CVE-2022-41352 | AttackerKB
https://attackerkb.com/topics/1DDTvUNFzH/cve-2022-41352/rapid7-analysis
Fortinet warns admins to patch critical auth bypass bug immediately
https://www.bleepingcomputer.com/news/security/fortinet-warns-admins-to-patch-critical-auth-bypass-bug-immediately/
FortiOS Release Notes | FortiGate / FortiOS 7.2.2 | Fortinet Documentation Library
https://docs.fortinet.com/document/fortigate/7.2.2/fortios-release-notes/760203/introduction-and-supported-models
2*yo on Twitter: "Looks like a new critical admin GUI vulnerability that allows attackers to bypass the admin authentication is coming on FortiGate and FortiProxy. Anyone could share the Fortinet Customer Support Bulletin CSB-221006-1 ? Is it already exploited @GreyNoiseIO ? #vuln #cve?" / Twitter
https://twitter.com/2xyo/status/1578123357840703518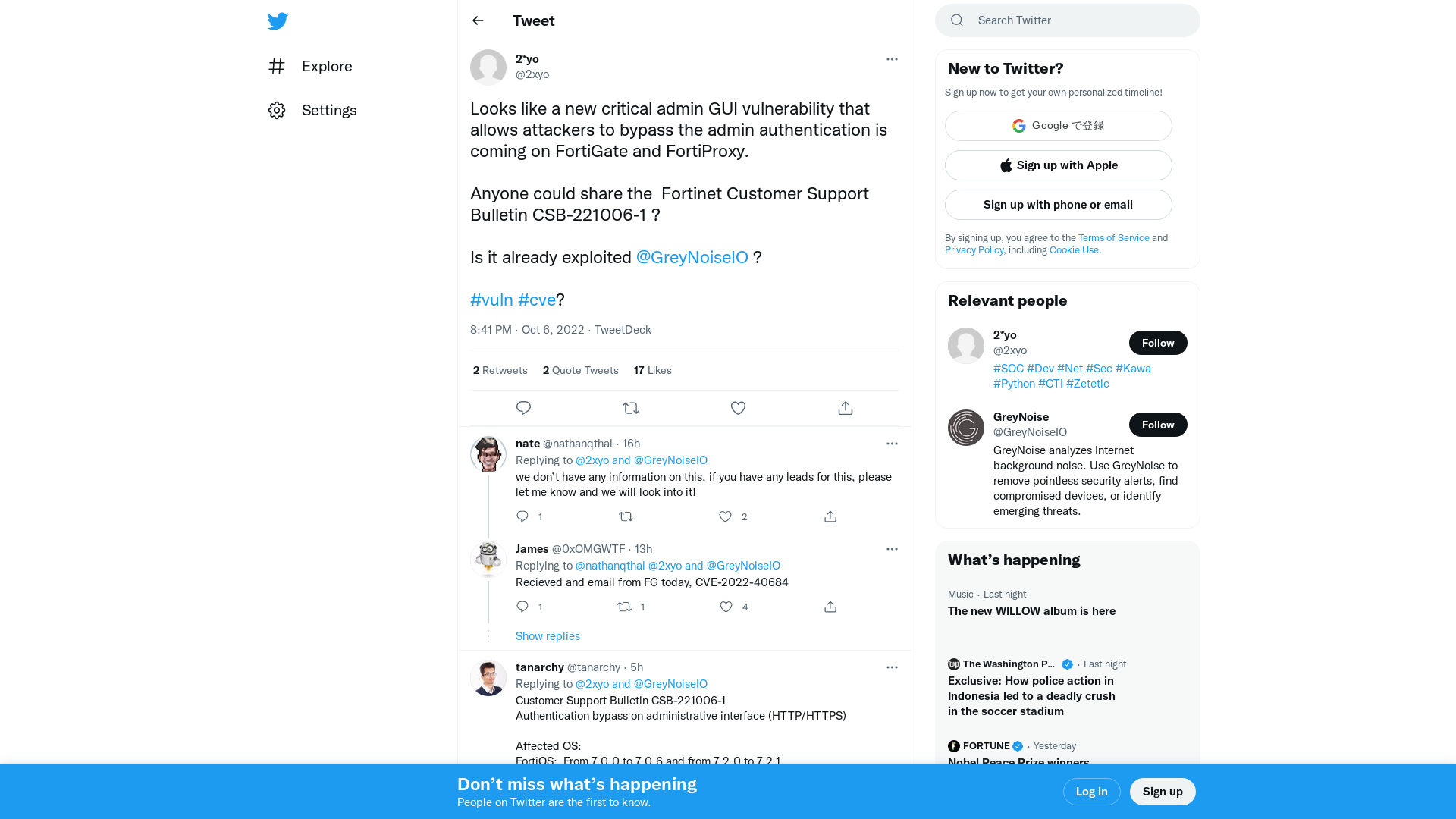
NSA, CISA, FBI Reveal Top CVEs Exploited by Chinese State-Sponsored Actors > National Security Agency/Central Security Service > Press Release View
https://www.nsa.gov/Press-Room/Press-Releases-Statements/Press-Release-View/Article/3181261/nsa-cisa-fbi-reveal-top-cves-exploited-by-chinese-state-sponsored-actors/
