Internet Explorer 0-day exploited by North Korean actor APT37
https://blog.google/threat-analysis-group/internet-explorer-0-day-exploited-by-north-korean-actor-apt37/
CVE-2022-41128: Type confusion in Internet Explorer's JScript9 engine | 0-days In-the-Wild
https://googleprojectzero.github.io/0days-in-the-wild/0day-RCAs/2022/CVE-2022-41128.html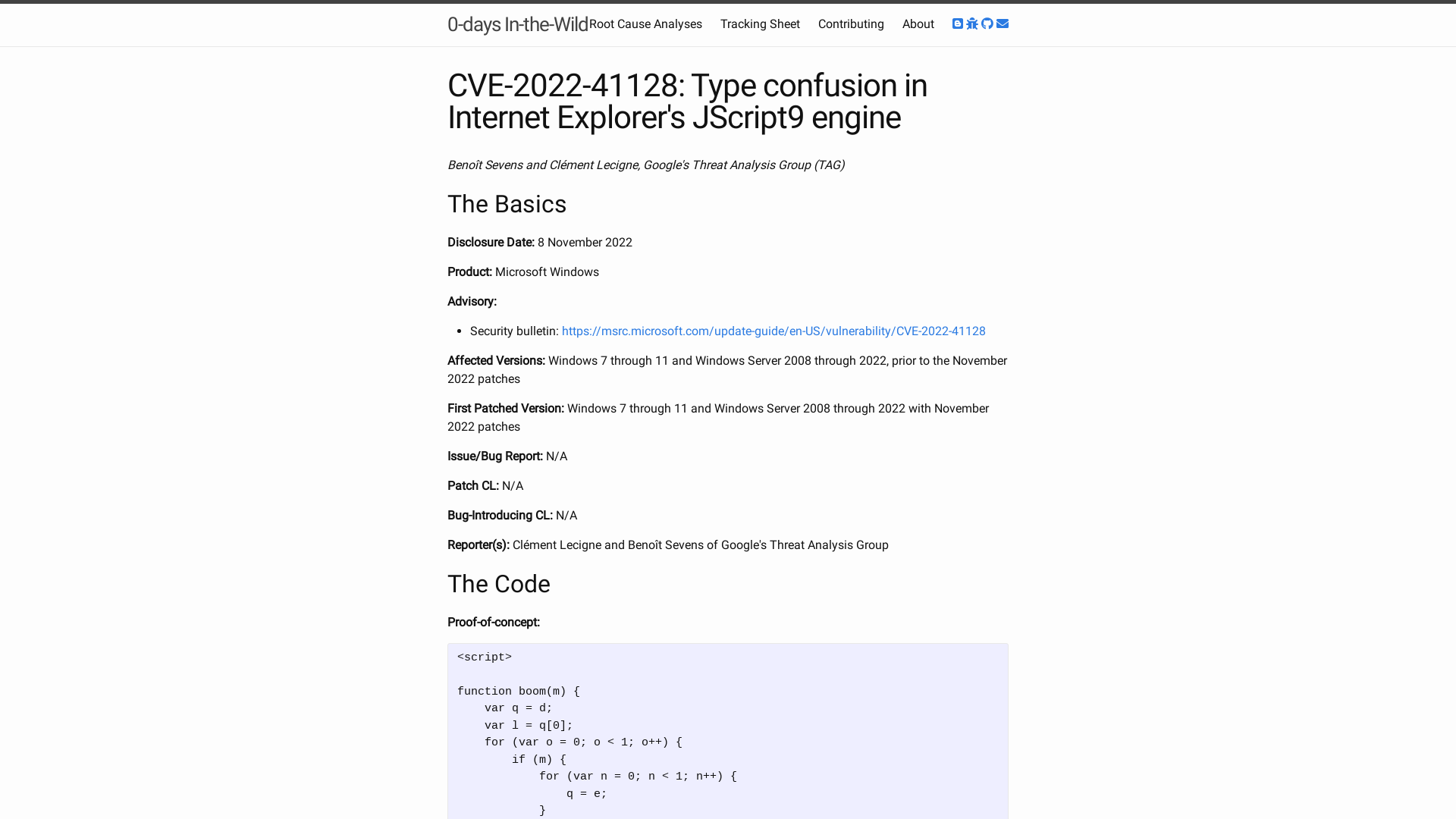
[단독] '이태원 참사' 악용한 악성코드 공격 포착
https://www.inews24.com/view/1534369![[단독] '이태원 참사' 악용한 악성코드 공격 포착](/image/screenshot/764c0fbb169e97e38e32d45404af5c6e.png)
