Critical Remote Code Execution Vulnerability in SPNEGO Extended Negotiation Security Mechanism
https://securityintelligence.com/posts/critical-remote-code-execution-vulnerability-spnego-extended-negotiation-security-mechanism/
Unmasking MirrorFace: Operation LiberalFace targeting Japanese political entities | WeLiveSecurity
https://www.welivesecurity.com/2022/12/14/unmasking-mirrorface-operation-liberalface-targeting-japanese-political-entities/
FBI’s Vetted Info Sharing Network ‘InfraGard’ Hacked – Krebs on Security
https://krebsonsecurity.com/2022/12/fbis-vetted-info-sharing-network-infragard-hacked/
FBI’s Vetted Info Sharing Network ‘InfraGard’ Hacked – Krebs on Security
https://krebsonsecurity.com/2022/12/fbis-vetted-info-sharing-network-infragard-hacked/?v=1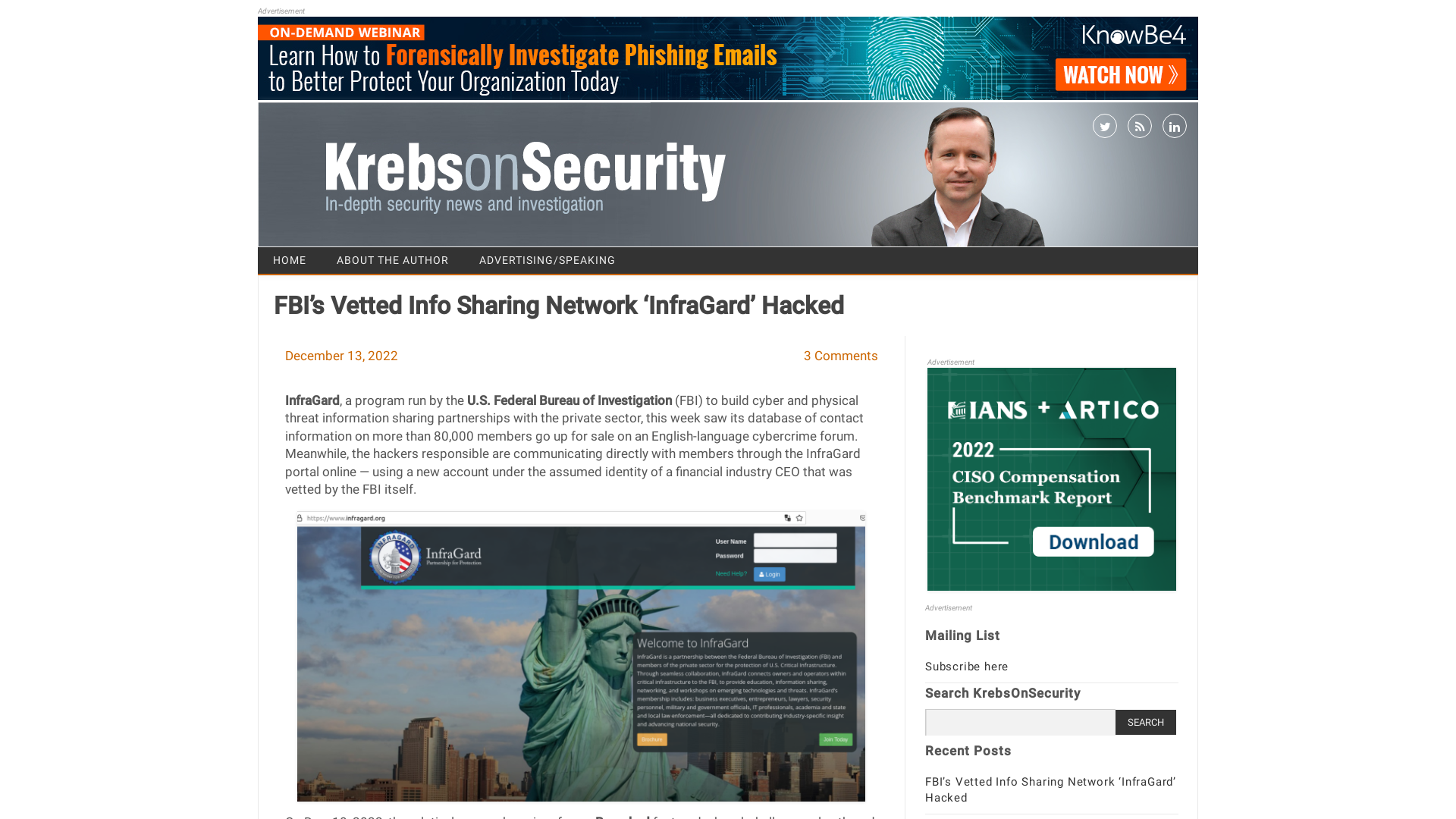
Would’ve, Could’ve, Should’ve…Did: TA453 Refuses to be Bound by Expectations | Proofpoint US
https://www.proofpoint.com/us/blog/threat-insight/ta453-refuses-be-bound-expectations
CVE-2022-41076 - Security Update Guide - Microsoft - PowerShell Remote Code Execution Vulnerability
