Chapter 1 — From Gozi to ISFB: The history of a mythical malware family. | by Benoit ANCEL | CSIS TechBlog | Oct, 2022 | Medium
https://medium.com/csis-techblog/chapter-1-from-gozi-to-isfb-the-history-of-a-mythical-malware-family-82e592577fef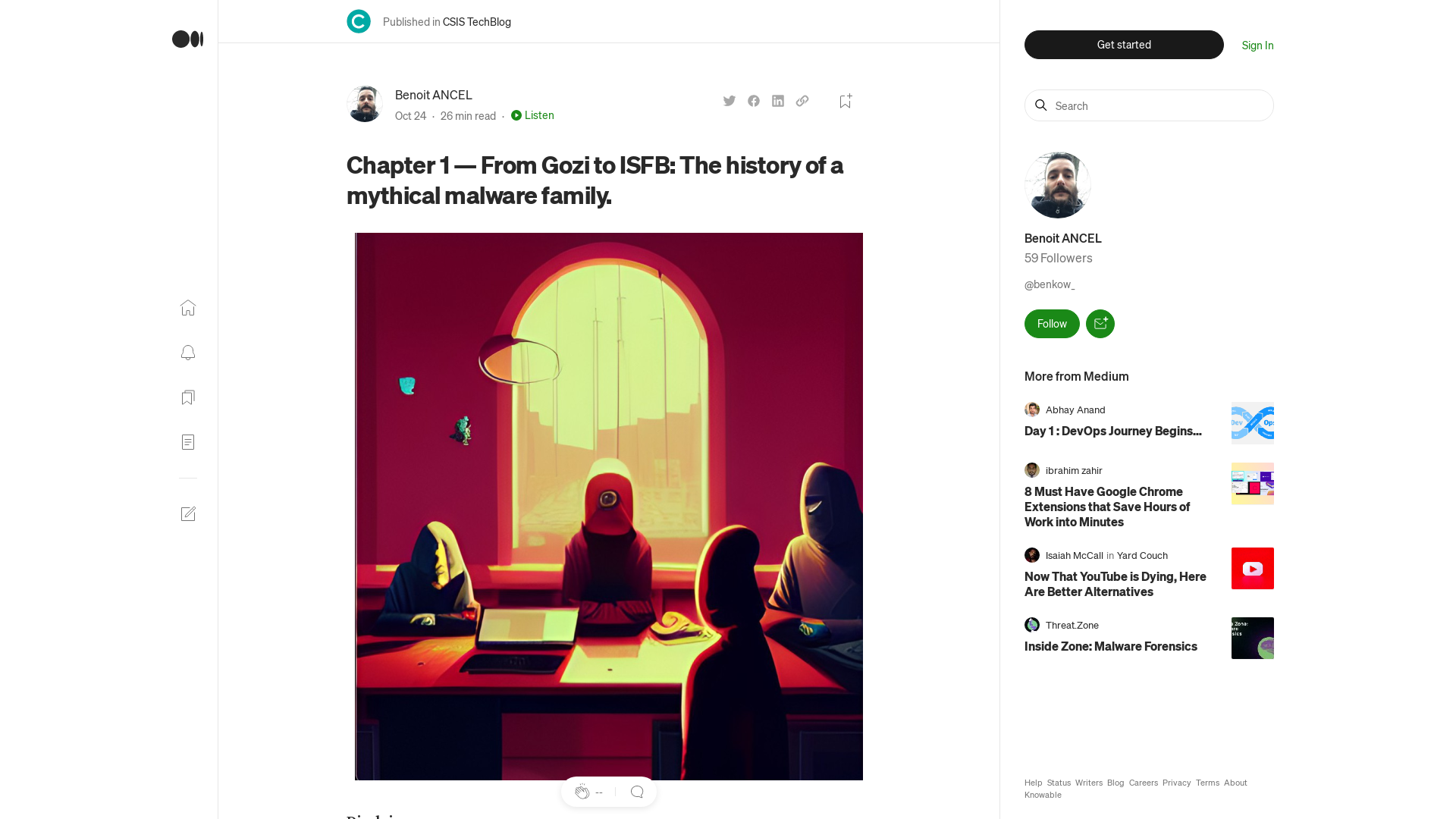
[angry-FSROP] Bypassing vtable Check in glibc File Structures | kylebot's Blog
https://blog.kylebot.net/2022/10/22/angry-FSROP/![[angry-FSROP] Bypassing vtable Check in glibc File Structures | kylebot's Blog](/image/screenshot/79f25da2c262d5c9eee82d6ca7bb794e.png)
Thousands of GitHub repositories deliver fake PoC exploits with malware
