GitHub - chainguard-dev/osquery-defense-kit: Production-ready detection & response queries for osquery
https://github.com/chainguard-dev/osquery-defense-kit
Exploited Windows zero-day lets JavaScript files bypass security warnings
https://www.bleepingcomputer.com/news/security/exploited-windows-zero-day-lets-javascript-files-bypass-security-warnings/
Critical Flaw Reported in Move Virtual Machine Powering the Aptos Blockchain Network
https://thehackernews.com/2022/10/critical-flaw-reported-in-move-virtual.html
#StopRansomware: Daixin Team | CISA
https://www.cisa.gov/uscert/ncas/alerts/aa22-294a
Smokeloader: The Pandora’s box of tricks, payloads and anti-analysis - BSides Portland 2022 - YouTube
https://www.youtube.com/watch?v=O69eMQ7NS8w&list=PLqdWoaf0o9zefFAO7wHFVp032cbX1IdfM&index=6
grsecurity - Canary in the Kernel Mine: Exploiting and Defending Against Same-Type Object Reuse
https://grsecurity.net/exploiting_and_defending_against_same_type_object_reuse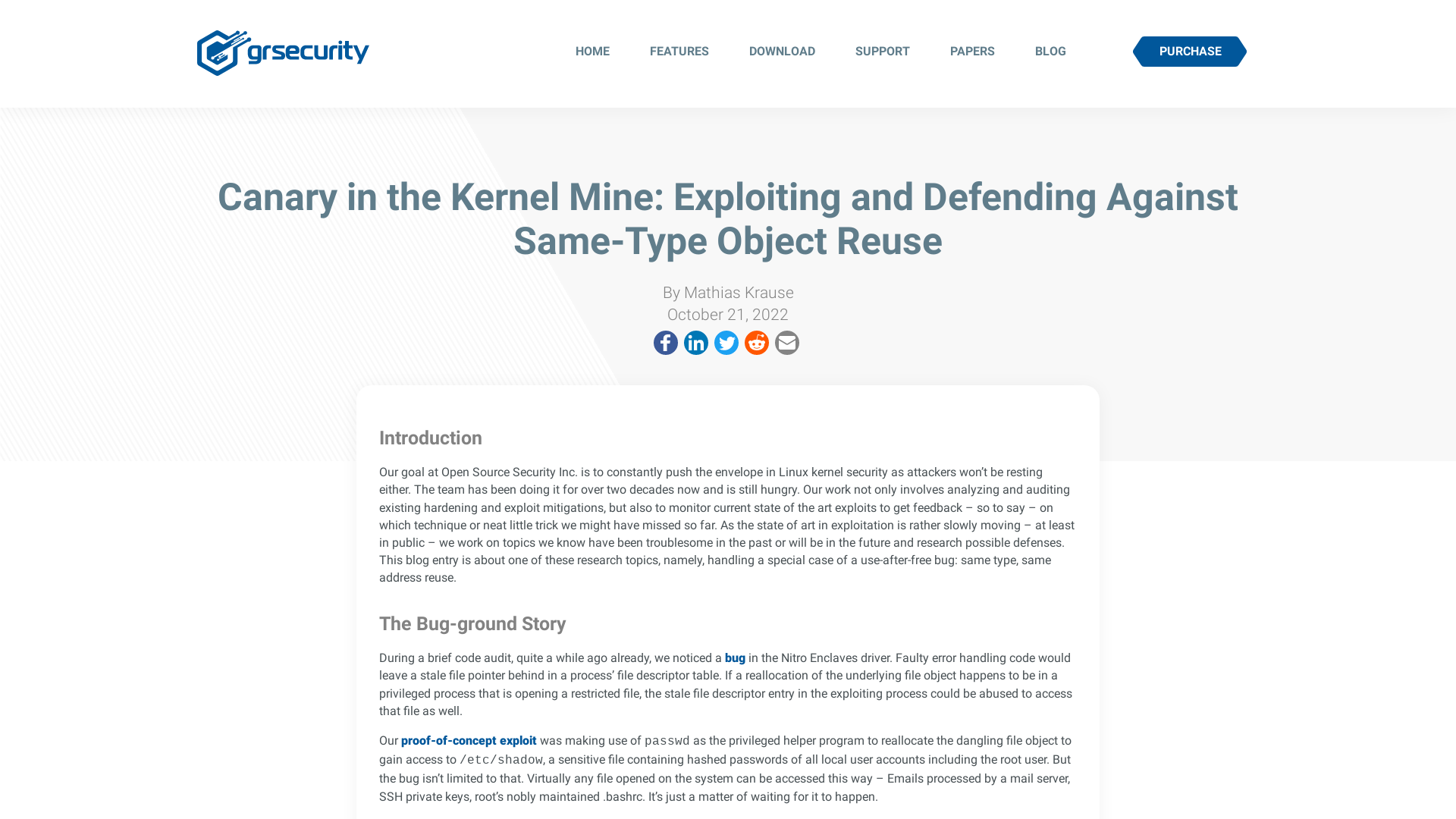
vx-underground on Twitter: "Black Reward, an Iranian hacker group, claims to have breached the Iranian government and exfiltrated sensitive data related to their nuclear programs. They informed the Iranian government they have 24 hours to release political prisoners or they will release the documents. https://t.co/17J8rZfAHo" / Twitter
