Stealing the LIGHTSHOW (Part One) — North Korea's UNC2970 | Mandiant
https://www.mandiant.com/resources/blog/lightshow-north-korea-unc2970
Making HTTP header injection critical via response queue poisoning | PortSwigger Research
https://portswigger.net/research/making-http-header-injection-critical-via-response-queue-poisoning
Central District of California | Federal Authorities Seize Internet Domain Selling Malware Used to Illegally Control and Steal Data from Victims’ Computers | United States Department of Justice
https://www.justice.gov/usao-cdca/pr/federal-authorities-seize-internet-domain-selling-malware-used-illegally-control-and
Apache HTTP Server 2.4 vulnerabilities - The Apache HTTP Server Project
https://httpd.apache.org/security/vulnerabilities_24.html#2.4.56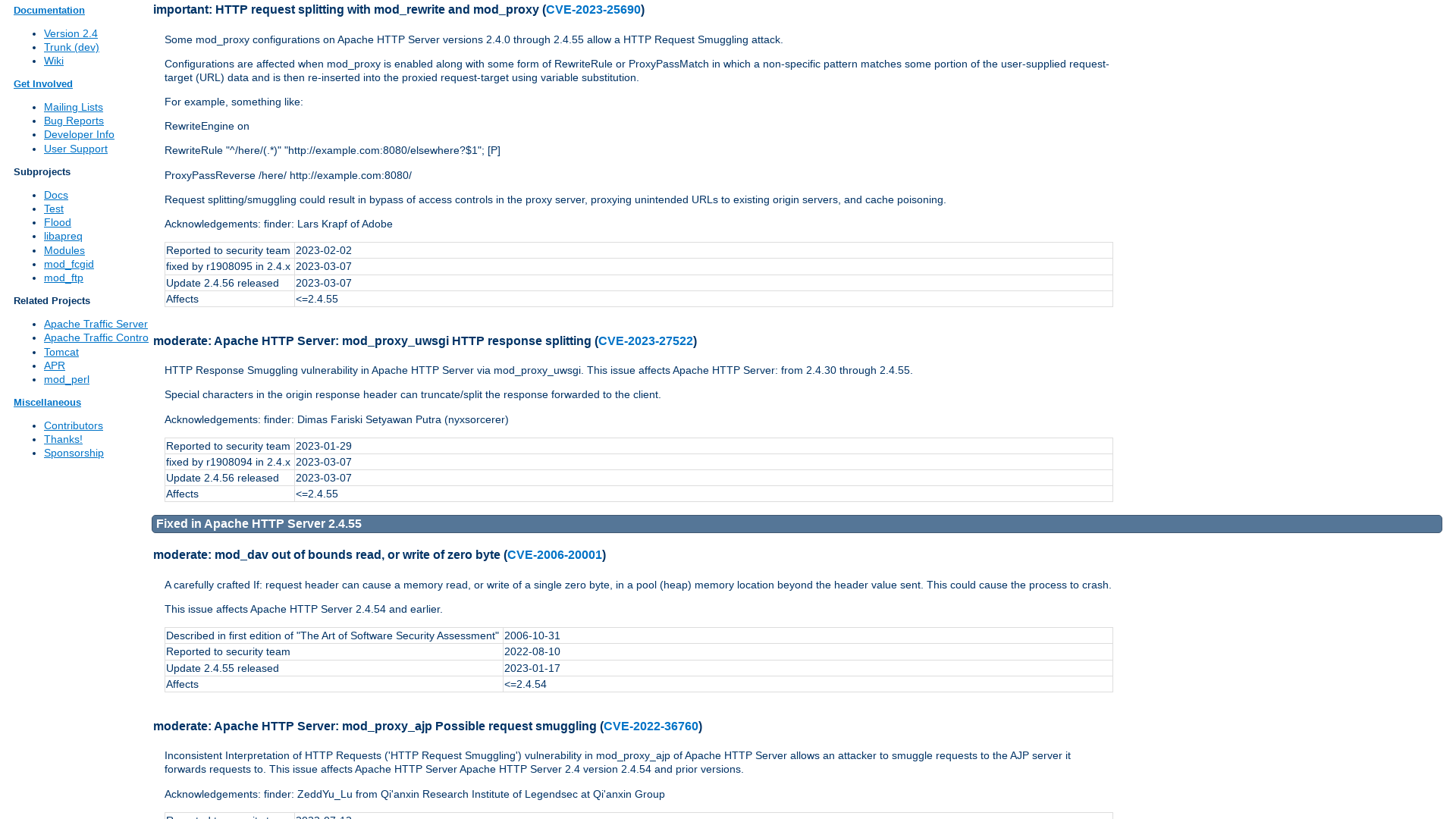
Qakbot/Qakbot_BB18_10.03.2023.txt at main · pr0xylife/Qakbot · GitHub
https://github.com/pr0xylife/Qakbot/blob/main/Qakbot_BB18_10.03.2023.txt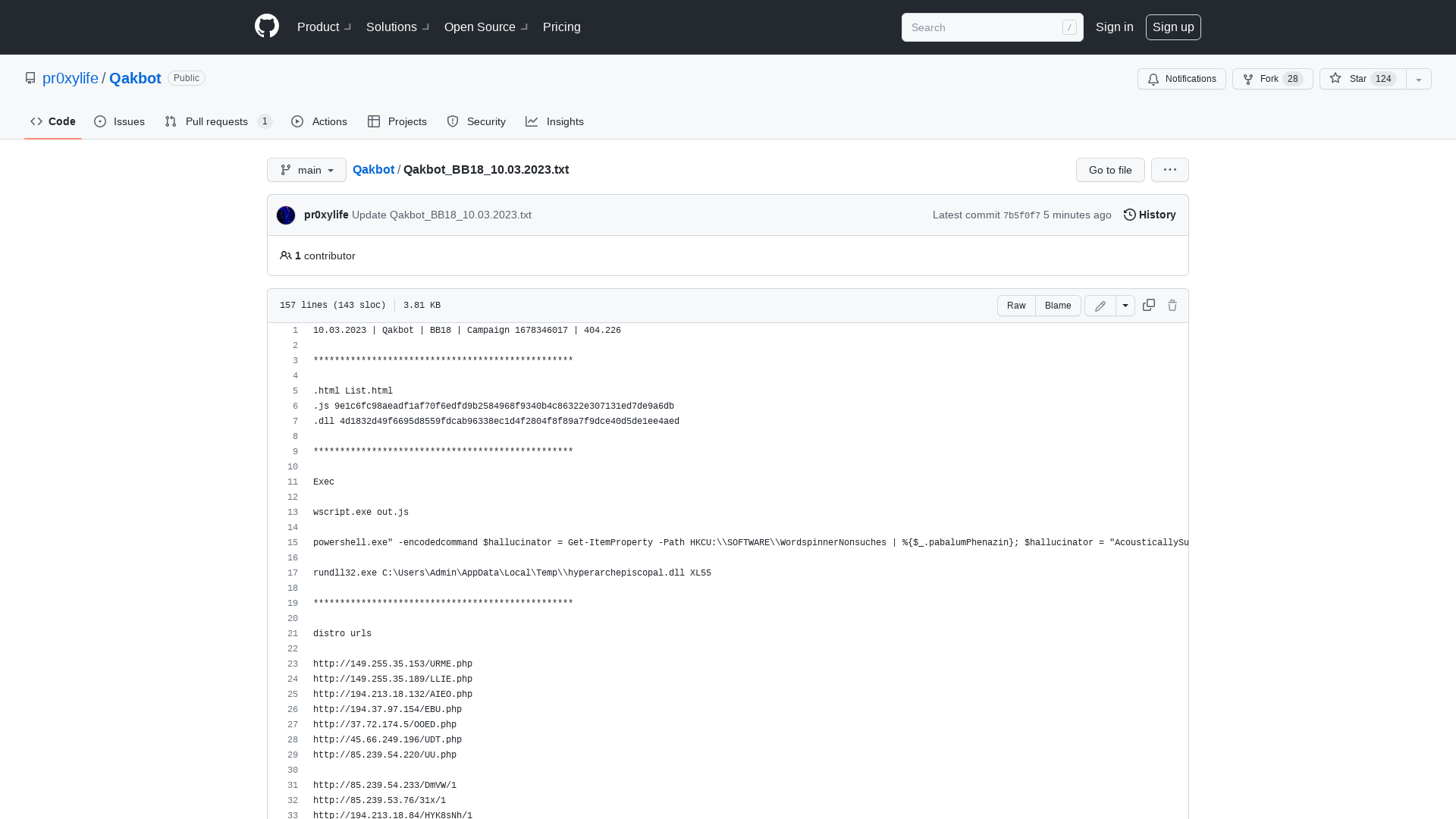
RussianPanda 🐼 🇺🇦 on Twitter: "We have been observing #BatLoader 🦇 using batch files to: ➡️ Install Python 3.9.9 ➡️ Use pip to install pywin32 and wmi