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2022-41076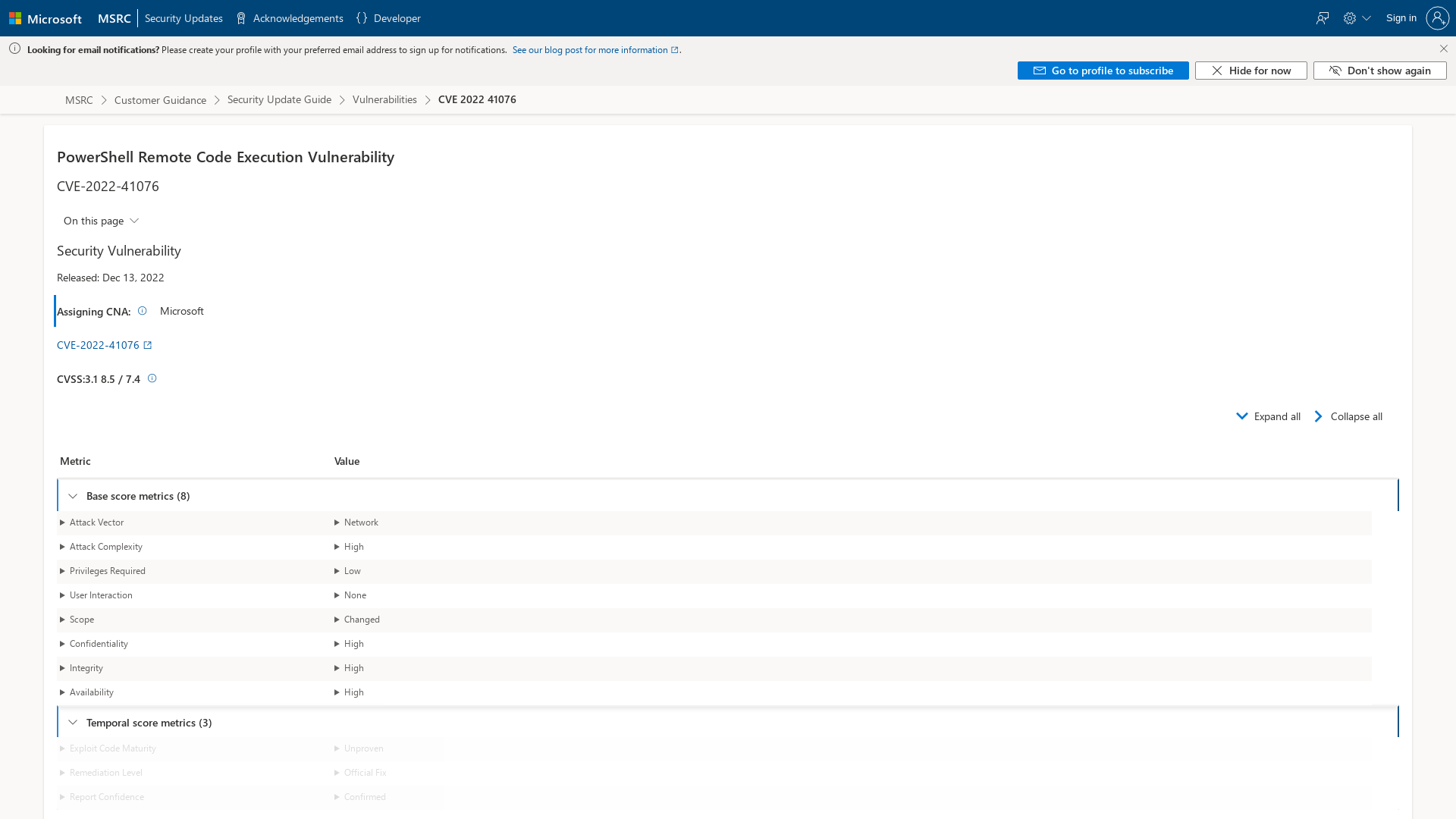
Apple security update fixes new iOS zero-day used to hack iPhones
https://www.bleepingcomputer.com/news/apple/apple-security-update-fixes-new-ios-zero-day-used-to-hack-iphones/
I Solemnly Swear My Driver Is Up to No Good: Hunting for Attestation Signed Malware | Mandiant
https://www.mandiant.com/resources/blog/hunting-attestation-signed-malware
Unusual Cache Poisoning between Akamai and S3 buckets
https://spyclub.tech/2022/12/14/unusual-cache-poisoning-akamai-s3/
Uncovering Windows Security Events | by Jonathan Johnson | Dec, 2022 | Medium
https://jsecurity101.medium.com/uncovering-window-security-events-8c11a9dcdf34
Microsoft-signed malicious Windows drivers used in ransomware attacks
https://www.bleepingcomputer.com/news/microsoft/microsoft-signed-malicious-windows-drivers-used-in-ransomware-attacks/
MalwareBazaar | Browse Checking your browser
https://bazaar.abuse.ch/sample/ce81b2ab0a243fe8e85a249b0f425007d858d7e9cc7e65af5d2f9e68efb5e5d0/
