Dissecting and Exploiting TCP/IP RCE Vulnerability “EvilESP”
https://securityintelligence.com/posts/dissecting-exploiting-tcp-ip-rce-vulnerability-evilesp/
GitHub - tijme/amd-ryzen-master-driver-v17-exploit: Cobalt Strike (CS) Beacon Object File (BOF) for kernel exploitation using AMD's Ryzen Master Driver (version 17).
https://github.com/tijme/amd-ryzen-master-driver-v17-exploit
CVE-2022-41033: Type confusion in Windows COM+ Event System Service | 0-days In-the-Wild
https://googleprojectzero.github.io/0days-in-the-wild//0day-RCAs/2022/CVE-2022-41033.html
GitHub - TurtleARM/CVE-2023-0179-PoC
https://github.com/TurtleARM/CVE-2023-0179-PoC
Technical Advisory – U-Boot – Unchecked Download Size and Direction in USB DFU (CVE-2022-2347) – NCC Group Research
https://research.nccgroup.com/2023/01/20/technical-advisory-u-boot-unchecked-download-size-and-direction-in-usb-dfu-cve-2022-2347/
晏子霜 on Twitter: "My first submitted poc can trigger on the latest windows, but Microsoft refused to pay an additional bounty because the submitted version number was not a preview. This is very unreasonable https://t.co/Vj3116mZDb" / Twitter
https://twitter.com/YanZiShuang/status/1616160317226254336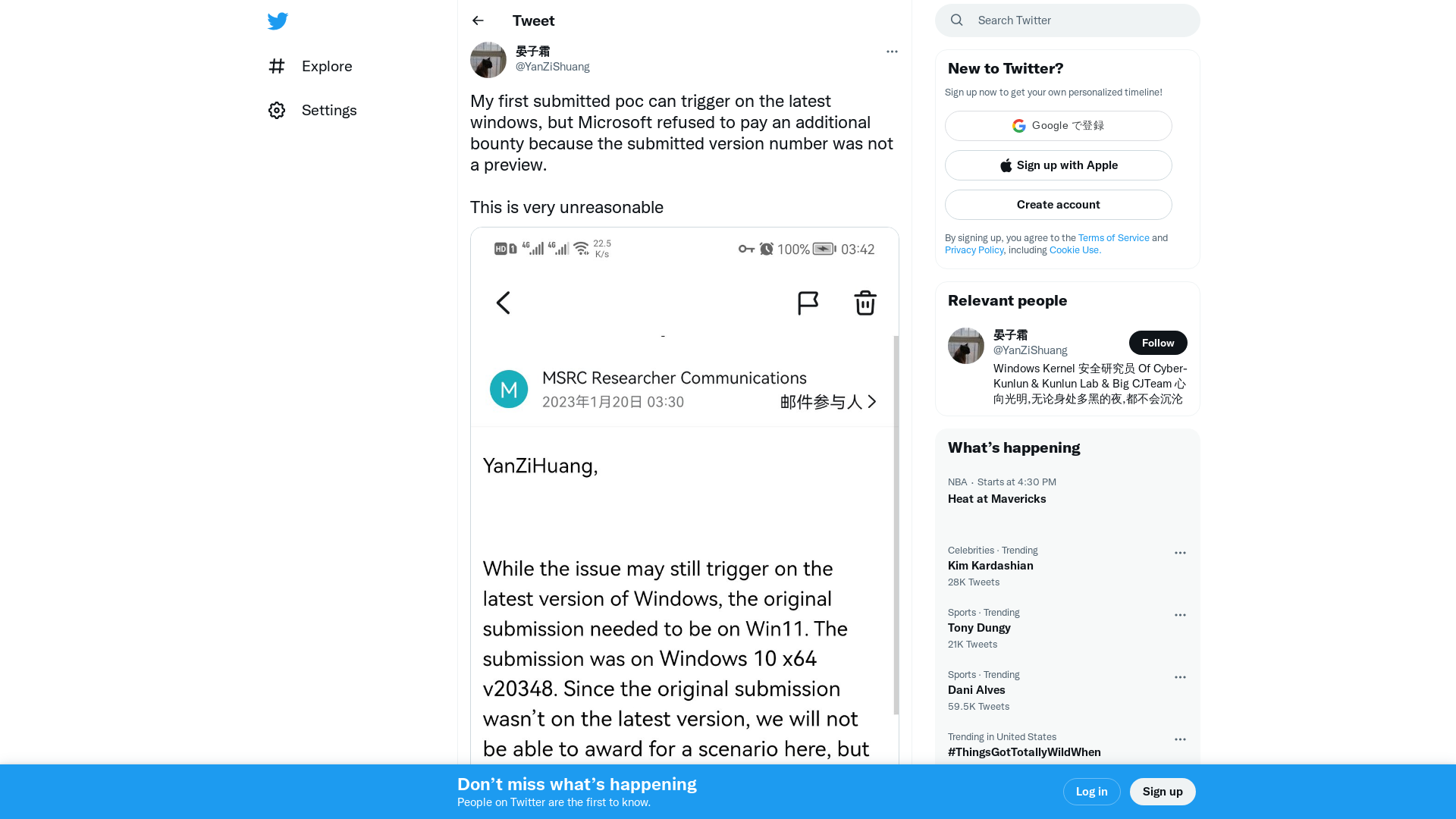
2022 Microsoft Teams RCE