https://www.bleepingcomputer.com/news/security/thousands-of-github-repositories-deliver-fake-poc-exploits-with-malware/
x86matthew - SharedMemUtils - A simple tool to automatically find vulnerabilities in shared memory objects
https://www.x86matthew.com/view_post?id=shared_mem_utils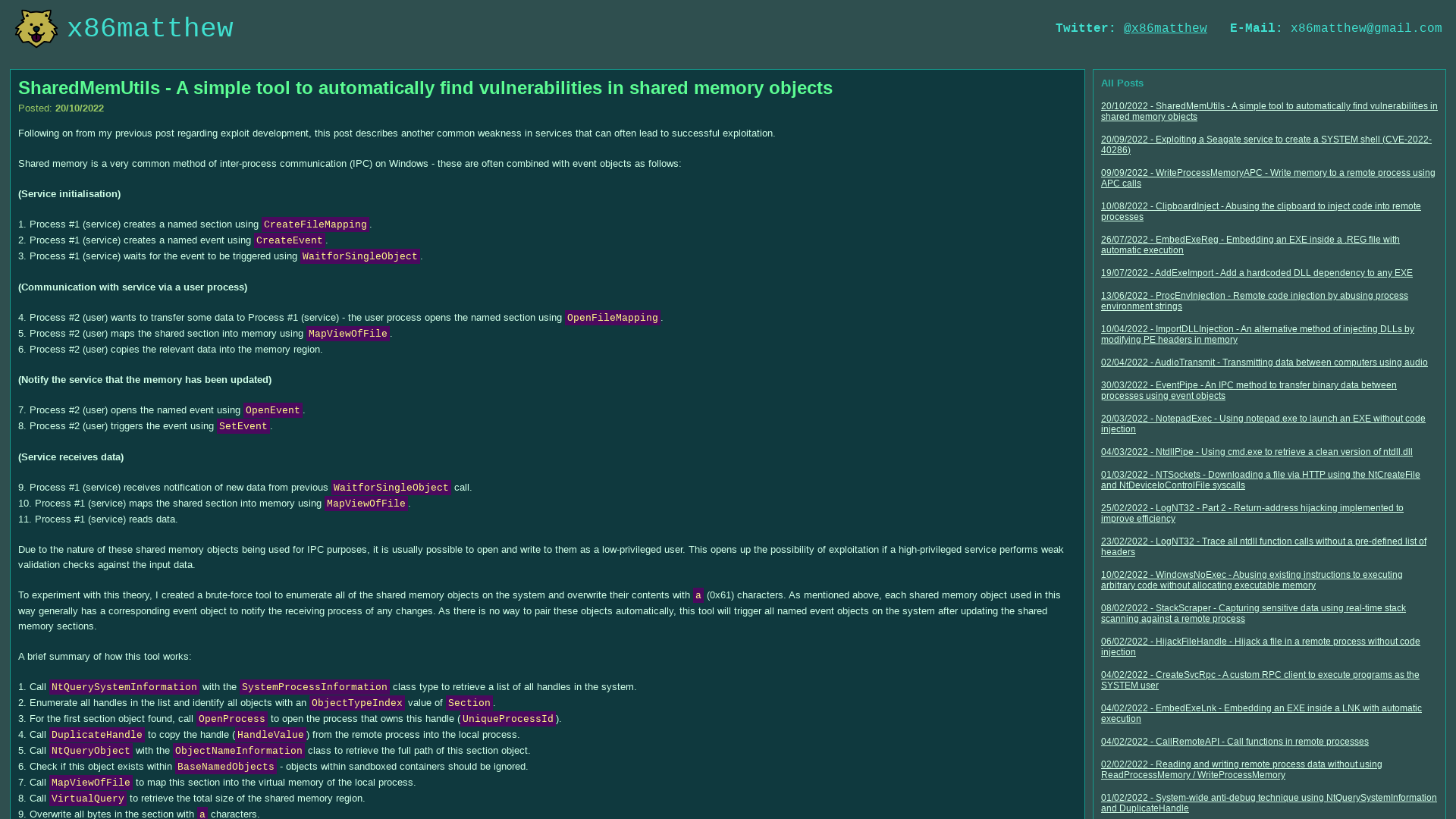
John Opdenakker on Twitter: "What makes a cyber attack advanced?" / Twitter
https://twitter.com/j_opdenakker/status/1584607173211959296
APT27 - One Year To Exfiltrate Them All: Intrusion In-Depth Analysis -
https://www.intrinsec.com/apt27-analysis/
CISA Warns of Daixin Team Hackers Targeting Health Organizations With Ransomware
https://thehackernews.com/2022/10/cisa-warns-of-daixin-team-hackers.html
