Project Zero: Analyzing a Modern In-the-wild Android Exploit
https://googleprojectzero.blogspot.com/2023/09/analyzing-modern-in-wild-android-exploit.html
Fake WinRAR proof-of-concept exploit drops VenomRAT malware
https://www.bleepingcomputer.com/news/security/fake-winrar-proof-of-concept-exploit-drops-venomrat-malware/
GitHub - lem0nSec/ShellGhost: A memory-based evasion technique which makes shellcode invisible from process start to end.
https://github.com/lem0nSec/ShellGhost
Voting machine companies use cybersecurity stress tests to take on conspiracy theorists | CNN Politics
https://www.cnn.com/2023/09/20/politics/voting-machines-cybersecurity-2024/index.html
Fresh Wave of Malicious npm Packages Threaten Kubernetes Configs and SSH Keys
https://thehackernews.com/2023/09/fresh-wave-of-malicious-npm-packages.html
GitLab Releases Urgent Security Patches for Critical Vulnerability
https://thehackernews.com/2023/09/gitlab-releases-urgent-security-patches.html
Analysis Nepal.rtf (MD5: 790FE61107AB269E5BAC5A605F3C4DF3) Malicious activity - Interactive analysis ANY.RUN
https://app.any.run/tasks/ca41f860-0e0c-4489-b59c-7b62ca089061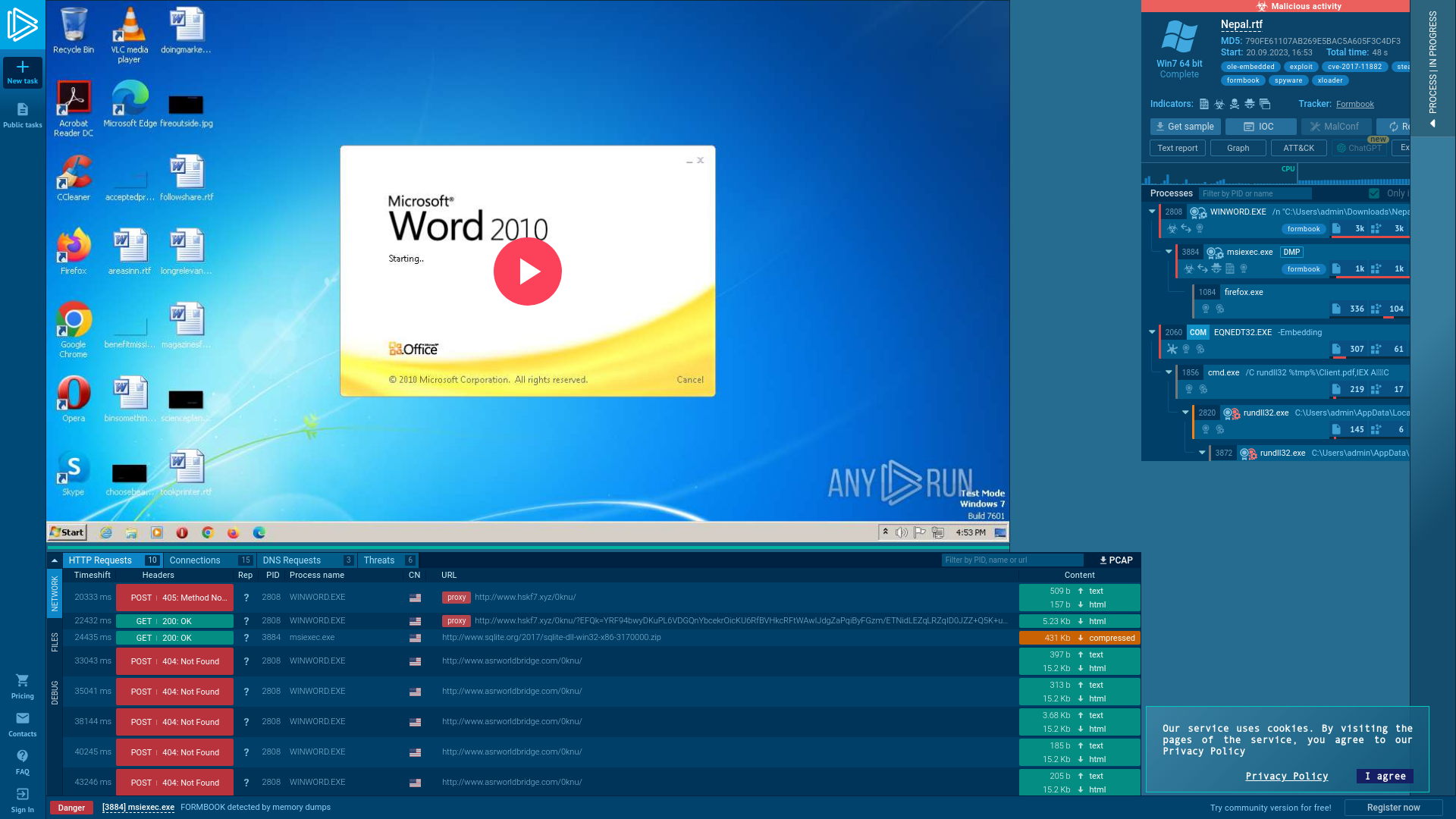
Signal Messenger Introduces PQXDH Quantum-Resistant Encryption
https://thehackernews.com/2023/09/signal-messenger-introduces-pqxdh.html
Finnish Authorities Dismantle Notorious PIILOPUOTI Dark Web Drug Marketplace
https://thehackernews.com/2023/09/finnish-authorities-dismantle-notorious.html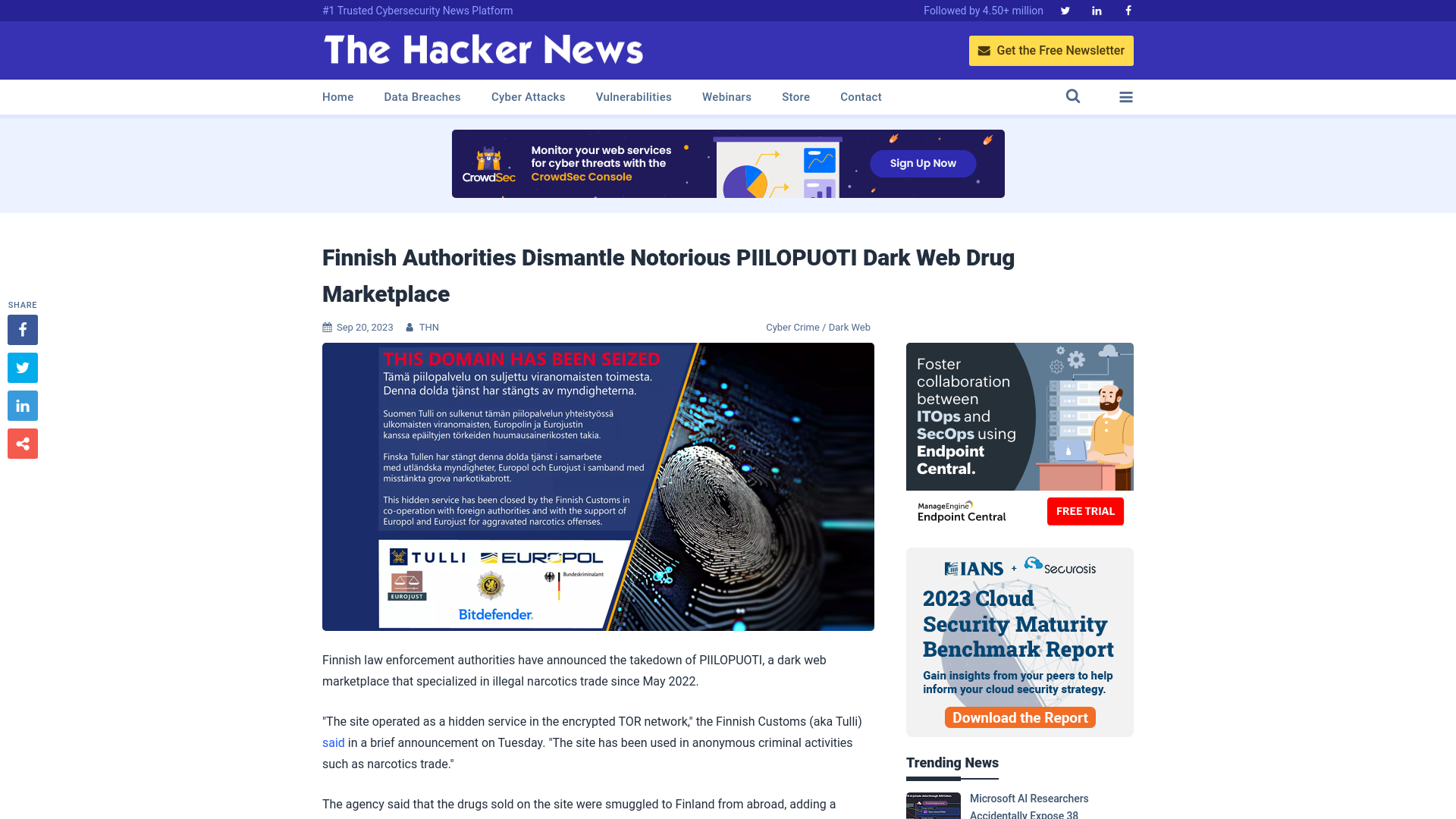
