Gozi - Italian ShellCode Dance - 0xToxin Labs
https://0xtoxin-labs.gitbook.io/malware-analysis/malware-analysis/gozi-italian-shellcode-dance
ScrubCrypt - The Rebirth of Jlaive - 0xToxin Labs
https://0xtoxin-labs.gitbook.io/malware-analysis/malware-analysis/scrubcrypt-the-rebirth-of-jlaive
Emotet malware now distributed in Microsoft OneNote files to evade defenses
https://www.bleepingcomputer.com/news/security/emotet-malware-now-distributed-in-microsoft-onenote-files-to-evade-defenses/
Exploiting aCropalypse: Recovering Truncated PNGs | Blog
https://www.da.vidbuchanan.co.uk/blog/exploiting-acropalypse.html
Bypassing PPL in Userland (again) – Sec Team Blog
https://blog.scrt.ch/2023/03/17/bypassing-ppl-in-userland-again/
Simon Aarons on Twitter: "Introducing acropalypse: a serious privacy vulnerability in the Google Pixel's inbuilt screenshot editing tool, Markup, enabling partial recovery of the original, unedited image data of a cropped and/or redacted screenshot. Huge thanks to @David3141593 for his help throughout! https://t.co/BXNQomnHbr" / Twitter
https://twitter.com/ItsSimonTime/status/1636857478263750656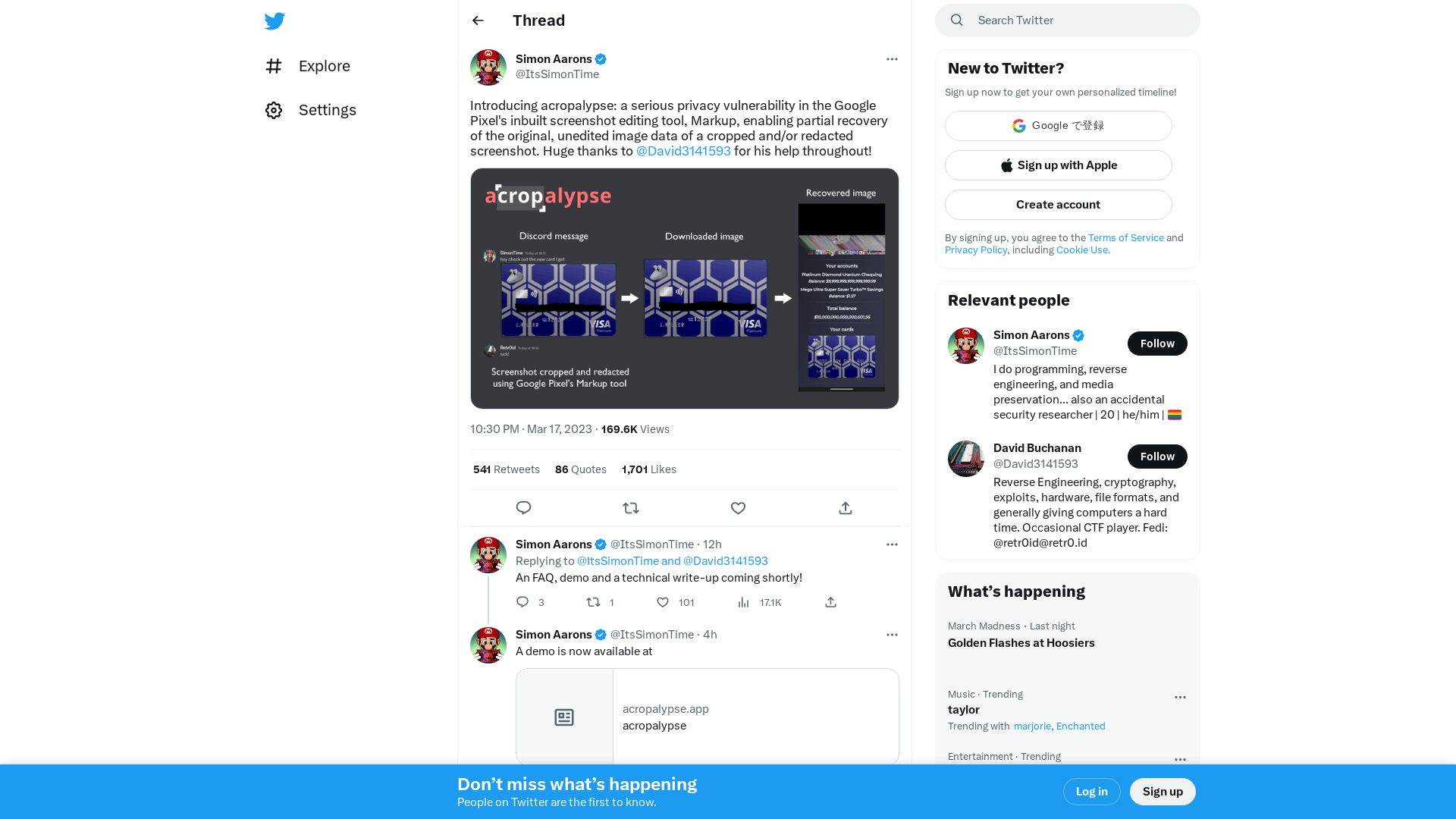
2023 Conference Information – PancakesCon 4
https://pancakescon.com/2023-conference-information/
GitHub - hackerhouse-opensource/iscsicpl_bypassUAC: UAC bypass for x64 Windows 7 - 11
https://github.com/hackerhouse-opensource/iscsicpl_bypassUAC
Chinese Hackers Exploit Fortinet Zero-Day Flaw for Cyber Espionage Attack