packages. ➡️ Unpack the compressed OpenSSL library files using PowerShell ➡️ Launching Python scripts obfuscated with PyArmor https://t.co/s9wNDbaxLU… https://t.co/MUbTODWl4z" / Twitter
https://twitter.com/i/web/status/1634091931868209152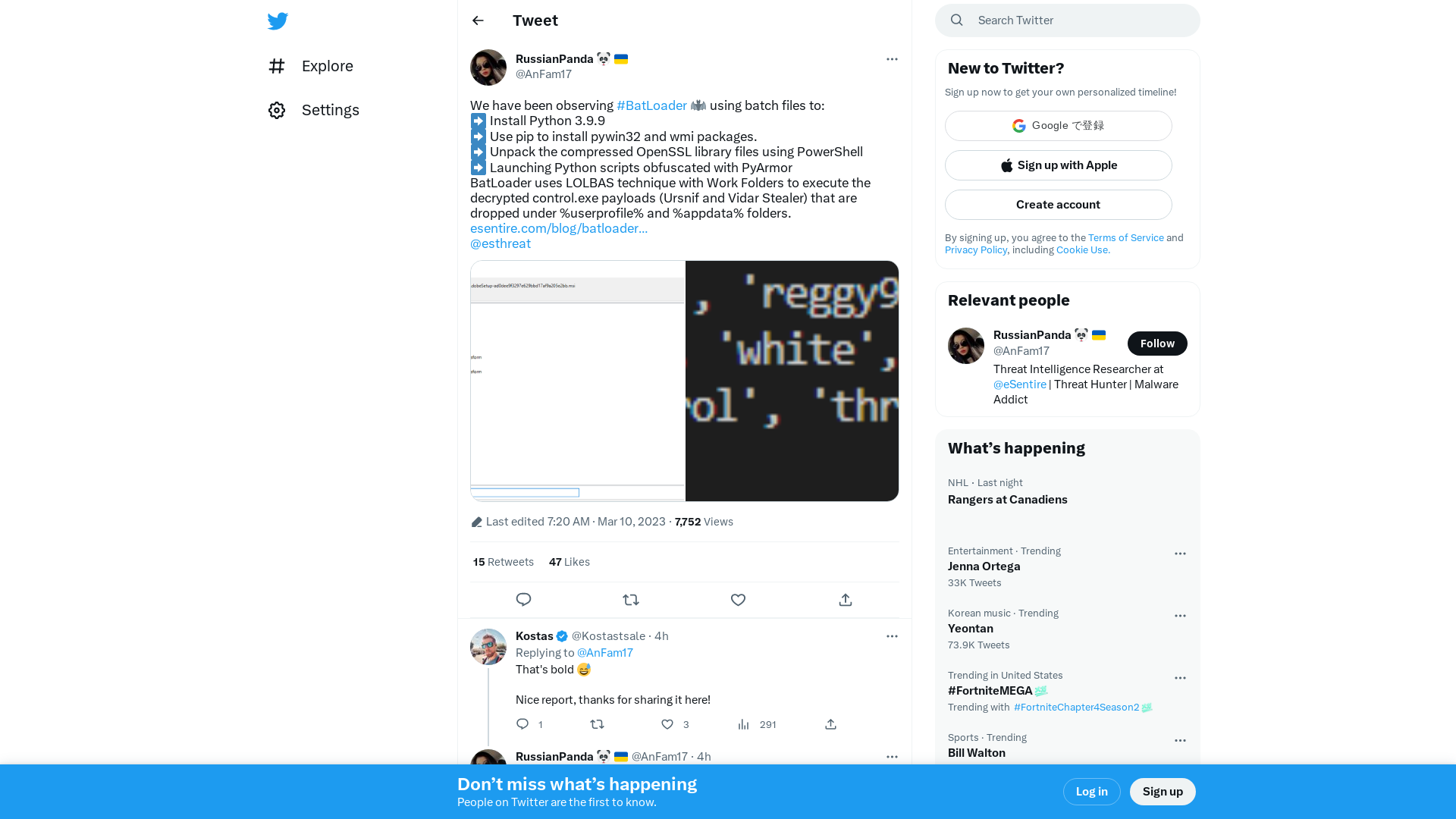
PwnAgent: A One-Click WAN-side RCE in Netgear RAX Routers with CVE-2023-24749
https://mahaloz.re/2023/02/25/pwnagent-netgear.html
eSentire | BatLoader Continues to Abuse Google Search Ads to Deliver…
https://www.esentire.com/blog/batloader-continues-to-abuse-google-search-ads-to-deliver-vidar-stealer-and-ursnif
