Varmint Al's Hunting Page
https://wiby.me/surprise/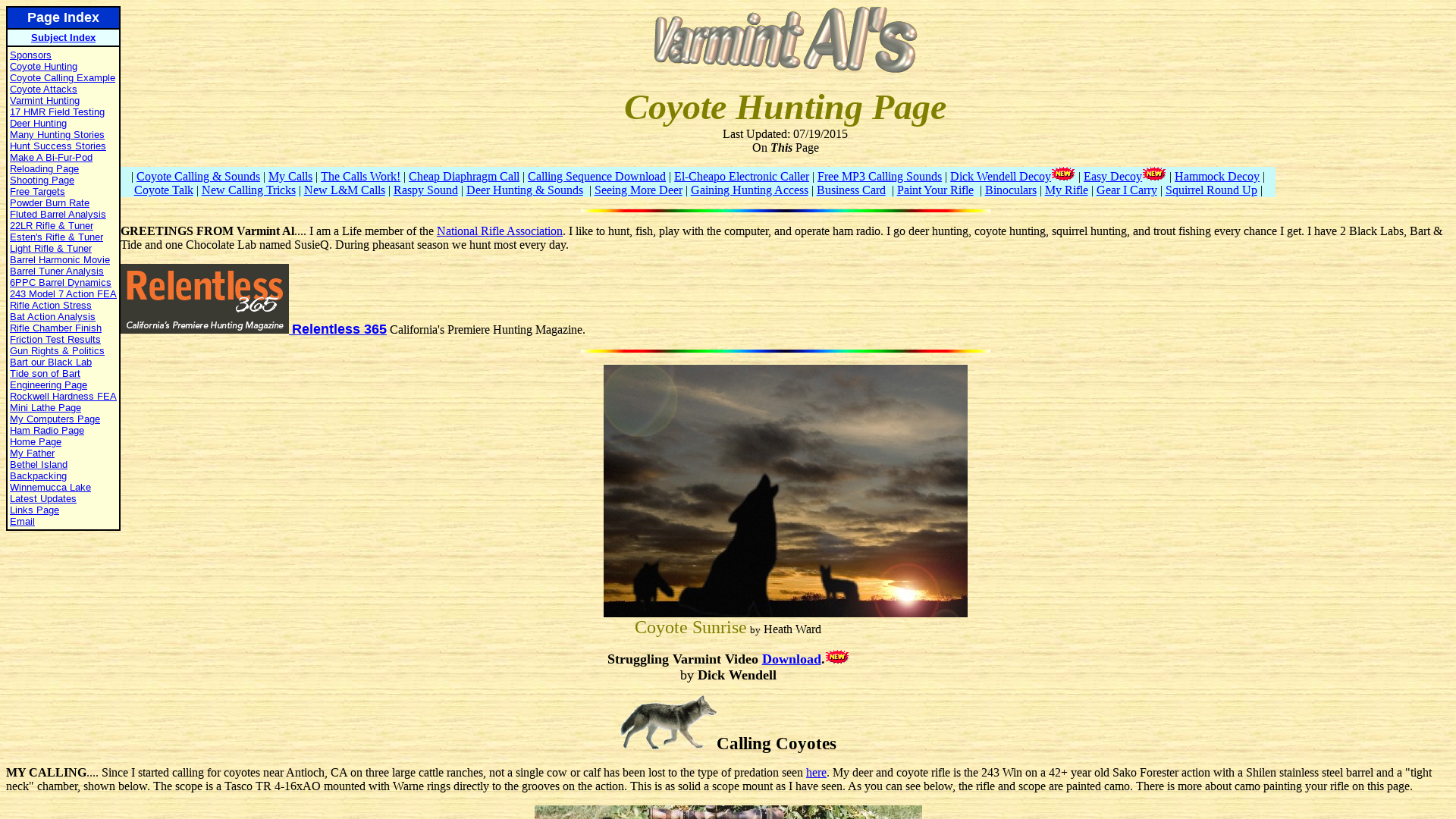
Analysis of Storm-0558 techniques for unauthorized email access | Microsoft Security Blog
https://www.microsoft.com/en-us/security/blog/2023/07/14/analysis-of-storm-0558-techniques-for-unauthorized-email-access/
Unpacking and Analysing DuckTail Stealer Malware! - Twitch
https://www.twitch.tv/videos/1872686049
Thousands of images on Docker Hub leak auth secrets, private keys
https://www.bleepingcomputer.com/news/security/thousands-of-images-on-docker-hub-leak-auth-secrets-private-keys/
Hacking Active Directory with Sliver C2 | by Root ♊ | Jul, 2023 | Medium
https://link.medium.com/rtNQVt22tBb
JSluice: There's Gold In Them Thar Files by Tomnomnom - YouTube
https://www.youtube.com/watch?v=BnQBp83YbqY