https://twitter.com/i/web/status/1583568821675126784
China Xinhua News on Twitter: "When he was not feeling well during the session, his staff, for his health, accompanied him to a room next to the meeting venue for a rest. Now, he is much better." / Twitter
https://twitter.com/XHNews/status/1583829975932997637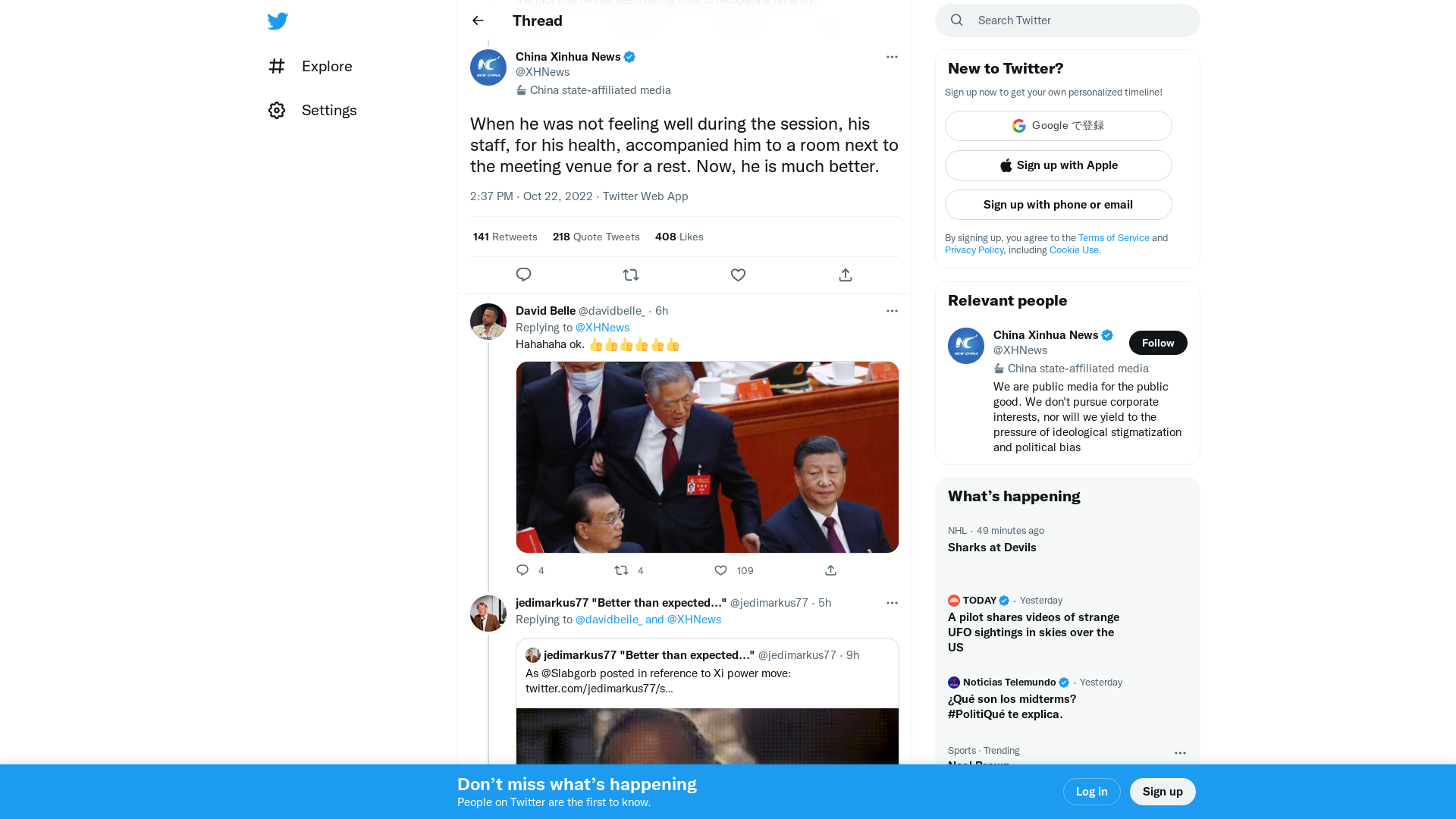
MalwareBazaar | Browse Checking your browser
https://bazaar.abuse.ch/browse/tag/kbacloud-freeboxos-fr/
MalwareBazaar | Browse Checking your browser
https://bazaar.abuse.ch/browse/tag/XeonusWallet/
VirusTotal - File - 73709989c2bc864eaac863974a65aa50a3e740e7796daaa726f96975a33b93c3
https://www.virustotal.com/gui/file/73709989c2bc864eaac863974a65aa50a3e740e7796daaa726f96975a33b93c3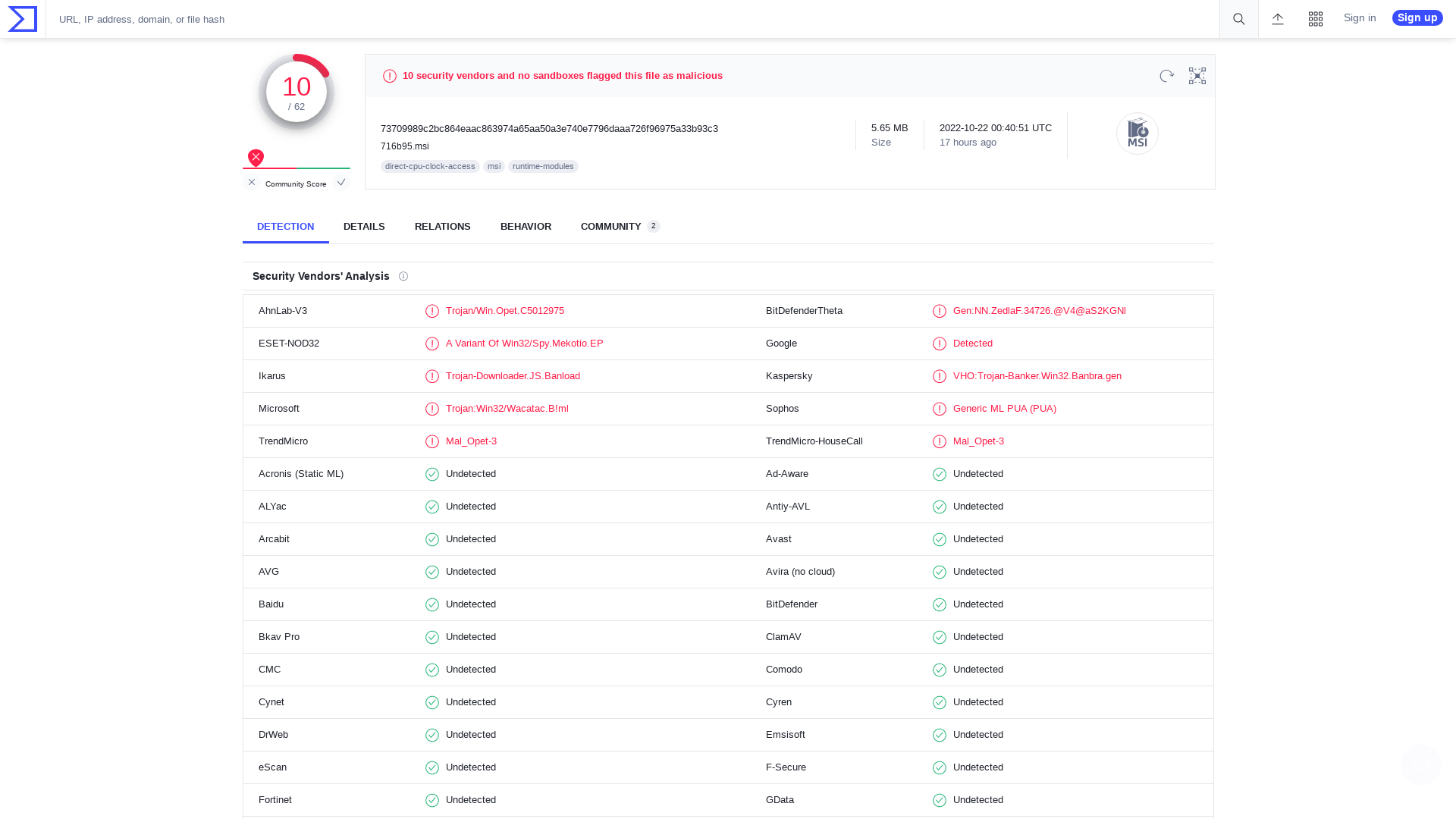
VirusTotal - File - 67b0763fa0c849e0fa4e9159f48cc8adf9684dd62a55a6379d5ff1a4215af87f
https://www.virustotal.com/gui/file/67b0763fa0c849e0fa4e9159f48cc8adf9684dd62a55a6379d5ff1a4215af87f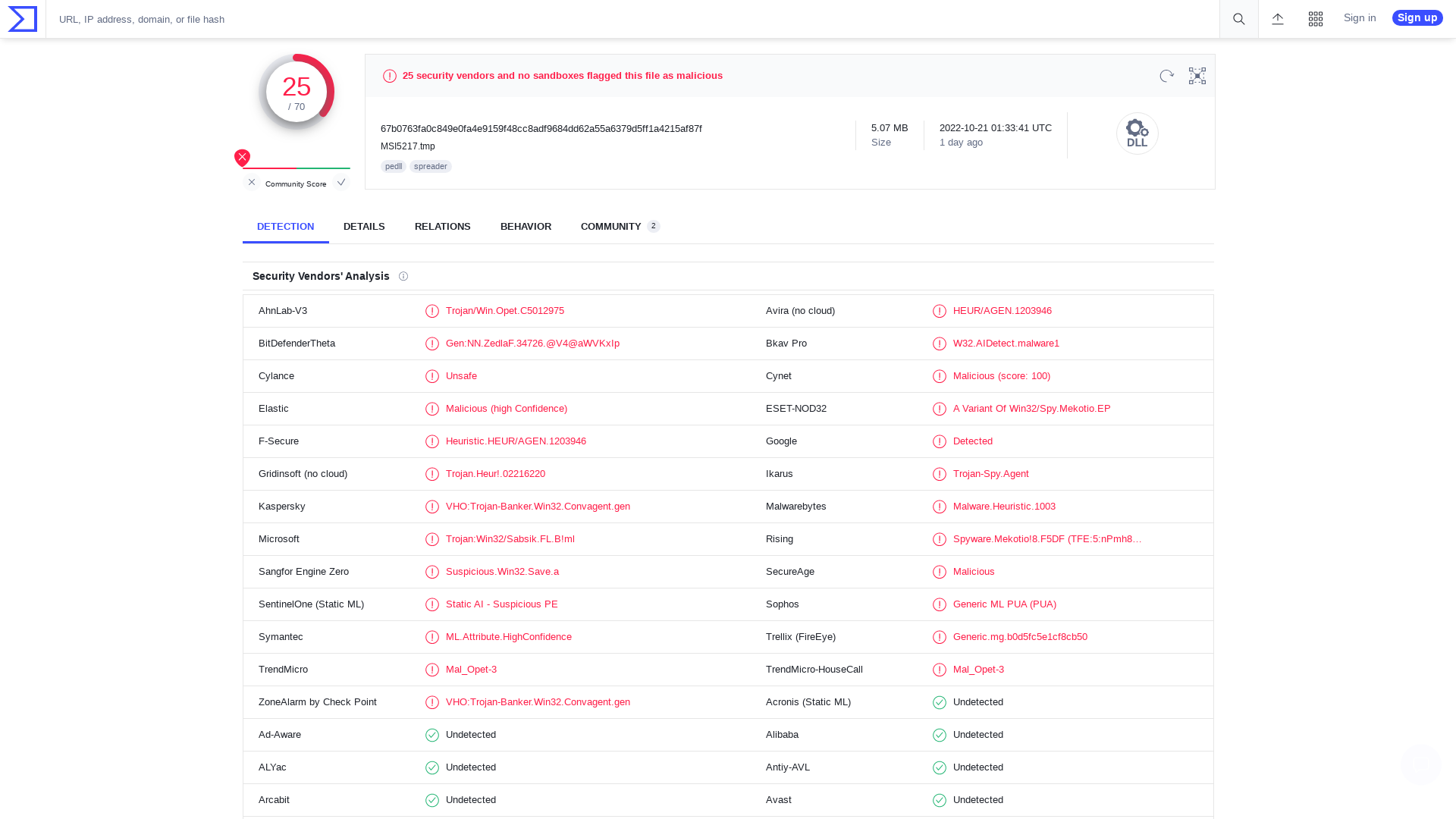
