Bypassing PPL in Userland (again) – Sec Team Blog
https://blog.scrt.ch/2023/03/17/bypassing-ppl-in-userland-again/
GitHub - itm4n/PPLmedic: Dump the memory of any PPL with a Userland exploit chain
https://github.com/itm4n/PPLmedic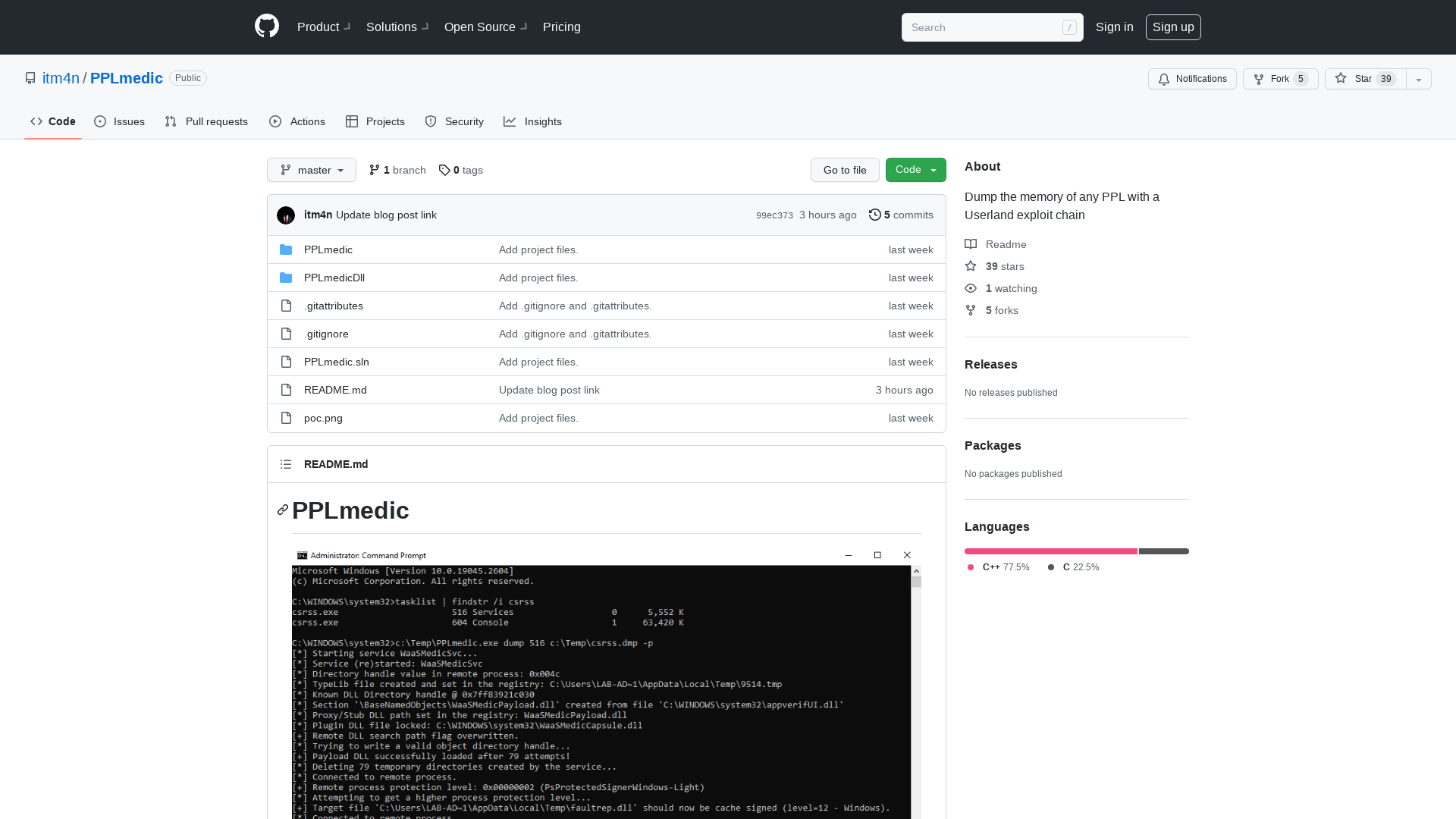
Fortinet Zero-Day and Custom Malware Used by Suspected Chinese Actor in Espionage Operation | Mandiant
https://www.mandiant.com/resources/blog/fortinet-malware-ecosystem
Project Zero: Samsung Mobile Chipsets Vulnerable to Baseband Code Execution Exploits - SecurityWeek
https://www.securityweek.com/project-zero-samsung-mobile-chipsets-vulnerable-to-baseband-code-execution-exploits/
CVE-2023-23397 - Bypass on Vimeo
https://vimeo.com/809084317
Project Zero: Multiple Internet to Baseband Remote Code Execution Vulnerabilities in Exynos Modems
https://googleprojectzero.blogspot.com/2023/03/multiple-internet-to-baseband-remote-rce.html
Peeking at Reaper’s surveillance operations - SEKOIA.IO Blog
https://blog.sekoia.io/peeking-at-reaper-surveillance-operations-against-north-korea-defectors/
GitHub - outflanknl/C2-Tool-Collection: A collection of tools which integrate with Cobalt Strike (and possibly other C2 frameworks) through BOF and reflective DLL loading techniques.