Project Zero: Exploiting CVE-2022-42703 - Bringing back the stack attack
https://googleprojectzero.blogspot.com/2022/12/exploiting-CVE-2022-42703-bringing-back-the-stack-attack.html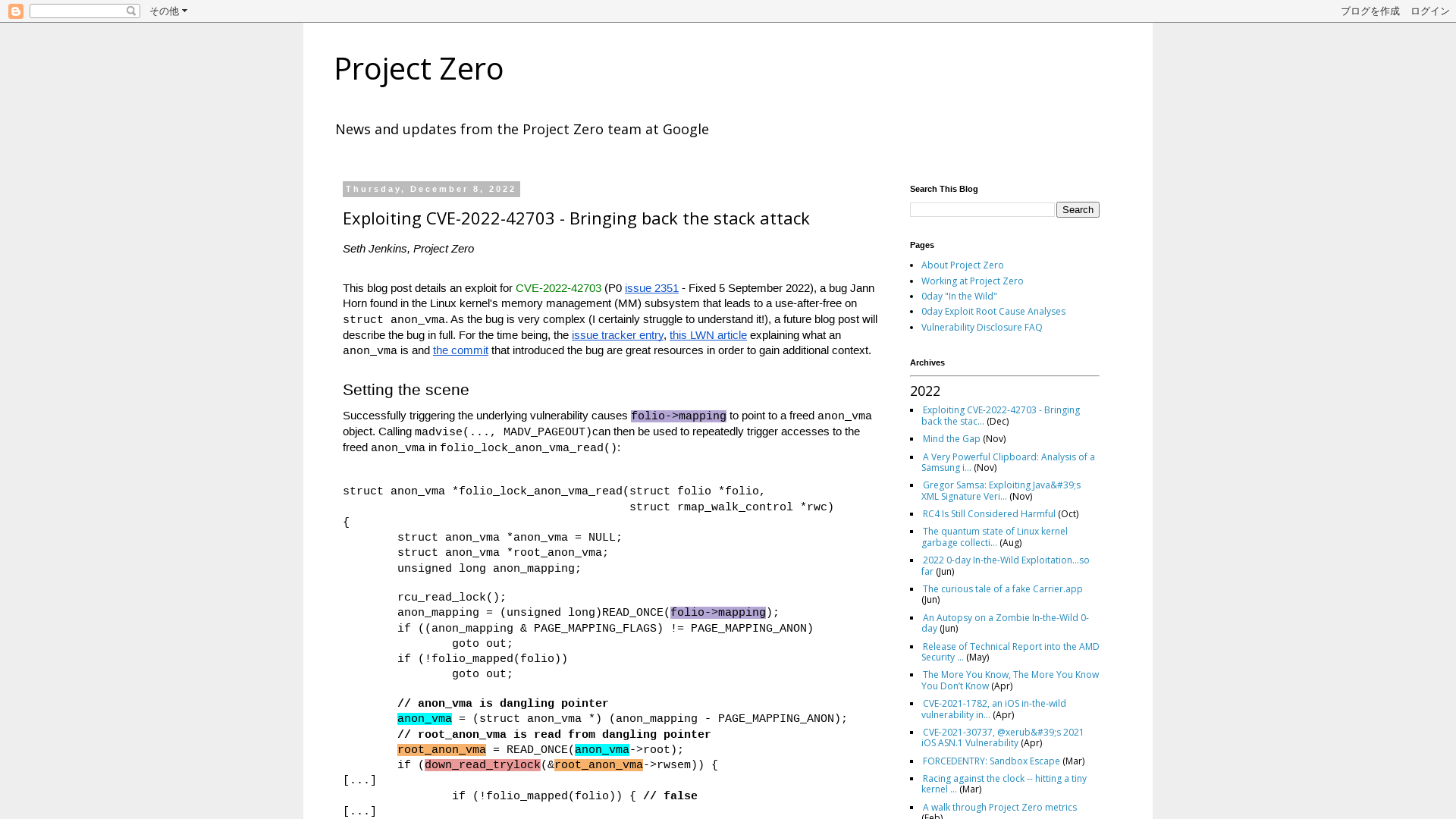
APT_REPORT/group123/IEexploit202212sample at master · blackorbird/APT_REPORT · GitHub
https://github.com/blackorbird/APT_REPORT/tree/master/group123/IEexploit202212sample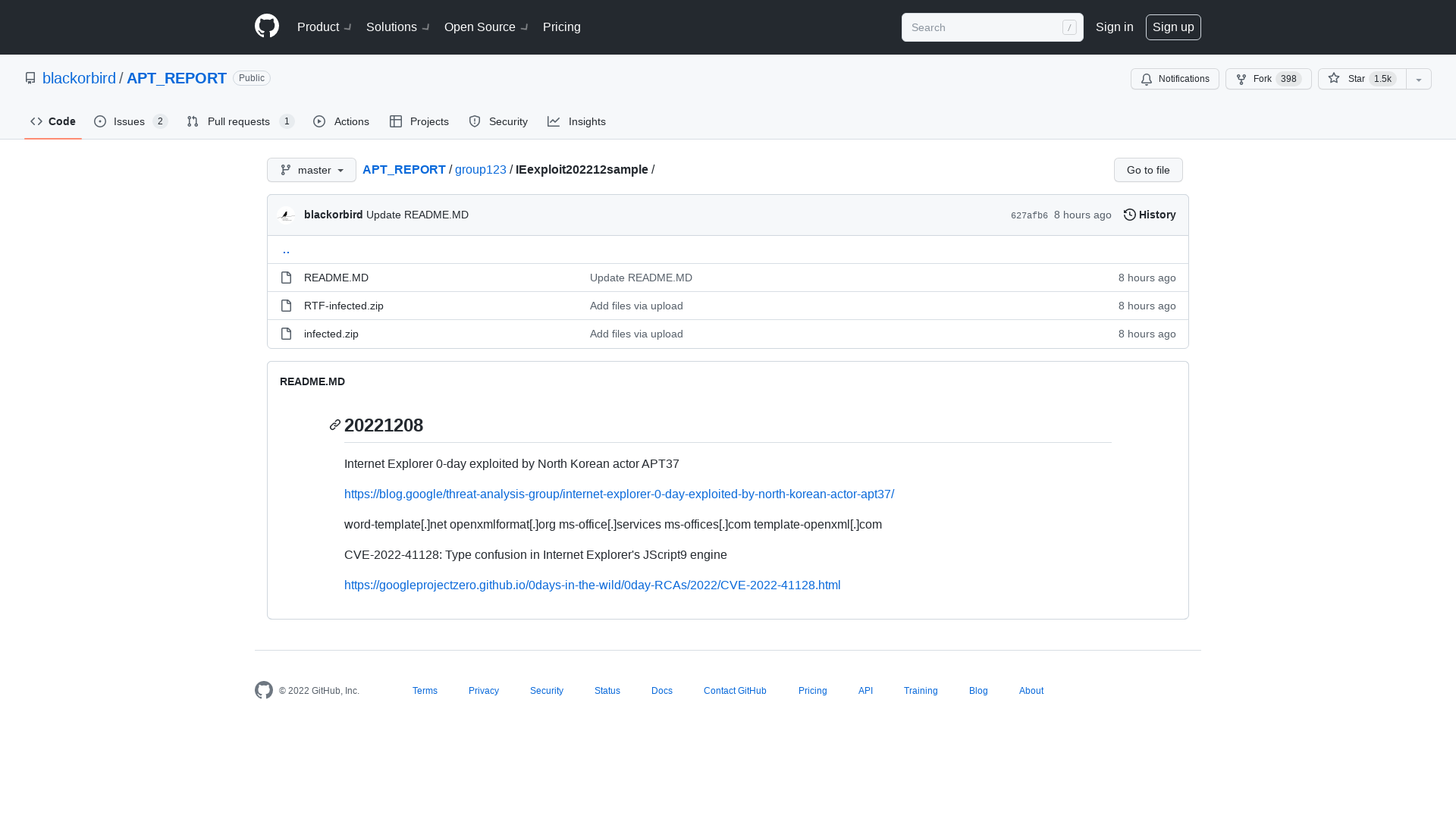
Zombinder: new obfuscation service used by Ermac, now distributed next to desktop stealers — ThreatFabric