WarHawk: the New Backdoor in the Arsenal of the SideWinder APT Group | Zscaler
https://www.zscaler.com/blogs/security-research/warhawk-new-backdoor-arsenal-sidewinder-apt-group-0
GitHub - hashview/hashview: A web front-end for password cracking and analytics
https://github.com/hashview/hashview
Your Microsoft Exchange Server Is a Security Liability | WIRED
https://www.wired.com/story/microsoft-exchange-server-vulnerabilities/
VirusTotal - File - 01ba4bb94394a834155724b06697fdb1c947adaee060a627658e70cb5e9a7e3e
https://www.virustotal.com/gui/file/01ba4bb94394a834155724b06697fdb1c947adaee060a627658e70cb5e9a7e3e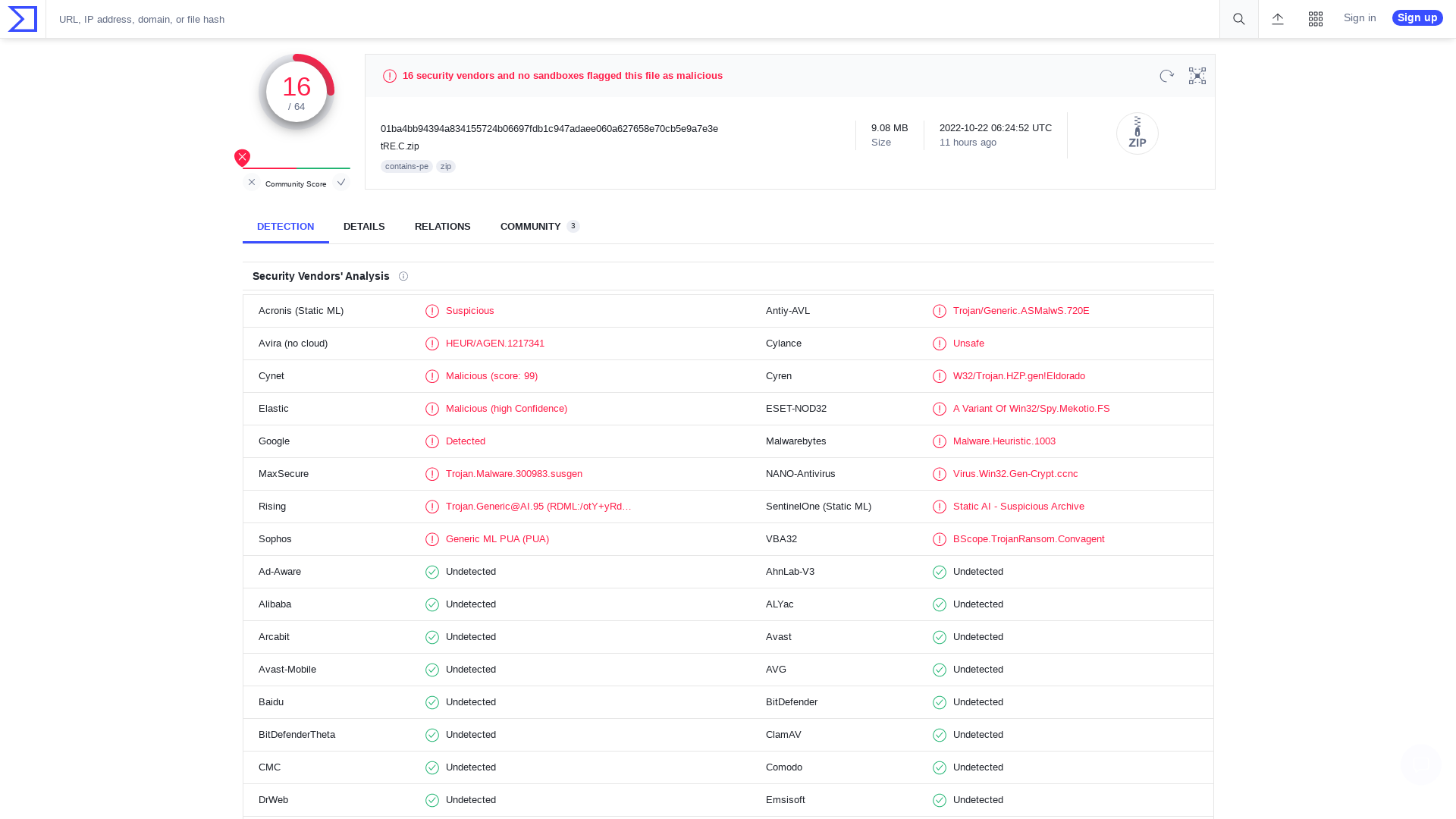
A technical analysis of the leaked LockBit 3.0 builder | Blue Team News
http://dlvr.it/SbVy0h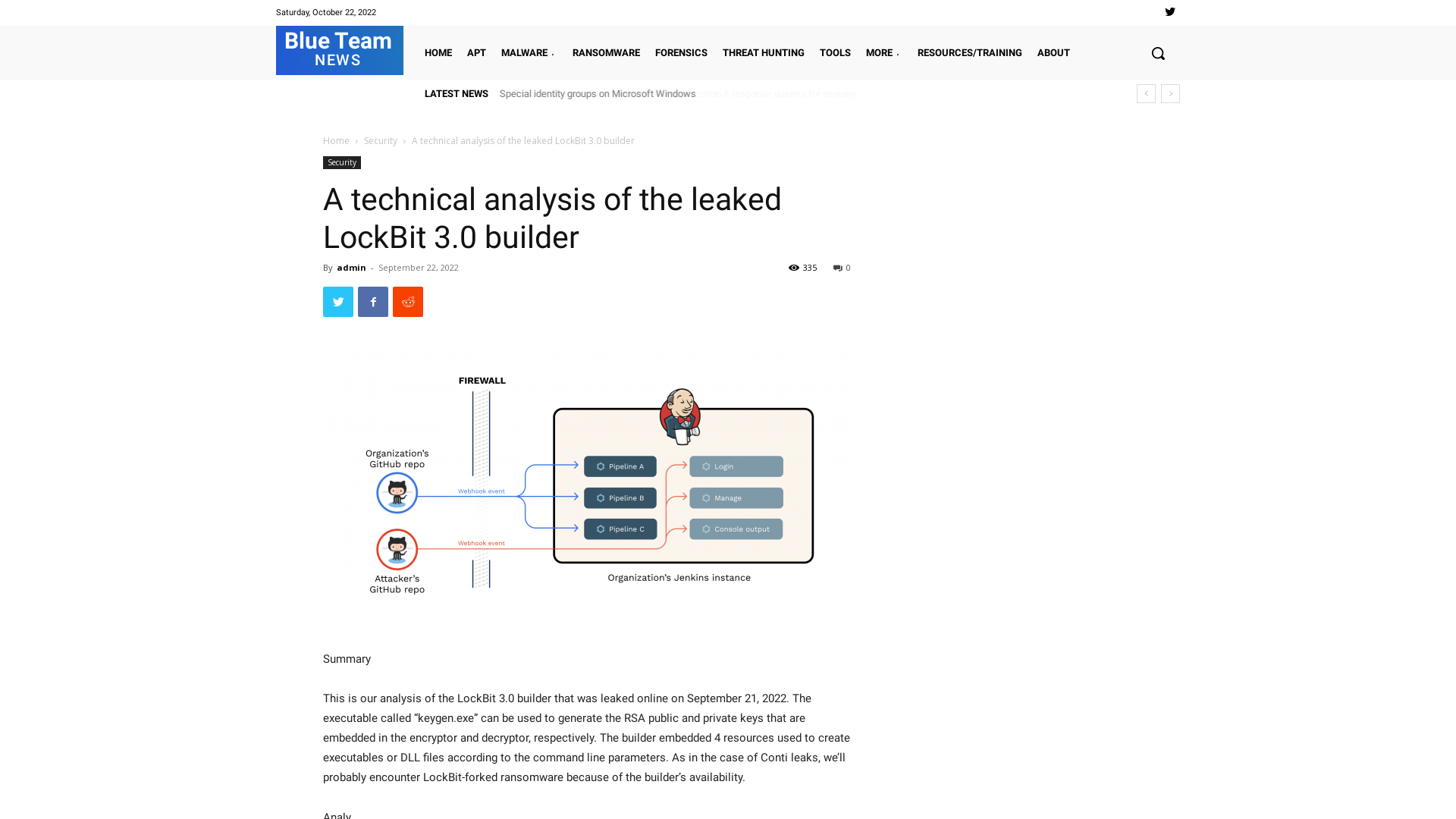
chompie on Twitter: "Remotely exploiting CVE-2022-34718, TCP/IP RCE bug #EvilEsp for DoS. This is a bug in Ipv6 fragmentation/IpSec, which allows OOB write if an Ipv6 fragment is contained inside an IpSec ESP payload. https://t.co/k1aoZX2kWq" / Twitter
https://twitter.com/chompie1337/status/1583666434668101637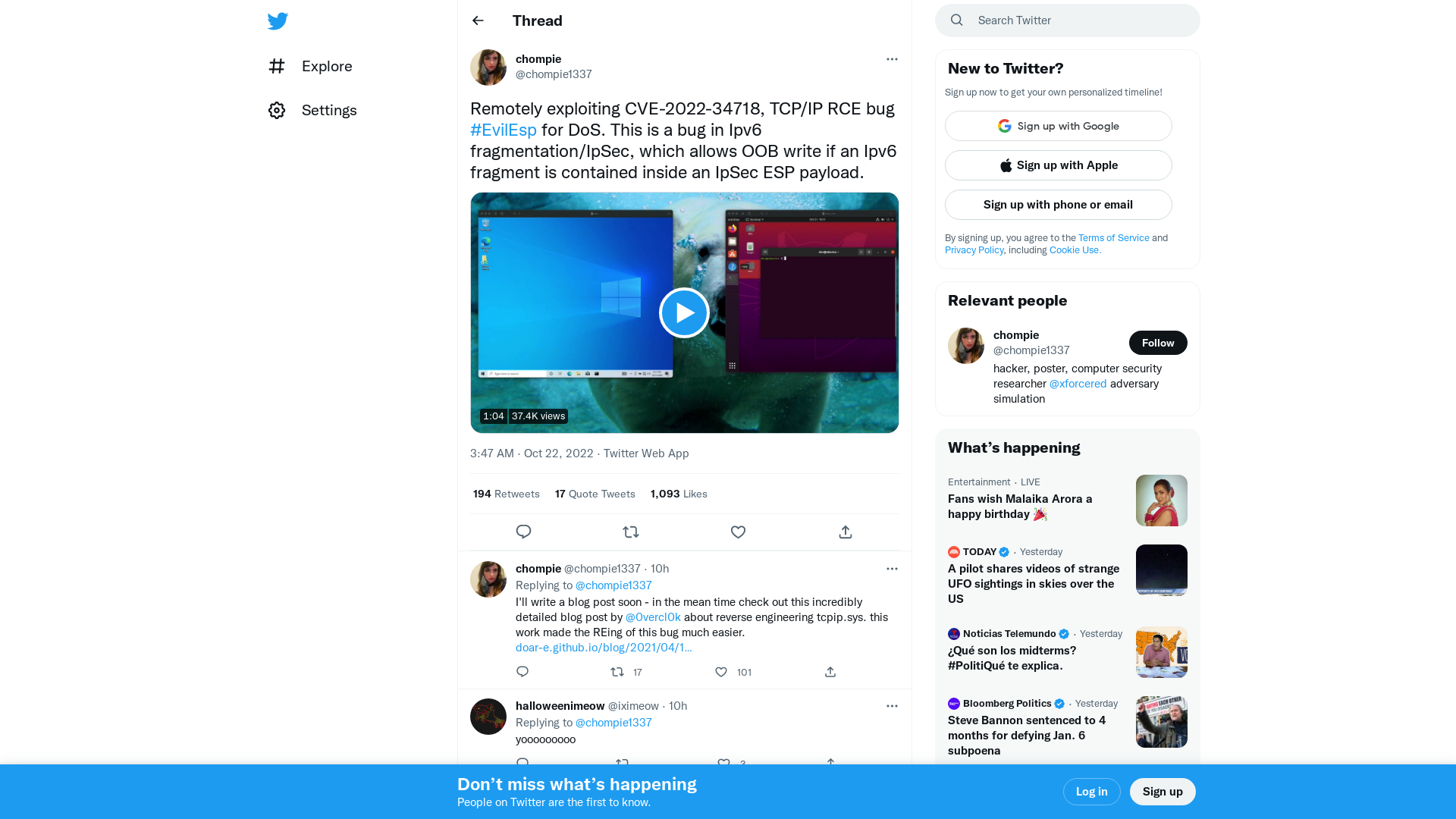
