eSentire | eSentire Threat Intelligence Malware Analysis: Raccoon…
https://www.esentire.com/blog/esentire-threat-intelligence-malware-analysis-raccoon-stealer-v2-part-2
Bootloaders.io
http://Bootloaders.io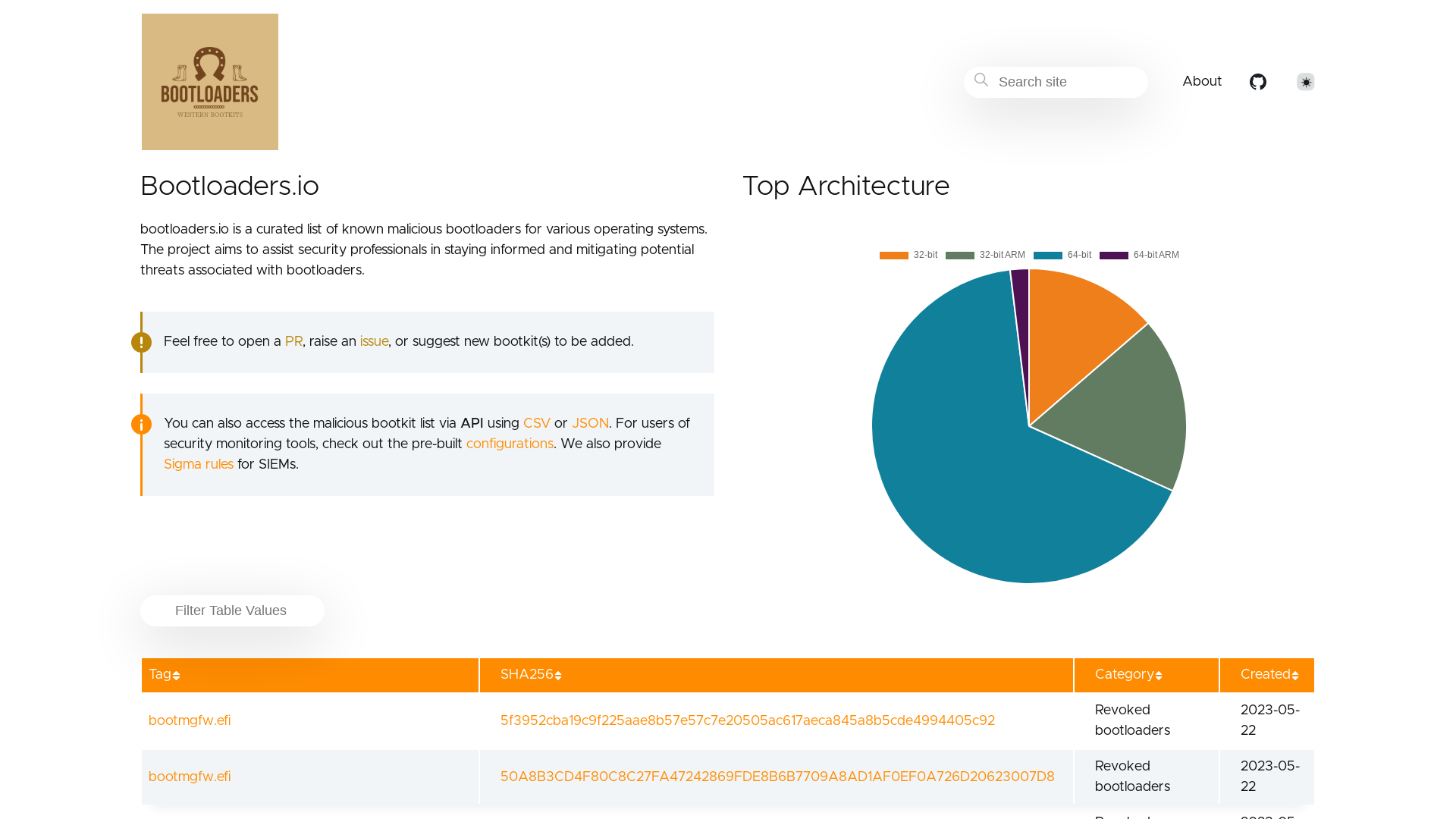
A cyberattack has disrupted hospitals and health care in several states | AP News
https://apnews.com/article/cyberattack-hospital-emergency-outage-4c808c1dad8686458ecbeababd08fecf
Leaked Secrets and Unlimited Miles: Hacking the Largest Airline and Hotel Rewards Platform
https://samcurry.net/Points-com/
Malicious npm Packages Found Exfiltrating Sensitive Data from Developers
https://thehackernews.com/2023/08/malicious-npm-packages-found.html
MalwareBazaar | Browse Checking your browser
https://bazaar.abuse.ch/browse/tag/agenziaentrate%20ita/
Cyber Ranges
https://dashboard.snaplabs.io/templates/121fda0a-6cc3-4889-bee3-2fe83856f530
Introducing Slinky Cat - Living off the AD Land
https://labs.lares.com/introducing-slinkycat/
Attackers use dynamic code loading to bypass Google Play store's malware detectionsSecurity Affairs
https://securityaffairs.com/149150/hacking/google-play-malware-versioning-evasion.html
Traces of Windows remote command execution
https://www.synacktiv.com/publications/traces-of-windows-remote-command-execution.html
お知らせ - NISC
https://www.nisc.go.jp/news/20230804.html
Microsoft kills Cortana in Windows 11 preview, long live AI!
