Lord Of The Ring0 - Part 4 | The call back home - Ido Veltzman - Security Blog
https://idov31.github.io/2023/02/24/lord-of-the-ring0-p4.html
[email protected] - Stand with 🇺🇦 on Twitter: "I know this isn’t news to most people, but having never before had a Microsoft branded keyboard, I was shocked to see the pop-a-calc button for those times when your RCE POC live demo isn’t quite going as planned. 💡Now I know why exploit writers spawn calc as a demo 😆 https://t.co/f77DlVm63N" / Twitter
https://twitter.com/rpargman/status/1632139906196832257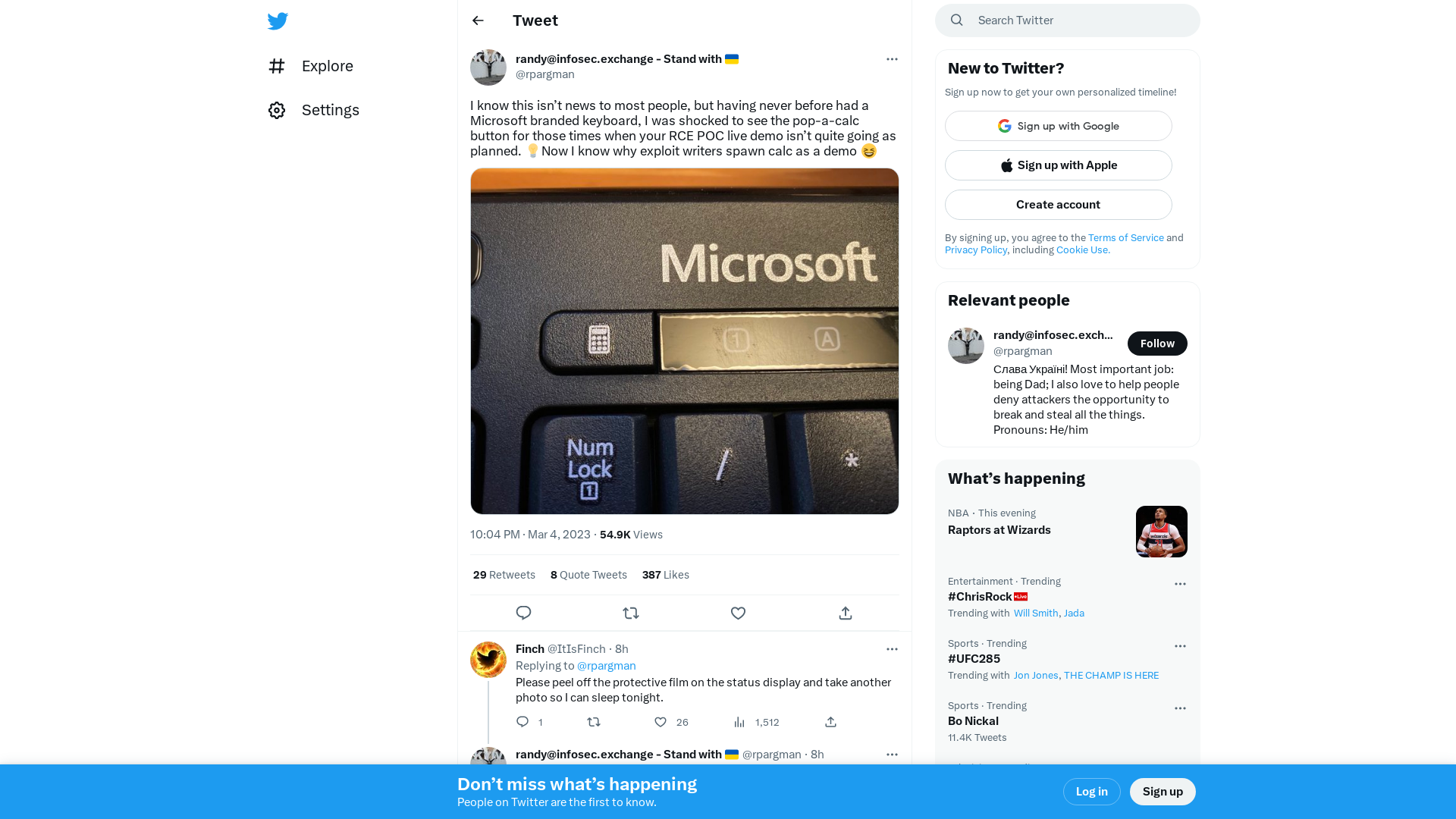
Josh on Twitter: "It's insane that Meterpreter + the Metasploit backend is a jawdroppingly complex piece of malware that many of us could (and do) learn so much from, but people call it shit because the default artifacts are sigged by Defender" / Twitter
https://twitter.com/passthehashbrwn/status/1630978329074454528