TommyLeaks and SchoolBoys: Two sides of the same ransomware gang
https://www.bleepingcomputer.com/news/security/tommyleaks-and-schoolboys-two-sides-of-the-same-ransomware-gang/
proxylife on Twitter: "#Qakbot - BB04 - url > .zip > .iso > .lnk > .cmd > .dll cmd /c Copy.lnk cmd.exe /c unmoistened\summoner.cmd reg regsvr32.exe unmoistened\face.dat https://t.co/5btxUndhsq https://t.co/yqQj5oUxjy IOC's https://t.co/or1rN6xiCS https://t.co/zMeSd0yv4O" / Twitter
https://twitter.com/pr0xylife/status/1584495515521404929
Chrome Browser Exploitation, Part 1: Introduction to V8 and JavaScript Internals - Jack Hacks
https://jhalon.github.io/chrome-browser-exploitation-1/
Nat on Twitter: "Using Office VBA Macro to exploit a vulnerable driver (zam64.sys) using DeviceIoControl, to get NT AUTHORITY\SYSTEM TL;DR - Ring 0 using Office Doc} Blogpost incoming soon lol Thanks to @Coldzer0x0 @kasua02 for the encouragement and help. https://t.co/psplpgvNuU" / Twitter
https://twitter.com/0xDISREL/status/1544482838279585794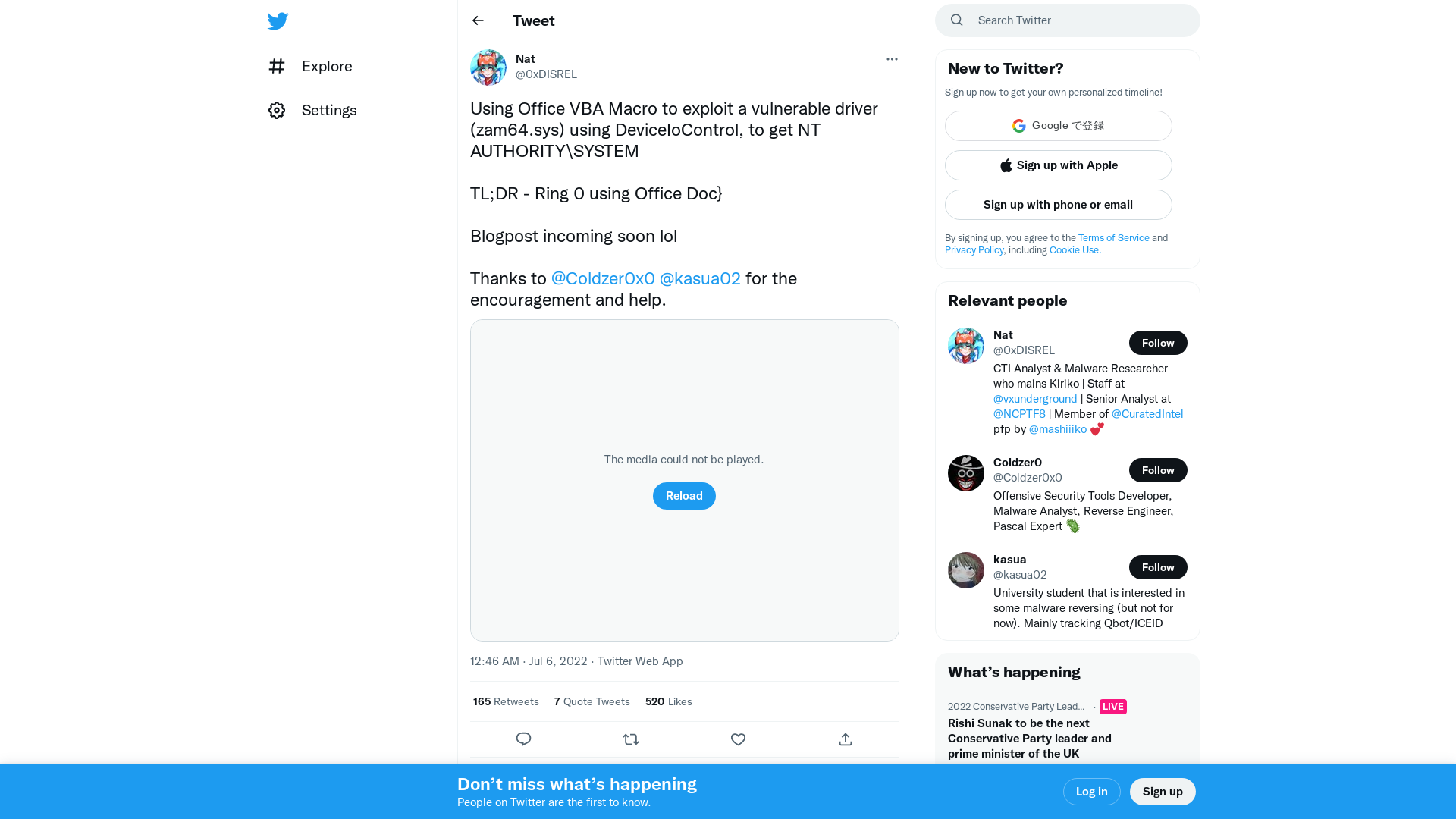
Frog Guy Rants | Ring0VBA - Getting Ring0 Using a Goddamn Word Document
https://disrel.com/posts/Ring0VBA-Getting-Ring0-Using-a-Goddamn-Word-Document/
Cybersecurity Difference Makers Awards | SANS Institute
https://www.sans.org/u/1nf5
MalwareBazaar | Browse Checking your browser
