Orange: A New Attack Surface on MS Exchange Part 4 - ProxyRelay!
https://blog.orange.tw/2022/10/proxyrelay-a-new-attack-surface-on-ms-exchange-part-4.html
A New Attack Surface on MS Exchange Part 4 - ProxyRelay! | DEVCORE
https://devco.re/blog/2022/10/19/a-new-attack-surface-on-MS-exchange-part-4-ProxyRelay/
Microsoft Office Online Server Remote Code Execution - MDSec
https://www.mdsec.co.uk/2022/10/microsoft-office-online-server-remote-code-execution/
ProxyRelay - A New Attack Surface on Microsoft Exchange Server! - YouTube
https://www.youtube.com/watch?v=IFRvmo6AZoY
PHP filters chain: What is it and how to use it
https://www.synacktiv.com/publications/php-filters-chain-what-is-it-and-how-to-use-it.html
Defenders beware: A case for post-ransomware investigations - Microsoft Security Blog
https://www.microsoft.com/security/blog/2022/10/18/defenders-beware-a-case-for-post-ransomware-investigations/
MDSec on Twitter: "In our latest blog post, we publish a MS "won't fix" unauthenticated SSRF to RCE in Microsoft Office Online Server https://t.co/x8BQGnckiC by @IndiShell1046 https://t.co/30vkPJTjJI" / Twitter
https://twitter.com/MDSecLabs/status/1582649850512150528
HTTP/3 connection contamination: an upcoming threat? | PortSwigger Research
https://portswigger.net/research/http-3-connection-contamination
Catalin Cimpanu on Twitter: "Security researcher Orange Tsai published today details on ProxyRelay, the fourth major vulnerability he found in Exchange servers. Previous include: -ProxyLogon -ProxyOracle -ProxyShell Blog: https://t.co/XxHFpqRaL2 Demo here: https://t.co/58BddTYSuc" / Twitter
https://twitter.com/campuscodi/status/1582459815531466753
Update About the 0-day Industry. In the past year or so, the active… | by Maor Shwartz | Oct, 2022 | Medium
https://medium.com/@maor_s/update-about-the-0-day-industry-8d8bb49e8dbb
VirusTotal - File - 725ca9e0571a6651e1bcf7dcf5d921fb004e753d67bfd135bd61f178b8aa5e4c