Obfuscating Rubeus using Codecepticon
https://www.pavel.gr/blog/obfuscating-rubeus-using-codecepticon
https://www.sans.org/u/1p3q
https://www.sans.org/u/1p3q
Vic: Home Edition on Twitter: "And now, something a bit different- Myself and @0xLegacyy are doing the Big Sleep Out to raise money for @JulianHouseUK! Last year we raised £820, please help us reach our goal of £500 this year 🙌 https://t.co/31iELnGP37" / Twitter
https://twitter.com/VicHarkness/status/1628450523174121474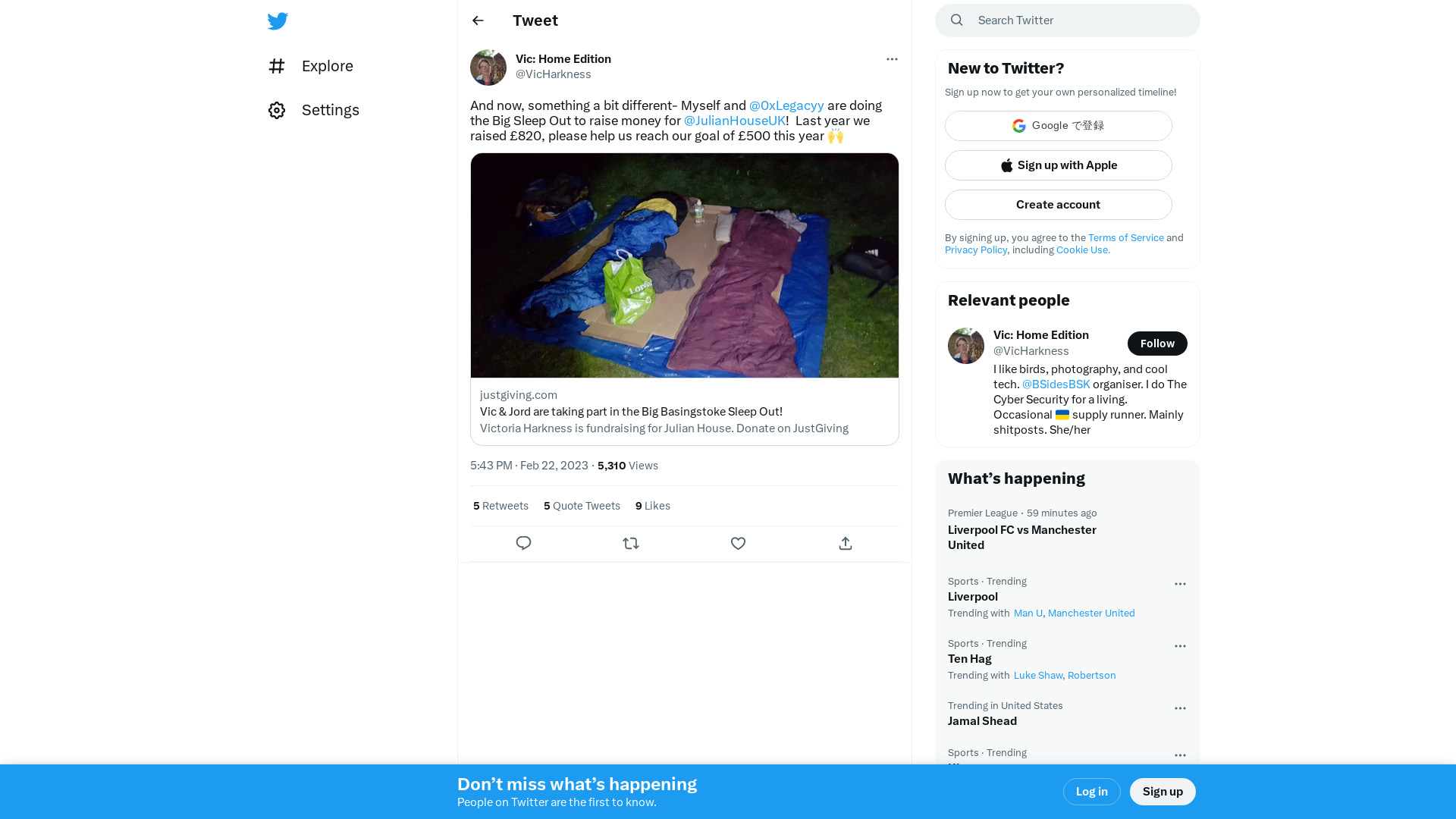
New TPM 2.0 flaws could let hackers steal cryptographic keys
https://www.bleepingcomputer.com/news/security/new-tpm-20-flaws-could-let-hackers-steal-cryptographic-keys/
What really is the Entry Point of a .NET Module? | Washi
https://washi.dev/blog/posts/entry-points/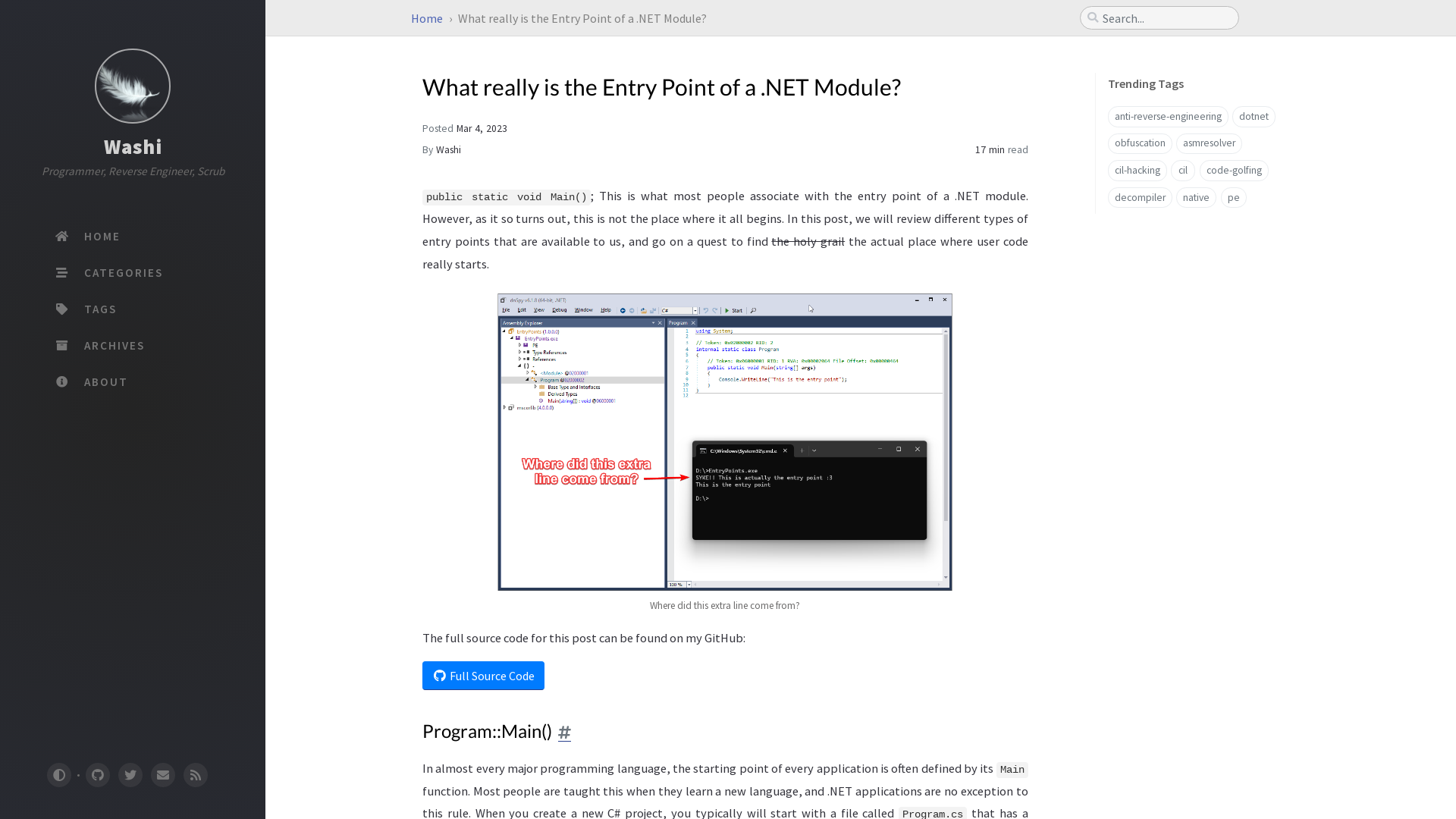
