People's Republic of China State-Sponsored Cyber Actor Living off the Land to Evade Detection | CISA
https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-144a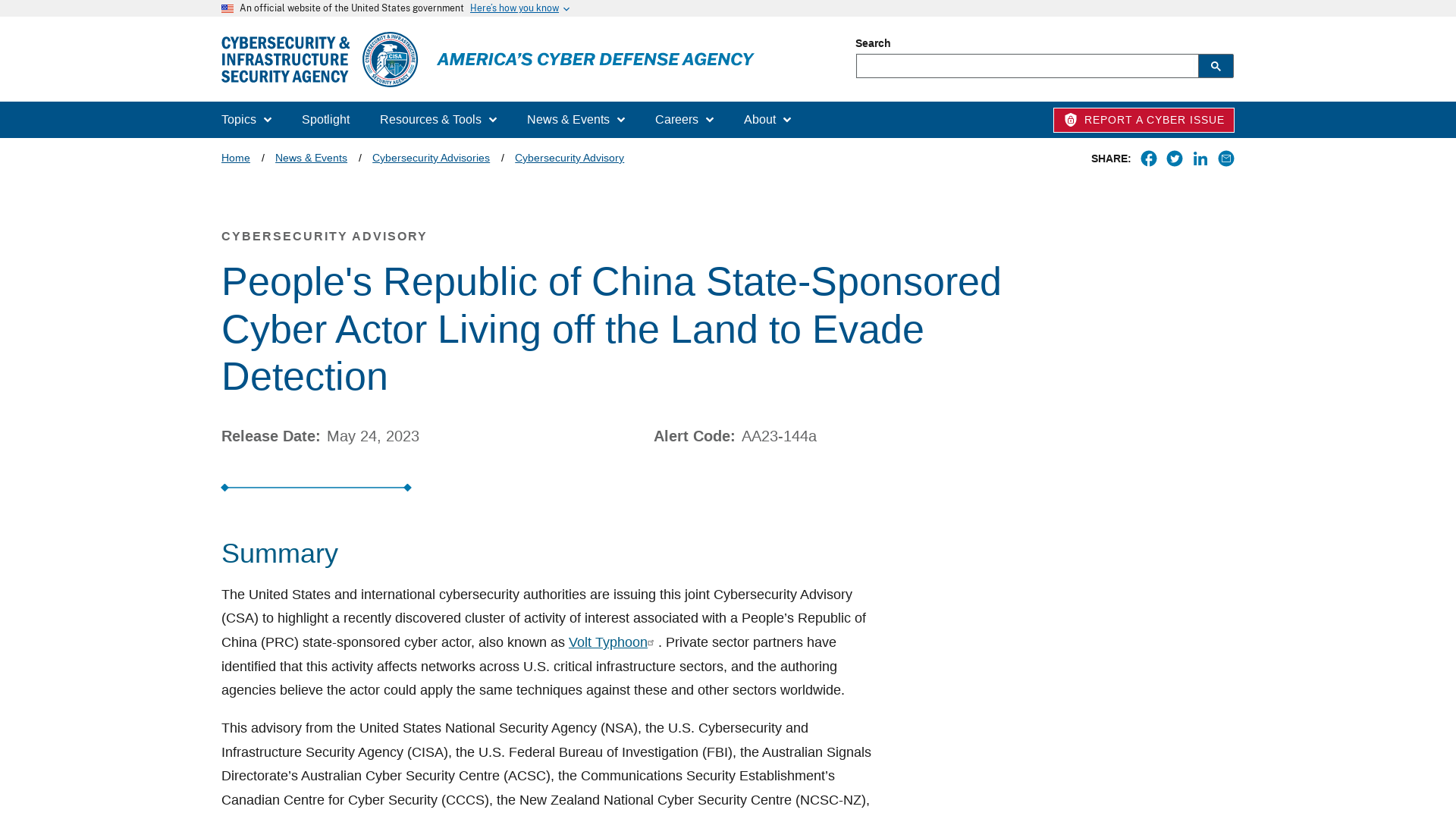
CVE-2022-3723: Logic Issue in Turbofan JIT Compiler | 0-days In-the-Wild
https://googleprojectzero.github.io/0days-in-the-wild//0day-RCAs/2022/CVE-2022-3723.html
ESET Research on Twitter: "#ESETResearch warns about a CPIO archive named “Jump Crypto Investment https://t.co/Er3H0htWQ2” uploaded to VirusTotal from the USA 🇺🇸. It is another malicious PDF viewer distributed by #Lazarus #APT for #macOS https://t.co/hGGJS9PI8G @pkalnai @michalmalik 1/7 https://t.co/Zb9F4lpS7u" / Twitter
https://twitter.com/ESETresearch/status/1656385173968019456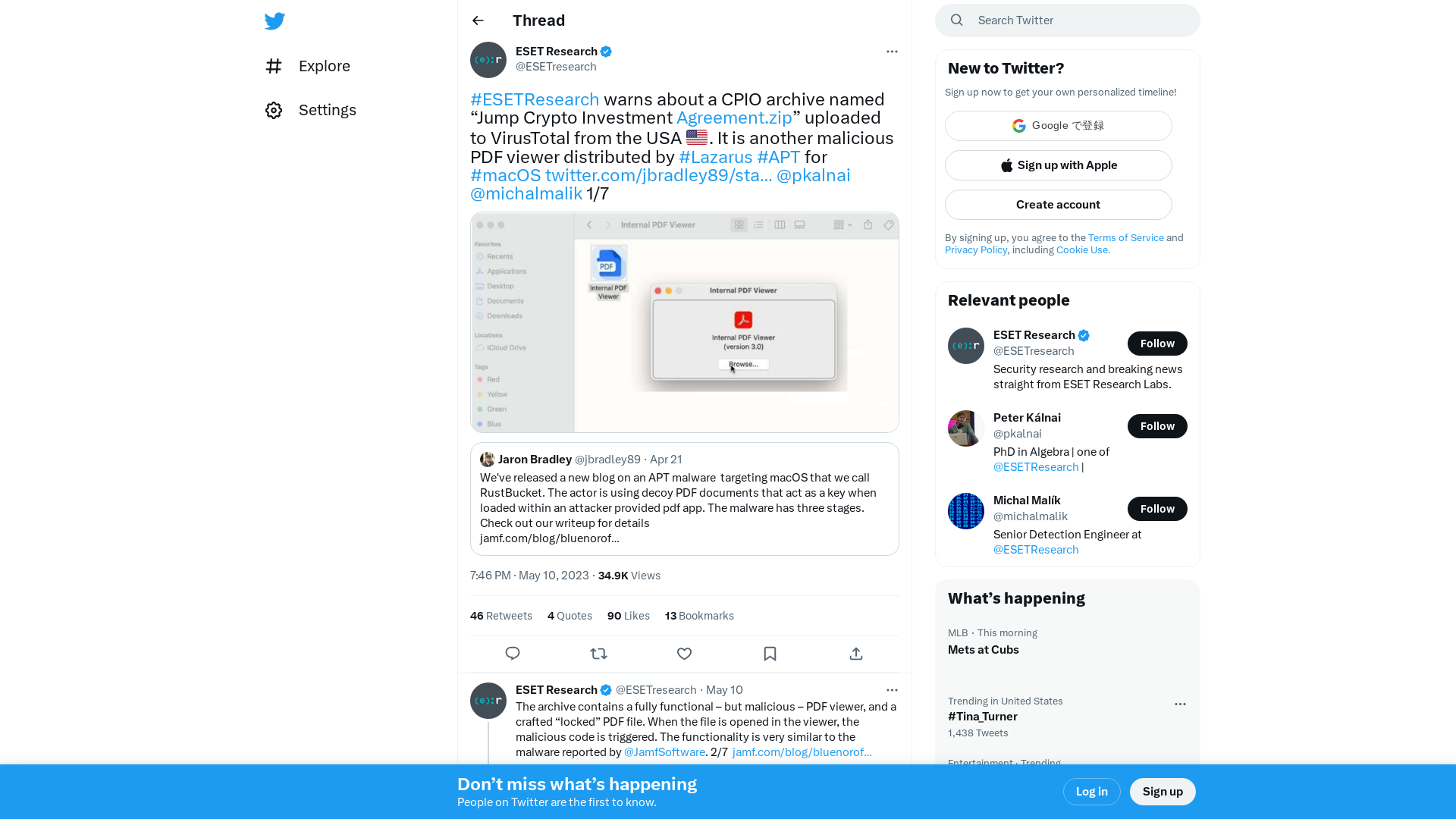
Operation "Total Exchange": New PowerExchange Backdoor Discovered in the UAE | FortiGuard Labs
https://www.fortinet.com/blog/threat-research/operation-total-exchange-backdoor-discovered
Infecting SSH Public Keys with backdoors
https://blog.thc.org/infecting-ssh-public-keys-with-backdoors
GitLab 'strongly recommends' patching max severity flaw ASAP
https://www.bleepingcomputer.com/news/security/gitlab-strongly-recommends-patching-max-severity-flaw-asap/
Free VPN Service SuperVPN Exposes 360 Million User Records