https://thehackernews.com/2023/03/chinese-hackers-exploit-fortinet-zero.html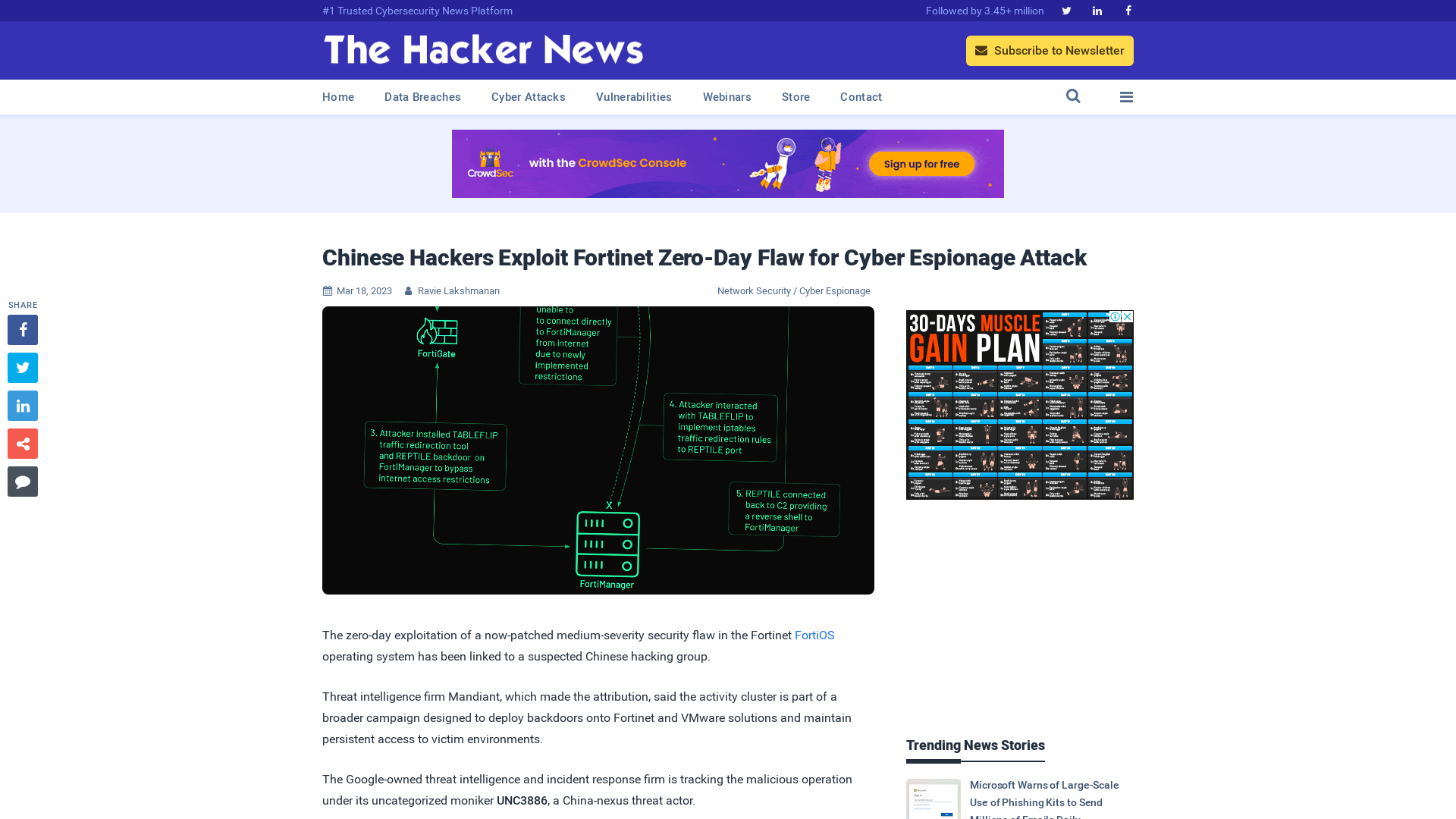
Women in CyberSecurity (WiCyS) on Twitter: "Dust off your boots and grab your cowboy hats! WE’LL SEE Y’ALL IN NASHVILLE! 🤠👢⭐️ #WiCyS2024 https://t.co/Y14rHF2YF7" / Twitter
https://twitter.com/wicysorg/status/1637181227177476098
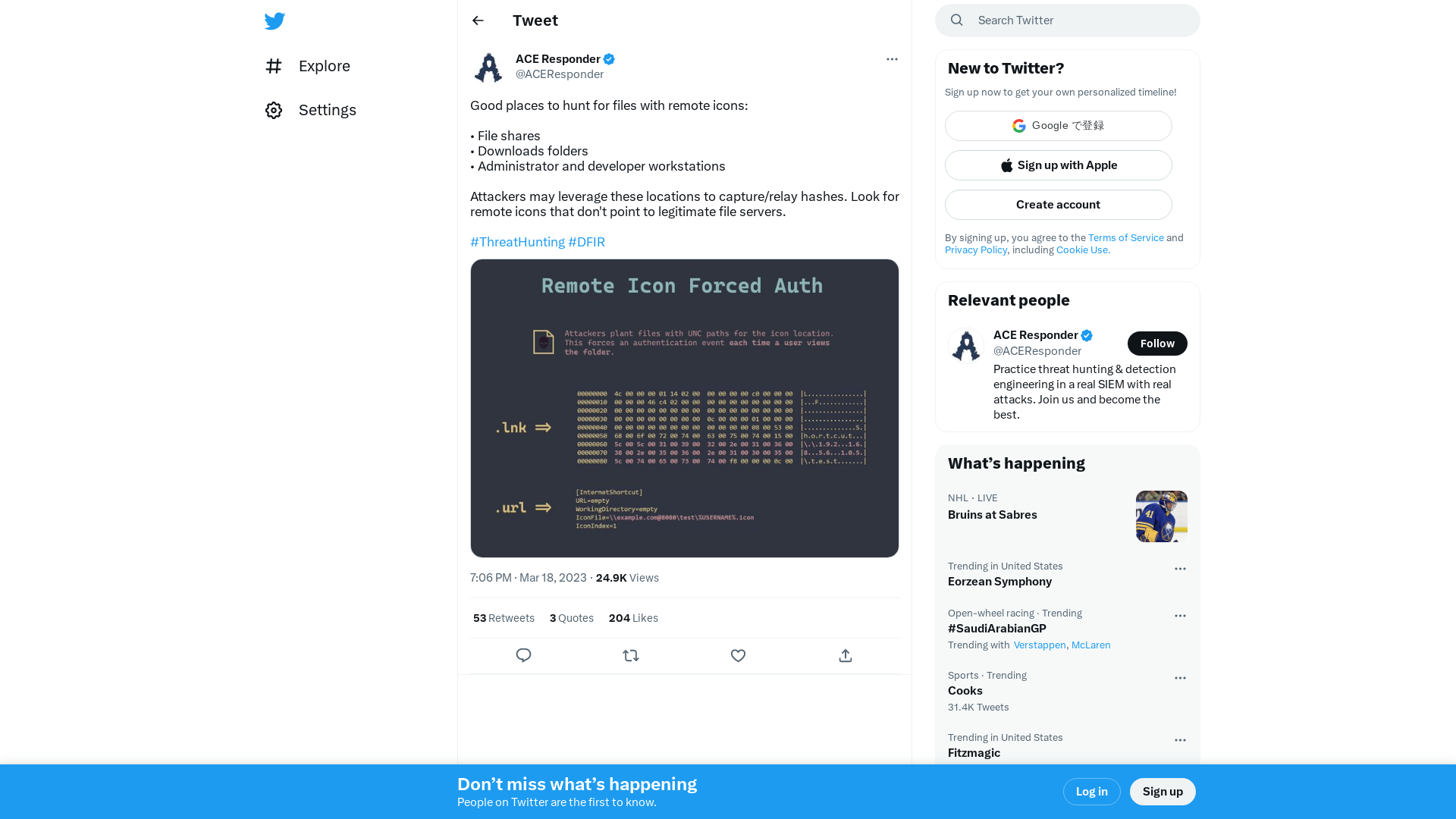
ACE Responder on Twitter: "Good places to hunt for files with remote icons: • File shares • Downloads folders • Administrator and developer workstations Attackers may leverage these locations to capture/relay hashes. Look for remote icons that don't point to legitimate file servers. #ThreatHunting… https://t.co/11H1eFrtC3" / Twitter
https://twitter.com/i/web/status/1637168533086904320