r-tec Blog | Evade signature-based phishing detections - r-tec Cyber Security
https://www.r-tec.net/r-tec-blog-evade-signature-based-phishing-detections.html
Webinar Registration - Zoom
https://ghst.ly/3Om0jDo
BloodHound Community Edition: A New Era | by Andy Robbins | Aug, 2023 | Posts By SpecterOps Team Members
https://posts.specterops.io/bloodhound-community-edition-a-new-era-d64689806e90
https://github.com/SpecterOps/BloodHound/raw/main/examples/docker-compose/docker-compose.yml
https://github.com/SpecterOps/BloodHound/raw/main/examples/docker-compose/docker-compose.yml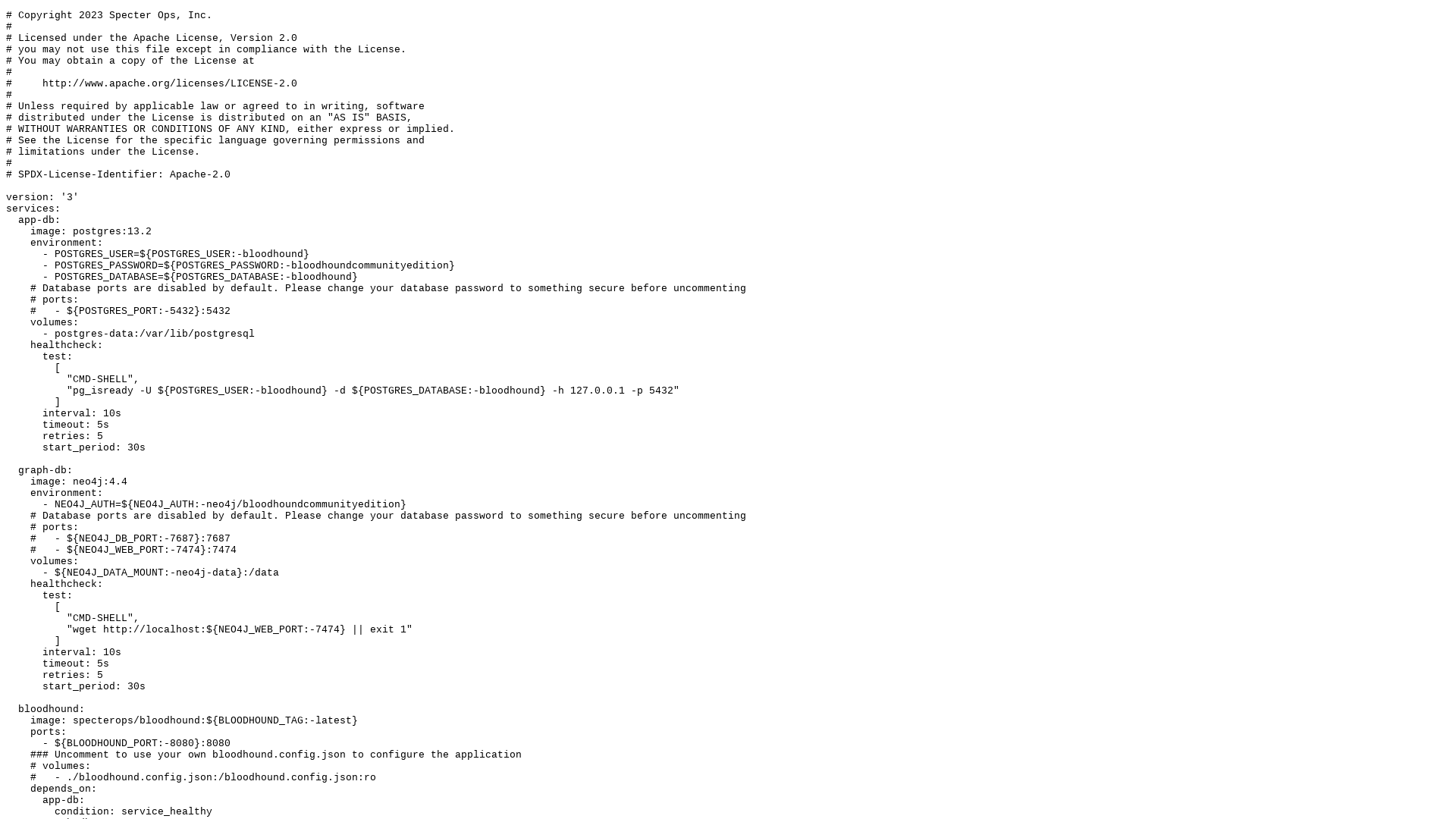
China hacked Japan’s classified defense cyber networks, officials say - The Washington Post
https://www.washingtonpost.com/national-security/2023/08/07/china-japan-hack-pentagon/
LOLBAS in the Wild: 11 Living-Off-The-Land Binaries That Could Be Used for Malicious Purposes
https://thehackernews.com/2023/08/lolbas-in-wild-11-living-off-land.html
QakBot Malware Operators Expand C2 Network with 15 New Servers
