Identifying and Exploiting Unsafe Deserialization in Ruby | by Plenum | Aug, 2023 | Medium
https://link.medium.com/tc9mOBQlUBb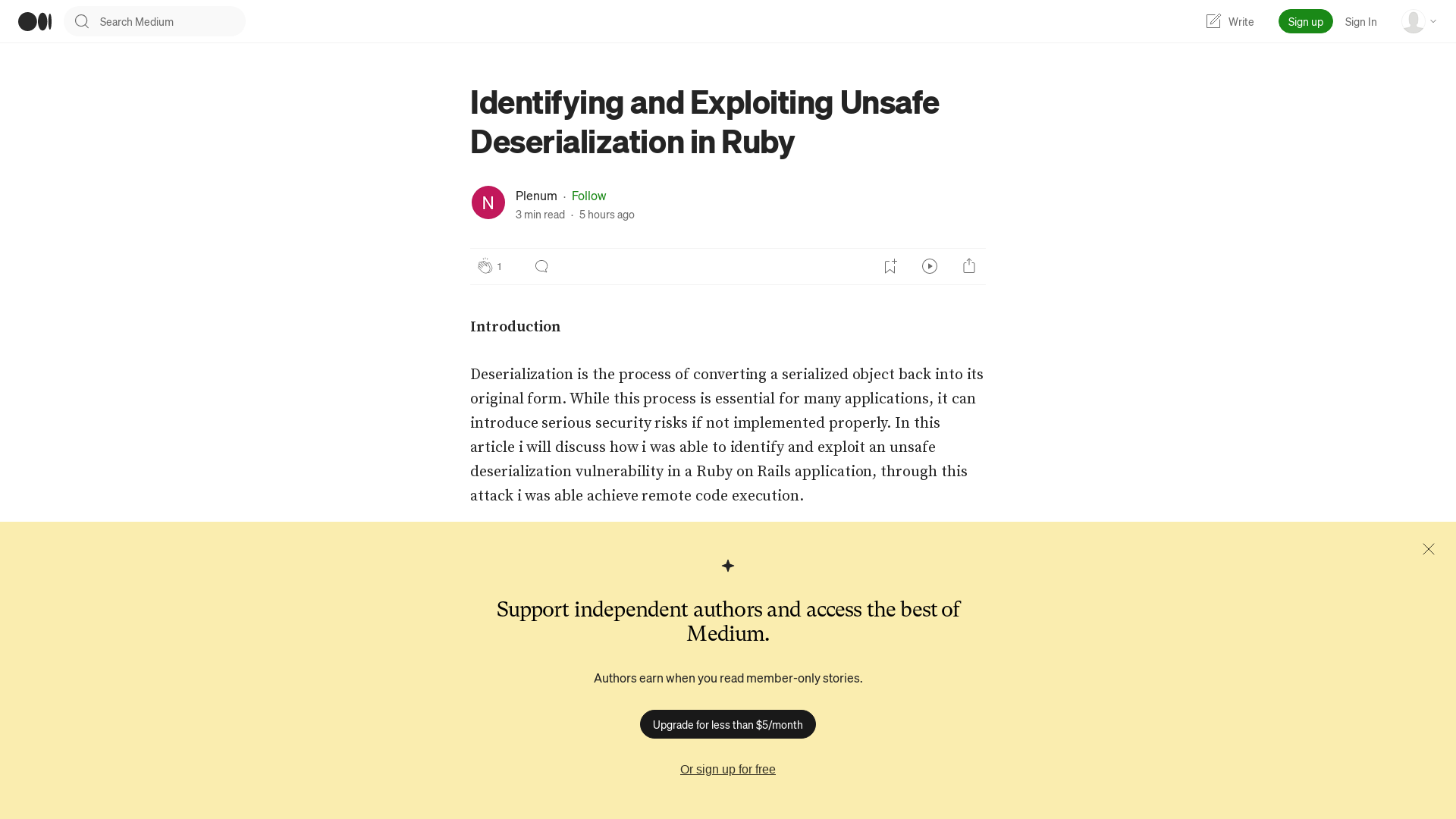
Ivanti EPMM (MobileIron Core) Authentication Bypass Attempt | GreyNoise Visualizer
https://viz.greynoise.io/tag/ivanti-epmm-mobileiron-core-authentication-bypass-attempt?days=10
Researchers Expose Space Pirates' Cyber Campaign Across Russia and Serbia
https://thehackernews.com/2023/08/researchers-expose-space-pirate-cyber.html
Cybercriminals Renting WikiLoader to Target Italian Organizations with Banking Trojan
https://thehackernews.com/2023/08/cybercriminals-renting-wikiloader-to.html
