CVE-2023-40547 - avoid incorrectly trusting HTTP headers · rhboot/shim@0226b56 · GitHub
https://github.com/rhboot/shim/commit/0226b56513b2b8bd5fd281bce77c40c9bf07c66d
Tesla hacked, 24 zero-days demoed at Pwn2Own Automotive 2024
https://www.bleepingcomputer.com/news/security/tesla-hacked-24-zero-days-demoed-at-pwn2own-automotive-2024/
MalwareBazaar | SHA256 a95fe0e3b0cb3c0a172eef317d1b213f8572156dc44026f470add87e563bb3d1 (NetSupport)
https://bazaar.abuse.ch/sample/a95fe0e3b0cb3c0a172eef317d1b213f8572156dc44026f470add87e563bb3d1/
Google Pixel phones unusable after January 2024 system update
https://www.bleepingcomputer.com/news/google/google-pixel-phones-unusable-after-january-2024-system-update/
Patch Your GoAnywhere MFT Immediately - Critical Flaw Lets Anyone Be Admin
https://thehackernews.com/2024/01/patch-your-goanywhere-mft-immediately.html
The Endless Struggle Against APT10: Insights from LODEINFO v0.6.6 - v0.7.3 Analysis - Researcher Blog - ITOCHU Cyber & Intelligence Inc.
https://blog-en.itochuci.co.jp/entry/2024/01/24/134100
Google Kubernetes Misconfig Lets Any Gmail Account Control Your Clusters
https://thehackernews.com/2024/01/google-kubernetes-misconfig-lets-any.html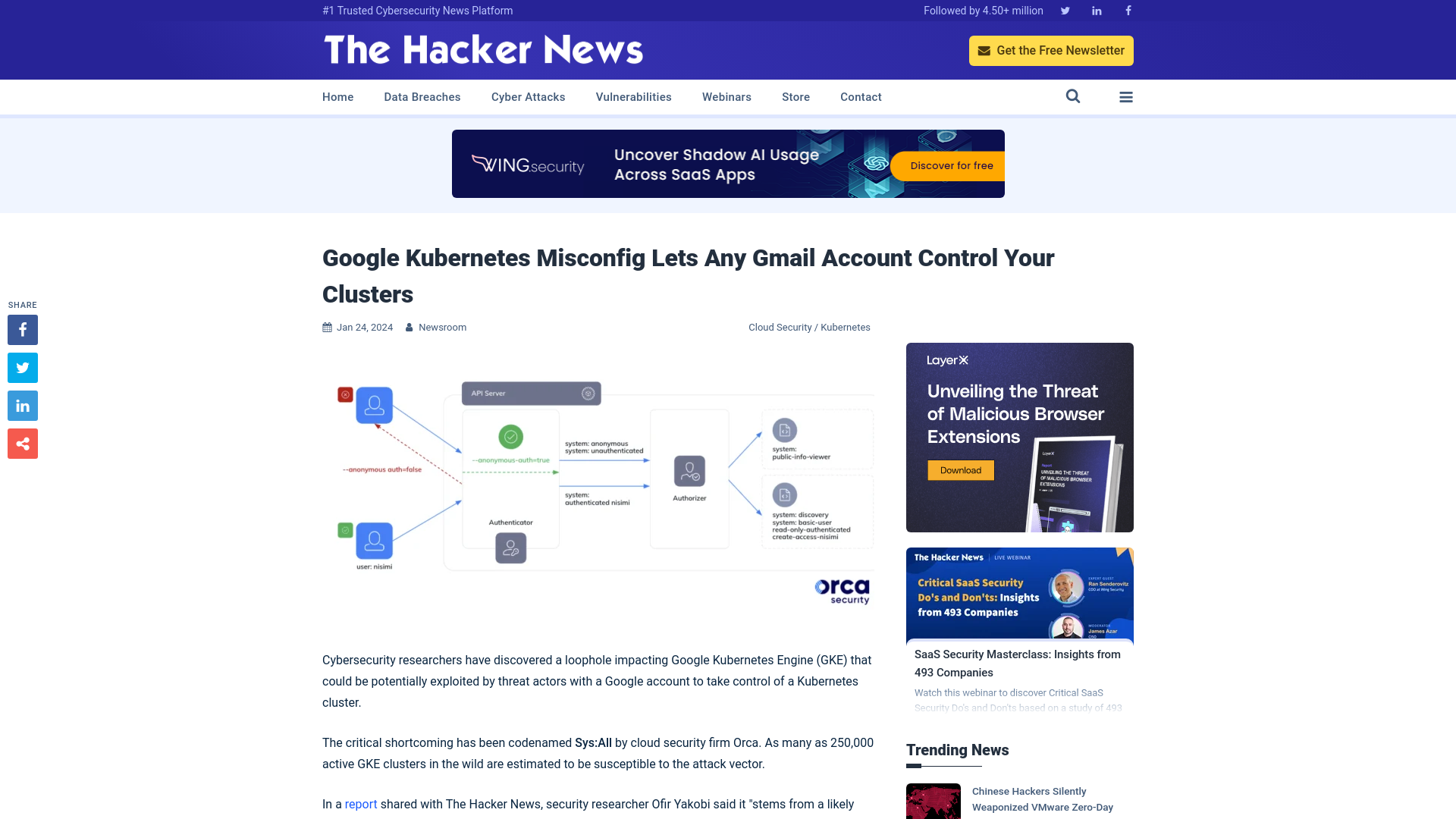
Over 5,300 GitLab servers exposed to zero-click account takeover attacks
https://www.bleepingcomputer.com/news/security/over-5-300-gitlab-servers-exposed-to-zero-click-account-takeover-attacks/
HPE: Russian hackers breached its security team’s email accounts
https://www.bleepingcomputer.com/news/security/hpe-russian-hackers-breached-its-security-teams-email-accounts/