https://www.hackread.com/free-vpn-service-supervpn-leaks-user-records/
COSMICENERGY: New OT Malware Possibly Related To Russian Emergency Response Exercises | Mandiant
https://www.mandiant.com/resources/blog/cosmicenergy-ot-malware-russian-response
BSidesCharm 2023 - AD and DNS: A Match Made in Heck - Jim Sykora and Jake Hildreth - YouTube
https://youtu.be/QSRxrTXj8G0
The Dark Frost Enigma: An Unexpectedly Prevalent Botnet Author Profile | Akamai
https://www.akamai.com/blog/security-research/dark-frost-botnet-unexpected-author-profile
China's Stealthy Hackers Infiltrate U.S. and Guam Critical Infrastructure Undetected
https://thehackernews.com/2023/05/chinas-stealthy-hackers-infiltrate-us.html
Special Offer for Asia Pacific Students | SANS Online Training
https://www.sans.org/u/1qM7
Special Offer for Asia Pacific Students | SANS Online Training
https://www.sans.org/u/1qGD
SANSFIRE Washington, DC 2023 | Cyber Security Training
https://www.sans.org/u/1opv
Barracuda Email Security Gateway (ESG) hacked via zero-day bugSecurity Affairs
https://securityaffairs.com/146620/hacking/barracuda-email-security-gateway-bug.html
Mercenary mayhem: A technical analysis of Intellexa's PREDATOR spyware
https://blog.talosintelligence.com/mercenary-intellexa-predator/

Rooting with root cause: finding a variant of a Project Zero bug | The GitHub Blog
