Open-source tool to query, browse and search CVEs - Help Net Security
https://www.helpnetsecurity.com/2024/02/01/cvemap-query-browse-search-cve/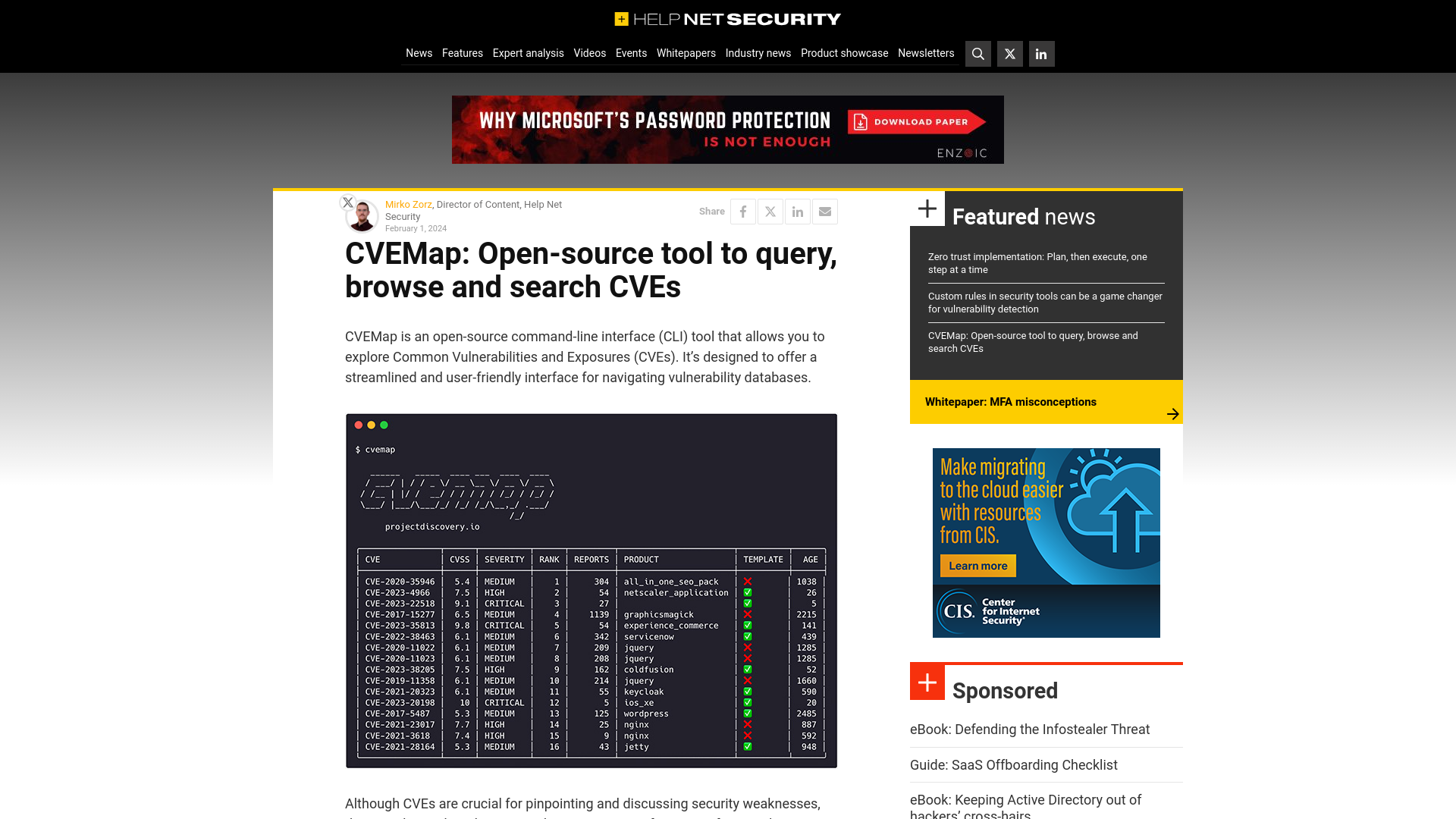
Arrests in $400M SIM-Swap Tied to Heist at FTX? – Krebs on Security
https://krebsonsecurity.com/2024/02/arrests-in-400m-sim-swap-tied-to-heist-at-ftx/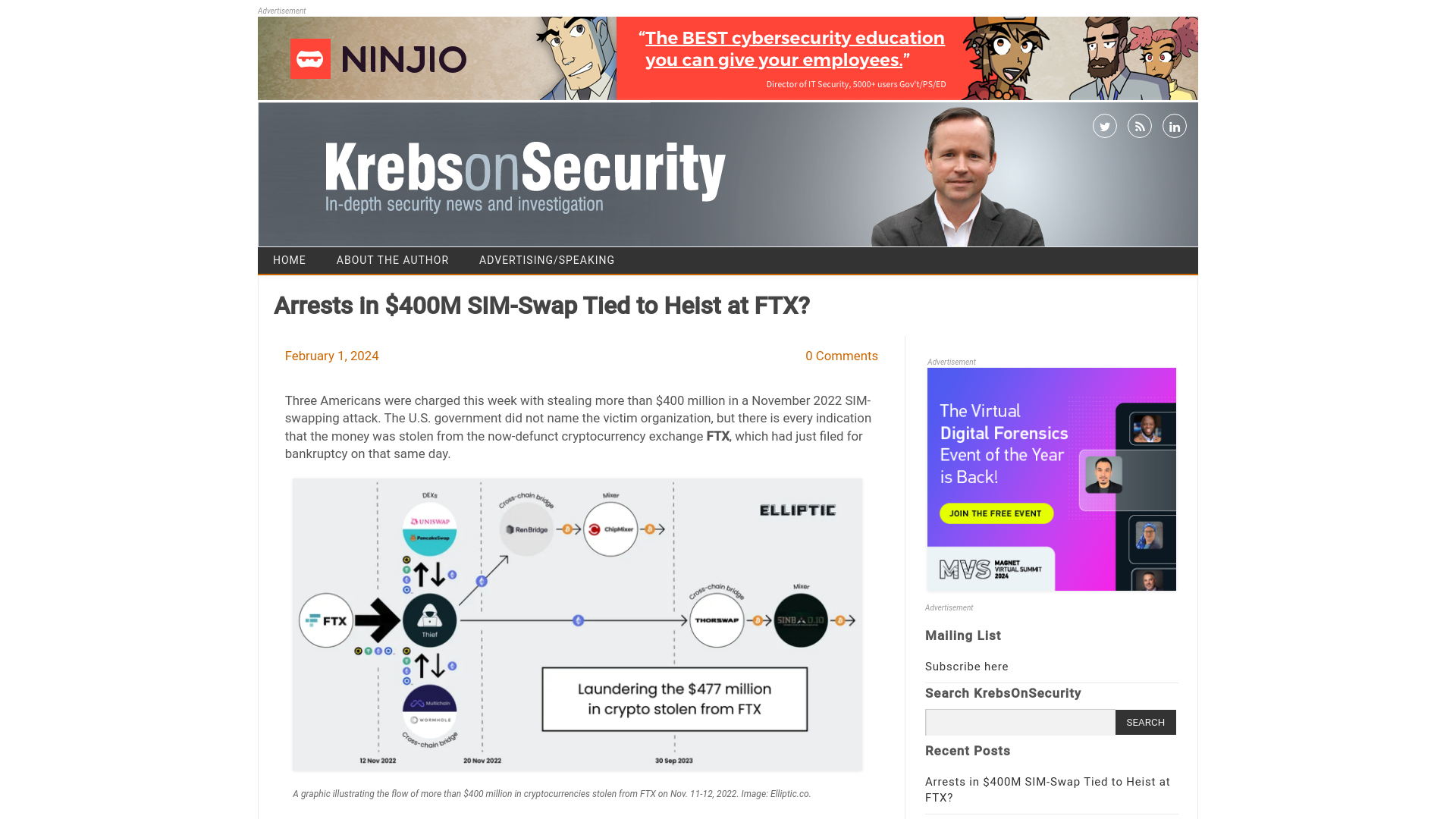
Jumpserver Preauth RCE Exploit Chain
https://sites.google.com/site/zhiniangpeng/blogs/Jumpserver
A Practical Guide to PrintNightmare in 2024 | itm4n's blog
https://itm4n.github.io/printnightmare-exploitation/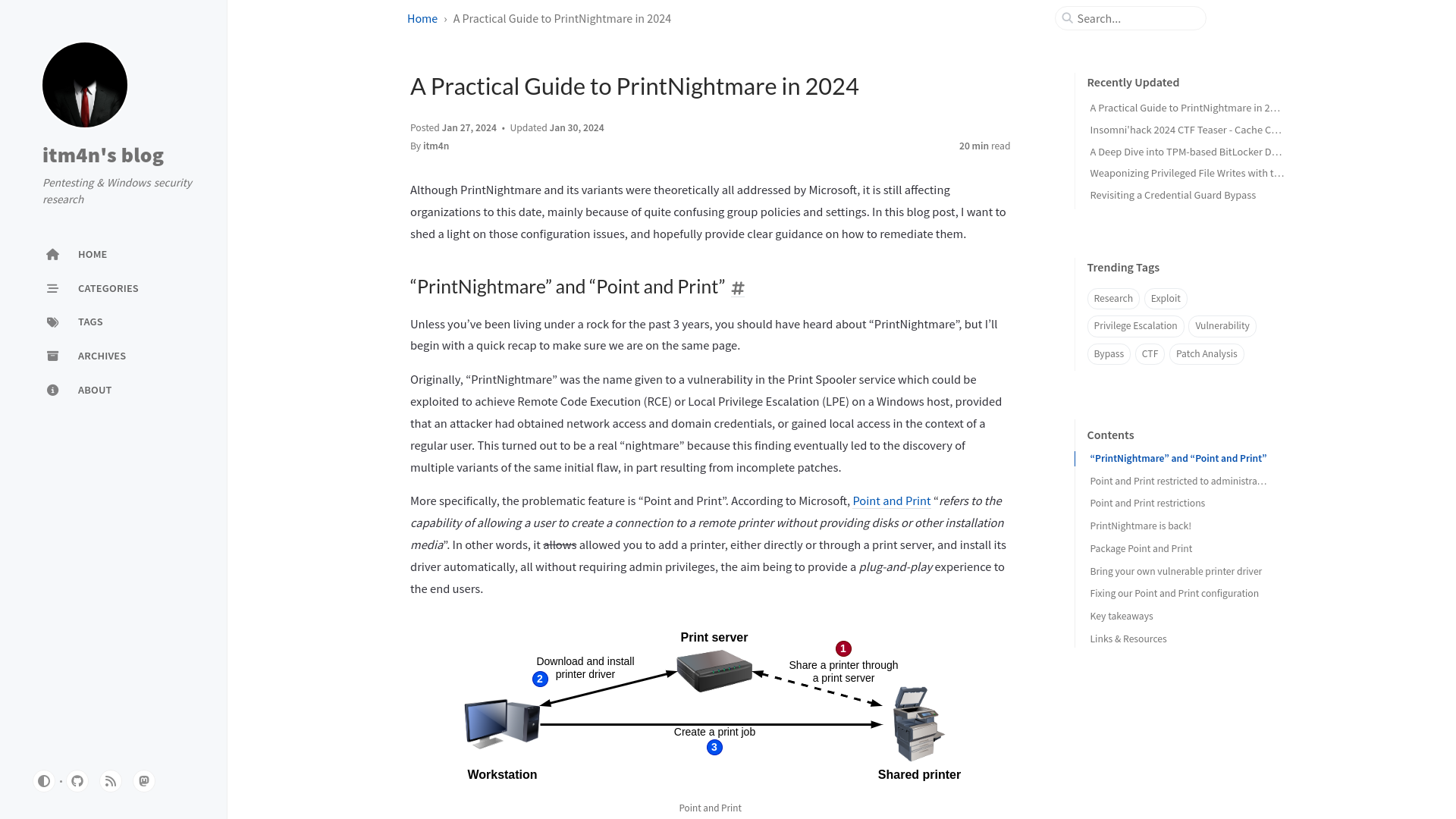
How to Build a Password Cracker
https://www.sevnx.com/blog/post/building-a-password-cracker