Defining the Cobalt Strike Reflective Loader
https://securityintelligence.com/posts/defining-cobalt-strike-reflective-loader/
AT&T alerts 9 million customers of data breach after vendor hack
https://www.bleepingcomputer.com/news/security/atandt-alerts-9-million-customers-of-data-breach-after-vendor-hack/
Security researchers targeted with new malware via job offers on LinkedIn
https://www.bleepingcomputer.com/news/security/security-researchers-targeted-with-new-malware-via-job-offers-on-linkedin/
MalwareBazaar | Browse Checking your browser
https://bazaar.abuse.ch/sample/befeb1ab986fae9a54d4761d072bf50fdbff5c6b1b89b66a6790a3f0bfc4243f/
GitHub - xforcered/Windows_LPE_AFD_CVE-2023-21768: LPE exploit for CVE-2023-21768
https://github.com/xforcered/Windows_LPE_AFD_CVE-2023-21768
Who’s Behind the NetWire Remote Access Trojan? – Krebs on Security
https://krebsonsecurity.com/2023/03/whos-behind-the-netwire-remote-access-trojan/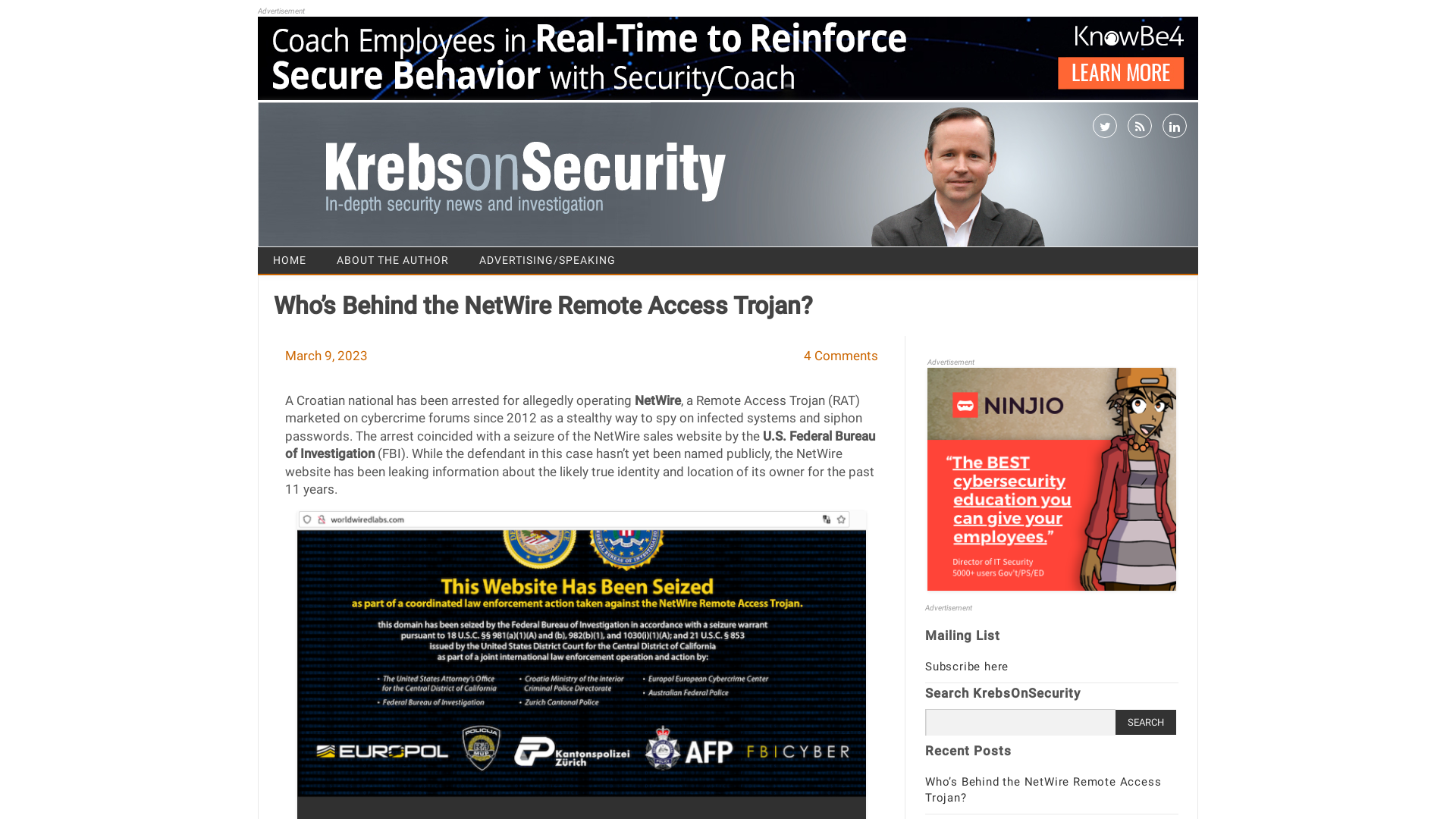
Markus Wulftange on Twitter: "@wdormann @codewhitesec Passwords are stored encrypted using DataProtectionScope.LocalMachine. But they get decrypted during serialization of