How to Investigate Insider Threats (Forensic Methodology)
https://www.inversecos.com/2022/10/how-to-investigate-insider-threats.html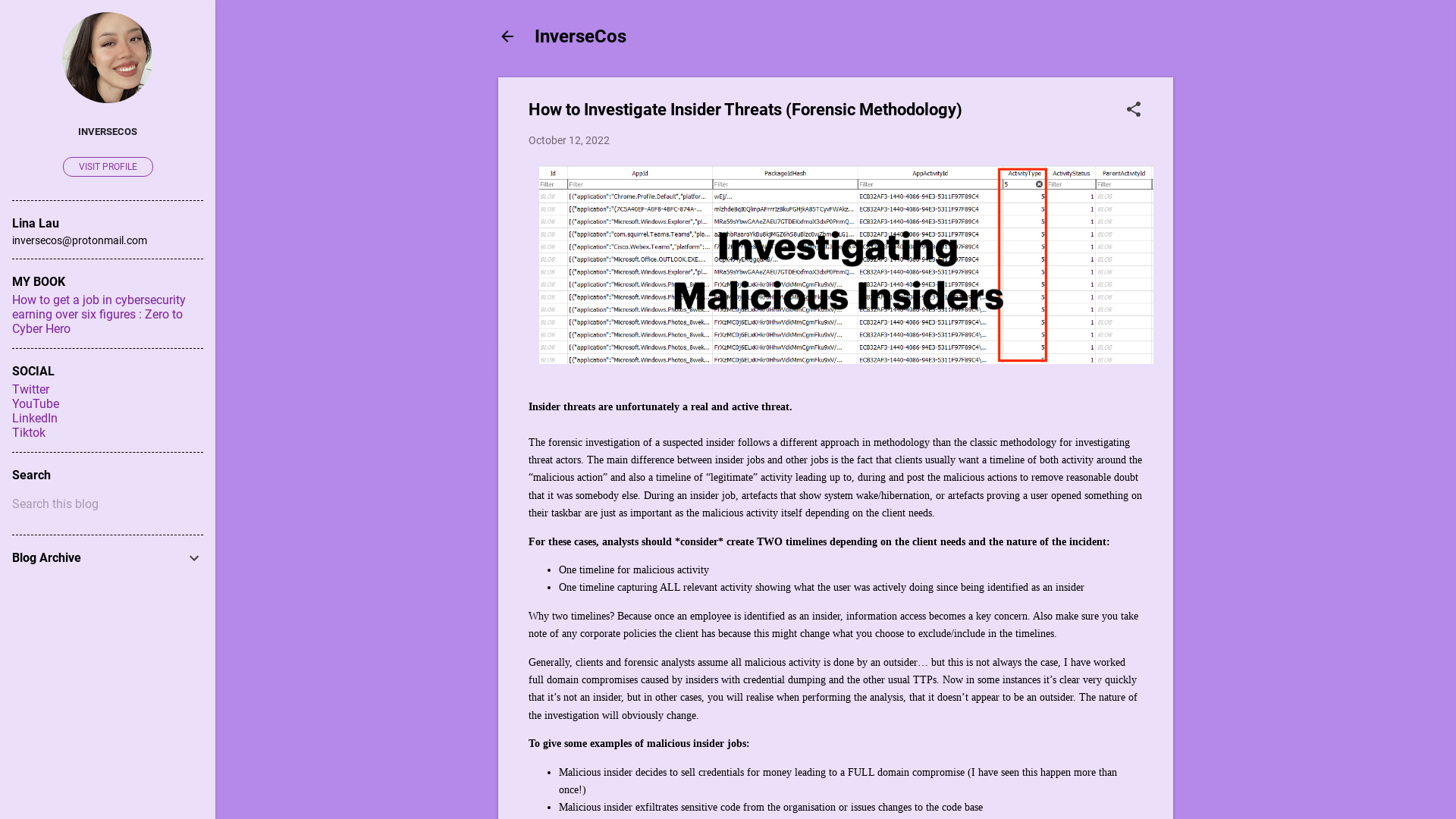
Pen Test Partners on Twitter: "Our @_EthicalChaos_ found that you could remotely install Windows Store apps and execute privileged services on the latest versions of Windows. This post has all the juicy CVE-2022-35841 details https://t.co/R4EyMaidrh #rce #cve https://t.co/Jy0Yms6AUj" / Twitter
https://twitter.com/PenTestPartners/status/1580480583137779712
Qakbot/Qakbot_BB_12.10.2022.txt at main · pr0xylife/Qakbot · GitHub