https://github.blog/2023-05-25-rooting-with-root-cause-finding-a-variant-of-a-project-zero-bug/
New Buhti ransomware gang uses leaked Windows, Linux encryptors
https://www.bleepingcomputer.com/news/security/new-buhti-ransomware-gang-uses-leaked-windows-linux-encryptors/
Buhti: New Ransomware Operation Relies on Repurposed Payloads | Symantec Enterprise Blogs
https://symantec-enterprise-blogs.security.com/blogs/threat-intelligence/buhti-ransomware
Malware/Qilin at main · rivitna/Malware · GitHub
https://github.com/rivitna/Malware/tree/main/Qilin
‘Operation Magalenha’ targets credentials of 30 Portuguese banks
https://www.bleepingcomputer.com/news/security/operation-magalenha-targets-credentials-of-30-portuguese-banks/
Ransomchats Viewer
https://ransomch.at/
Volt Typhoon targets US critical infrastructure with living-off-the-land techniques | Microsoft Security Blog
https://www.microsoft.com/en-us/security/blog/2023/05/24/volt-typhoon-targets-us-critical-infrastructure-with-living-off-the-land-techniques/
Chinese Cyberespionage Group BRONZE SILHOUETTE Targets U.S. Government and Defense Organizations | Secureworks
https://www.secureworks.com/blog/chinese-cyberespionage-group-bronze-silhouette-targets-us-government-and-defense-organizations
Buhti Ransomware Gang Switches Tactics, Utilizes Leaked LockBit and Babuk Code