https://bazaar.abuse.ch/sample/4df936e24707cbb9332c99488a20f5fa0f9e0ac5cc3a2ea4d509f3539ea79200/
Qakbot/Qakbot_BB04_24.10.2022.txt at main · pr0xylife/Qakbot · GitHub
https://github.com/pr0xylife/Qakbot/blob/main/Qakbot_BB04_24.10.2022.txt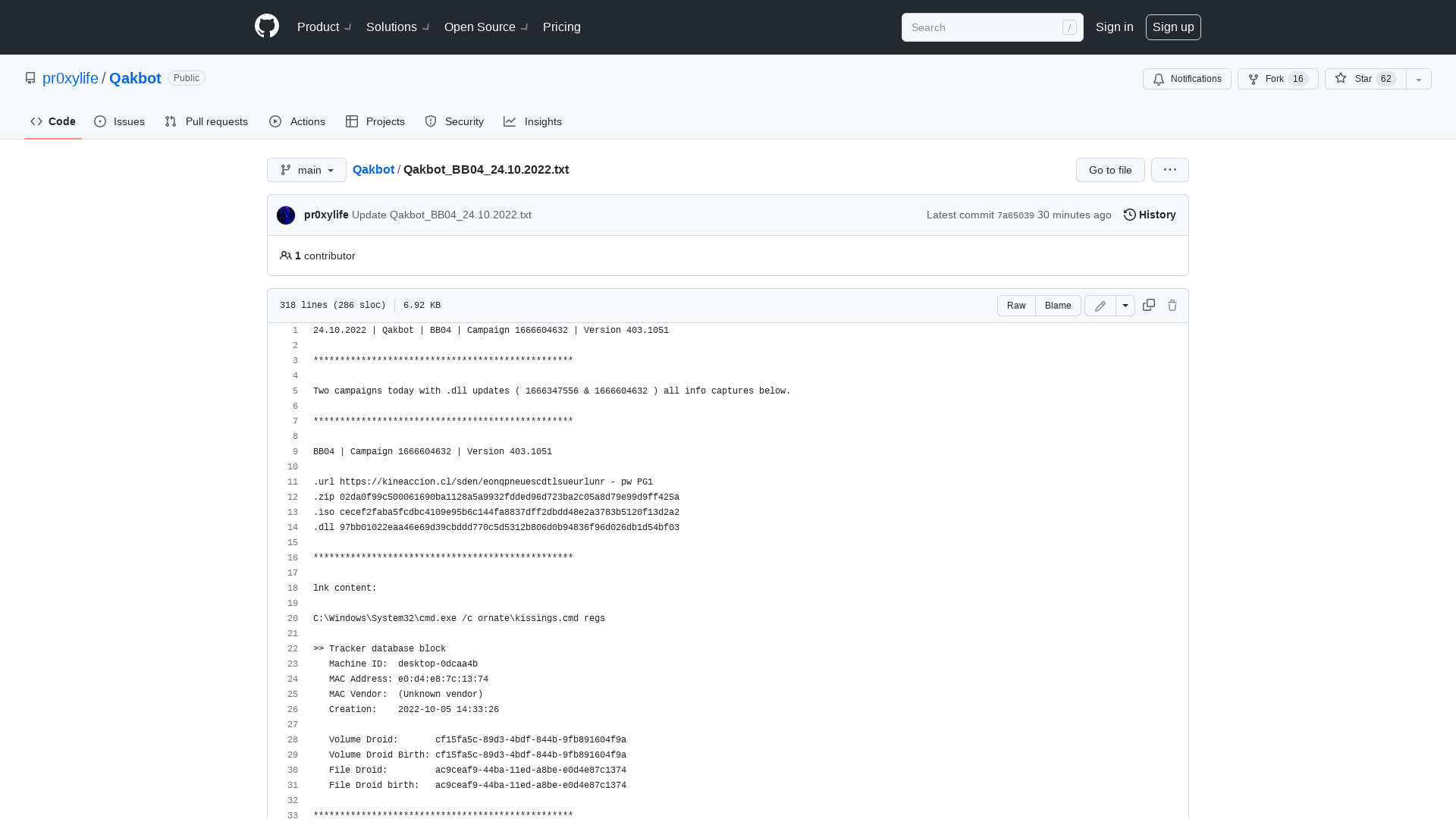
Exploit archaeology a forensic history of in the wild NSO Group exploits Donncha Ó Cearbhaill Amnest - YouTube
https://youtu.be/NvS67qiq8bw?t=1
Hot on the Trail of a Mass-School-Shooting Hoaxer | WIRED
https://www.wired.com/story/school-swatting-textnow-ethiopia/
Huawei Probe, Tech Secrets Targeted by Chinese Spies, US Alleges - Bloomberg
