Exploitation of Citrix Zero-Day by Possible Espionage Actors (CVE-2023-3519) | Mandiant
https://www.mandiant.com/resources/blog/citrix-zero-day-espionage
Apple Threatens to Pull iMessage and FaceTime from U.K. Amid Surveillance Demands
https://thehackernews.com/2023/07/apple-threatens-to-pull-imessage-and.html
V8 Sandbox - Code Pointer Sandboxing - Google ドキュメント
https://docs.google.com/document/d/1CPs5PutbnmI-c5g7e_Td9CNGh5BvpLleKCqUnqmD82k/edit?usp=sharing
Recon 2023 - Daniel Wegemer - Enabling Security Research On Qualcomm Wifi Chips - YouTube
https://www.youtube.com/watch?v=y1puT_4en5I
Over 15K Citrix servers likely vulnerable to CVE-2023-3519 attacks
https://www.bleepingcomputer.com/news/security/over-15k-citrix-servers-likely-vulnerable-to-cve-2023-3519-attacks/
GitHub - jfjallid/go-secdump: Tool to remotely dump secrets from the Windows registry
https://github.com/jfjallid/go-secdump
GitHub - therealdreg/masm32-kernel-programming: masm32 kernel programming, drivers, tutorials, examples, and tools (credits Four-F)
https://github.com/therealdreg/masm32-kernel-programming
https://www.qualys.com/2023/07/19/cve-2023-38408/rce-openssh-forwarded-ssh-agent.txt
https://www.qualys.com/2023/07/19/cve-2023-38408/rce-openssh-forwarded-ssh-agent.txt
GitHub - MzHmO/PowershellKerberos: Some scripts to abuse kerberos using Powershell
https://github.com/MzHmO/PowershellKerberos
PE-Obfuscator: PE obfuscator with Evasion in mind
https://securityonline.info/pe-obfuscator-pe-obfuscator-with-evasion-in-mind/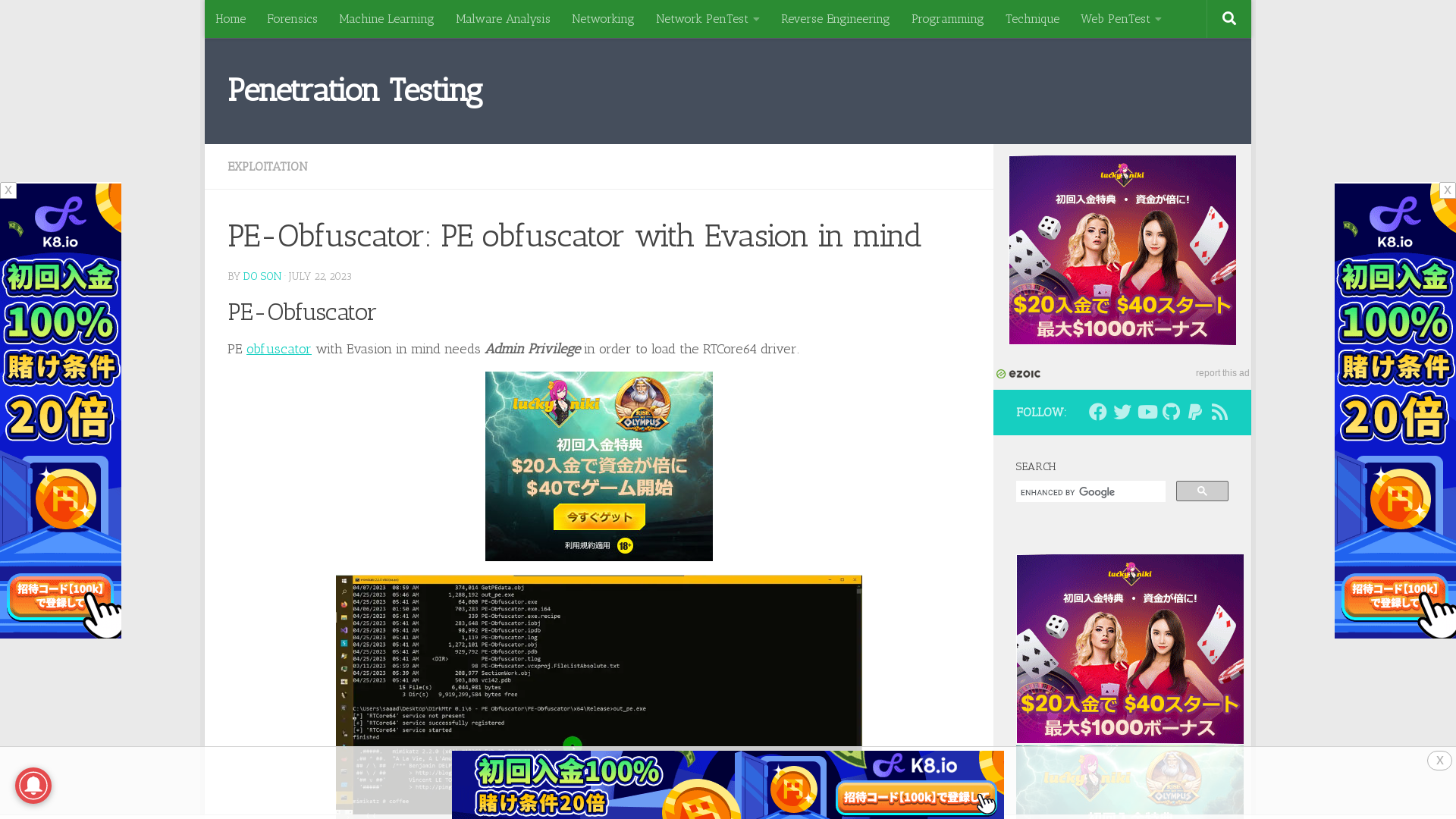
aa23-201a_csa_threat_actors_exploiting_citrix-cve-2023-3519_to_implant_webshells.pdf
https://www.cisa.gov/sites/default/files/2023-07/aa23-201a_csa_threat_actors_exploiting_citrix-cve-2023-3519_to_implant_webshells.pdf
Attacking MS Exchange Web Interfaces – PT SWARM
https://swarm.ptsecurity.com/attacking-ms-exchange-web-interfaces/
Mobile App Pentesting: AndroGOAT Assessment Walkthrough | by Martian | Jul, 2023 | InfoSec Write-ups
https://infosecwriteups.com/mobile-pentesting-androgoat-assessment-walkthrough-1a63a7edc677
Attacking Active Directory: 0 to 0.9 | zer1t0
https://zer1t0.gitlab.io/posts/attacking_ad