https://github.com/outflanknl/C2-Tool-Collection
Lookalike Telegram and WhatsApp Websites Distributing Cryptocurrency Stealing Malware
https://thehackernews.com/2023/03/lookalike-telegram-and-whatsapp.html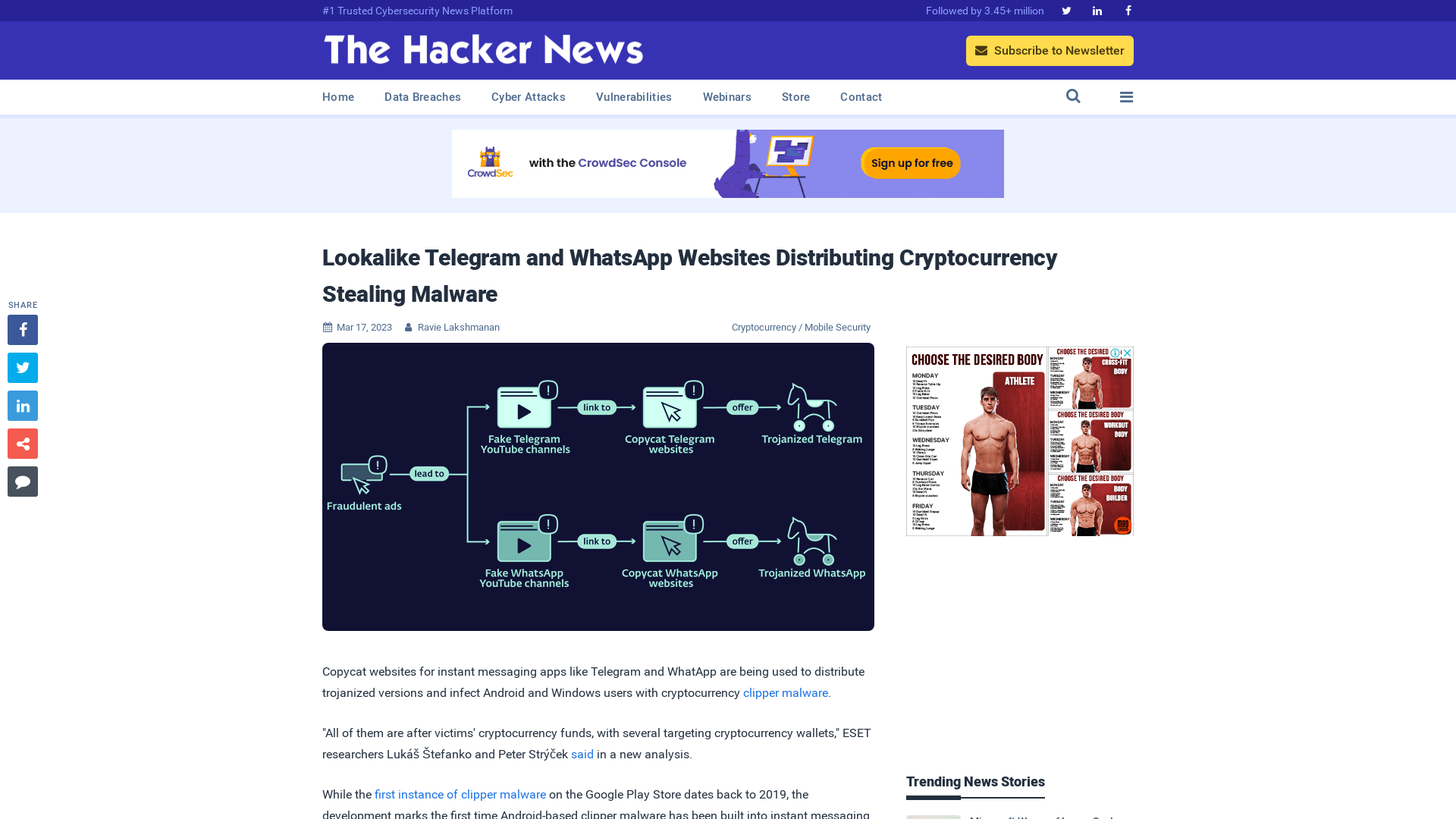
sigma/proc_creation_win_rundll32_webdav_client_susp_execution.yml