https://www.bleepingcomputer.com/news/microsoft/microsoft-kills-cortana-in-windows-11-preview-long-live-ai/
Fake VMware vConnector package on PyPI targets IT pros
https://www.bleepingcomputer.com/news/security/fake-vmware-vconnector-package-on-pypi-targets-it-pros/
Meet Window Snyder, the trailblazer who helped secure the internet and billions of devices | TechCrunch
https://techcrunch.com/2023/08/04/window-snyder-cybersecurity-trailblazer/
Extended warranty robocallers fined $300 million after 5 billion scam calls
https://www.bleepingcomputer.com/news/security/extended-warranty-robocallers-fined-300-million-after-5-billion-scam-calls/
BTV @ DEF CON 31 [VEGAS] | Eventbrite
https://www.eventbrite.com/cc/btv-def-con-31-vegas-2468339![BTV @ DEF CON 31 [VEGAS] | Eventbrite](/image/screenshot/0c07a4870d9f72f895d3719ec15f1f96.png)
Log in to Twitter / X
https://twitter.com/i/broadcasts/1RDGlalydwlJL
New PaperCut critical bug exposes unpatched servers to RCE attacks
https://www.bleepingcomputer.com/news/security/new-papercut-critical-bug-exposes-unpatched-servers-to-rce-attacks/
Google offers on-campus hotel 'special' to lure workers back in
https://www.cnbc.com/2023/08/04/google-offers-on-campus-hotel-special-to-lure-workers-back-in.html
Google explains how Android malware slips onto Google Play Store
https://www.bleepingcomputer.com/news/security/google-explains-how-android-malware-slips-onto-google-play-store/
Microsoft Criticized Over Handling of Critical Power Platform Vulnerability - SecurityWeek
https://www.securityweek.com/microsoft-criticized-over-handling-of-critical-power-platform-vulnerability/
VirusTotal - File - 2cfec021b06404bdb56e855db49658aaba35ec7d3be500e5c86490d57ca7e7c5
https://www.virustotal.com/gui/file/2cfec021b06404bdb56e855db49658aaba35ec7d3be500e5c86490d57ca7e7c5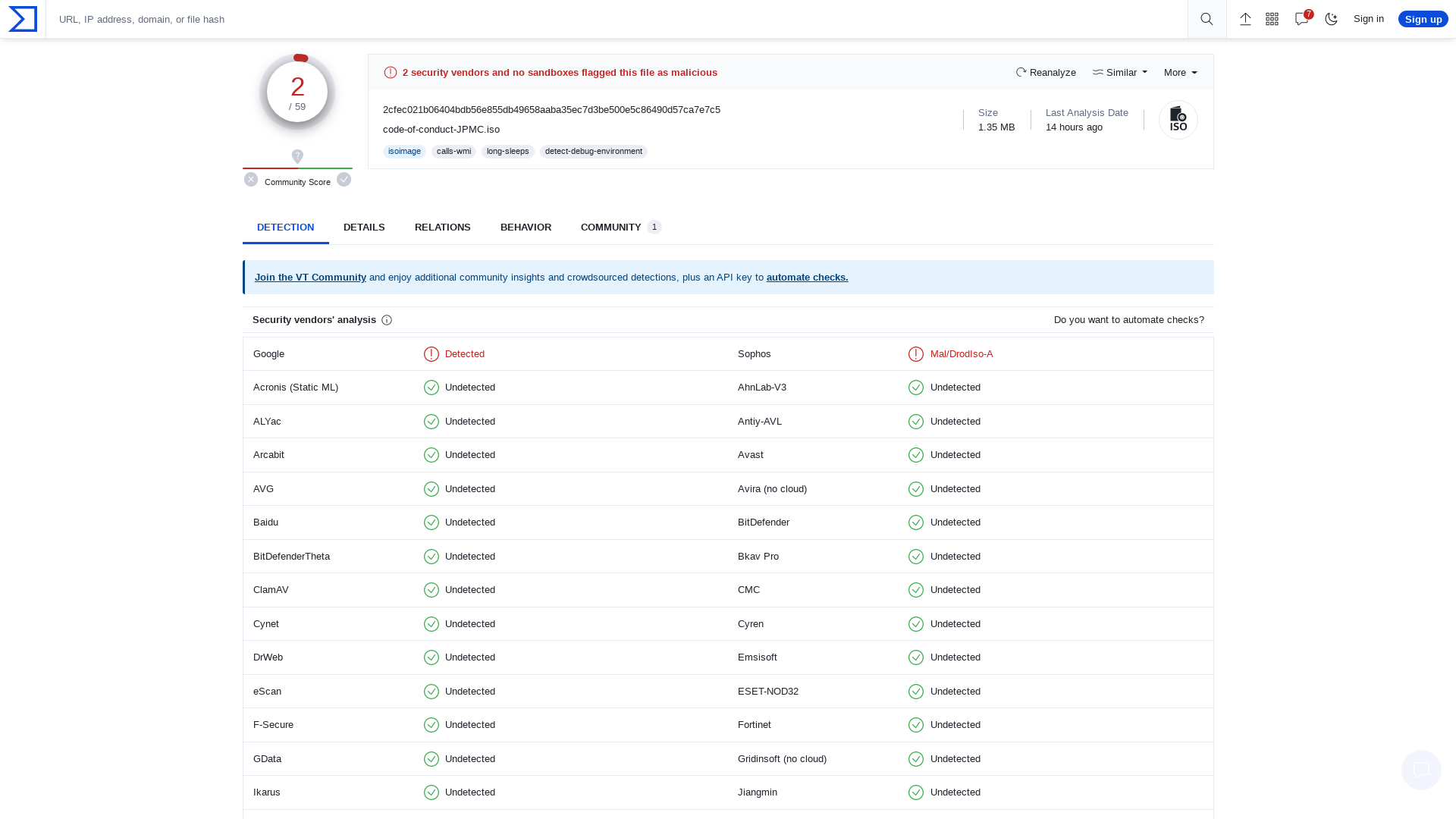