https://thehackernews.com/2023/08/qakbot-malware-operators-expand-c2.html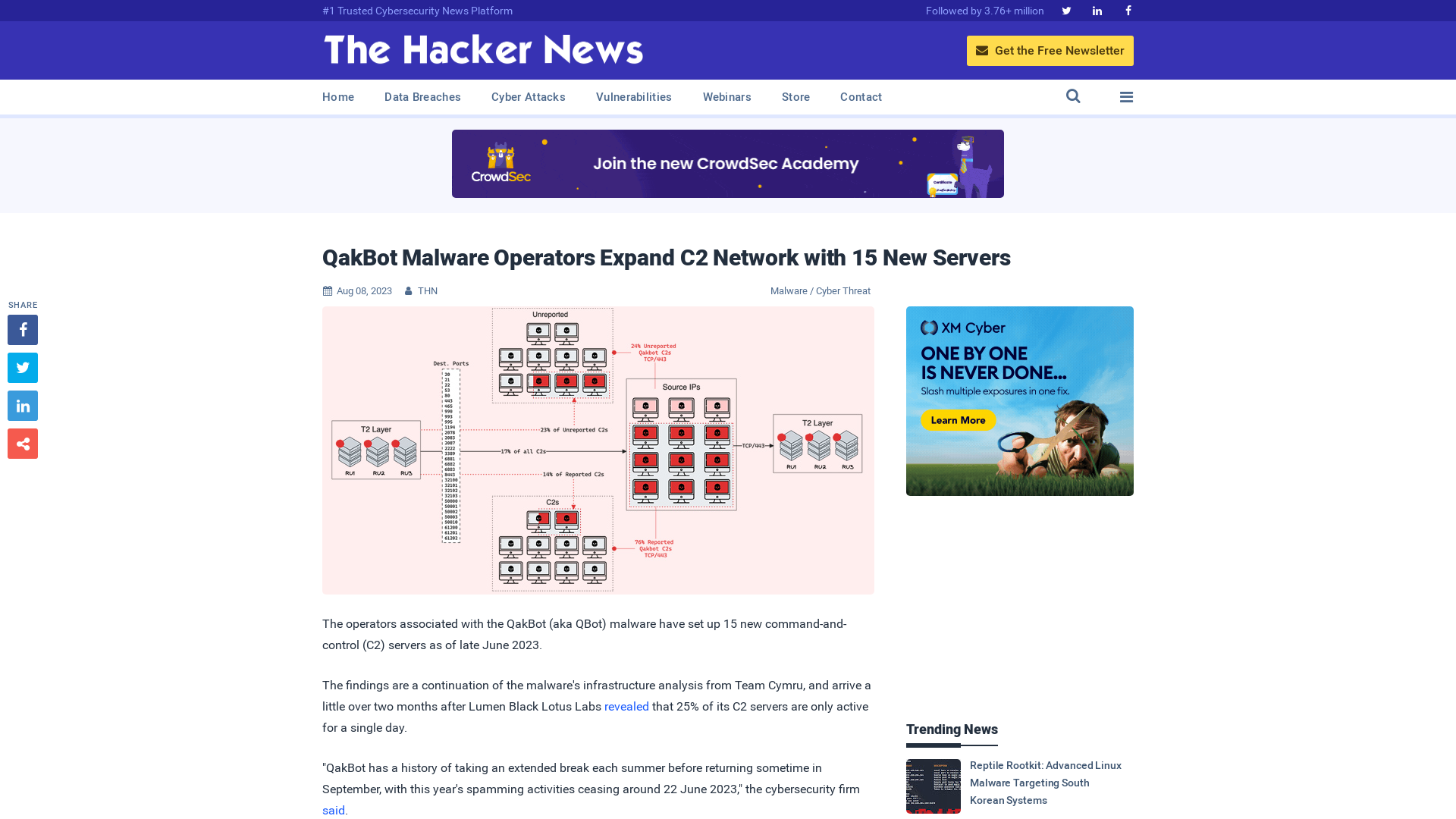
Ozzie Osband, Originator of "3-2-1" Telephone Area Code and "Rocket Hobo," Passes Away at 72
https://talkoftitusville.com/2023/08/06/ozzie-osband-originator-of-3-2-1-telephone-area-code-and-rocket-hobo-passes-away-at-72/
Black Hat Preview: The Business of Cyber Takes Center Stage - SecurityWeek
https://www.securityweek.com/black-hat-preview-the-business-of-cyber-takes-center-stage/
Special Offer for Asia Pacific Students | SANS Online Training
https://www.sans.org/u/1rOI
Microsoft August 2023 Patch Tuesday warns of 2 zero-days, 87 flaws
https://www.bleepingcomputer.com/news/microsoft/microsoft-august-2023-patch-tuesday-warns-of-2-zero-days-87-flaws/
How we made $5000 with this exploit - YouTube
https://www.youtube.com/watch?v=Wgo3bGv6KqI
GitHub - alexandreborges/malwoverview: Malwoverview is a first response tool used for threat hunting and offers intel information from Virus Total, Hybrid Analysis, URLHaus, Polyswarm, Malshare, Alien Vault, Malpedia, Malware Bazaar, ThreatFox, Triage, InQuest and it is able to scan Android devices against VT.