https://www.threatfabric.com/blogs/zombinder-ermac-and-desktop-stealers.html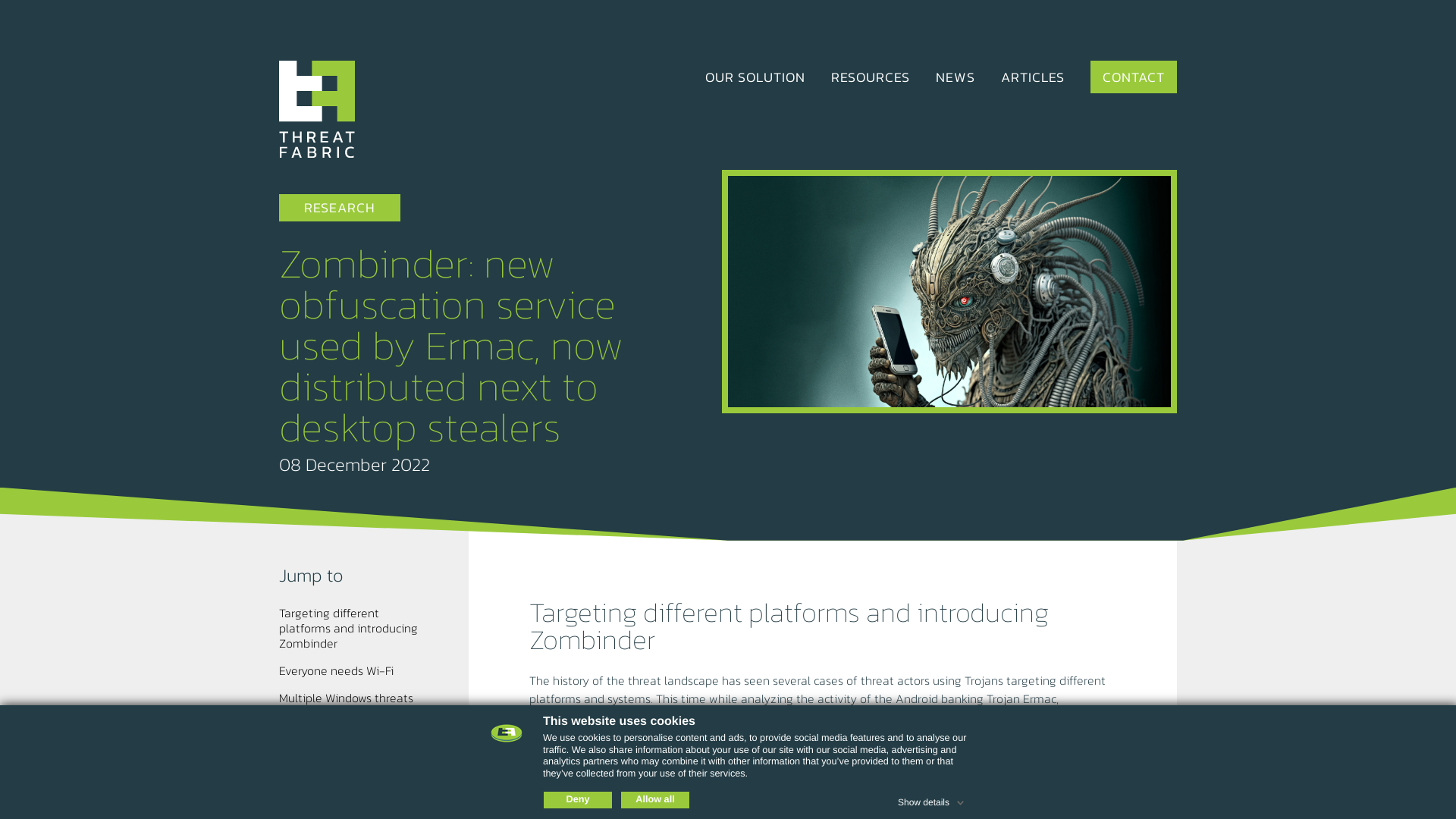
Unit 42 on Twitter: "2022-12-07 (Wednesday): #Bumblebee malware from 2022-12-06 led to #CobaltStrike activity on 23.108.57[.]213:443 using ceyuvigi[.]com. IoCs available at: https://t.co/nDGOgla1Cz https://t.co/jzQHo1AHf5" / Twitter
https://twitter.com/Unit42_Intel/status/1600587285577203715![Unit 42 on Twitter: "2022-12-07 (Wednesday): #Bumblebee