FBI, CISA, and NSA reveal top exploited vulnerabilities of 2022
https://www.bleepingcomputer.com/news/security/fbi-cisa-and-nsa-reveal-top-exploited-vulnerabilities-of-2022/
10 ways to exploit JWT (JSON Web Token): | by Musab Alharany | Jul, 2023 | Medium
https://medium.com/@musab_alharany/10-ways-to-exploit-json-web-token-jwt-ac5f4efbc41b
Film companies lose battle to unmask Reddit users
https://www.malwarebytes.com/blog/news/2023/08/old-reddit-posts-come-back-to-haunt-users-in-piracy-case
Spotify down: music searches, pages, account signups not working
https://www.bleepingcomputer.com/news/technology/spotify-down-music-searches-pages-account-signups-not-working/
NYC Couple Pleads Guilty to Money Laundering in $3.6 Billion Bitfinex Hack
https://thehackernews.com/2023/08/nyc-couple-pleads-guilty-to-money.html
Use Native Pointer of Function to Bypass The Latest Chrome v8 Sandbox (exp of issue1378239) | by Numen Cyber Labs | Aug, 2023 | Medium
https://medium.com/@numencyberlabs/use-native-pointer-of-function-to-bypass-the-latest-chrome-v8-sandbox-exp-of-issue1378239-251d9c5b0d14
Don’t you (forget NLP): Prompt injection with control characters in ChatGPT - Dropbox
https://dropbox.tech/machine-learning/prompt-injection-with-control-characters-openai-chatgpt-llm
Threat Actors Abuse Cloudflare Tunnel for Persistent Access, Data Theft - SecurityWeek
https://www.securityweek.com/threat-actors-abuse-cloudflare-tunnel-for-persistent-access-data-theft/
Poverty Stealer - Rule Signatures - Emerging Threats
https://community.emergingthreats.net/t/poverty-stealer/839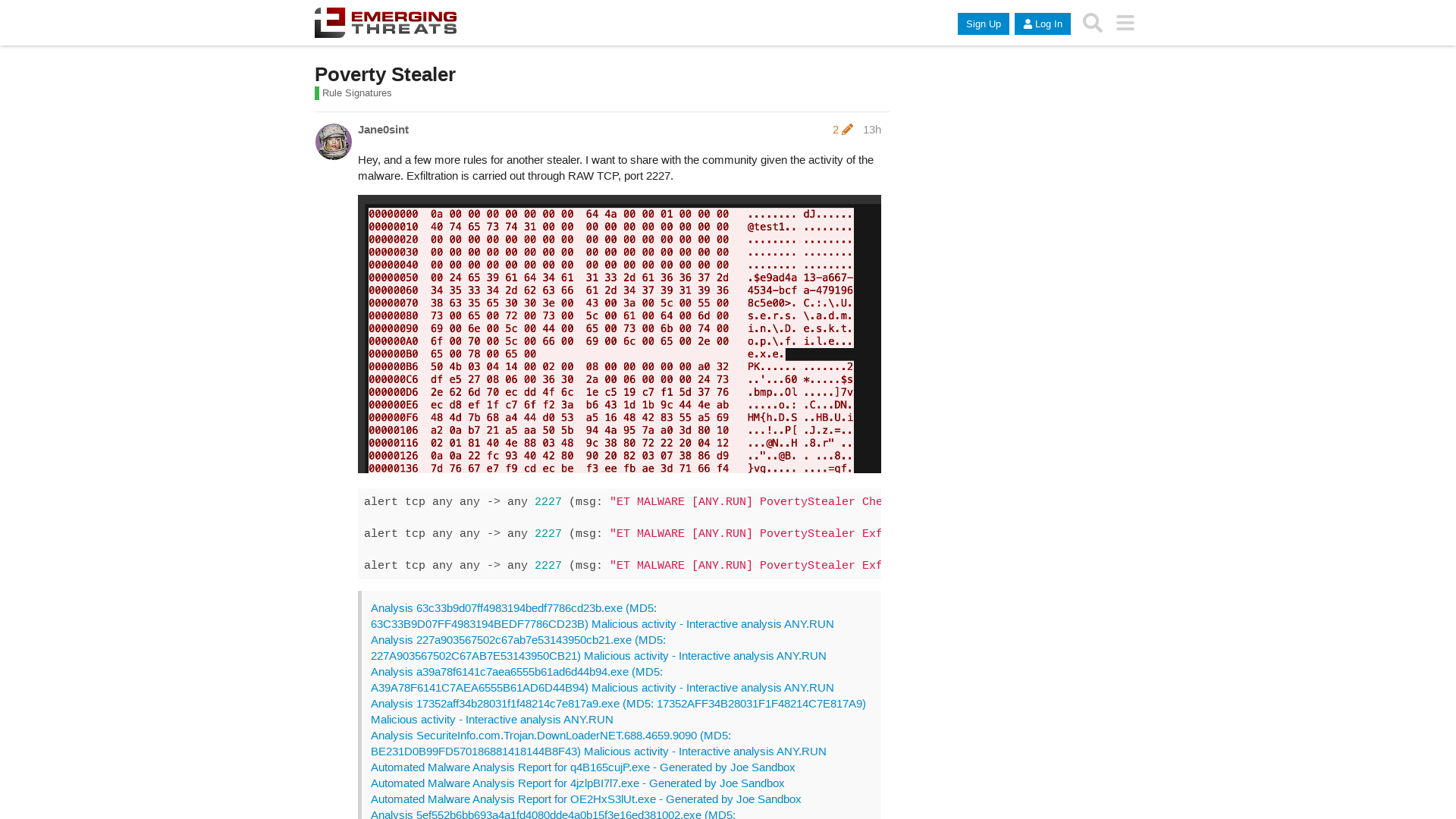
Removing Control Flow Flattening with Binary Ninja