https://github.com/alexandreborges/malwoverview
New Yashma Ransomware Variant Targets Multiple English-Speaking Countries
https://thehackernews.com/2023/08/new-yashma-ransomware-variant-targets.html
Intel BIOS Advisory – Memory Corruption in HID Drivers | NCC Group Research Blog | Making the world safer and more secure
https://research.nccgroup.com/2023/08/08/intel-bios-advisory-memory-corruption-in-hid-drivers/
DEF CON 31 Living Next Door to Russia
https://info.defcon.org/event/?id=50859
Understanding Active Directory Attack Paths to Improve Security
https://thehackernews.com/2023/08/understanding-active-directory-attack.html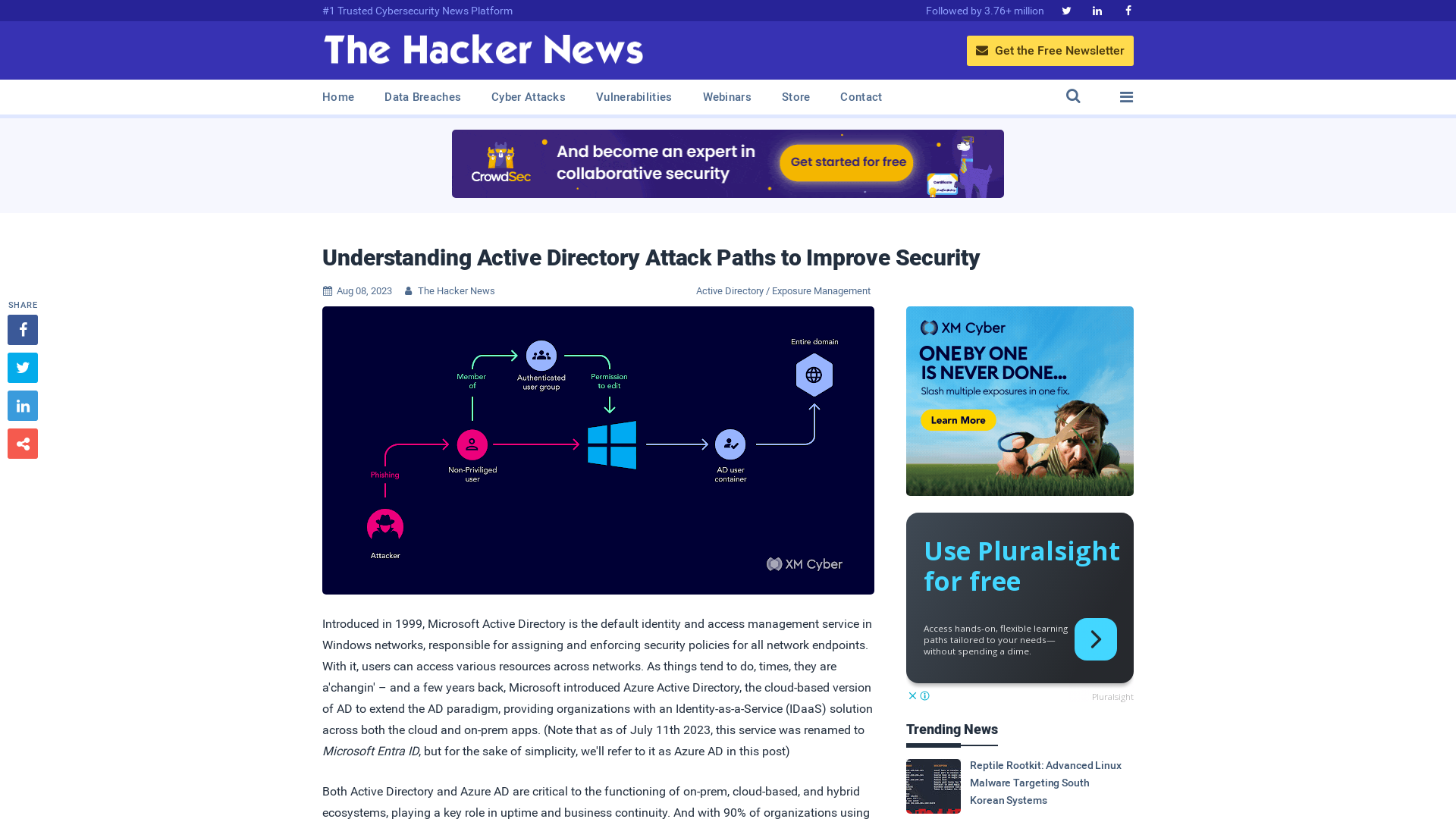
Cookieless DuoDrop: IIS Auth Bypass & App Pool Privesc in ASP.NET Framework (CVE-2023-36899) | Soroush Dalili (@irsdl) Blog
https://soroush.me/blog/2023/08/cookieless-duodrop-iis-auth-bypass-app-pool-privesc-in-asp-net-framework-cve-2023-36899/