ARM 64 Assembly Series — Data Processing (Part 1) | by +Ch0pin🕷️ | Medium
https://valsamaras.medium.com/arm-64-assembly-series-data-processing-part-1-b6f6f877c56b
Introduction to x64 Linux Binary Exploitation (Part 4)- Stack Canaries | by +Ch0pin🕷️ | Medium
https://valsamaras.medium.com/introduction-to-x64-linux-binary-exploitation-part-4-stack-canaries-e9b6dd2c3127
Police Are Getting Help From Social Media Sites to Prosecute People for Abortion
https://www.businessinsider.com/police-getting-help-social-media-to-prosecute-people-seeking-abortions-2023-2
(PDF) A brief note on "Exonerating Morocco disproving the spyware"
https://www.researchgate.net/publication/368985450_A_brief_note_on_Exonerating_Morocco_disproving_the_spyware
Introduction to x64 Linux Binary Exploitation (Part 5)- ASLR | by +Ch0pin🕷️ | Medium
https://valsamaras.medium.com/introduction-to-x64-linux-binary-exploitation-part-5-aslr-394d0dc8e4fb
ARM 64 Assembly Series — Branch. Previous posts: Basic definitions and… | by +Ch0pin🕷️ | Medium
https://valsamaras.medium.com/arm-64-assembly-series-branch-9ce820987fc6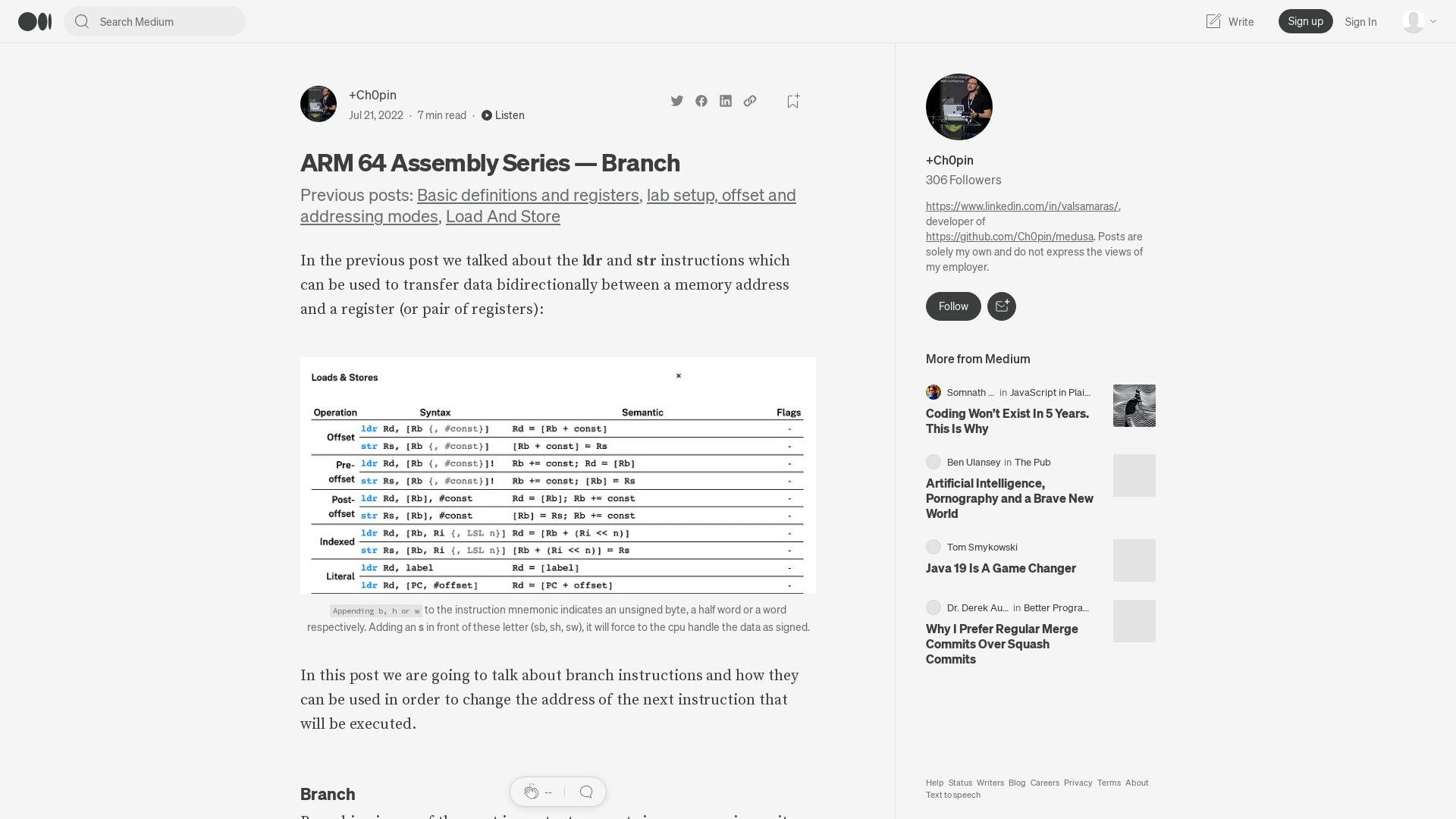
From on-prem to Global Admin without password reset - Cloudbrothers
https://cloudbrothers.info/en/prem-global-admin-password-reset/
Introduction to x64 Linux Binary Exploitation (Part 2)—return into libc | by +Ch0pin🕷️ | Medium
https://valsamaras.medium.com/introduction-to-x64-binary-exploitation-part-2-return-into-libc-c325017f465
https://pastebin.com/raw/Bk1hu2d6
https://pastebin.com/raw/Bk1hu2d6
Introduction to x64 Linux Binary Exploitation (Part 1) | by +Ch0pin🕷️ | Medium
https://valsamaras.medium.com/introduction-to-x64-linux-binary-exploitation-part-1-14ad4a27aeef
Having fun with KeePass2: DLL Hijacking and hooking APIs | Cyberdough
https://skr1x.github.io/keepass-dll-hijacking/