at master · SigmaHQ/sigma · GitHub
https://github.com/SigmaHQ/sigma/blob/master/rules/windows/process_creation/proc_creation_win_rundll32_webdav_client_susp_execution.yml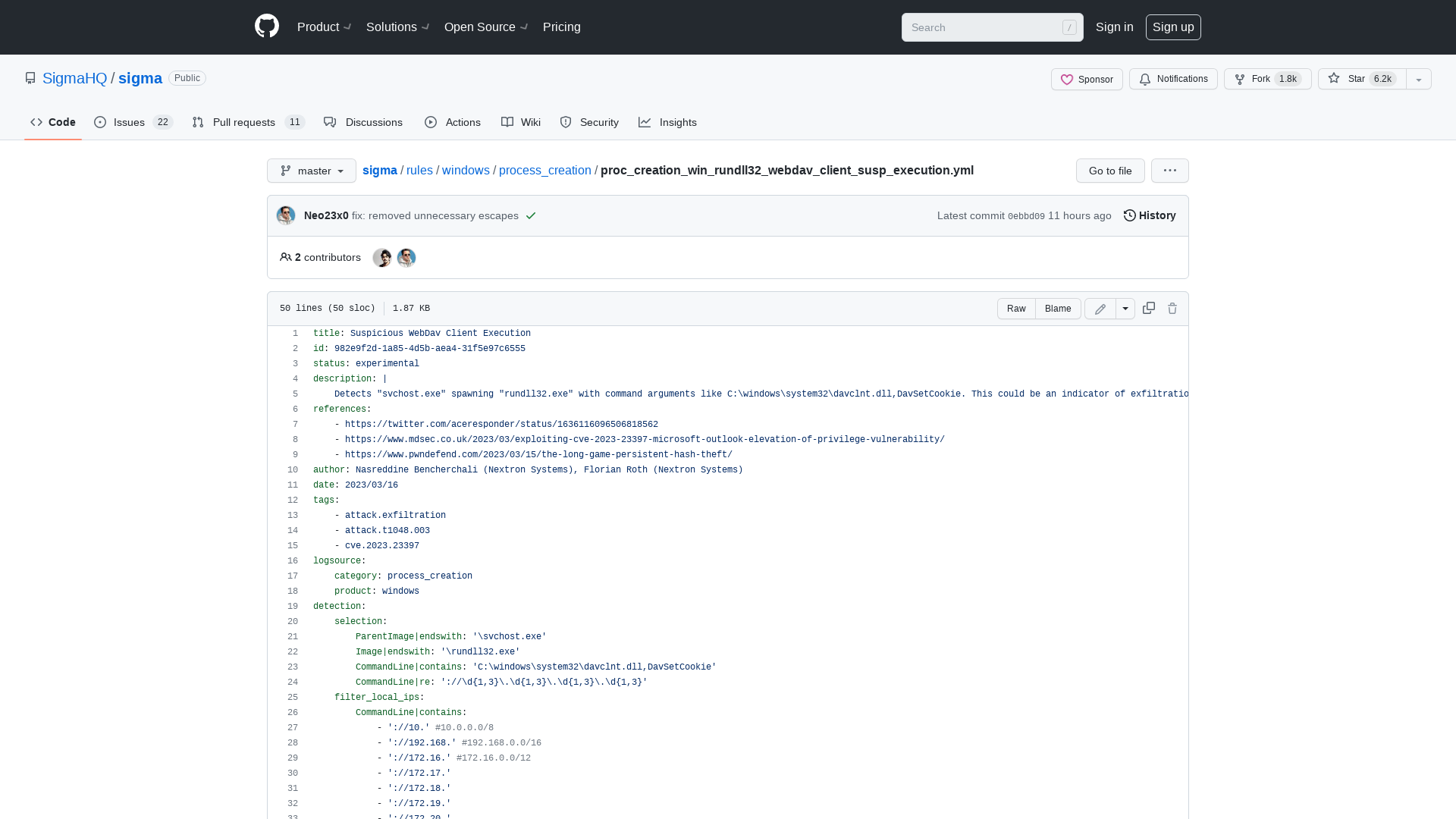
https://raw.githubusercontent.com/CronUp/EnAnalisis/main/2023-03-17_Emotet_Stats