Antonio Cocomazzi on Twitter: "After 18 months #RemotePotato0 has been silently fixed 🥳 The downgrade attack performed in the ResolveOxid2 response (part of DCOM activation) does not work anymore and with the October 22 patch the client always authenticates with level INTEGRITY during the IRemUnkown bind https://t.co/UdRSgOd9cV" / Twitter
https://twitter.com/splinter_code/status/1583555613950255104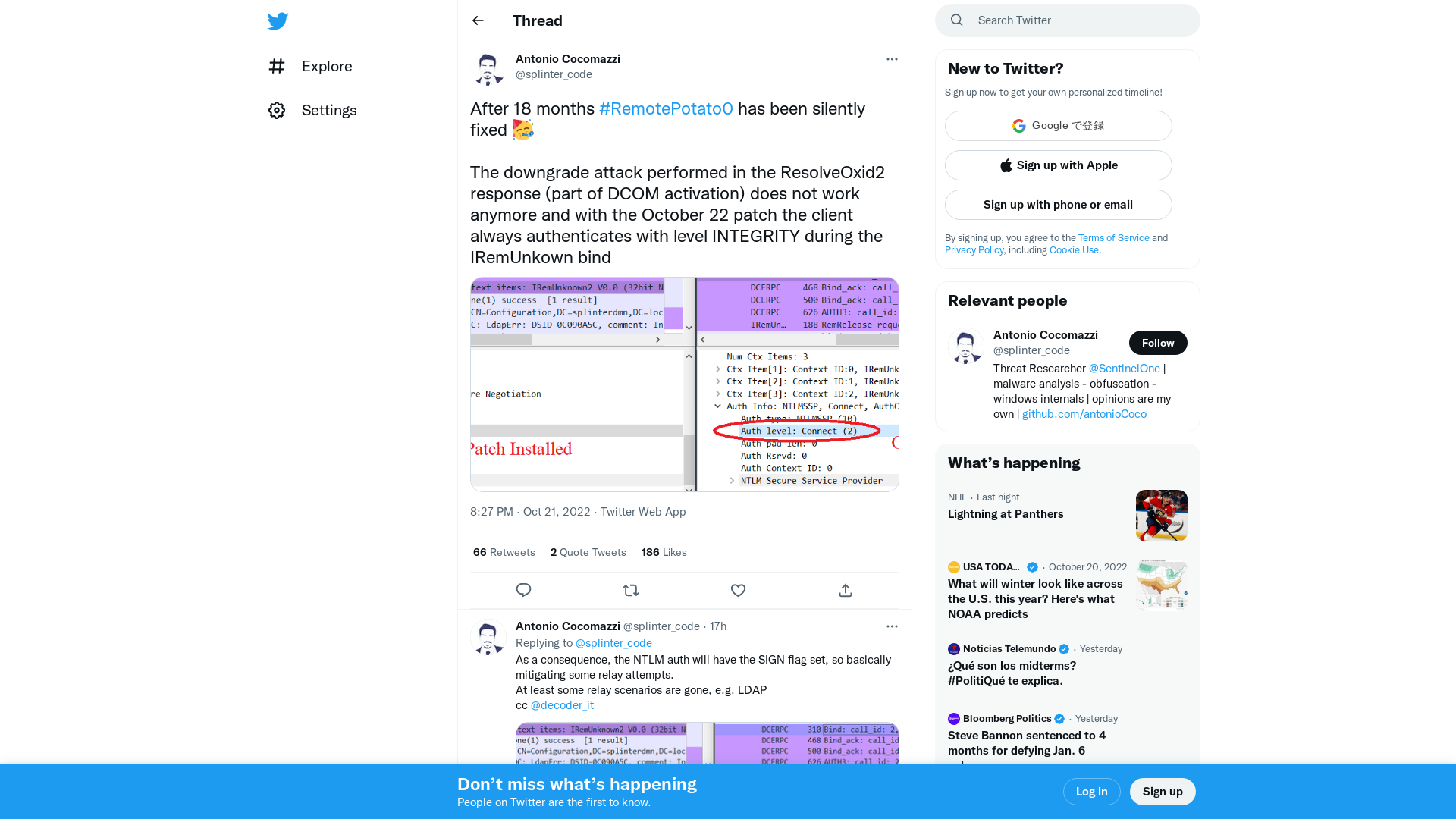
New release - 0.8.0
http://www.hashview.io/releases/2022/10/21/release-0-8-0.html
Modern Binary/Patch Diffing! / Twitter
https://twitter.com/i/broadcasts/1nAKErNBVWRGL
GitHub - decalage2/awesome-security-hardening: A collection of awesome security hardening guides, tools and other resources
https://github.com/decalage2/awesome-security-hardening
Fighting Golden Ticket Attacks with Privileged Attribute Certificate (PAC)
https://www.varonis.com/blog/pac_requestor-and-golden-ticket-attacks
Release Fuzzilli Version 0.9.2 · googleprojectzero/fuzzilli · GitHub
https://github.com/googleprojectzero/fuzzilli/releases/tag/v0.9.2
Andy Greenberg on Twitter: "The logical conclusion of the endless cycle of security vulnerabilities, active exploitation, and bypassed mitigations in Microsoft Exchange? “You need to move off of on-premise Exchange forever. That’s the bottom line." https://t.co/qvKUs1OBeD Even Microsoft seems to agree." / Twitter