TransUnion denies it was hacked, links leaked data to 3rd party
https://www.bleepingcomputer.com/news/security/transunion-denies-it-was-hacked-links-leaked-data-to-3rd-party/
Critical Security Flaws Exposed in Nagios XI Network Monitoring Software
https://thehackernews.com/2023/09/critical-security-flaws-exposed-in.html
Trend Micro Releases Urgent Fix for Actively Exploited Critical Security Vulnerability
https://thehackernews.com/2023/09/trend-micro-releases-urgent-fix-for.html
T-Mobile app glitch let users see other people's account info
https://www.bleepingcomputer.com/news/security/t-mobile-app-glitch-let-users-see-other-peoples-account-info/
Signal adds quantum-resistant encryption to its E2EE messaging protocol
https://www.bleepingcomputer.com/news/security/signal-adds-quantum-resistant-encryption-to-its-e2ee-messaging-protocol/
Intel Launches New Attestation Service as Part of Trust Authority Portfolio - SecurityWeek
https://www.securityweek.com/intel-launches-new-attestation-service-as-part-of-trust-authority-portfolio/
The dark web drug marketplace PIILOPUOTI dismantled by Finnish Customs
https://securityaffairs.com/151131/deep-web/finnish-police-seized-piilopuoti-marketplace.html
GraphRunner: A Post-Exploitation Toolset for M365 – Beau Bullock & Steve Borosh – Wild West Hackin' Fest
https://wildwesthackinfest.com/event/graphrunner-a-post-exploitation-toolset-for-m365/
Release YARA v4.4.0-rc1 · VirusTotal/yara · GitHub
https://github.com/VirusTotal/yara/releases/tag/v4.4.0
SANS Digital Forensics and Incident Response - YouTube