the CCredentials object before transit. So, yes, the client receives the passwords in plaintext as depicted. https://t.co/bBlFM1iRJx" / Twitter
https://twitter.com/mwulftange/status/1634091601944363010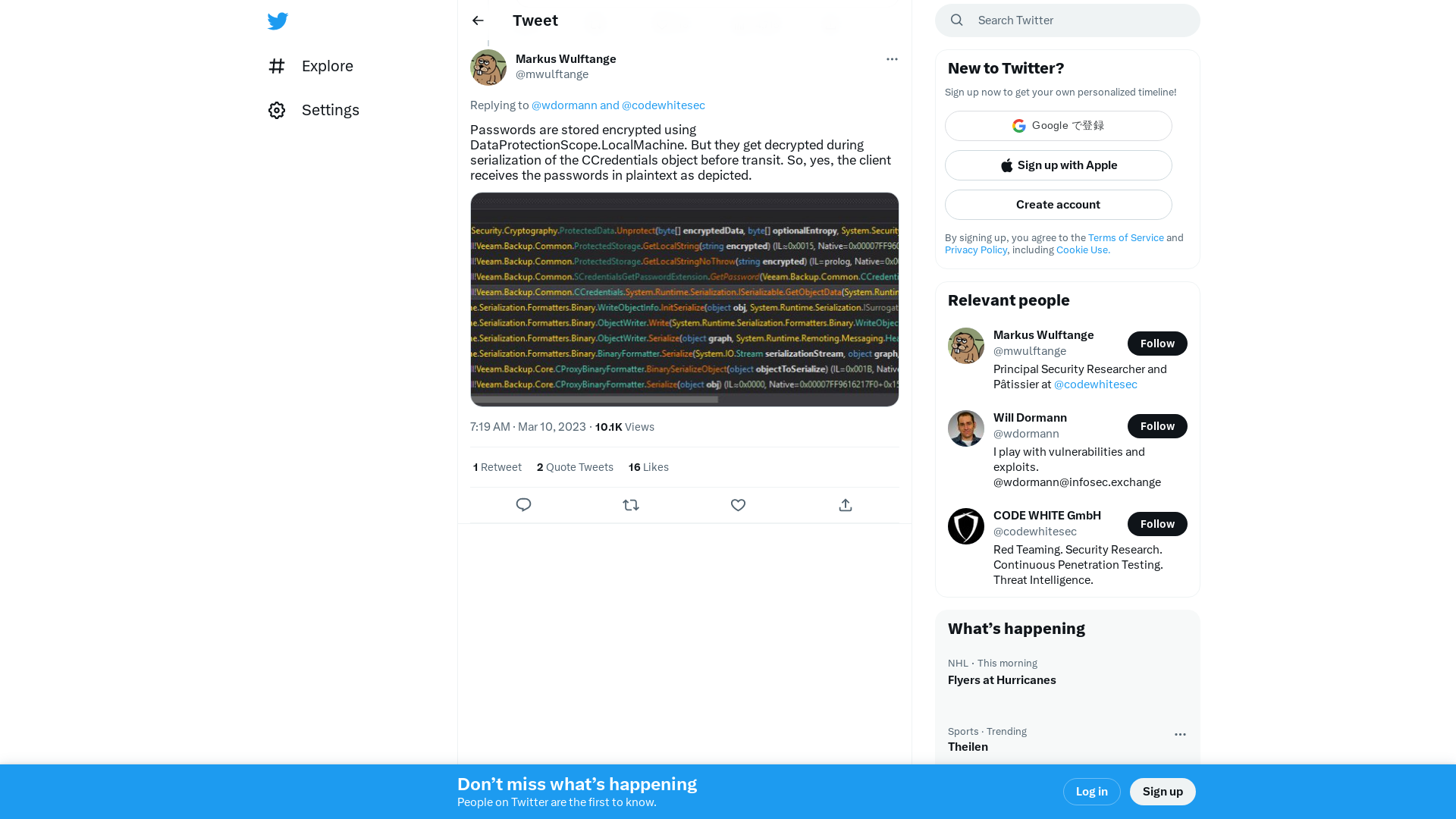
Malware-Traffic-Analysis.net - 2023-03-08 - IcedID (Bokbot) infection with BackChannel and VNC traffic
https://www.malware-traffic-analysis.net/2023/03/08/index.html
Police seize Netwire RAT malware infrastructure, arrest admin
https://www.bleepingcomputer.com/news/security/police-seize-netwire-rat-malware-infrastructure-arrest-admin/