https://twitter.com/a_greenberg/status/1583444843287568385
Wholesale giant METRO hit by IT outage after cyberattack
https://www.bleepingcomputer.com/news/security/wholesale-giant-metro-hit-by-it-outage-after-cyberattack/
CSI_EMBRACING_ZT_SECURITY_MODEL_UOO115131-21.PDF
https://media.defense.gov/2021/Feb/25/2002588479/-1/-1/0/CSI_EMBRACING_ZT_SECURITY_MODEL_UOO115131-21.PDF
Malware development: persistence - part 7. Winlogon. Simple C++ example. - cocomelonc
https://cocomelonc.github.io/tutorial/2022/06/12/malware-pers-7.html
BlackByte ransomware uses new data theft tool for double-extortion
https://www.bleepingcomputer.com/news/security/blackbyte-ransomware-uses-new-data-theft-tool-for-double-extortion/
GitHub - jimilinuxguy/lrs-pager-systems-bruteforce: Long Range Pager Systems pagers and coasters URH and YS1 (yardstick one / cc11xx) information and brute force tool
https://github.com/jimilinuxguy/lrs-pager-systems-bruteforce
Triage | Malware sandboxing report by Hatching Triage
https://tria.ge/221021-18va8ahdg8
Hackers Started Exploiting Critical "Text4Shell" Apache Commons Text Vulnerability