https://youtube.com/@SANSForensics?feature=shared
UK Minister Warns Meta Over End-to-End Encryption - SecurityWeek
https://www.securityweek.com/uk-minister-warns-meta-over-end-to-end-encryption/
Remote Code Execution in Tutanota Desktop due to Code Flaw | Sonar
https://www.sonarsource.com/blog/remote-code-execution-in-tutanota-desktop-due-to-code-flaw/
CrowdStrike Achieves 100% in MITRE Engenuity ATT&CK Evaluations: Enterprise
https://www.crowdstrike.com/blog/crowdstrike-achieves-100-percent-mitre-engenuity-attack-enterprise-evaluation/
Trend Micro addresses actively exploited zero-day in Apex One
https://securityaffairs.com/151095/hacking/trend-micro-apex-one-zero-day-flaw.html
P2PInfect botnet activity surges 600x with stealthier malware variants
https://www.bleepingcomputer.com/news/security/p2pinfect-botnet-activity-surges-600x-with-stealthier-malware-variants/
Behind the Scenes of BBTok: Analyzing a Banker’s Server Side Components - Check Point Research
https://research.checkpoint.com/2023/behind-the-scenes-of-bbtok-analyzing-a-bankers-server-side-components/
Tor-Based Drug Marketplace Piilopuoti Shut Down by Law Enforcement - SecurityWeek
https://www.securityweek.com/tor-based-drug-marketplace-piilopuoti-shut-down-by-law-enforcement/
Program | Australian Cyber Conference Melbourne 2023
https://cyberconference.com.au/melbourne/program
Atos Unify Vulnerabilities Could Allow Hackers to Backdoor Systems - SecurityWeek
https://www.securityweek.com/atos-unify-vulnerabilities-could-allow-hackers-to-backdoor-systems/
Quick, Draw!