https://thehackernews.com/2023/05/buhti-ransomware-gang-switches-tactics.html
Neutralize threats before Impact
http://Sekoia.io
Exclusive: Russian hypersonic scientist accused of betraying secrets to China | Reuters
https://www.reuters.com/world/russian-hypersonic-scientist-accused-betraying-secrets-china-sources-2023-05-24/
Daily Cyber Briefing - Thursday 25th May / Twitter
https://twitter.com/i/broadcasts/1vOxwMagbVbGB
Four Key GDPR Trends on the Law’s Fifth Anniversary - Infosecurity Magazine
https://www.infosecurity-magazine.com/news-features/gdpr-trends-fifth-anniversary/
RFC: Enforcing Bounds Safety in C (-fbounds-safety) - Clang Frontend - LLVM Discussion Forums
https://discourse.llvm.org/t/rfc-enforcing-bounds-safety-in-c-fbounds-safety/70854
How to start reviewing code?. Too often (me included), savvy code… | by PentesterLab | PentesterLab
https://blog.pentesterlab.com/how-to-start-reviewing-code-bc39df869140
the tiny corp raised $5.1M | the singularity is nearer
https://geohot.github.io/blog/jekyll/update/2023/05/24/the-tiny-corp-raised-5M.html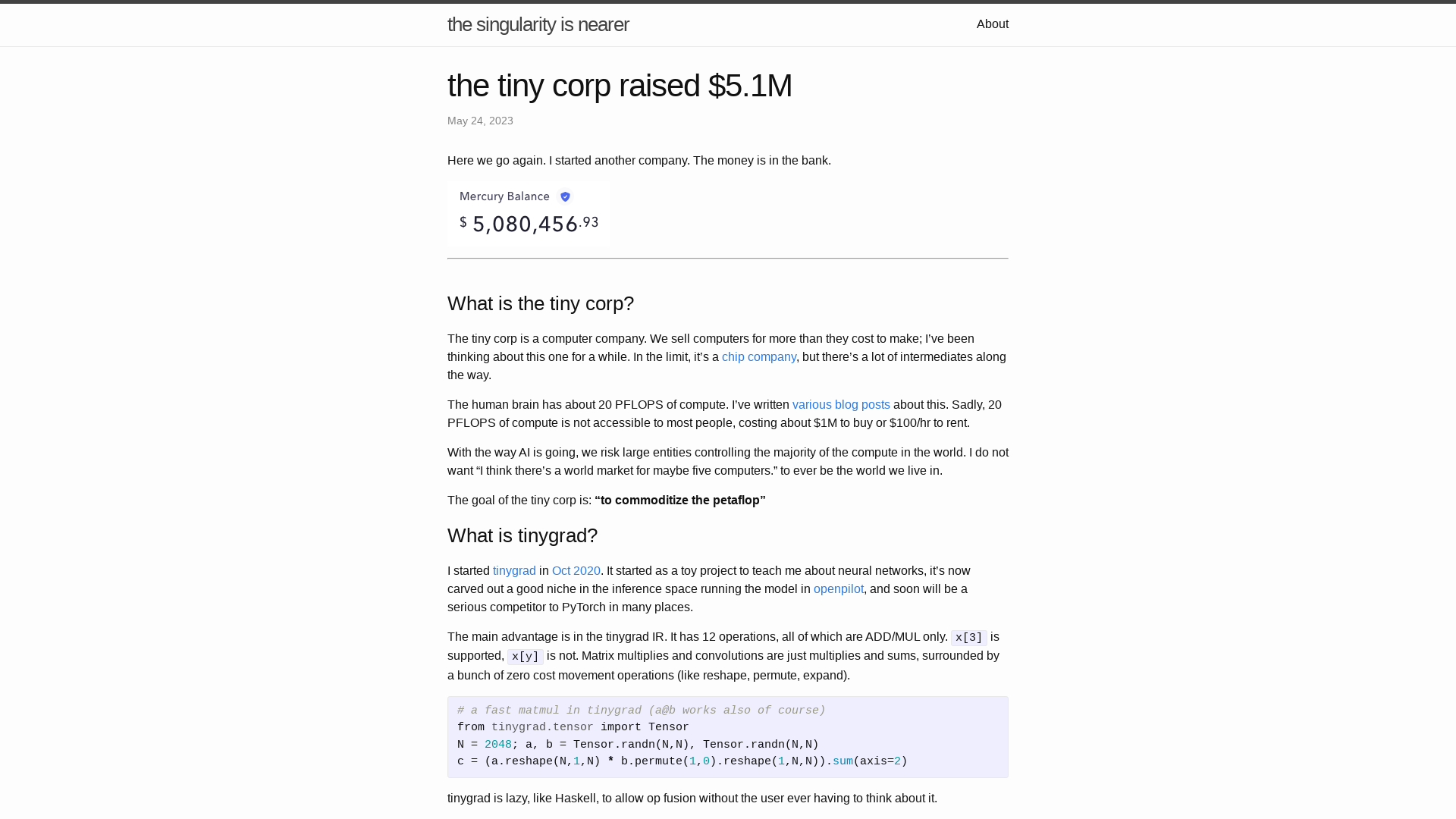
New PowerExchange malware backdoors Microsoft Exchange servers
https://www.bleepingcomputer.com/news/security/new-powerexchange-malware-backdoors-microsoft-exchange-servers/