US Says It Disrupted a China Cyber Threat, but Warns Hackers Could Still Wreak Havoc for Americans - SecurityWeek
https://www.securityweek.com/us-says-it-disrupted-a-china-cyber-threat-but-warns-hackers-could-still-wreak-havoc-for-americans/
FritzFrog Returns with Log4Shell and PwnKit, Spreading Malware Inside Your Network
https://thehackernews.com/2024/02/fritzfrog-returns-with-log4shell-and.html
Evolution of UNC4990: Uncovering USB Malware's Hidden Depths | Mandiant
https://www.mandiant.com/resources/blog/unc4990-evolution-usb-malware
How to protect Evilginx using Cloudflare and HTML Obfuscation
https://www.jackphilipbutton.com/post/how-to-protect-evilginx-using-cloudflare-and-html-obfuscation
U.S. Feds Shut Down China-Linked "KV-Botnet" Targeting SOHO Routers
https://thehackernews.com/2024/02/us-feds-shut-down-china-linked-kv.html
Nitrogen shelling malware from hacked sites | Malwarebytes
https://www.malwarebytes.com/blog/threat-intelligence/2024/01/nitrogen-shelling-malware-from-hacked-sites
CISA Sets 48-hour Deadline for Removal of Insecure Ivanti Products - SecurityWeek
https://www.securityweek.com/cisa-sets-48-hour-deadline-for-removal-of-insecure-ivanti-products/
Binary Ninja - Reverse Engineering a Cobalt Strike Dropper With Binary Ninja
https://binary.ninja/2022/07/22/reverse-engineering-cobalt-strike.html
AzAdvertizer
https://www.azadvertizer.net/