iOS 17: New Version, New Acronyms — Dataflow Forensics
https://www.df-f.com/blog/ios17
Android 14 to let you block connections to unencrypted cellular networks
https://www.bleepingcomputer.com/news/google/android-14-to-block-connections-to-unencrypted-cellular-networks/
Interpol takes down 16shop phishing-as-a-service platform
https://www.bleepingcomputer.com/news/security/interpol-takes-down-16shop-phishing-as-a-service-platform/
Hackers increasingly abuse Cloudflare Tunnels for stealthy connections
https://www.bleepingcomputer.com/news/security/hackers-increasingly-abuse-cloudflare-tunnels-for-stealthy-connections/
New Downfall attacks on Intel CPUs steal encryption keys, data
https://www.bleepingcomputer.com/news/security/new-downfall-attacks-on-intel-cpus-steal-encryption-keys-data/
Notorious phishing platform shut down, arrests in international police operation
https://www.interpol.int/News-and-Events/News/2023/Notorious-phishing-platform-shut-down-arrests-in-international-police-operation
https://redsiege.com/jargon
https://redsiege.com/jargon
Authorities Warn Health Sector of Attacks by Rhysida Group
https://www.healthcareinfosecurity.com/authorities-warn-health-sector-attacks-by-rhysida-group-a-22753
20230808_press.pdf
https://www.npa.go.jp/bureau/cyber/pdf/20230808_press.pdf
Google Online Security Blog: Downfall and Zenbleed: Googlers helping secure the ecosystem
https://security.googleblog.com/2023/08/downfall-and-zenbleed-googlers-helping.html
New Inception attack leaks sensitive data from all AMD Zen CPUs
https://www.bleepingcomputer.com/news/security/new-inception-attack-leaks-secrets-from-all-amd-zen-cpus/
CVE-2023-39526: Critical SQL injection in PrestaShop
https://securityonline.info/cve-2023-39526-critical-sql-injection-in-prestashop/
eSentire | eSentire Threat Intelligence Malware Analysis: Raccoon…
https://www.esentire.com/blog/esentire-threat-intelligence-malware-analysis-raccoon-stealer-v2-part-2
UK Electoral Commission data breach exposes 8 years of voter data