Kasseika Ransomware Using BYOVD Trick to Disarms Security Pre-Encryption
https://thehackernews.com/2024/01/kasseika-ransomware-using-byovd-trick.html
PE relocation Table | MalwareID Unpacking Guide
http://malwareid.in/unpack/unpacking-basics/pe-relocation-table
VexTrio TDS: Inside a massive 70,000-domain cybercrime operation
https://www.bleepingcomputer.com/news/security/vextrio-tds-inside-a-massive-70-000-domain-cybercrime-operation/
Victory! Ring Announces It Will No Longer Facilitate Police Requests for Footage from Users | Electronic Frontier Foundation
https://www.eff.org/deeplinks/2024/01/ring-announces-it-will-no-longer-facilitate-police-requests-footage-users
ScarCruft | Attackers Gather Strategic Intelligence and Target Cybersecurity Professionals - SentinelOne
https://www.sentinelone.com/labs/a-glimpse-into-future-scarcruft-campaigns-attackers-gather-strategic-intelligence-and-target-cybersecurity-professionals/
VirusTotal - File - 710191b05ec3faf6012bad12e6d66a638301da9c6f0b6a14413b716023c1fcfb
https://www.virustotal.com/gui/file/710191b05ec3faf6012bad12e6d66a638301da9c6f0b6a14413b716023c1fcfb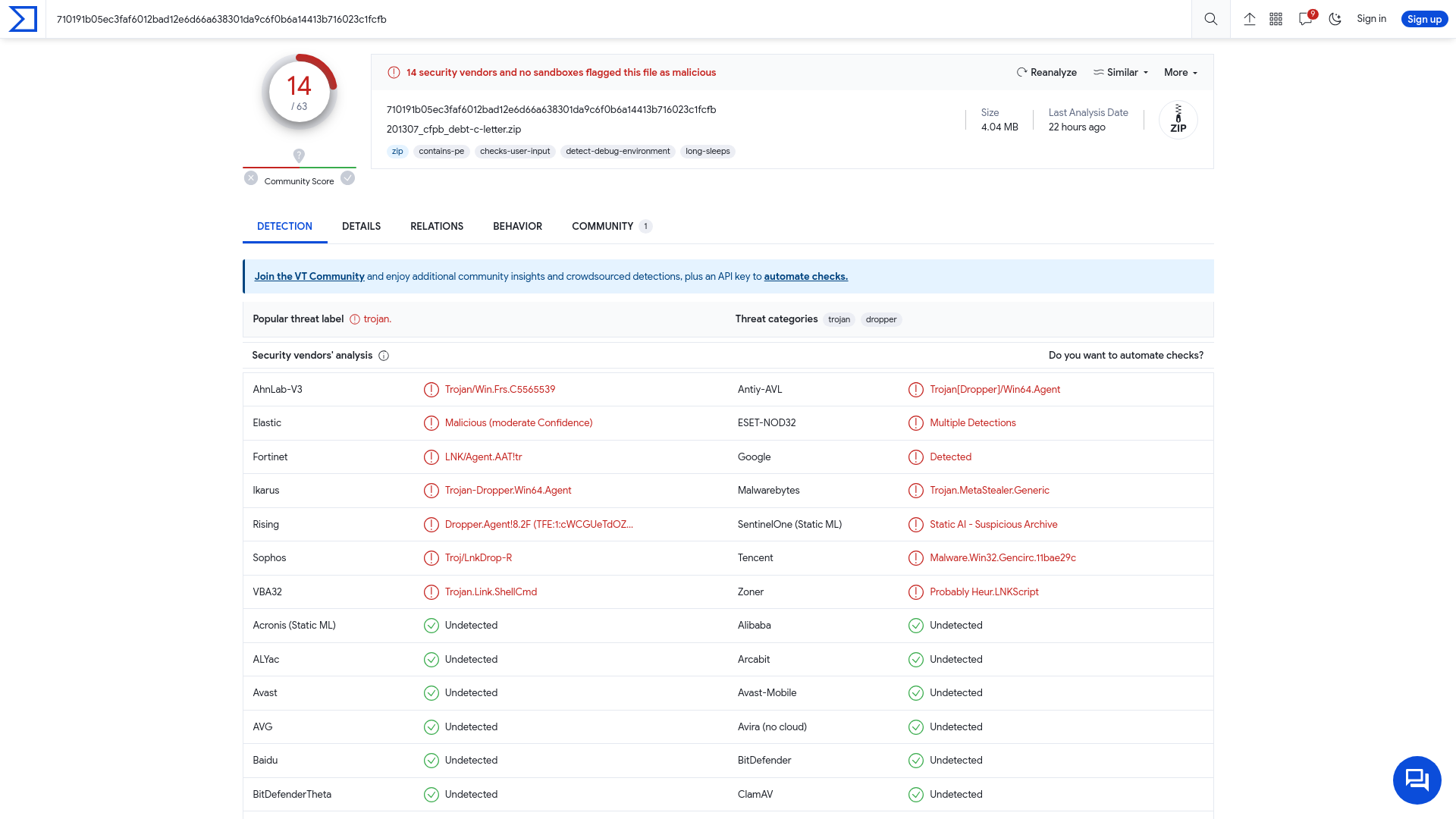
U.S., U.K., Australia Sanction Russian REvil Hacker Behind Medibank Breach
https://thehackernews.com/2024/01/us-uk-australia-sanction-russian-revil.html
SANS Las Vegas 2024 | Cyber Security Training
https://www.sans.org/u/1ukQ
Webinar - 2023 Major Conference Roundup - YouTube
https://www.youtube.com/watch?v=UXC0G7rGJpg
Akira ransomware attack on Tietoevry disrupted the services of many Swedish organizations