https://www.virustotal.com/gui/file/725ca9e0571a6651e1bcf7dcf5d921fb004e753d67bfd135bd61f178b8aa5e4c/detection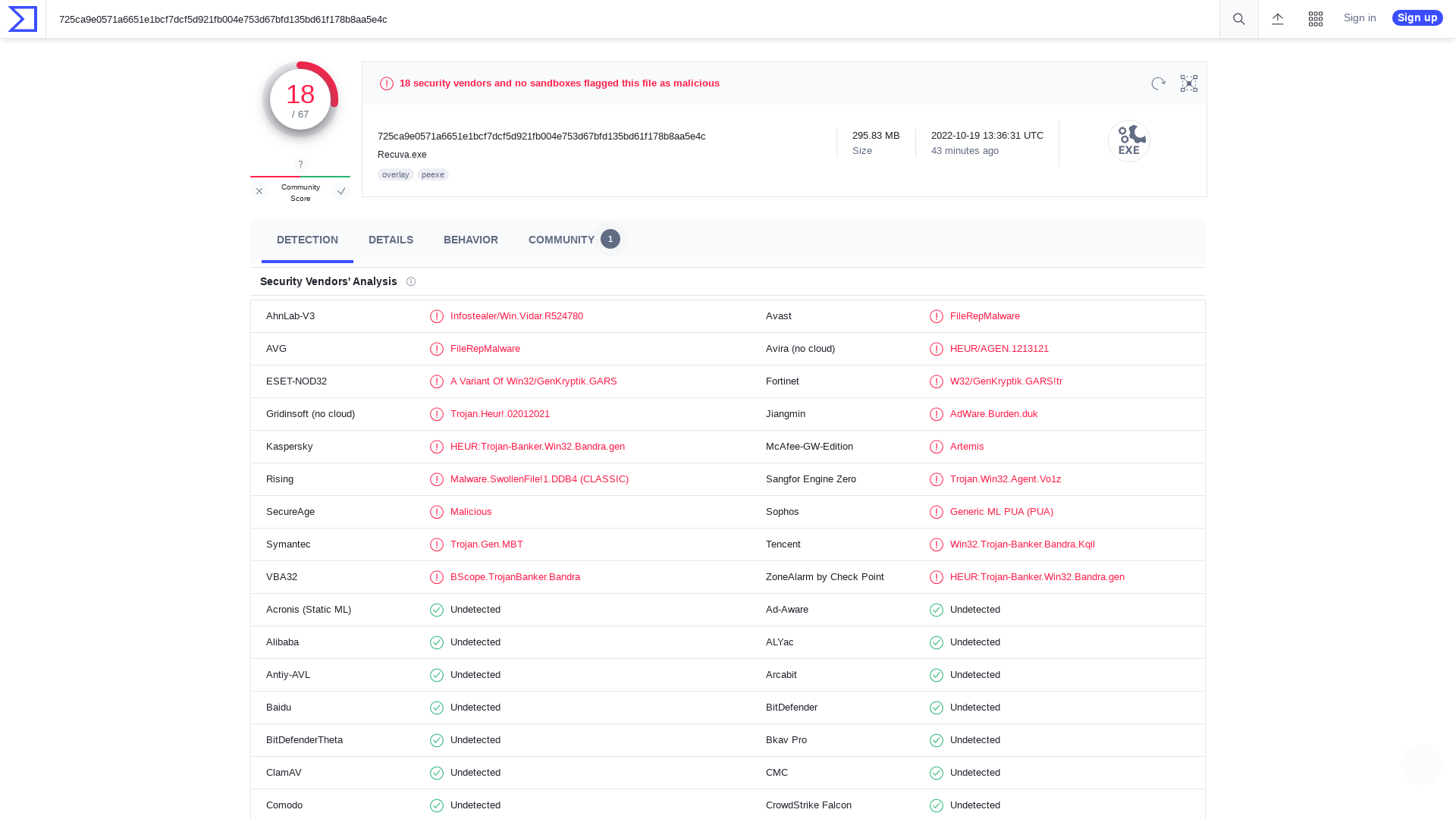
Guest Blog Post - Memory corruption vulnerabilities in Edge | Microsoft Browser Vulnerability Research
https://microsoftedge.github.io/edgevr/posts/memory-corruption-vulnerabilities-in-edge/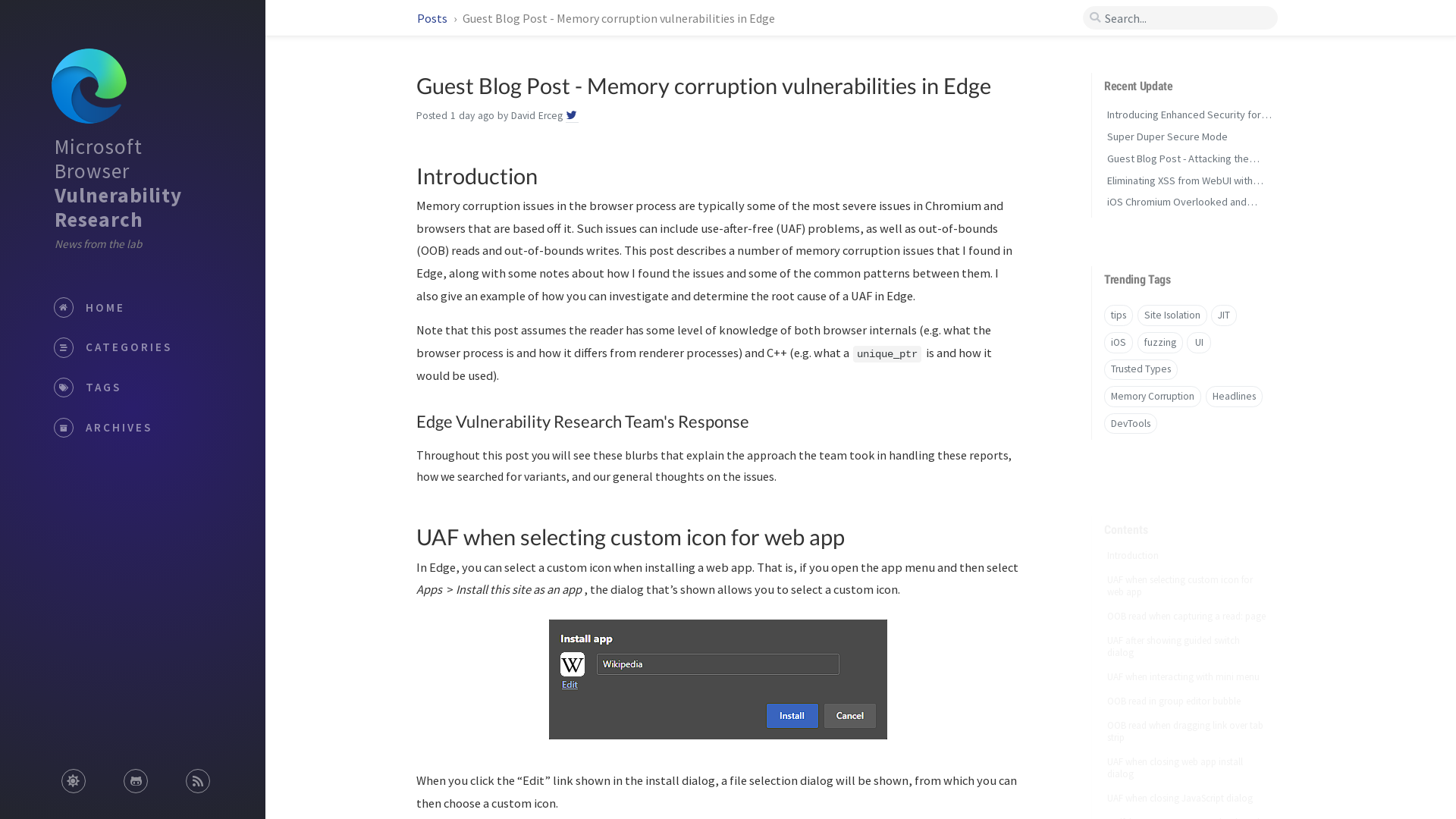
Hexacon - Conference – Speakers
https://2022.hexacon.fr/conference/speakers/
Consortium led by Smartfin acquires leading cybersecurity software provider Hex-Rays - Smartfin
https://smartfinvc.com/news/smartfin-acquires-leading-cybersecurity-software-provider-hex-rays-together-with-sfpim-and-sriw/
‘They said: aren’t you that porn star?’ The woman hunting down image-based abuse | Sexual harassment | The Guardian
https://www.theguardian.com/global-development/2022/oct/19/they-said-arent-you-that-porn-star-the-woman-hunting-down-image-based-abuse