https://thehackernews.com/2022/10/hackers-started-exploiting-critical.html
Kerberos Golden Ticket PAC Updates for the Nov2021 Microsoft Updates by JoeDibley · Pull Request #380 · gentilkiwi/mimikatz · GitHub
https://github.com/gentilkiwi/mimikatz/pull/380
Android adware apps in Google Play downloaded over 20 million times
https://www.bleepingcomputer.com/news/security/android-adware-apps-in-google-play-downloaded-over-20-million-times/
GitHub - cisagov/ScubaGear: Automation to assess the state of your M365 tenant against CISA's baselines
https://github.com/cisagov/ScubaGear
Reverse-engineering tcpip.sys: mechanics of a packet of the death (CVE-2021-24086)
https://doar-e.github.io/blog/2021/04/15/reverse-engineering-tcpipsys-mechanics-of-a-packet-of-the-death-cve-2021-24086
VirusTotal - File - ca7f297dc04acad2fab04d5dc2de9475aed4186805f6c237c10b8f56b384cf30
https://www.virustotal.com/gui/file/ca7f297dc04acad2fab04d5dc2de9475aed4186805f6c237c10b8f56b384cf30/detection
MalwareBazaar | Browse Checking your browser
https://bazaar.abuse.ch/browse/tag/srvdwnld-com/