https://quickdraw.withgoogle.com/
International Criminal Court hit with a cyber attack
https://securityaffairs.com/151115/hacking/international-criminal-court-cyber-attack.html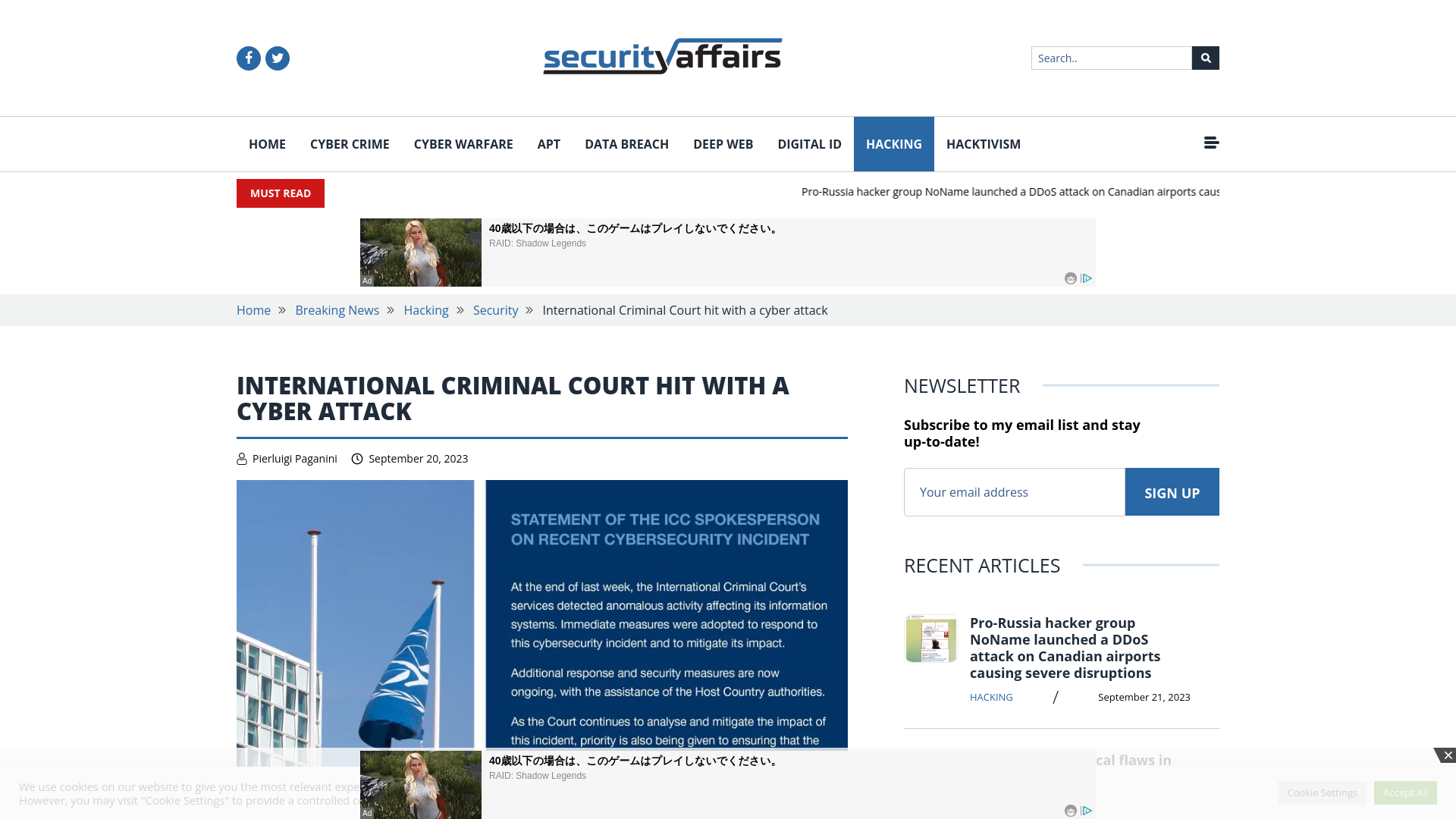
Free Download Manager releases script to check for Linux malware
https://www.bleepingcomputer.com/news/security/free-download-manager-releases-script-to-check-for-linux-malware/