First look: Windows 11 is getting native macOS or Linux-like Sudo command
https://www.windowslatest.com/2024/02/01/first-look-windows-11-is-getting-native-macos-or-linux-like-sudo-command/
Security Fest - IT Security Conference May 30-31 2024, Gothenburg, Sweden
https://securityfest.com/
New Windows Event Log zero-day flaw gets unofficial patches
https://www.bleepingcomputer.com/news/microsoft/new-windows-event-log-zero-day-flaw-gets-unofficial-patches/
Hackers push USB malware payloads via news, media hosting sites
https://www.bleepingcomputer.com/news/security/hackers-push-usb-malware-payloads-via-news-media-hosting-sites/
Qualys TRU Discovers Important Vulnerabilities in GNU C Library’s syslog() | Qualys Security Blog
https://blog.qualys.com/vulnerabilities-threat-research/2024/01/30/qualys-tru-discovers-important-vulnerabilities-in-gnu-c-librarys-syslog
Google shares fix for Pixel phones hit by bad system update
https://www.bleepingcomputer.com/news/mobile/google-shares-fix-for-pixel-phones-hit-by-bad-system-update/
HeadCrab 2.0 Goes Fileless, Targeting Redis Servers for Crypto Mining
https://thehackernews.com/2024/02/headcrab-20-goes-fileless-targeting.html
PurpleFox malware infects thousands of computers in Ukraine
https://www.bleepingcomputer.com/news/security/purplefox-malware-infected-thousands-of-systems-in-ukraine/
Creating FLIRT Signatures in IDA Pro for CTF's, Malware, etc... - YouTube
https://www.youtube.com/watch?v=TqIUsLQ-HjE