Week 10 – 2023 – This Week In 4n6
http://thisweekin4n6.com/2023/03/05/week-10-2023/
Introduction to x64 Linux Binary Exploitation (Part 3)- RoP Chains | by +Ch0pin🕷️ | Medium
https://valsamaras.medium.com/introduction-to-x64-linux-binary-exploitation-part-3-rop-chains-3cdcf17e8826
A New Vector For “Dirty” Arbitrary File Write to RCE · Doyensec's Blog
https://blog.doyensec.com//2023/02/28/new-vector-for-dirty-arbitrary-file-write-2-rce.html
diaphora/compilation_units.md at master · joxeankoret/diaphora · GitHub
https://github.com/joxeankoret/diaphora/blob/master/doc/articles/compilation_units.md
The Red Report 2023.pdf - Google ドライブ
https://drive.google.com/file/d/1Rp2QF4e5-zvdtPJApaiRQEGtscweb8SV/view
New FiXS ATM Malware Targeting Mexican Banks
https://thehackernews.com/2023/03/new-fixs-atm-malware-targeting-mexican.html
ARM 64 Assembly Series— Basic definitions and registers | by +Ch0pin🕷️ | Medium
https://valsamaras.medium.com/arm-64-assembly-series-basic-definitions-and-registers-ec8cc1334e40
ARM 64 Assembly Series — Load and Store | by +Ch0pin🕷️ | Medium
https://valsamaras.medium.com/arm-64-assembly-series-load-and-store-6bfe9c1d1896
ARM 64 Assembly Series — Offset and Addressing modes | by +Ch0pin🕷️ | Medium
https://valsamaras.medium.com/arm-64-assembly-series-offset-and-addressing-modes-aa48b65b4c99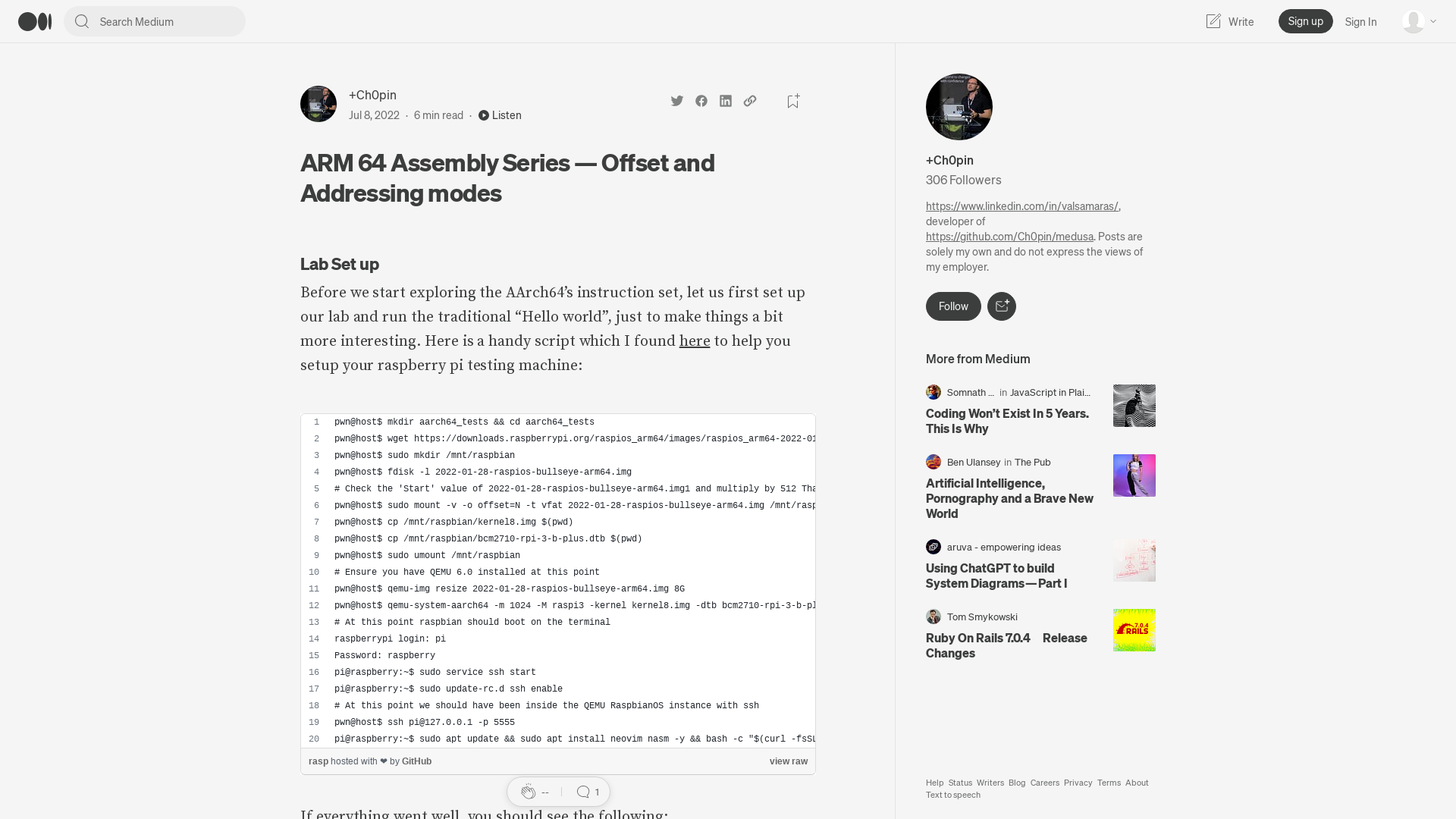
fucked up looking computers on Twitter: "https://t.co/cfTxMrrygU" / Twitter
https://twitter.com/fuckeduppcs/status/1632004967988105217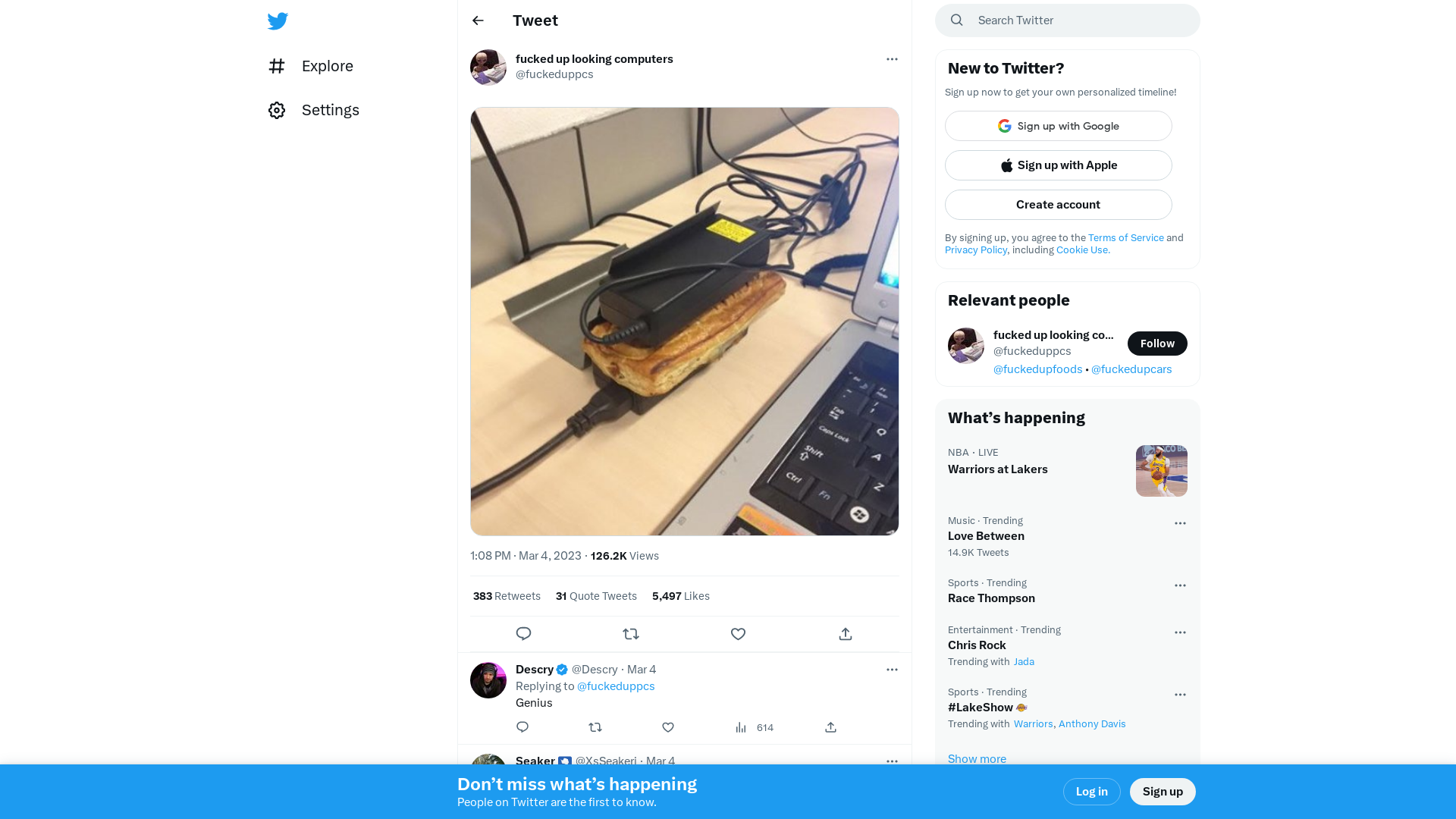
Bypass TCC via iCloud
https://wojciechregula.blog/post/bypass-tcc-via-icloud/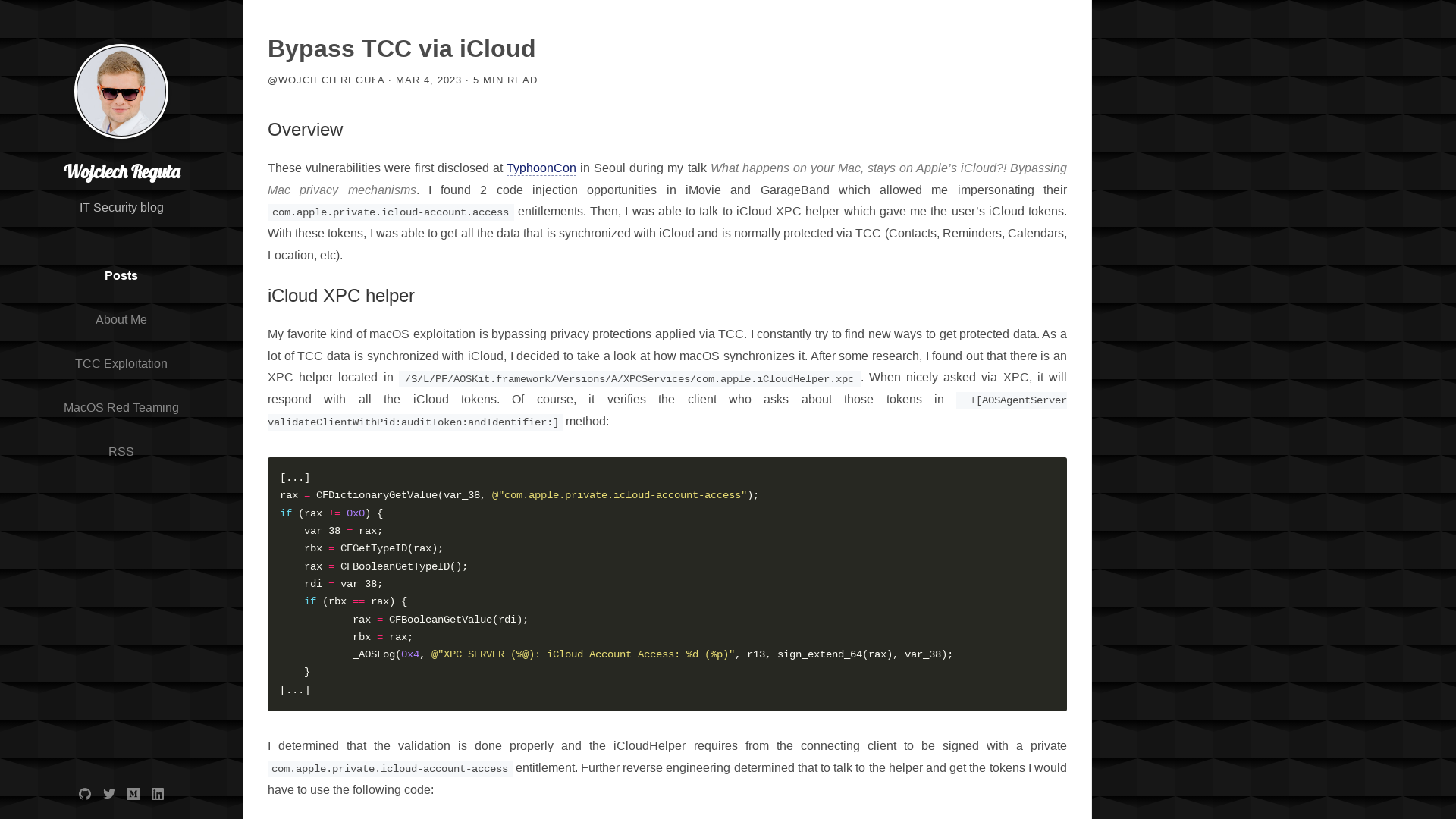
#1847140 Argo CD reconciles apps outside configured namespaces when sharding is enabled