European Bank Customers Targeted in SpyNote Android Trojan Campaign
https://thehackernews.com/2023/08/european-bank-customers-targeted-in.html
Out of the Sandbox: WikiLoader Digs Sophisticated Evasion | Proofpoint US
https://www.proofpoint.com/us/blog/threat-insight/out-sandbox-wikiloader-digs-sophisticated-evasion
China's APT31 Suspected in Attacks on Air-Gapped Systems in Eastern Europe
https://thehackernews.com/2023/08/chinas-apt31-suspected-in-attacks-on.html
New NodeStealer Targeting Facebook Business Accounts and Crypto Wallets
https://thehackernews.com/2023/08/new-nodestealer-targeting-facebook.html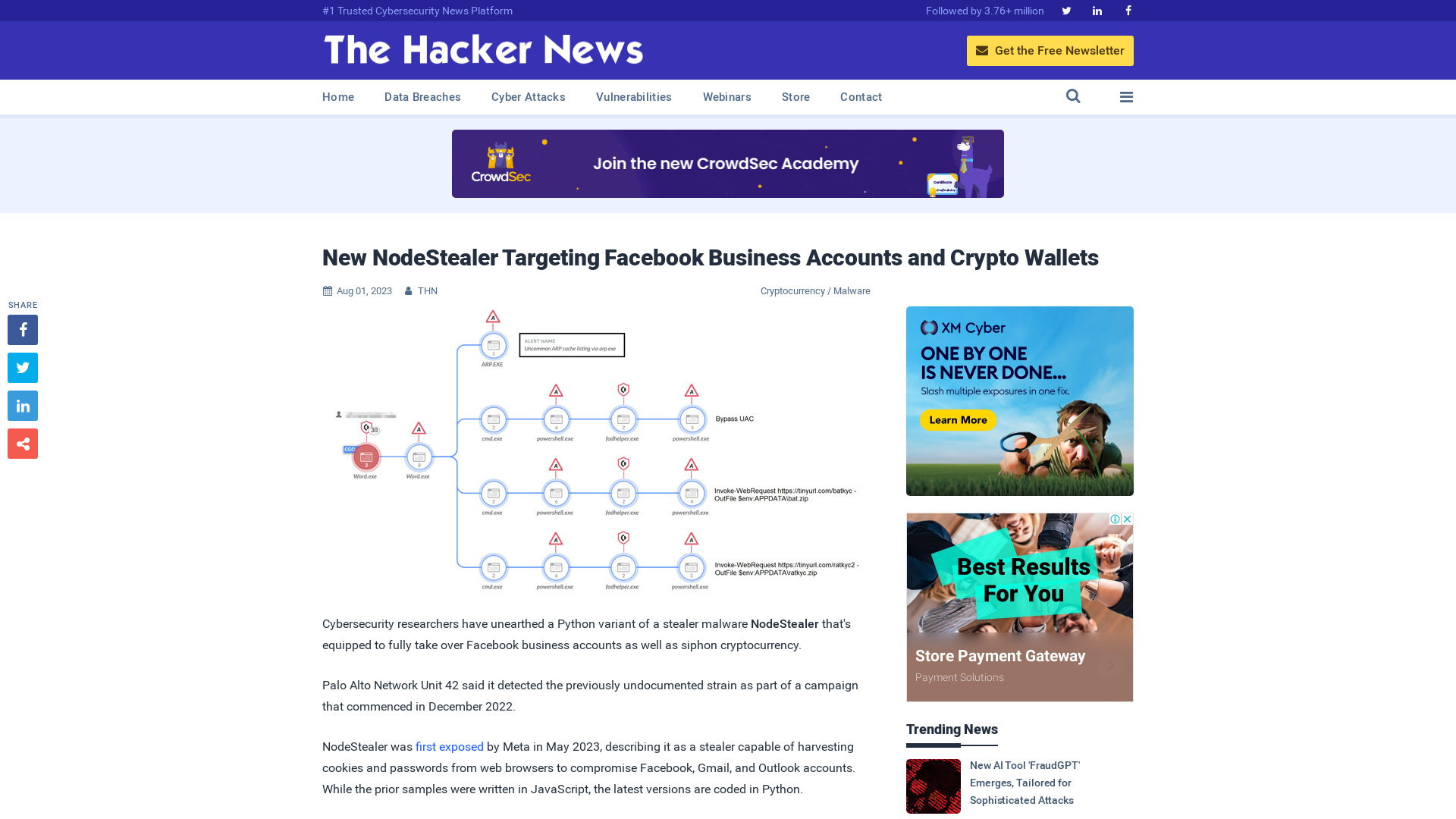
Manipulated Caiman: The Sophisticated Snare of Mexico's Banking Predators - Perception Point
https://perception-point.io/blog/manipulated-caiman-the-sophisticated-snare-of-mexicos-banking-predators-technical-edition/
Sliver C2 Being Distributed Through Korean Program Development Company - ASEC BLOG
https://asec.ahnlab.com/en/55652/
ZAP – ZAP is Joining the Software Security Project
https://www.zaproxy.org/blog/2023-08-01-zap-is-joining-the-software-security-project/
Cloud company assisted 17 different government hacking groups -US researchers | Reuters