Apache Commons Text flaw is not a repeat of Log4Shell (CVE-2022-42889) - Help Net Security
https://www.helpnetsecurity.com/2022/10/19/cve-2022-42889/
Verizon notifies prepaid customers their accounts were breached
https://www.bleepingcomputer.com/news/security/verizon-notifies-prepaid-customers-their-accounts-were-breached/
23000$ for Authentication Bypass & File Upload & Arbitrary File Overwrite | by h4x0r_dz | Oct, 2022 | Medium
https://medium.com/@h4x0r_dz/23000-for-authentication-bypass-file-upload-arbitrary-file-overwrite-2578b730a5f8
GitHub - zimawhit3/Bitmancer: Nim Library for Offensive Security Development
https://github.com/zimawhit3/Bitmancer
Researchers Detail Azure SFX Flaw That Could've Allowed Attackers to Gain Admin Access
https://thehackernews.com/2022/10/researchers-detail-azure-sfx-flaw-that.html
Experts Warn of Stealthy PowerShell Backdoor Disguising as Windows Update
https://thehackernews.com/2022/10/experts-warn-of-stealthy-powershell.html
Browser Exploitation: Firefox OOB to RCE • Vulndev
https://vulndev.io/2022/09/09/browser-exploitation-firefox-oob-to-rce/
Changing memory protection using APC
https://blog.offensive.af/changing-memory-protection-using-apc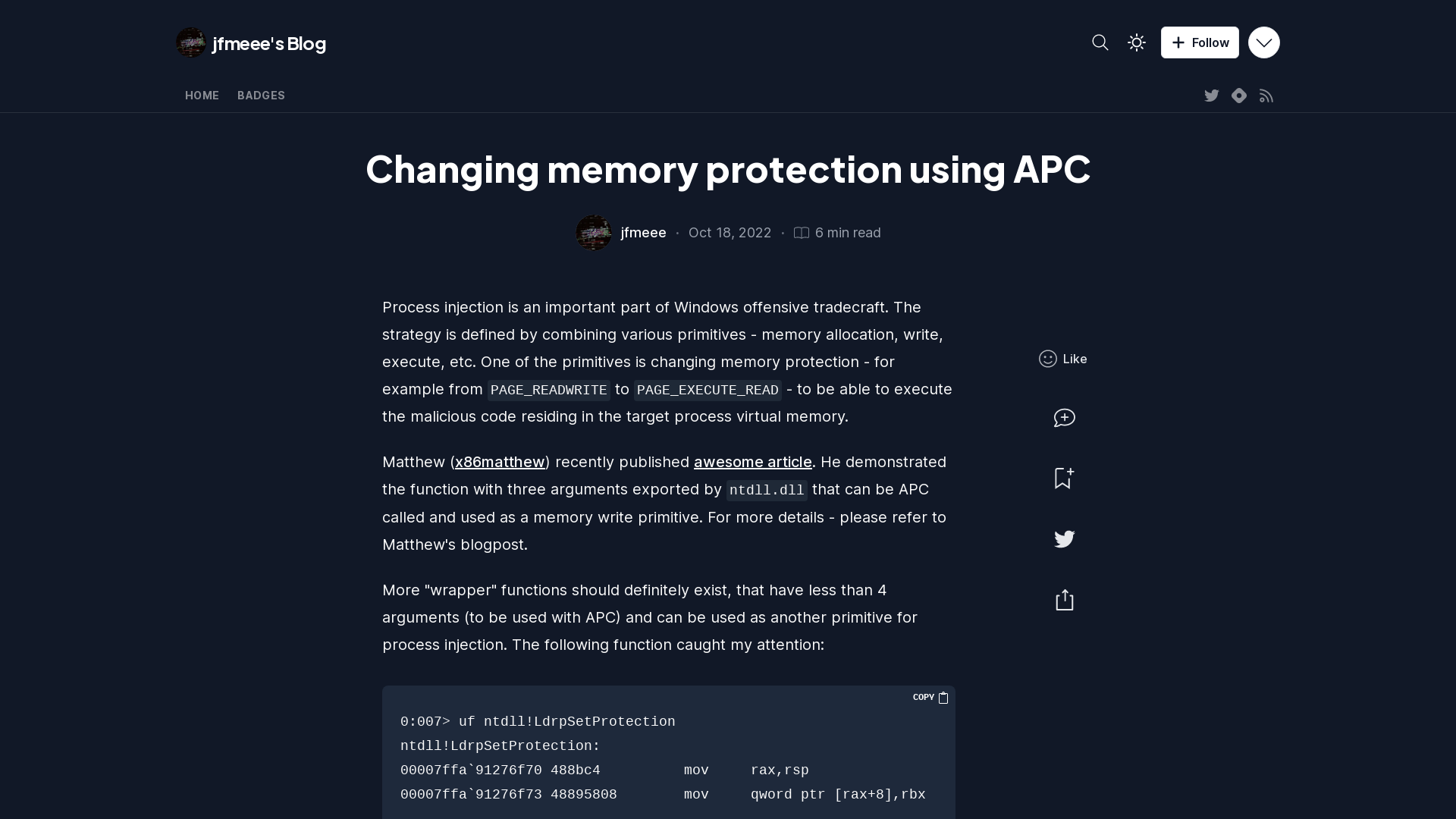
Rob Joyce on Twitter: "We are getting better at sanitizing sensitive intelligence to enable cybersecurity. What we know is only useful if someone can use it. https://t.co/WDli5FI4ut" / Twitter
https://twitter.com/nsa_csdirector/status/1582688840359084032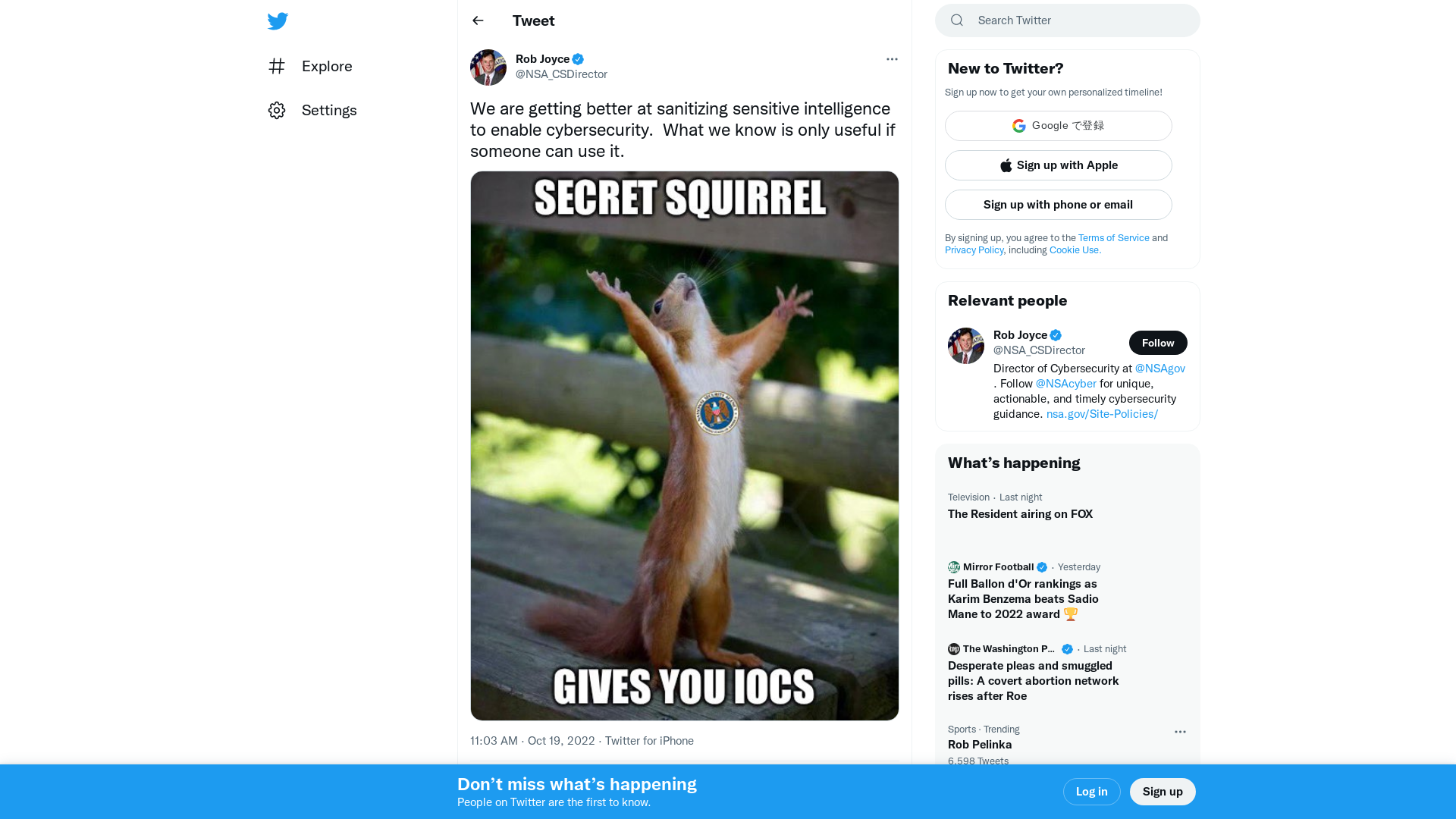
Spyder Loader: Malware Seen in Recent Campaign Targeting Organizations in Hong Kong | Symantec Enterprise Blogs
https://symantec-enterprise-blogs.security.com/blogs/threat-intelligence/spyder-loader-cuckoobees-hong-kong
GitHub - olafhartong/sysmon-parser: Automatically generated Sysmon parser for Azure Sentinel
https://github.com/olafhartong/sysmon-parser/