https://raw.githubusercontent.com/CronUp/EnAnalisis/main/2023-03-17_Emotet_Stats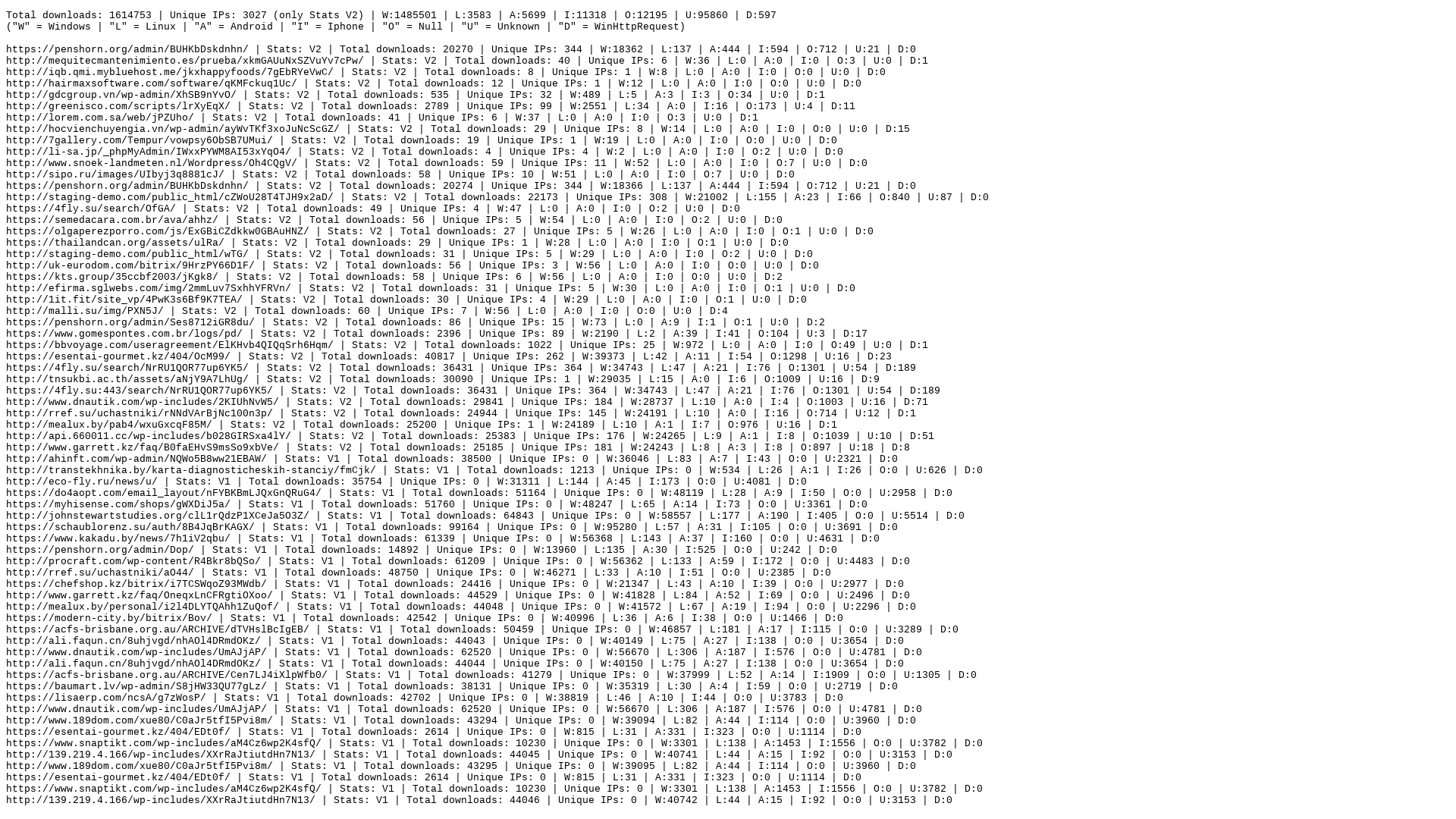
Talos uncovers espionage campaigns targeting CIS countries, embassies and EU health care agency
https://blog.talosintelligence.com/yorotrooper-espionage-campaign-cis-turkey-europe/