https://blog.pksecurity.io/2023/01/16/2022-microsoft-teams-rce.html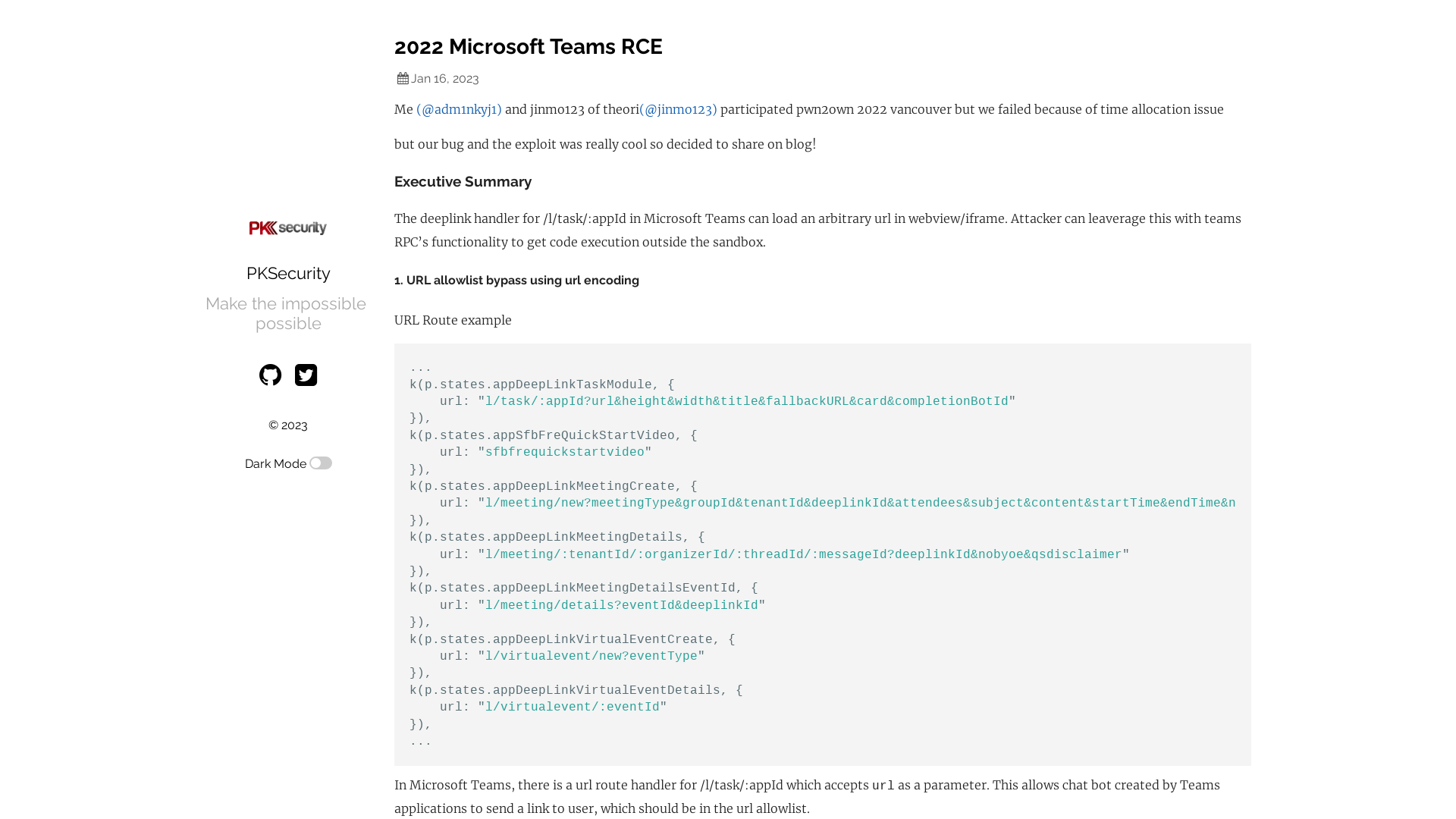
Zero to Hero: The process of reversing and exploiting complex vulnerabilities! / Twitter
https://twitter.com/i/broadcasts/1rmxPkRrMDEJN
GitHub - john-xor/temp
https://github.com/john-xor/temp
VirusTotal - File - b5403448598de334b4a94ed9ab9e14a9e22160753a73ae98fa81b9172a385414
https://www.virustotal.com/gui/file/b5403448598de334b4a94ed9ab9e14a9e22160753a73ae98fa81b9172a385414/community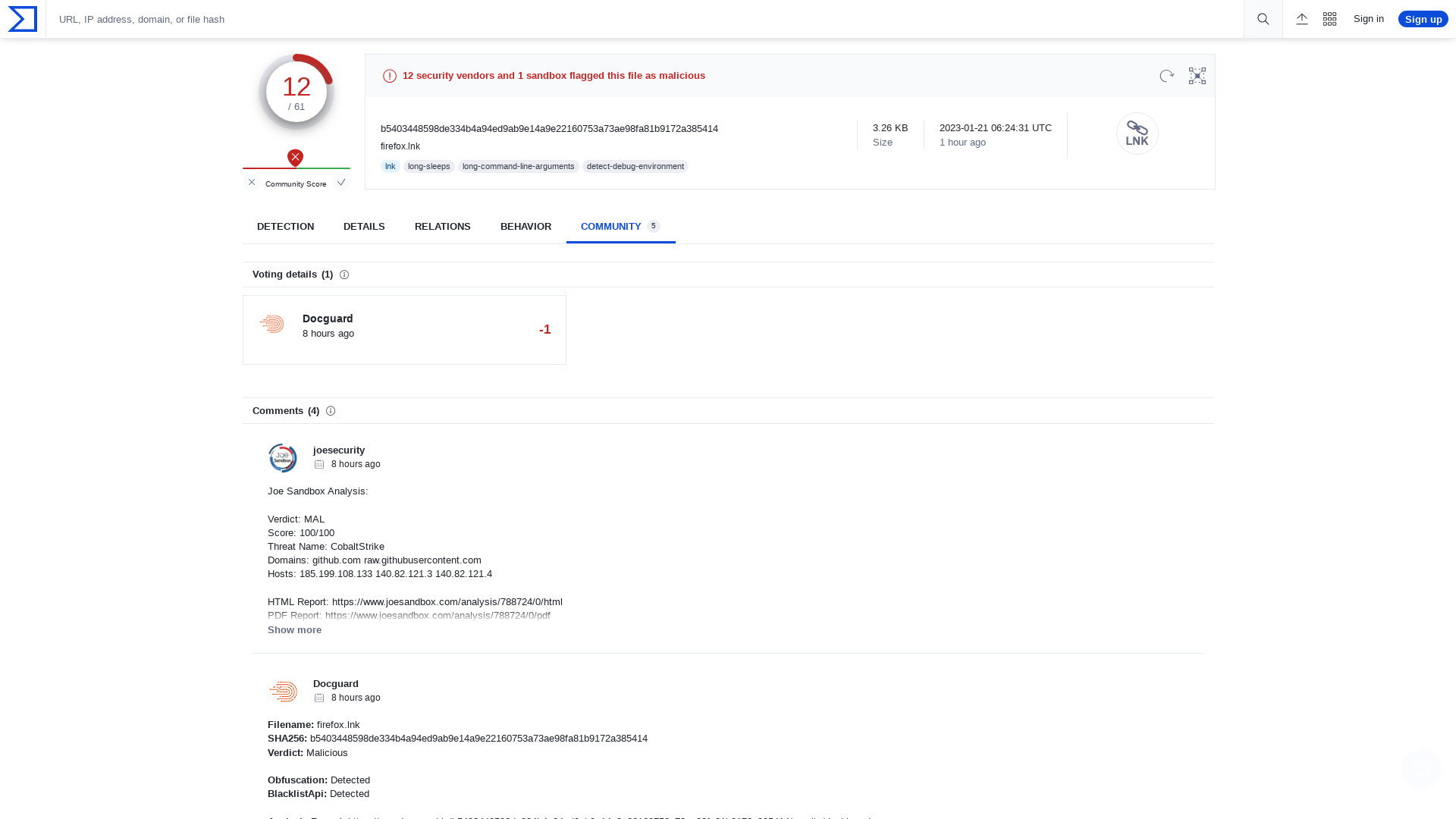
MalwareBazaar | Browse Checking your browser
https://bazaar.abuse.ch/sample/b5403448598de334b4a94ed9ab9e14a9e22160753a73ae98fa81b9172a385414/