Qakbot/Qakbot_BB10_14.12.2022.txt at main · pr0xylife/Qakbot · GitHub
https://github.com/pr0xylife/Qakbot/blob/main/Qakbot_BB10_14.12.2022.txt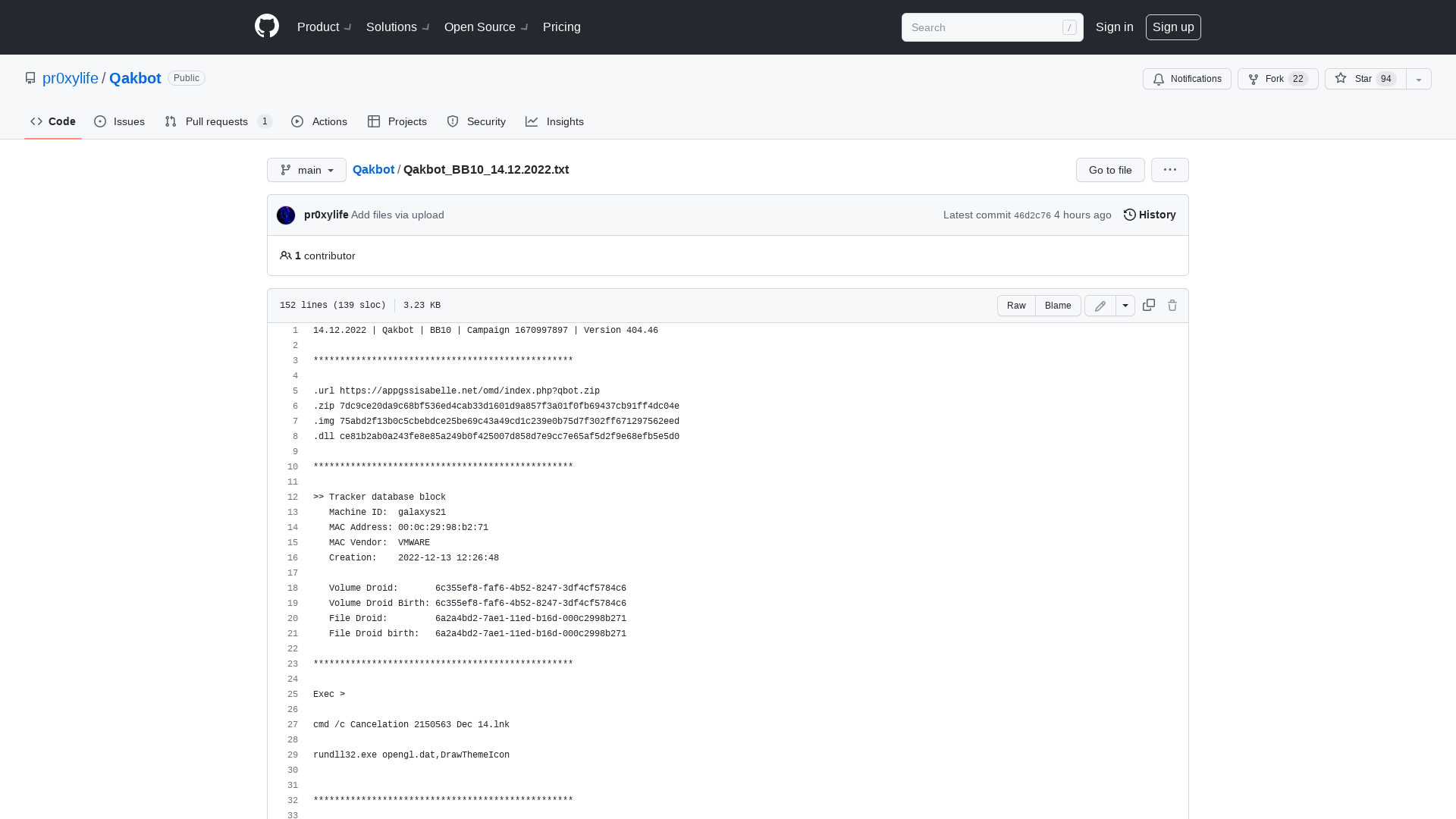
AWS ECR Public Vulnerability
https://blog.lightspin.io/aws-ecr-public-vulnerability
chompie on Twitter: "Demonstrating CVE-2022-37958 RCE Vuln. Reachable via any Windows application protocol that authenticates. Yes, that means RDP, SMB and many more. Please patch this one, it's serious! https://t.co/ikOrTvQIJs https://t.co/bOTmL5Fh2H" / Twitter
https://twitter.com/chompie1337/status/1602757336908660736
Microsoft: December Windows Server updates break Hyper-V VM creation
https://www.bleepingcomputer.com/news/microsoft/microsoft-december-windows-server-updates-break-hyper-v-vm-creation/
New Actively Exploited Zero-Day Vulnerability Discovered in Apple Products
https://thehackernews.com/2022/12/new-actively-exploited-zero-day.html
Reassessing cyberwarfare. Lessons learned in 2022 | Securelist
https://securelist.com/reassessing-cyberwarfare-lessons-learned-in-2022/108328/