https://www.lodsb.com/removing-control-flow-flattening-with-binary-ninja?ref=twitter-share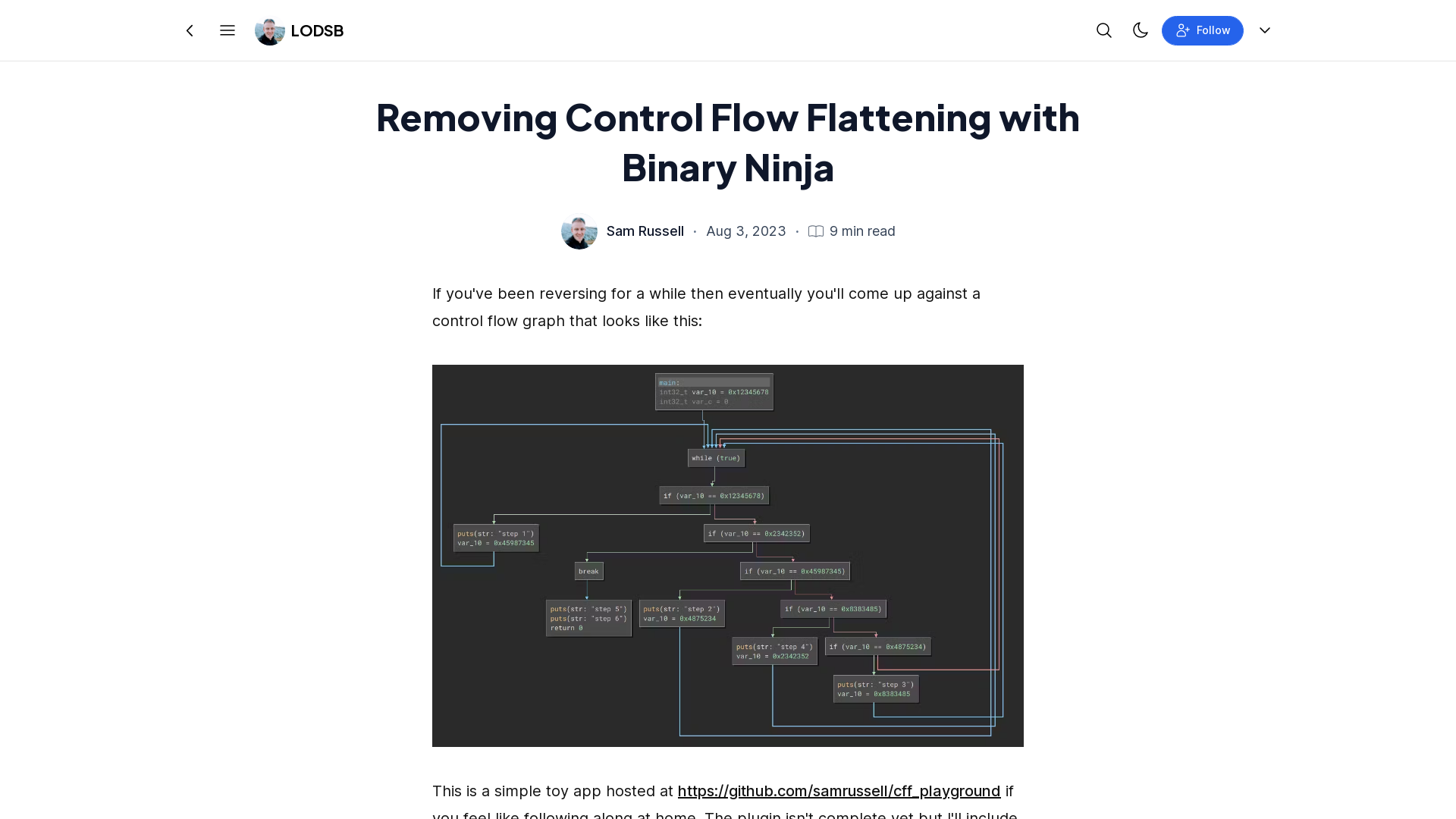
ANY.RUN - Interactive Online Malware Sandbox
http://ANY.RUN
IBM X-Force Research & Development - Insights on Security Threats
https://securityintelligence.com/x-force/
CommSec Track - HITBSecConf2023 - Phuket
https://conference.hitb.org/hitbsecconf2023hkt/commsec-track/
Dominic Alvieri on Twitter: "UCLA posted by CLoP Ransomware. @UCLA https://t.co/pHSMkKhvp7" / X
https://twitter.com/alvierid/status/1673486369841192963?s=46&t=j5mEwvRLGb4QhLYNi4_W0Q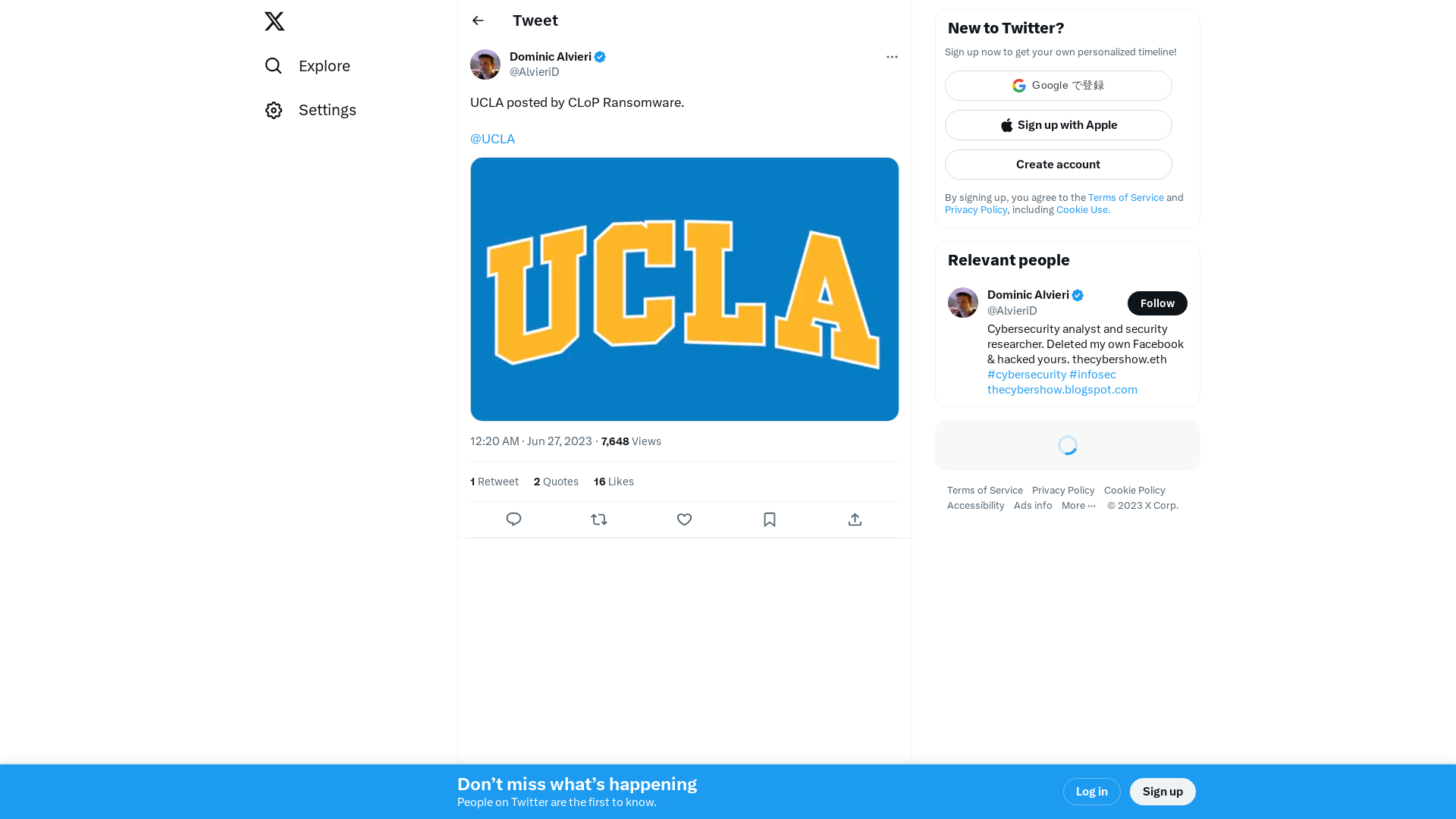
Profile / X
https://twitter.com/Codebendar_Cate?t=tzyxtvwr83jP4CgyEvCO1g&s=09
Major Cybersecurity Agencies Collaborate to Unveil 2022's Most Exploited Vulnerabilities
https://thehackernews.com/2023/08/major-cybersecurity-agencies.html
Windows Internals: Day 2 (Pavel)
https://training.trainsec.net/windows-internals-day-2-pavel