https://github.com/pr0xylife/Qakbot/blob/main/Qakbot_BB_12.10.2022.txt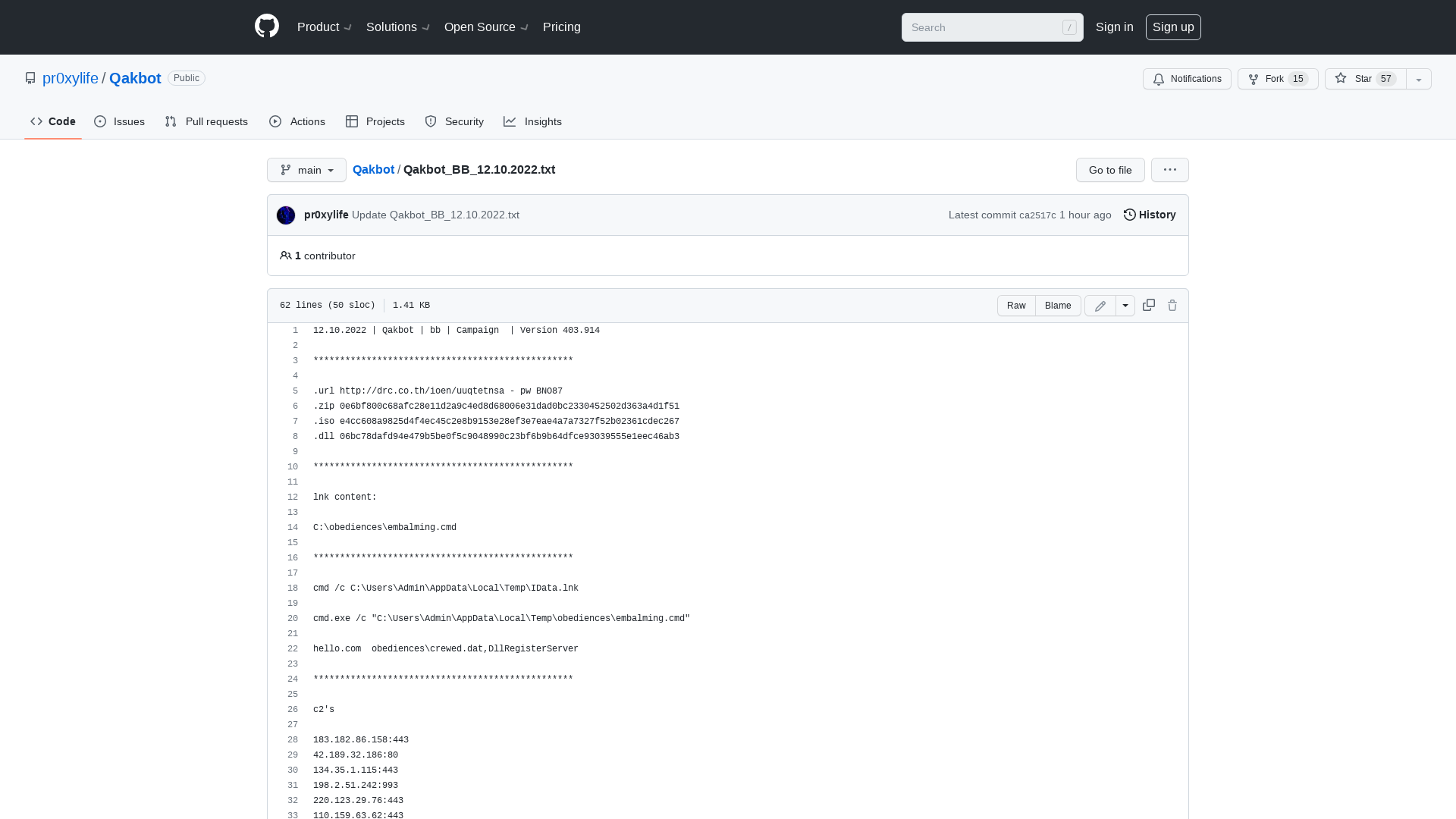
New Chinese Malware Attack Framework Targets Windows, macOS, and Linux Systems
https://thehackernews.com/2022/10/new-chinese-malware-attack-framework.html
Budworm: Espionage Group Returns to Targeting U.S. Organizations | Broadcom Software Blogs
https://symantec-enterprise-blogs.security.com/blogs/threat-intelligence/budworm-espionage-us-state
Lazarus Group Uses the DLL Side-Loading Technique (mi.dll) - ASEC BLOG
https://asec.ahnlab.com/en/39828/
Dwight Rhinosoros on Twitter: "We talk a lot about the militarization of police and not enough about the militarization of sales bros. https://t.co/jOOS1yBFXq" / Twitter