malware from 2022-12-06 led to #CobaltStrike activity on 23.108.57[.]213:443 using ceyuvigi[.]com. IoCs available at: https://t.co/nDGOgla1Cz https://t.co/jzQHo1AHf5" / Twitter](/image/screenshot/1016acfd6c8ae7fb676005dcce0fd15e.png)
GitHub - klezVirus/SilentMoonwalk: PoC Implementation of a TRUE call stack spoofer
https://github.com/klezVirus/SilentMoonwalk
Training • NorthSec 2022
https://nsec.io/training-sessions/
Ryan Naraine on Twitter: "A lobbying outfit representing big tech is calling on the US government’s Office of Management and Budget (OMB) to “discourage agencies” from requiring SBOMs, arguing that “it is premature and of limited utility...” My story https://t.co/iwENFTcBpf" / Twitter
https://twitter.com/ryanaraine/status/1600623726763966464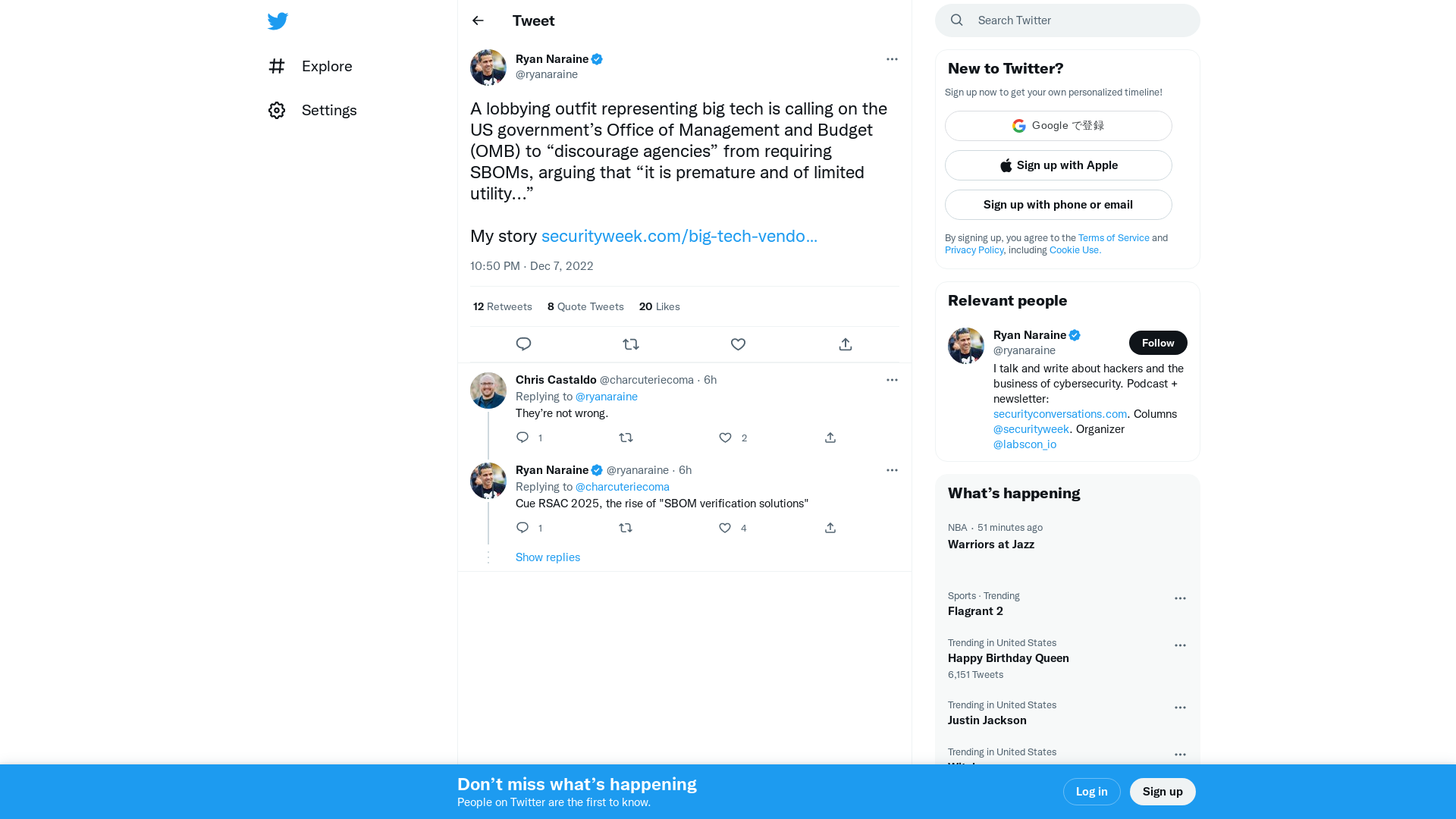
James Clayton on Twitter: "NEW: The BBC has obtained pictures of inside Twitter - rooms that have been converted into bedrooms - for staff to sleep in. The city of San Francisco is investigating as it's a commercial building. https://t.co/Y4vKxZXQhB" / Twitter