https://hackerone.com/reports/1847140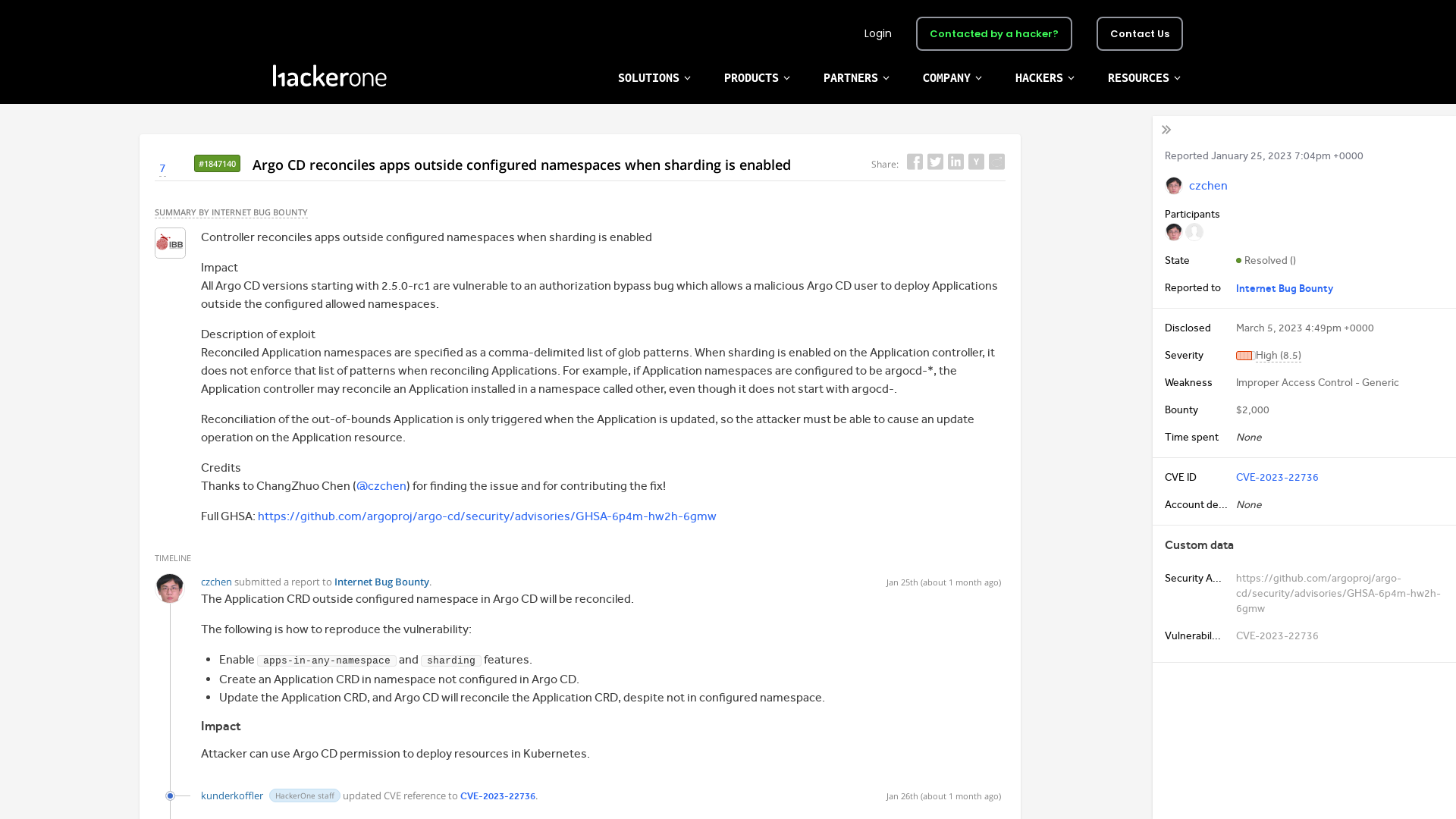
FiXS, a new ATM malware that is targeting Mexican banksSecurity Affairs
https://securityaffairs.com/143022/malware/fixs-atm-malware-mexican-banks.html
Table of Geographical Locations - Win32 apps | Microsoft Learn
https://learn.microsoft.com/en-us/windows/win32/intl/table-of-geographical-locations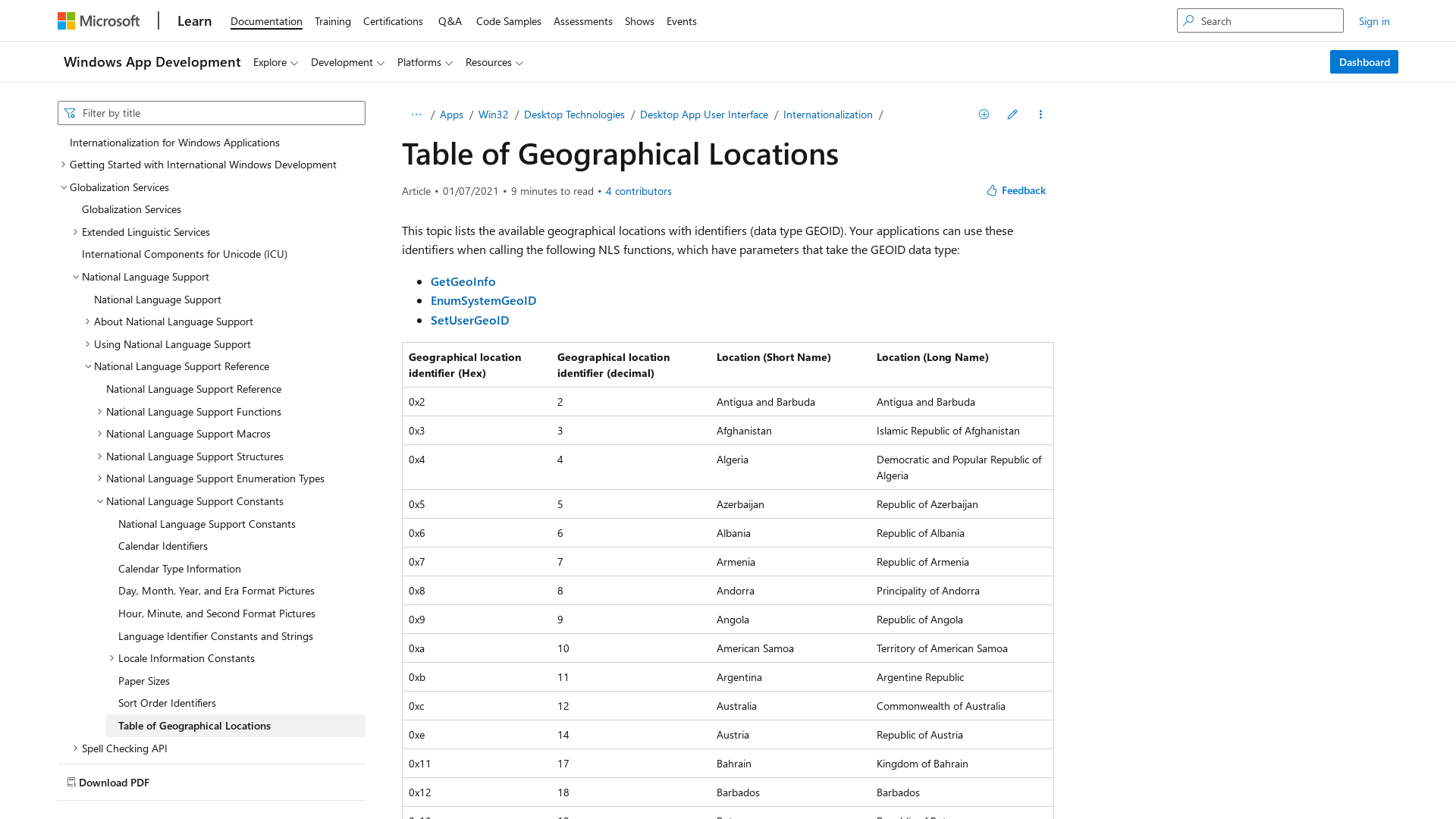
Remote Code Execution via Prototype Pollution in Blitz.js | Sonar
https://www.sonarsource.com/blog/blitzjs-prototype-pollution/
Thousands of websites hacked as part of redirection campaignSecurity Affairs
https://securityaffairs.com/142975/hacking/ftp-credentials-traffic-redirection-campaign.html
FiXS the new ATM Malware in LATAM - Metabase Q
https://www.metabaseq.com/fixs-atms-malware/
GitHub - 0xor0ne/flipperbit: Corrupted files generator. Random bits flipper.