https://www.bleepingcomputer.com/news/security/uk-electoral-commission-data-breach-exposes-8-years-of-voter-data/
DNS Takeover Explained: Protect Your Online Domain | Trickest
https://trickest.com/blog/dns-takeover-explained-protect-your-online-domain/
technical-report.pdf
https://ssu.gov.ua/uploads/files/DKIB/technical-report.pdf
Honeypot Recon: New Variant of SkidMap Targeting Redis | Trustwave
https://www.trustwave.com/en-us/resources/blogs/spiderlabs-blog/honeypot-recon-new-variant-of-skidmap-targeting-redis/
TikTok facing fines for violating children’s privacy
https://www.malwarebytes.com/blog/news/2023/08/tiktok-facing-fines-for-violating-childrens-privacy
CVE-2023-34034 Spring WebFlux Security Bypass Write-up & PoC
https://jfrog.com/blog/spring-webflux-cve-2023-34034-write-up-and-proof-of-concept/
RedHotel: A Prolific, Chinese State-Sponsored Group Operating at a Global Scale | Recorded Future
https://www.recordedfuture.com/redhotel-a-prolific-chinese-state-sponsored-group-operating-at-a-global-scale
Patch Tuesday: Adobe Patches 30 Acrobat, Reader Vulns - SecurityWeek