https://twitter.com/jamesclayton5/status/1600619990691954688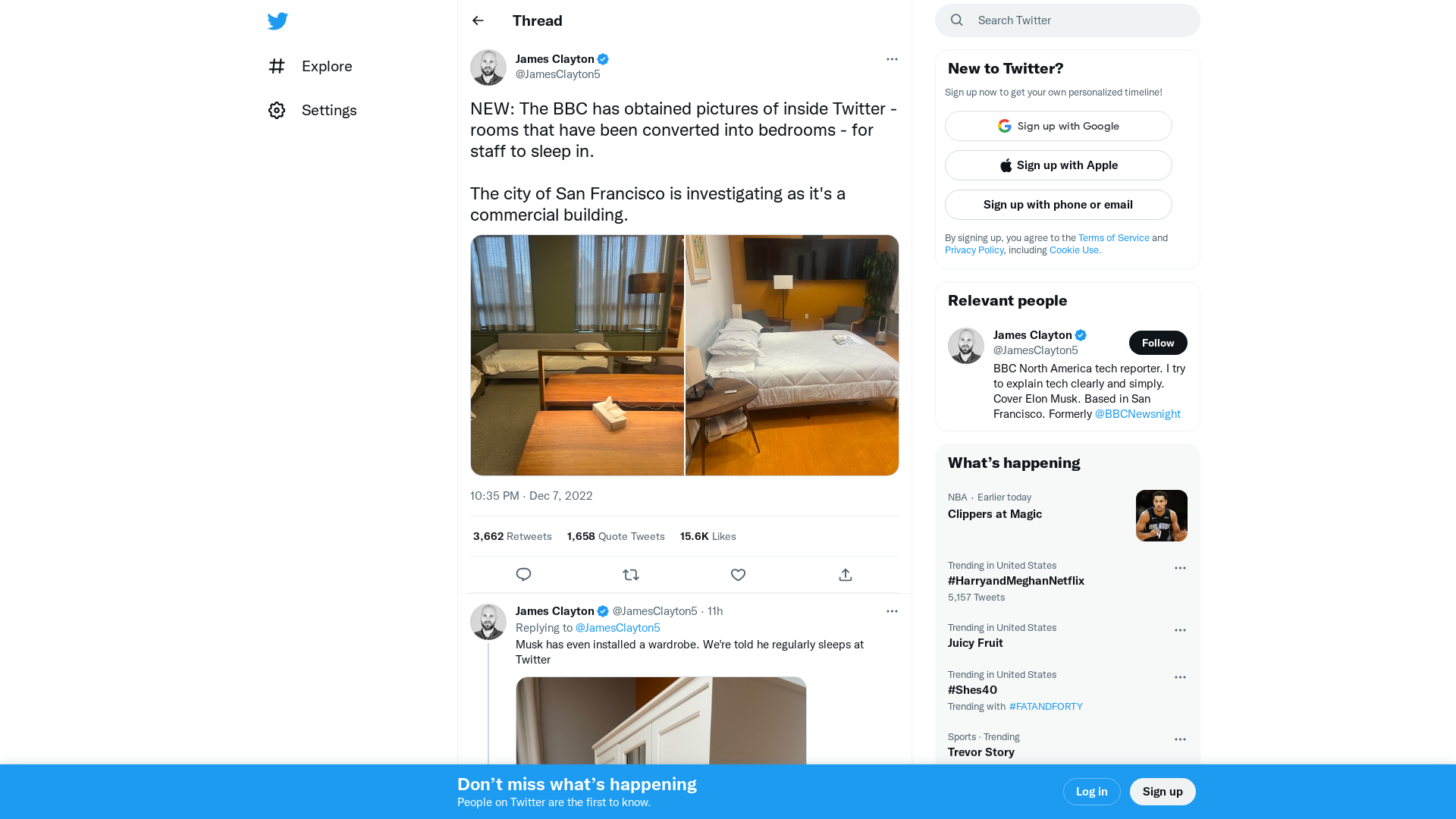
Google: North Korean gov’t hackers used Internet Explorer zero-day to target South Korea users - The Record by Recorded Future
https://therecord.media/google-north-korean-govt-hackers-used-internet-explorer-zero-day-to-target-south-korea-users/
MalwareBazaar | Browse Checking your browser
https://bazaar.abuse.ch/sample/40ab463703114d972269c34abeecf0f796c88c20cceaaf0e582ed0a132e556fa/