https://twitter.com/rhinosoros/status/1580236256314654729
Researchers Uncover Custom Backdoors and Spying Tools Used by Polonium Hackers
https://thehackernews.com/2022/10/researchers-uncover-custom-backdoors.html
Black Basta Ransomware Gang Infiltrates networks via QAKBOT, Brute Ratel, and Cobalt Strike
https://research.trendmicro.com/3TdFUBq
WIP19 Espionage | New Chinese APT Targets IT Service Providers and Telcos With Signed Malware - SentinelOne
https://www.sentinelone.com/labs/wip19-espionage-new-chinese-apt-targets-it-service-providers-and-telcos-with-signed-malware/
Ongoing exploitation of CVE-2022-41352 (Zimbra 0-day) | Securelist
https://securelist.com/ongoing-exploitation-of-cve-2022-41352-zimbra-0-day/107703/
Cisco Talos Intelligence Group - Comprehensive Threat Intelligence: Alchimist: A new attack framework in Chinese for Mac, Linux and Windows
https://blog.talosintelligence.com/2022/10/alchimist-offensive-framework.html
Daniel Cuthbert on Twitter: "I do apologise for the language but just f*** off now with this bullshit. We've had enough of threat intel firms/ambulance chasers telling us how the dark web was the hotbed of all criminality, and now this? GTFO https://t.co/Nb4Z0VKrfw" / Twitter