GitHub - D1rkMtr/PatchThatAMSI: this repo contains 6 AMSI patches , both force the triggering of a conditional jump inside AmsiOpenSession() that close the Amsi scanning session. The 1st patch by corrupting the Amsi context header and the 2nd patch by changing the string "AMSI" that will be compared to the Amsi context header to "D1RK". The other just set ZF to 1.
https://github.com/D1rkMtr/PatchThatAMSI
October 22, 2022 - by the grugq - The Info Op
https://grugq.substack.com/p/october-22-2022
GitHub - yeyintminthuhtut/Awesome-Red-Teaming: List of Awesome Red Teaming Resources
https://github.com/yeyintminthuhtut/Awesome-Red-Teaming
sn🥶vvcr💥sh on Twitter: "🧶 (5/) Inside the Sliver beacon I shall use the ‘impersonate’ module to steal the victim user token and execute Certify (available as an armory package) to request a brand new certificate on her behalf 📜 https://t.co/vyKeusnvmX" / Twitter
https://twitter.com/snovvcrash/status/1563247673553330177
Dear friends and countrymenAs a part of the Iranian hacker community and bor - Pastebin.com
https://pastebin.com/Pm4yfsac
Dave Kennedy on Twitter: "Friend that’s getting into security asked me if he should go Networking+ or Security+. First, certs aren’t something that I think are necessary in many cases however whatever can separate you from other resumes is a good thing. 1/2" / Twitter
https://twitter.com/hackingdave/status/1583811178614378497
vx-underground on Twitter: "Black Reward, an Iranian hacker group, claims to have breached the Iranian government and exfiltrated sensitive data related to their nuclear programs. They informed the Iranian government they have 24 hours to release political prisoners or they will release the documents. https://t.co/17J8rZfAHo" / Twitter
https://twitter.com/vxunderground/status/1583568821675126784
MalwareBazaar | Browse Checking your browser
https://bazaar.abuse.ch/browse/tag/206-188-196-244/
GRIMM Cyber on Twitter: "#GRIMMCon, our popular conference series believes in fostering new speakers, pairing them with mentors & welcoming them into the #cybersecurity community. GRIMMCon 0x8, will be on May 18, 2023. The theme is #inclusion. Stay tuned! #ShareTheMicInCyber #BelongingInCyber #dei https://t.co/phSMxLKUv6" / Twitter
https://twitter.com/grimmcyber/status/1583540707142561793
VirusTotal - File - f2779c63373e33fdbd001f336df36b01b0360cd6787c1cd29a6524cc7bcf1ffb
https://www.virustotal.com/gui/file/f2779c63373e33fdbd001f336df36b01b0360cd6787c1cd29a6524cc7bcf1ffb/detection