https://www.bloomberg.com/news/articles/2022-10-24/chinese-spies-tried-to-obstruct-probe-of-a-telecom-us-alleges
MalwareBazaar | Browse Checking your browser
https://bazaar.abuse.ch/sample/5bb4a3ccf4e566179ed6534df7f9e55315d79298b291126cf060df2f8ba9dd54/
Fake books - lcamtuf’s thing
https://lcamtuf.substack.com/p/fake-books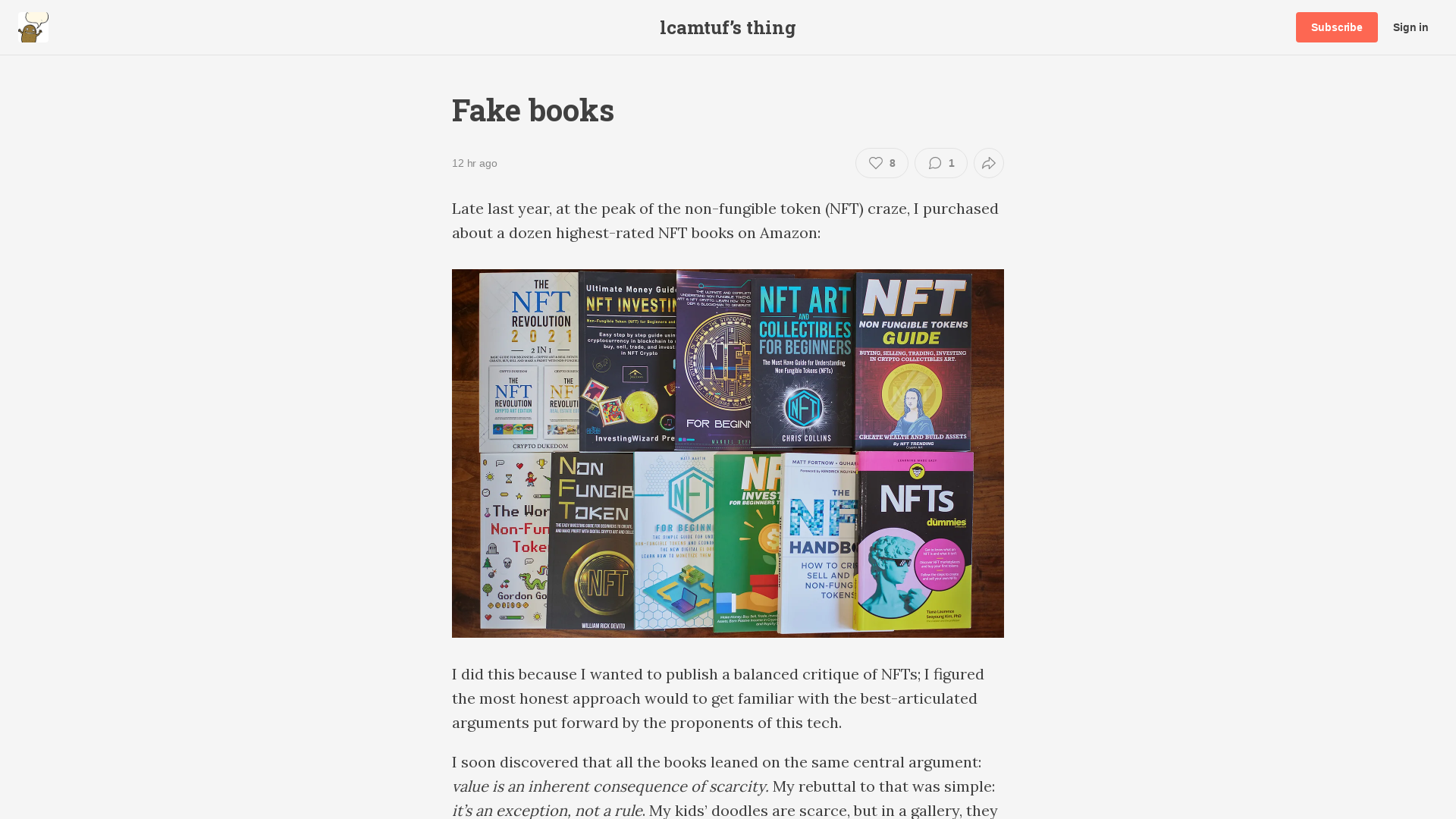
Indian Spy Agency Bought Hardware Matching Equipment Used for Pegasus
https://www.occrp.org/en/daily/16915-indian-spy-agency-bought-hardware-matching-equipment-used-for-pegasus
Pendragon car dealer refuses $60 million LockBit ransomware demand
https://www.bleepingcomputer.com/news/security/pendragon-car-dealer-refuses-60-million-lockbit-ransomware-demand/