https://twitter.com/dcuthbert/status/1580558022576726017
BountyTricks/CVE-2022-40684.yaml at main · NagliNagli/BountyTricks · GitHub
https://github.com/NagliNagli/BountyTricks/blob/main/CVE-2022-40684.yaml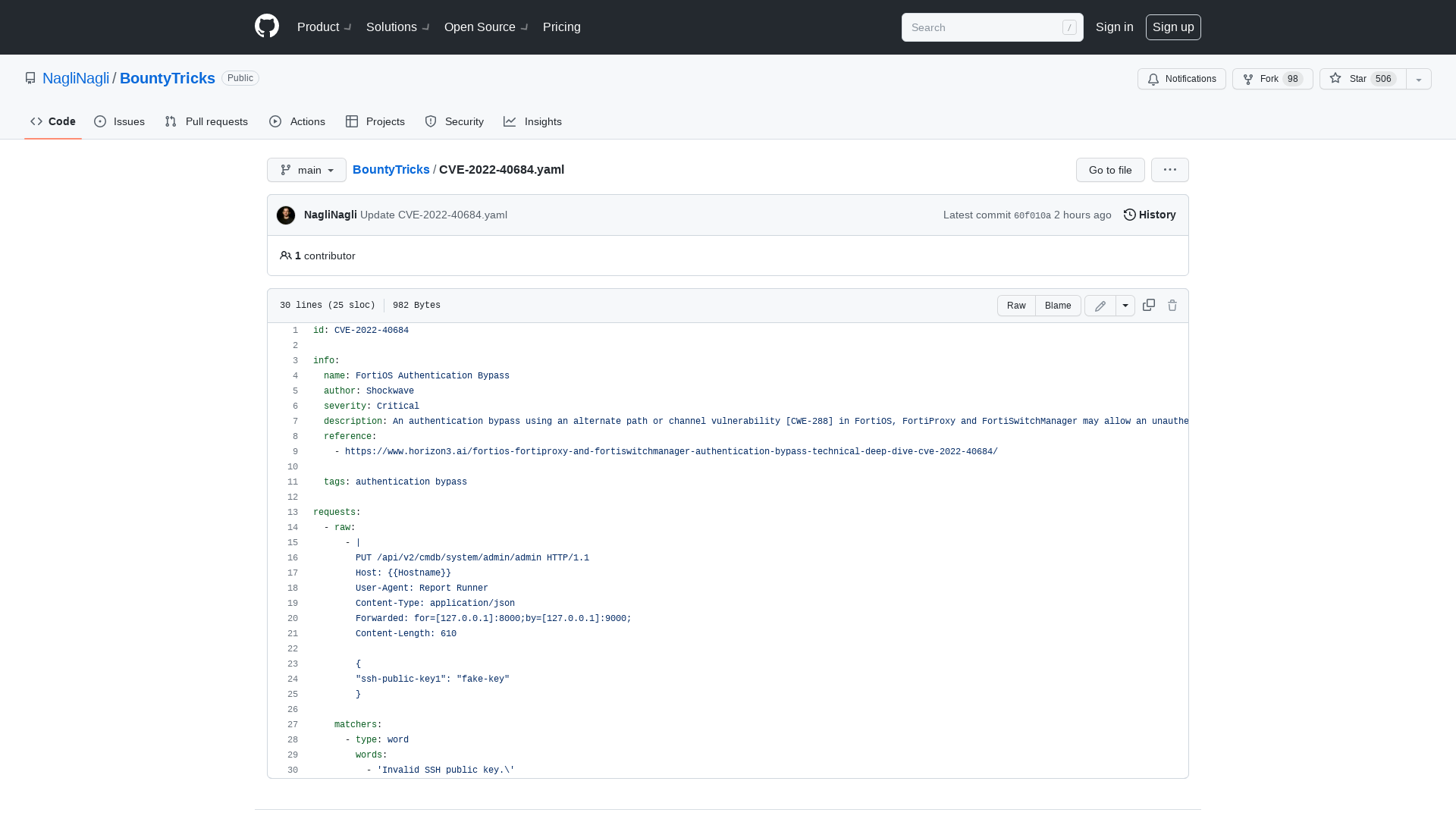
GreyNoise Trends
https://viz.greynoise.io/tag/fortios-authentication-bypass-attempt?days=3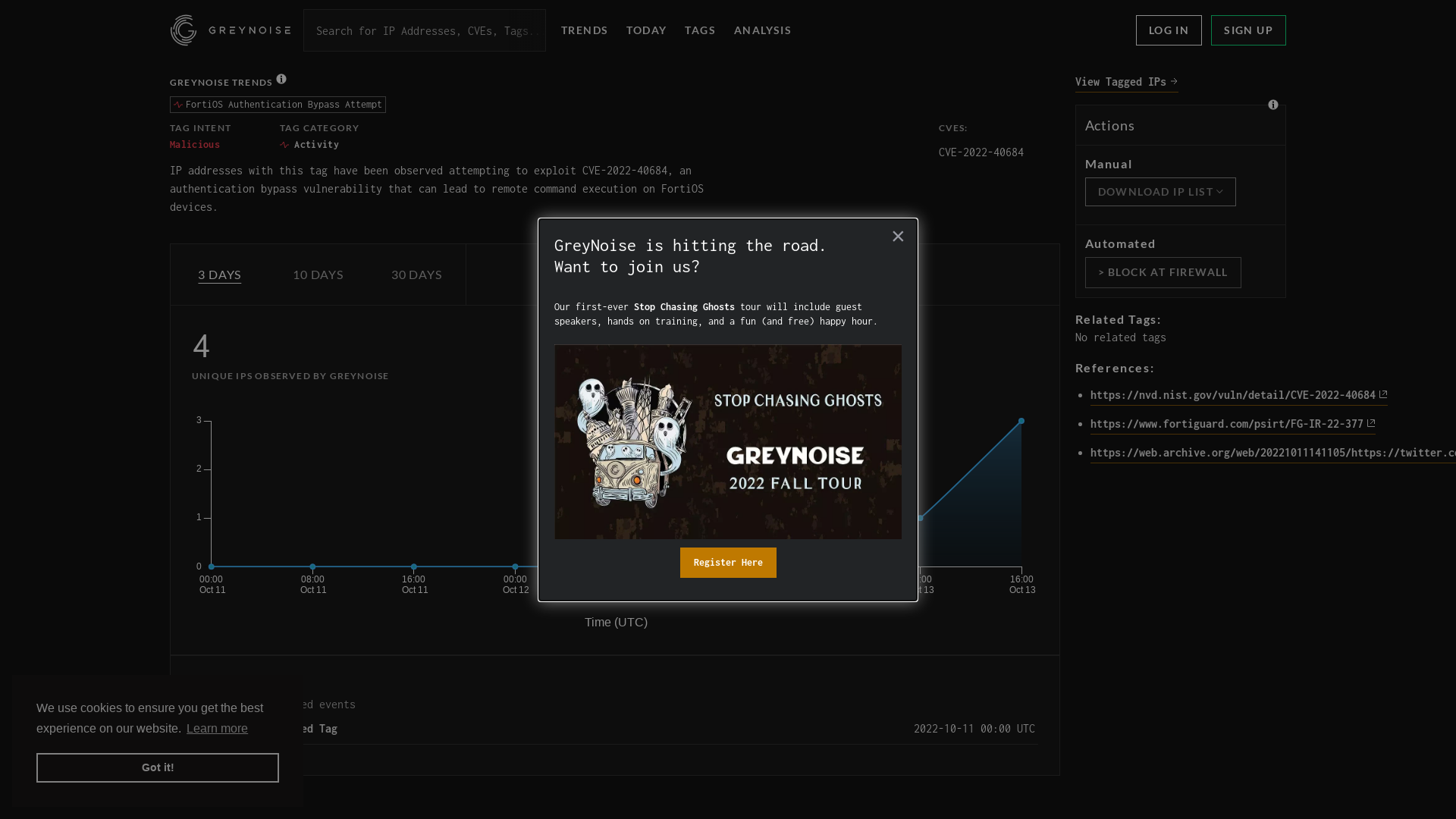
Microsoft Defender adds command and control traffic detection
https://www.bleepingcomputer.com/news/microsoft/microsoft-defender-adds-command-and-control-traffic-detection/
Linux Kernel Exploit (CVE-2022-32250) with mqueue | Theori