https://www.reuters.com/technology/cloud-company-assisted-17-different-government-hacking-groups-us-researchers-2023-08-01/
APT_REPORT/konni/20230727_threat_inteligence_report_Konni.pdf at master · blackorbird/APT_REPORT · GitHub
https://github.com/blackorbird/APT_REPORT/blob/master/konni/20230727_threat_inteligence_report_Konni.pdf
Copy of CSM Login Okta - Customer Support
https://beyondtrustcorp.service-now.com/csm?id=kb_article_view&sysparm_article=KB0020207
200 Canon Printer Models May Expose Wi-Fi Connection Data - SecurityWeek
https://www.securityweek.com/200-canon-printer-models-may-expose-wi-fi-connection-data/
CVE-2023-3519 | AttackerKB
https://attackerkb.com/topics/si09VNJhHh/cve-2023-3519/rapid7-analysis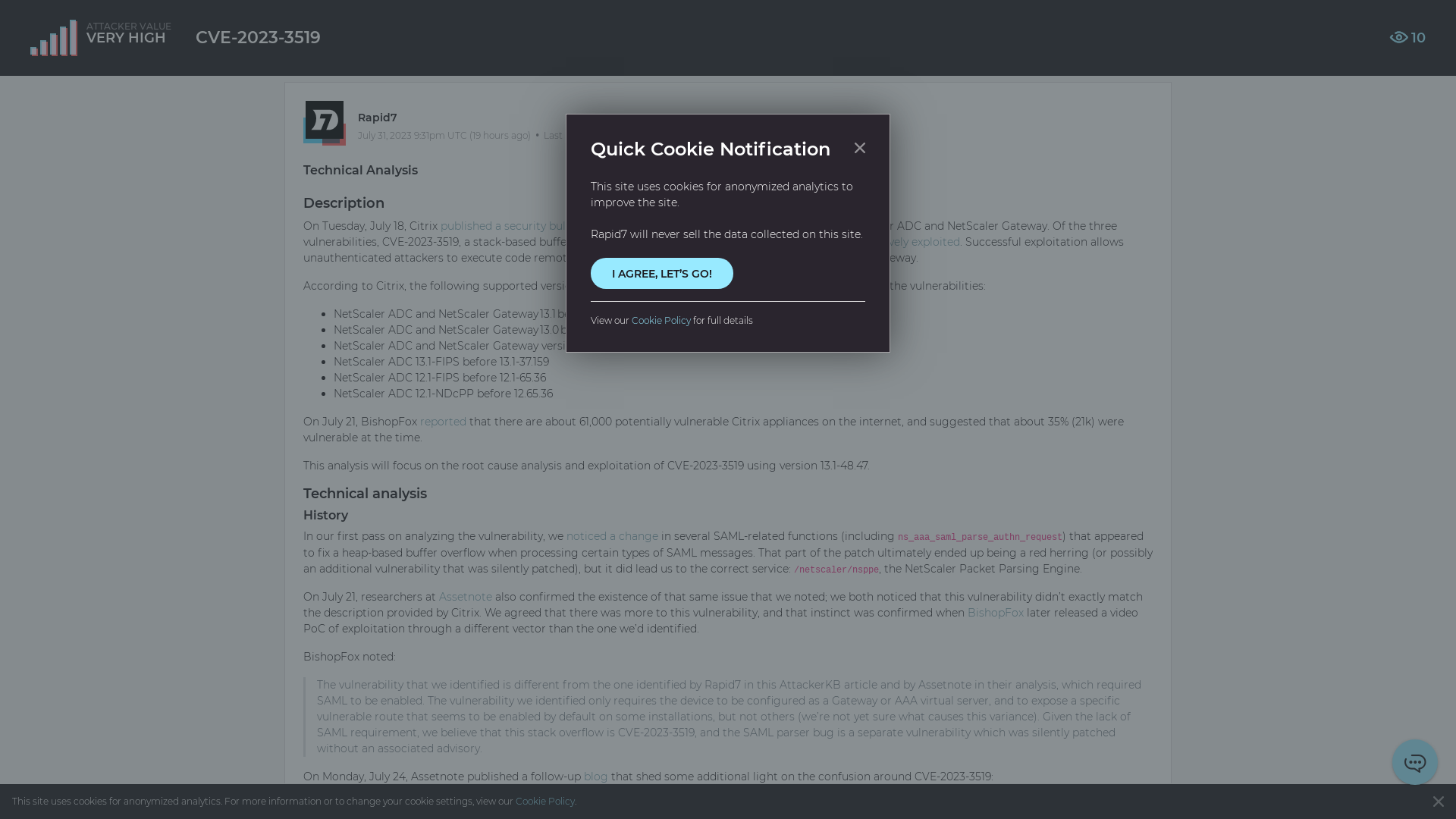
Analysis https://www.evarlic.com/wp-content/download/File_pass1234.7z Malicious activity - Interactive analysis ANY.RUN
https://app.any.run/tasks/ab935ea1-b1be-4b14-8681-94377482d312/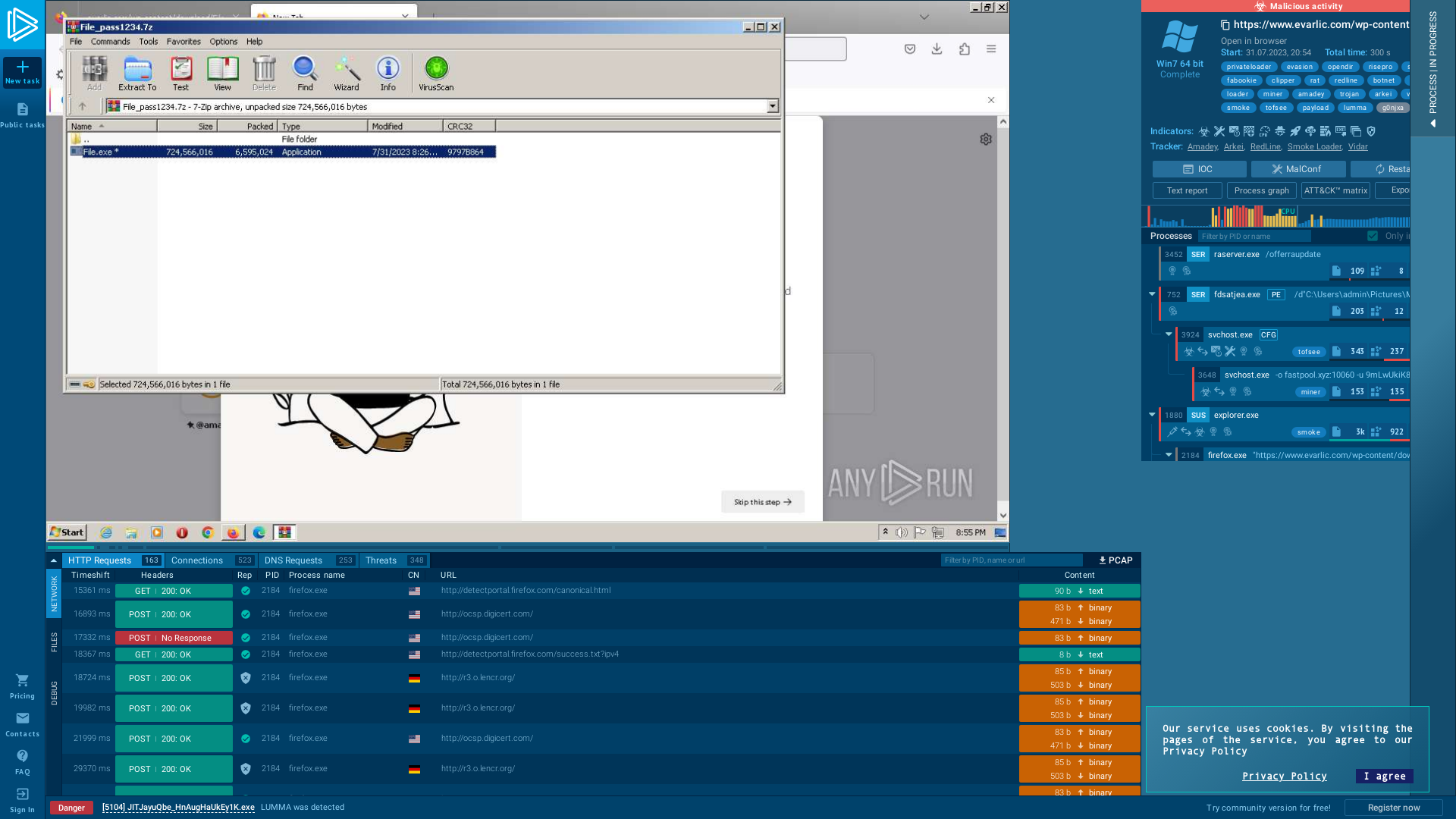
Retail chain Hot Topic discloses wave of credential-stuffing attacks
https://www.bleepingcomputer.com/news/security/retail-chain-hot-topic-discloses-wave-of-credential-stuffing-attacks/
The Most Useful Recon Trick - YouTube
https://youtu.be/zDB-SdT6_FI