https://www.securityweek.com/patch-tuesday-adobe-patches-30-acrobat-reader-vulns/
Microsoft Office update breaks actively exploited RCE attack chain
https://www.bleepingcomputer.com/news/security/microsoft-office-update-breaks-actively-exploited-rce-attack-chain/
Analysis gtr.exe (MD5: 4449DB01A06234E6223E932114EE390A) Malicious activity - Interactive analysis ANY.RUN
https://app.any.run/tasks/20bcc67d-86ca-4a18-8489-a630aeb25151/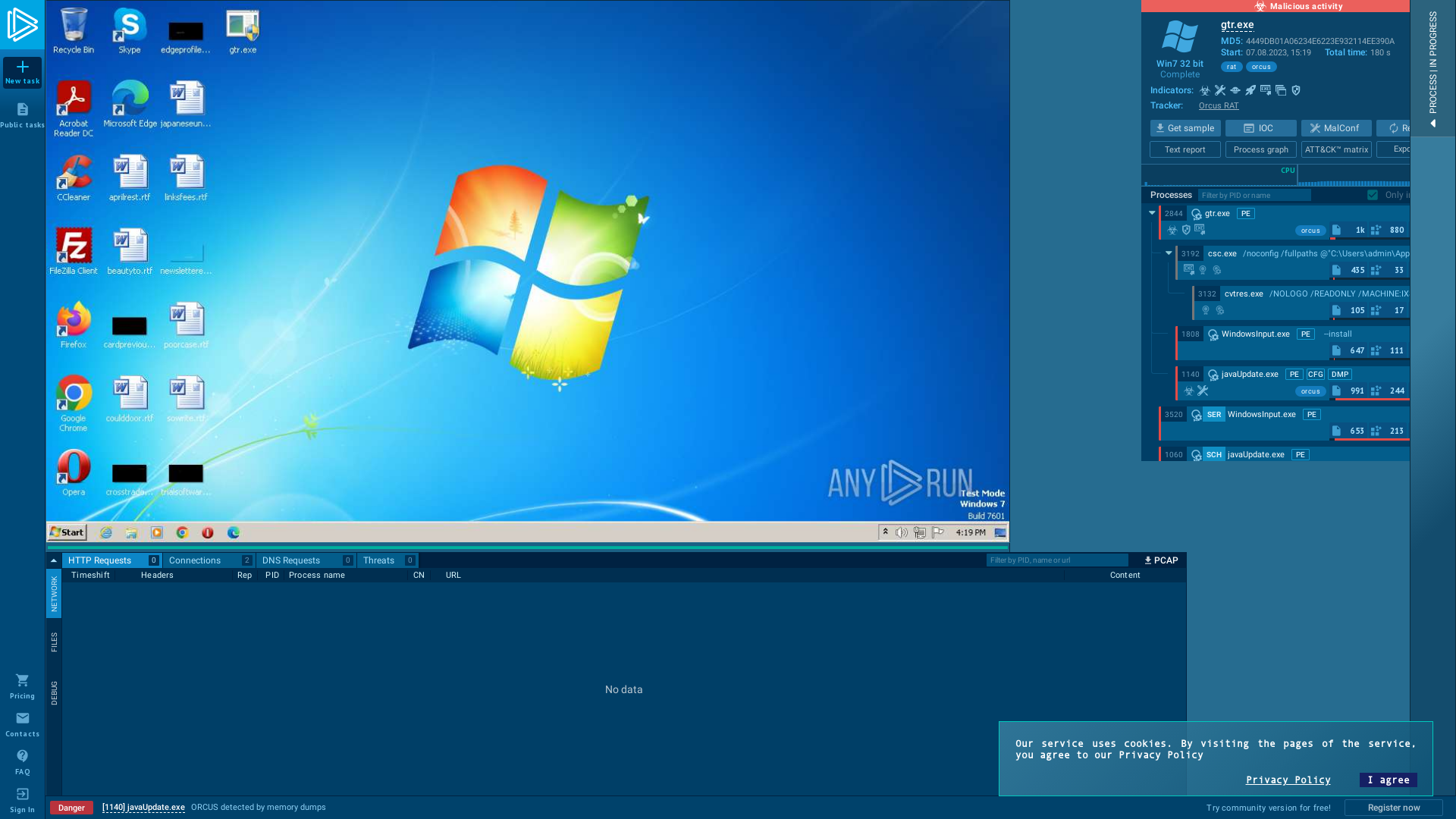
Google Online Security Blog: Android 14 introduces first-of-its-kind cellular connectivity security features
https://security.googleblog.com/2023/08/android-14-introduces-first-of-its-kind.html
Hackers Abusing Cloudflare Tunnels for Covert Communications
https://thehackernews.com/2023/08/hackers-abusing-cloudflare-tunnels-for.html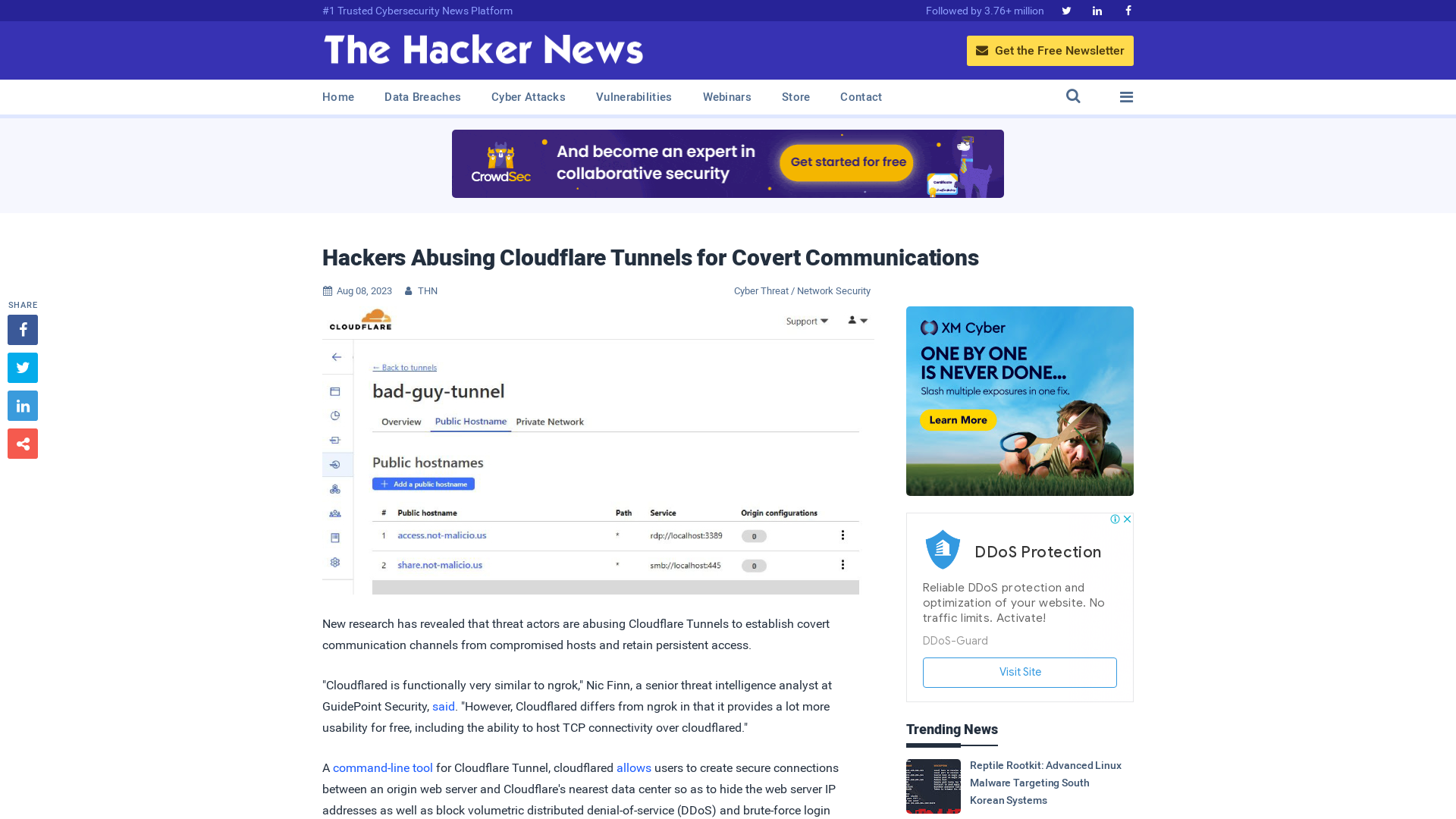
2022's most routinely exploited vulnerabilities—history repeats
https://www.malwarebytes.com/blog/news/2023/08/the-2022-top-routinely-exploited-vulnerabilities-history-repeats