https://blog.theori.io/research/CVE-2022-32250-linux-kernel-lpe-2022/
GitHub - ORCx41/AtomPePacker: A Highly capable Pe Packer
https://github.com/ORCx41/AtomPePacker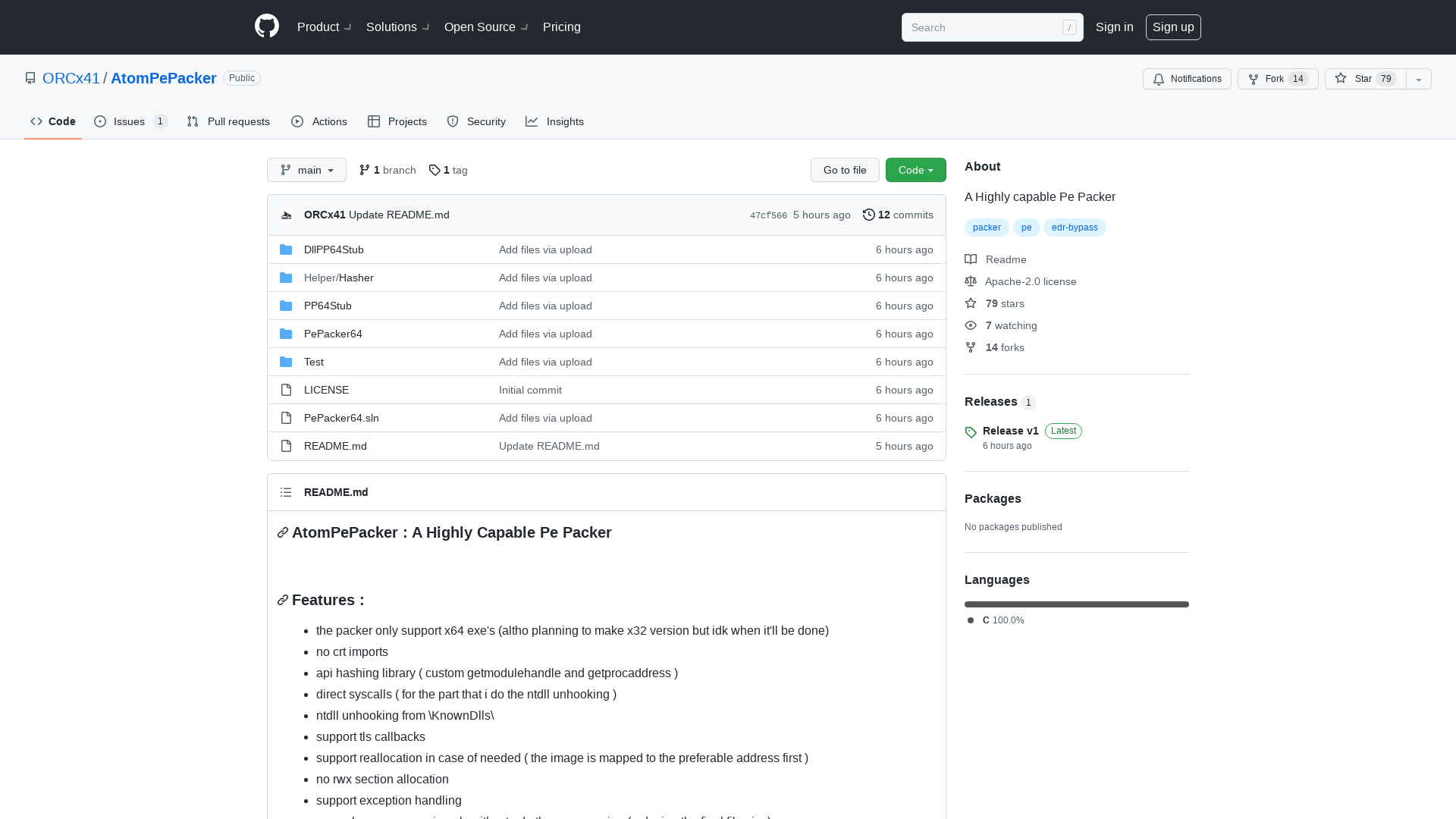
New Alchimist attack framework targets Windows, macOS, Linux
https://www.bleepingcomputer.com/news/security/new-alchimist-attack-framework-targets-windows-macos-linux/
Malign Influence During the 2022 US Midterm Elections
https://www.recordedfuture.com/malign-influence-during-the-2022-us-midterm-elections-disinformation-misinformation