https://securityaffairs.com/158031/cyber-crime/tietoevry-akira-ransomware-attack.html
Detailed Analysis of DarkGate; Investigating new top-trend backdoor malware | by S2W | S2W BLOG | Jan, 2024 | Medium
https://medium.com/s2wblog/detailed-analysis-of-darkgate-investigating-new-top-trend-backdoor-malware-0545ecf5f606
The near-term impact of AI on the cyber threat - NCSC.GOV.UK
https://www.ncsc.gov.uk/report/impact-of-ai-on-cyber-threat
Enter The Gates: An Analysis of the DarkGate AutoIt Loader | Splunk
https://www.splunk.com/en_us/blog/security/enter-the-gates-an-analysis-of-the-darkgate-autoit-loader.html
Hiding payloads in Java source code strings | PortSwigger Research
https://portswigger.net/research/hiding-payloads-in-java-source-code-strings
GitHub - VNCERT-CC/CVE-2023-22527-confluence: [Confluence] CVE-2023-22527 realworld poc
https://github.com/VNCERT-CC/CVE-2023-22527-confluence![GitHub - VNCERT-CC/CVE-2023-22527-confluence: [Confluence] CVE-2023-22527 realworld poc](/image/screenshot/36d8365485e4b013fe95ff39b9e05b16.png)
分析官と攻撃者の解析回避を巡る終わりなき戦い: LODEINFO v0.6.6 - v0.7.3 の解析から - ITOCHU Cyber & Intelligence Inc.
https://blog.itochuci.co.jp/entry/2024/01/24/134047
The Unknown Risks of The Software Supply Chain: A Deep-Dive
https://thehackernews.com/2024/01/the-unknown-risks-of-software-supply.html
Exploiting 0-click Android Bluetooth vulnerability to inject keystrokes without pairing - Mobile Hacker
https://www.mobile-hacker.com/2024/01/23/exploiting-0-click-android-bluetooth-vulnerability-to-inject-keystrokes-without-pairing/