https://github.com/0xor0ne/flipperbit
GitHub Security Lab audited DataHub: Here's what they found | The GitHub Blog
https://github.blog/2023-03-03-github-security-lab-audited-datahub-heres-what-they-found/
VirusTotal - File - 6019120f81c432820354fd7763baa7c6bd4611e92813a8b0e5edf0a342472f16
https://www.virustotal.com/gui/file/6019120f81c432820354fd7763baa7c6bd4611e92813a8b0e5edf0a342472f16/details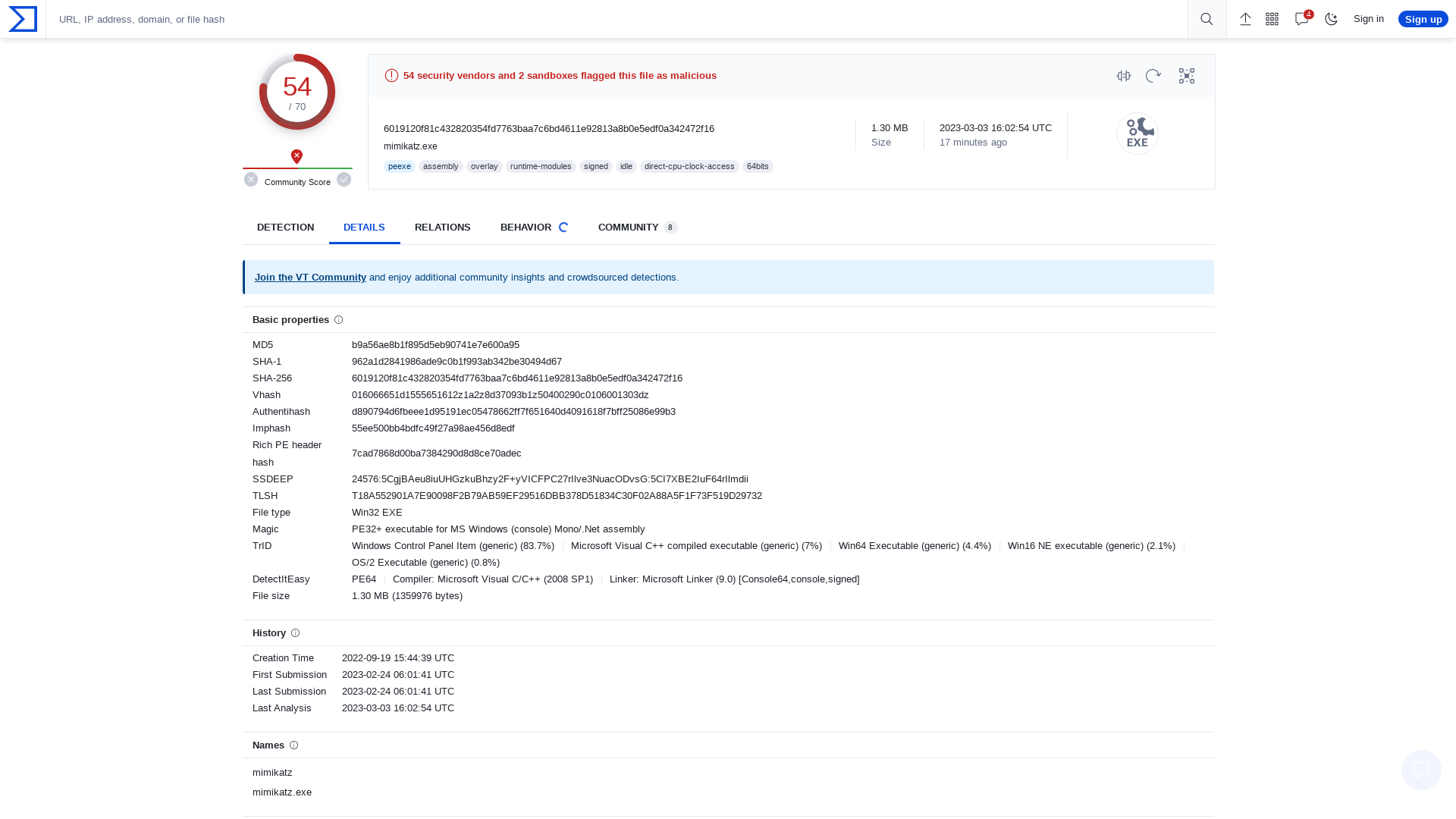
DCP Podcast on Twitter: ""A lot of times we let our sensor's limitations be the limitations of our thinking..." -@jaredcatkinson, Episode 29: Olaf Hartong. Full episode available at https://t.co/N4KxCBps6Y or wherever you consume podcasts! #infosecurity #infosec #detection #detectionengineering https://t.co/GqKTnIFFz5" / Twitter
https://twitter.com/dcpthepodcast/status/1632410647354052610
SANS Threat Hunting London 2023 - Cyber security training courses - London, UK | SANS Institute
https://www.sans.org/u/1pcx