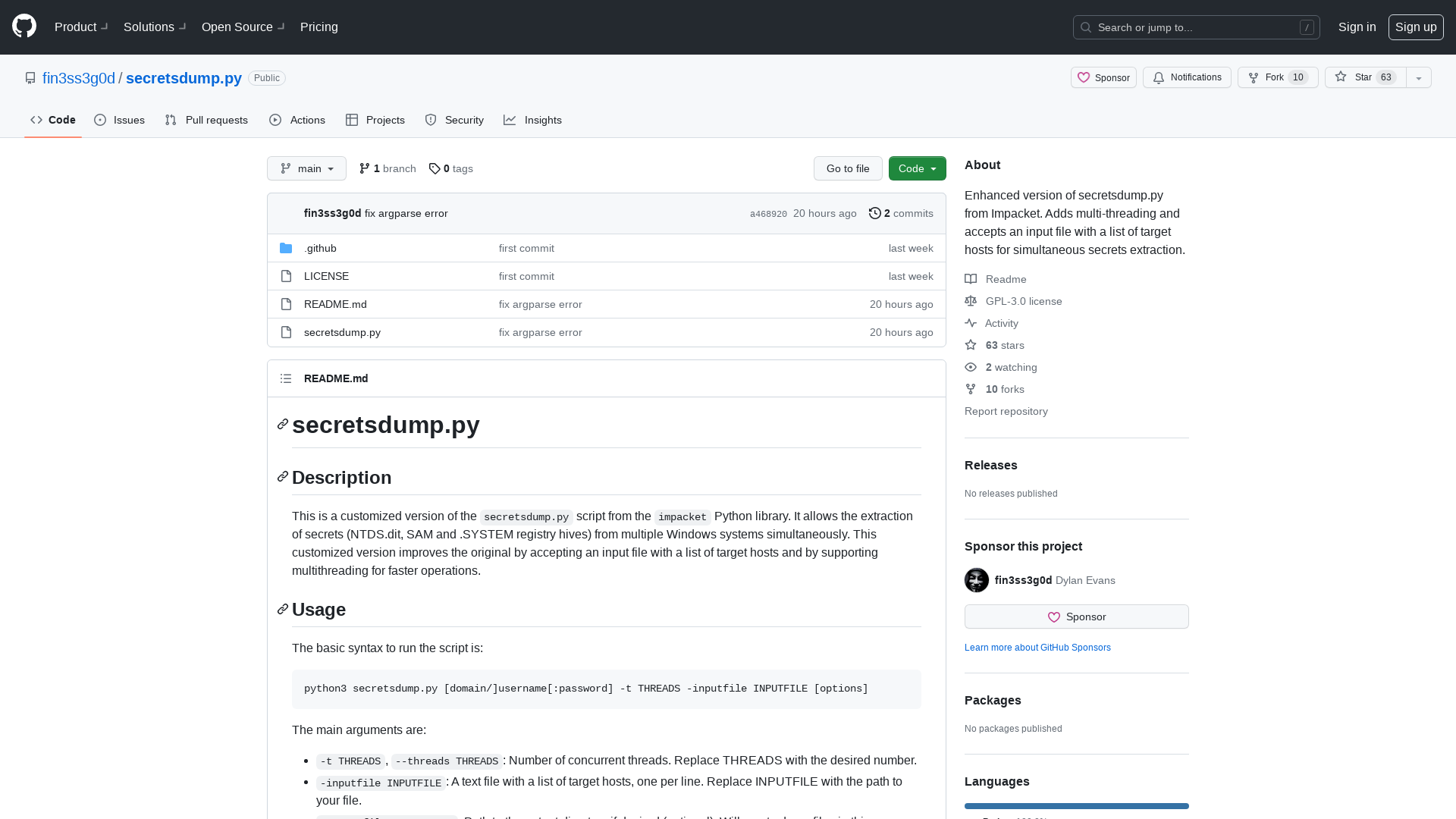
GitHub - waf-bypass-maker/waf-community-bypasses
https://github.com/waf-bypass-maker/waf-community-bypasses
http://archwisp.com/mixes/Archwisp%20-%20DEF%20CON%2028%20Defcon%20Parties%20Mix.mp3
http://archwisp.com/mixes/Archwisp%20-%20DEF%20CON%2028%20Defcon%20Parties%20Mix.mp3
【注意喚起】インターネット境界に設置された装置に対するサイバー攻撃について~ネットワーク貫通型攻撃に注意しましょう~ | 情報セキュリティ | IPA 独立行政法人 情報処理推進機構
https://www.ipa.go.jp/security/security-alert/2023/alert20230801.html
MCTTP 2023 Talk Preview by Oddvar Moe - YouTube
https://youtu.be/EwW-lLVgQRU
VirusTotal - File - 904d3fa49f2a9c201153f1c533afd6255fbb21c5ef34331bd8be959f8c6d99fe