Let's write a PDF file - Speaker Deck
https://speakerdeck.com/ange/lets-write-a-pdf-file
CVE-2024-21633 - MobSF Remote code execution | QU35T blog
https://www.qu35t.pw/posts/2024-21633-mobsf-rce/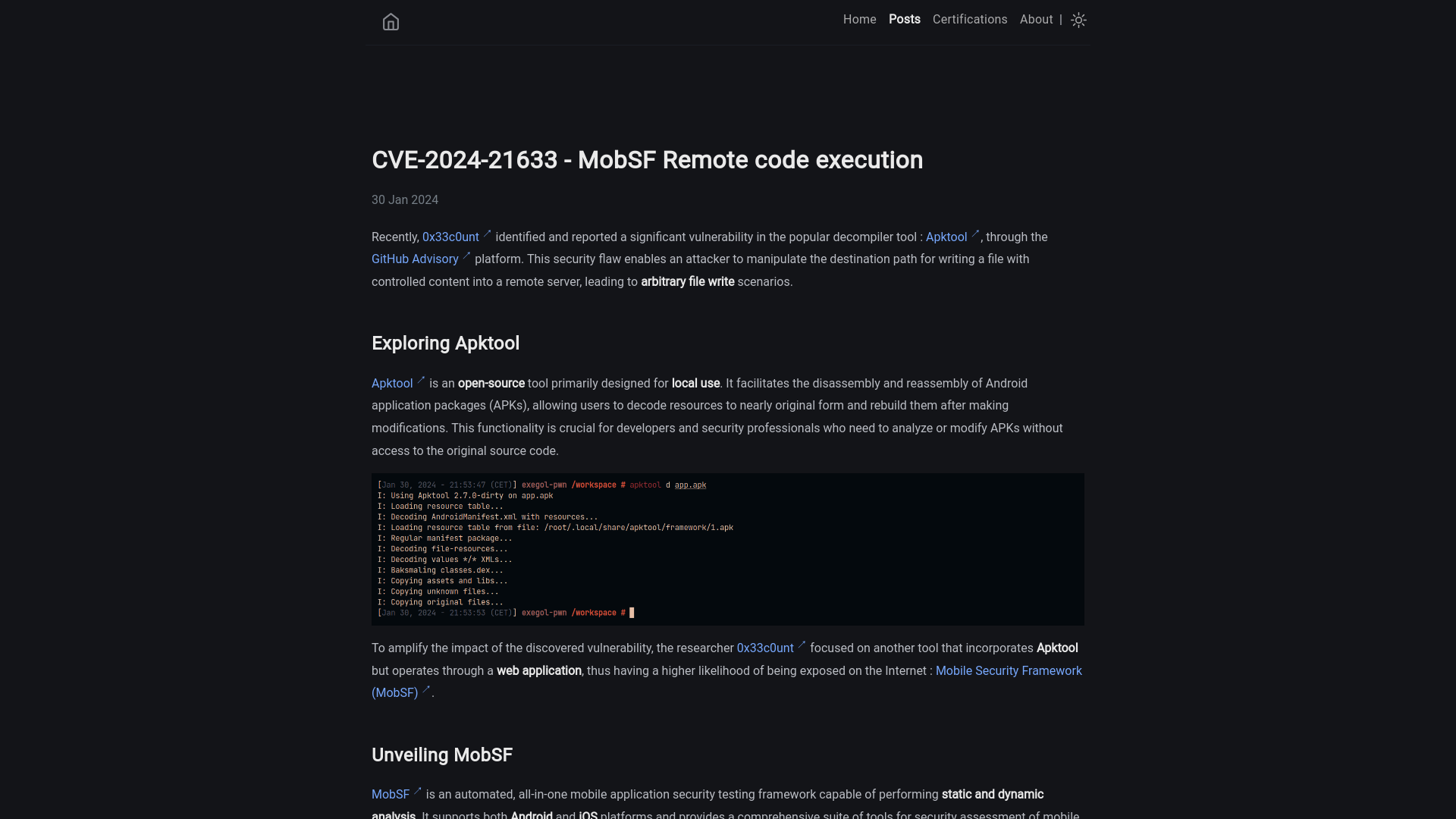
BugBounty.jp
http://BugBounty.jp
More Android apps riddled with malware spotted on Google Play
https://www.bleepingcomputer.com/news/security/more-android-apps-riddled-with-malware-spotted-on-google-play/
We build X.509 chains so you don’t have to | Trail of Bits Blog
https://blog.trailofbits.com/2024/01/25/we-build-x-509-chains-so-you-dont-have-to/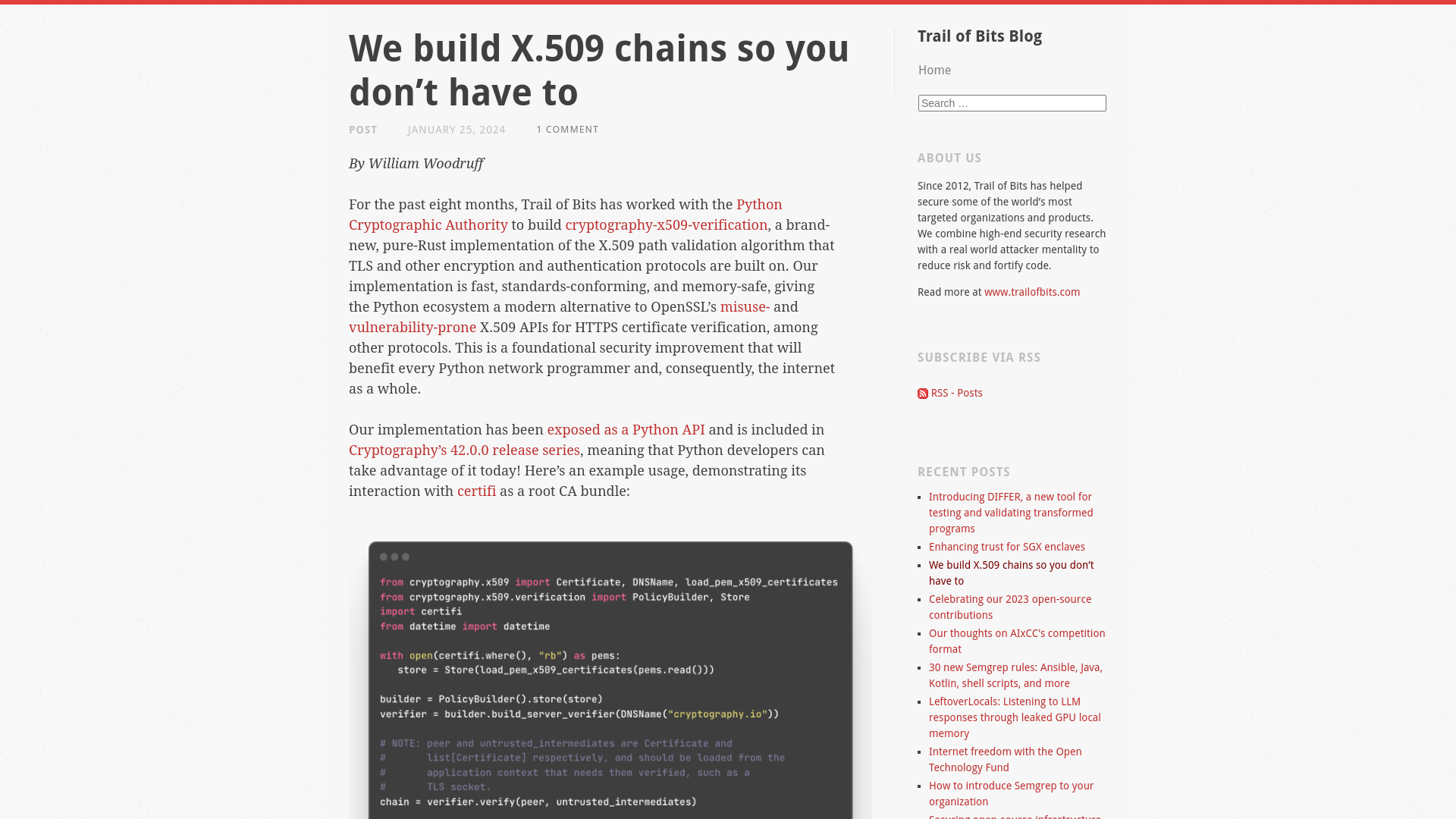
Chess.com - Play Chess Online - Free Games
http://chess.com