GreyNoise on Twitter: "GreyNoise has observed the first IP exploiting CVE-2022-40684, FortiOS Authentication Bypass Attempt. The IP leveraged the authentication bypass and attempted to export a backup of the FortiOS configuration. https://t.co/AknYbOfLYn https://t.co/zdpKHYB1Kk" / Twitter
https://twitter.com/GreyNoiseIO/status/1580557335231365123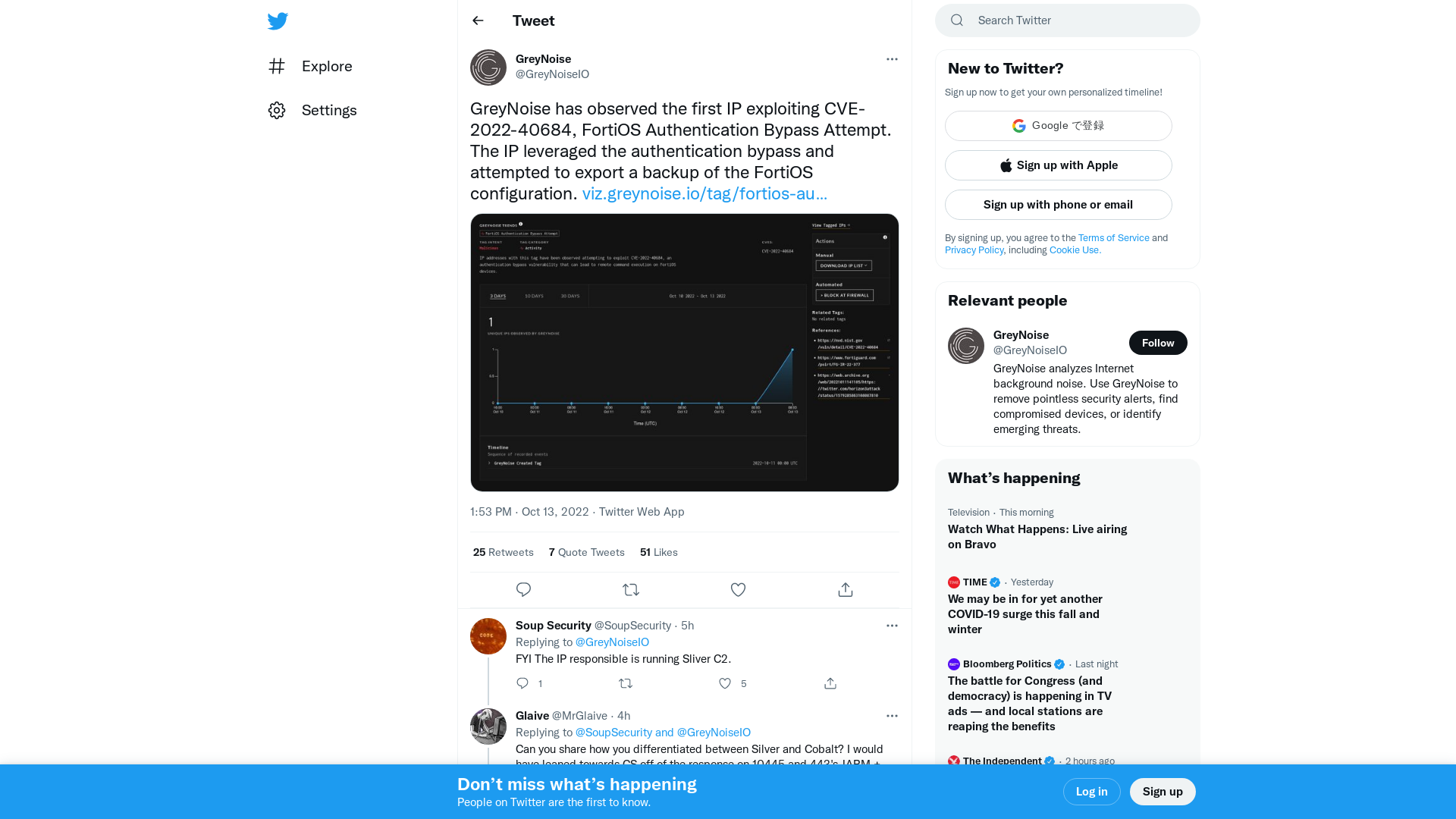
Android Developers Blog: Bringing passkeys to Android & Chrome
https://android-developers.googleblog.com/2022/10/bringing-passkeys-to-android-and-chrome.html
Pwning ManageEngine — From Endpoint to Exploit | by Erik Wynter | Oct, 2022 | Medium
https://medium.com/@erik.wynter/pwning-manageengine-from-endpoint-to-exploit-bc5793836fd