https://www.virustotal.com/gui/file/904d3fa49f2a9c201153f1c533afd6255fbb21c5ef34331bd8be959f8c6d99fe/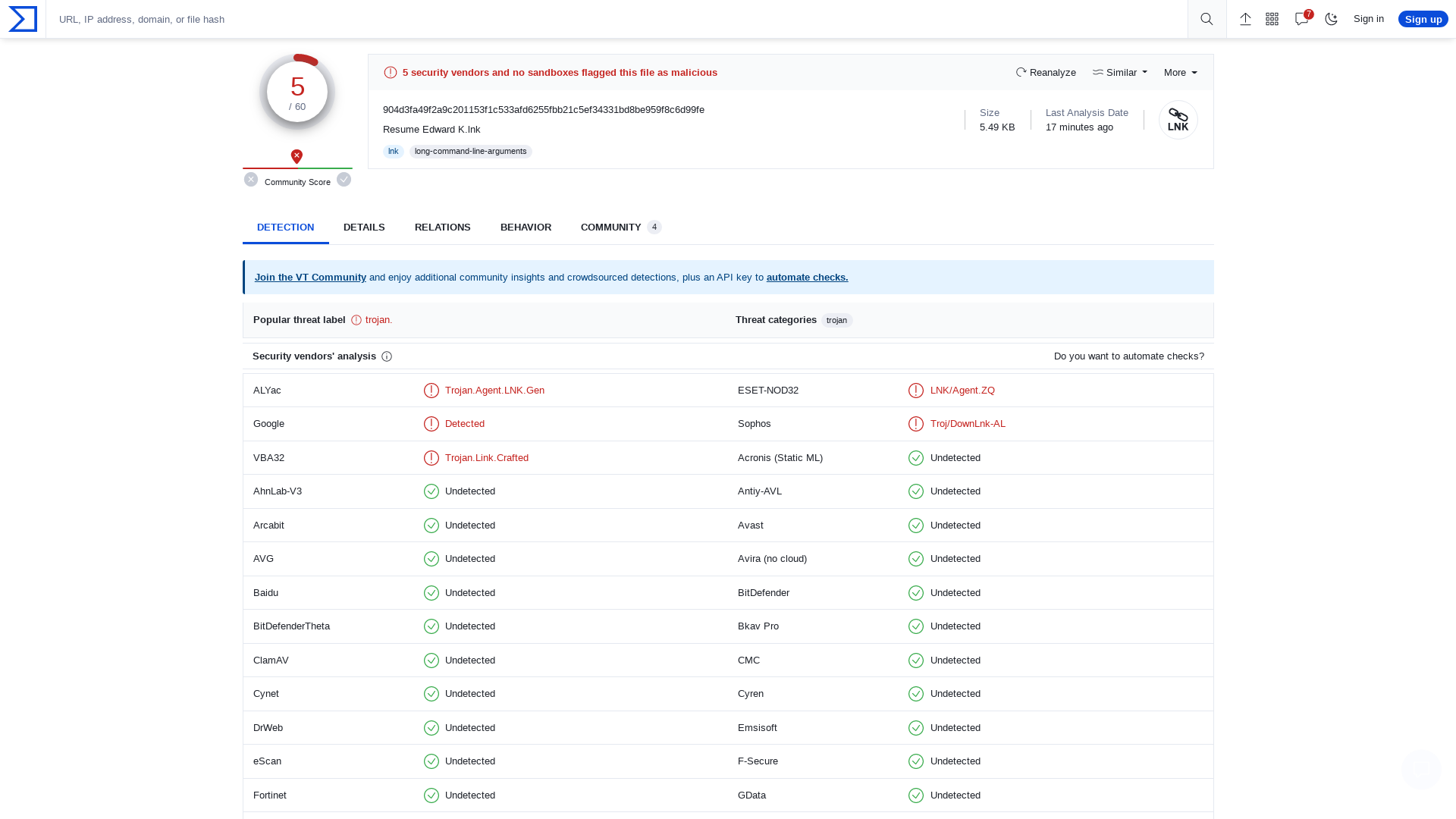
The gap in users' identity security knowledge gives cybercriminals an opening - Help Net Security
https://www.helpnetsecurity.com/2023/08/01/identity-security-knowledge/
Virtual Influence: A New Take on an Old Saying · rez0
https://rez0.blog/personal/2023/07/30/virtual-influence.html
Hackers use new malware to breach air-gapped devices in Eastern Europe
https://www.bleepingcomputer.com/news/security/hackers-use-new-malware-to-breach-air-gapped-devices-in-eastern-europe/