Joint_CSA_Top_CVEs_Exploited_by_PRC_cyber_actors_.PDF
https://media.defense.gov/2022/Oct/06/2003092365/-1/-1/0/Joint_CSA_Top_CVEs_Exploited_by_PRC_cyber_actors_.PDF
Hacker steals $566 million worth of crypto from Binance Bridge
https://www.bleepingcomputer.com/news/security/hacker-steals-566-million-worth-of-crypto-from-binance-bridge/
GitHub - med0x2e/vba2clr: Running .NET from VBA
https://github.com/med0x2e/vba2clr
Hackers Can Use 'App Mode' in Chromium Browsers' for Stealth Phishing Attacks
https://thehackernews.com/2022/10/hackers-can-use-app-mode-in-chromium.html
VirusTotal - Search - crowdsourced_yara_rule:000b20879c|MAL_QBot_HTML_Smuggling_Indicators_Oct22_1
https://www.virustotal.com/gui/search/crowdsourced_yara_rule%253A000b20879c%257CMAL_QBot_HTML_Smuggling_Indicators_Oct22_1/files
Florian Roth ⚡ on Twitter: "@ankit_anubhav @Max_Mal_ @1ZRR4H @0xToxin @pr0xylife I wrote a rule based on that info - I hope it covers them all https://t.co/G64P4CFnuB https://t.co/0Pl19Z4xvD" / Twitter
https://twitter.com/cyb3rops/status/1578297065754398720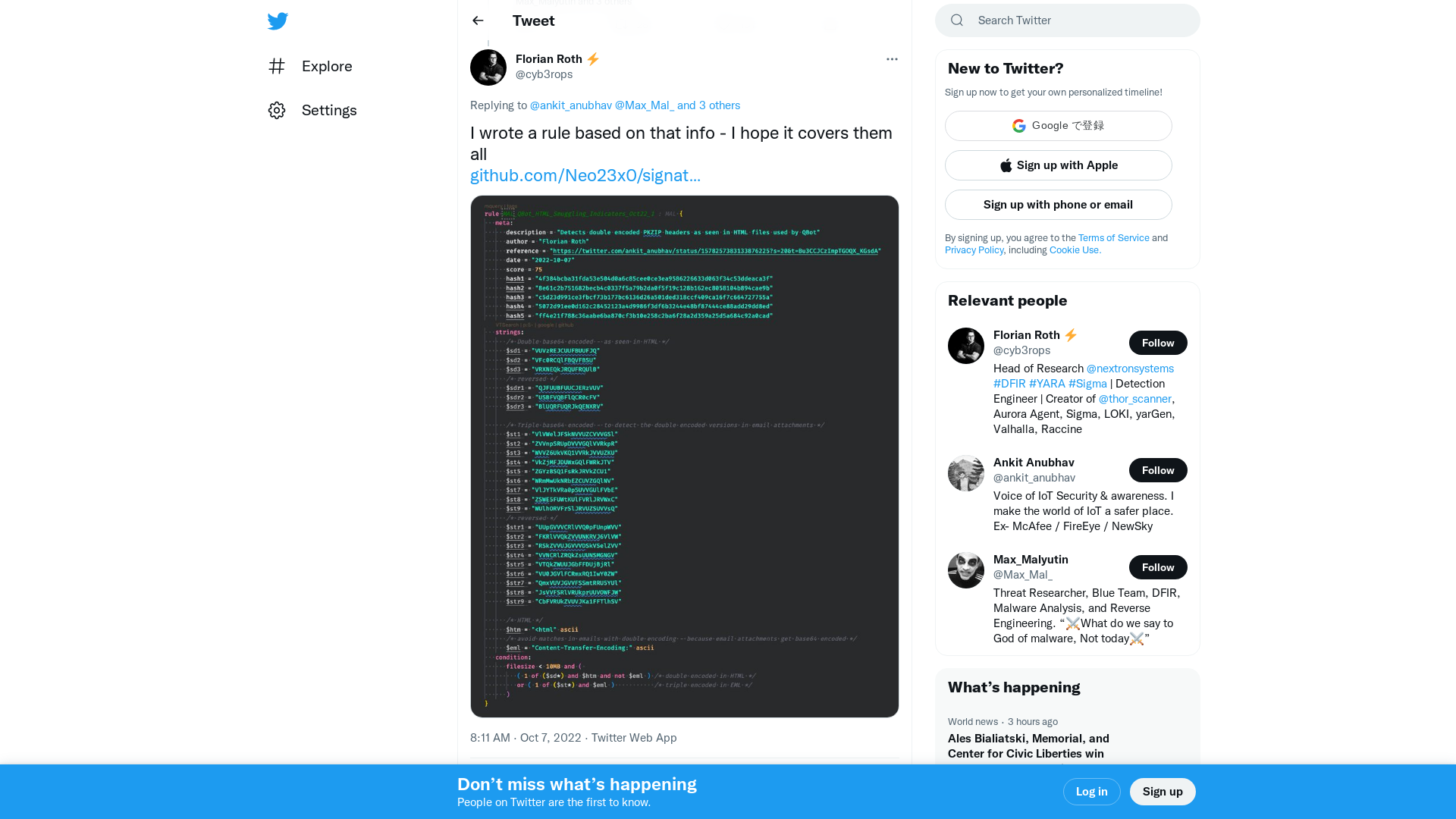
abuse-of-legitimate-security-tools-and-the-hph.pdf
https://www.hhs.gov/sites/default/files/abuse-of-legitimate-security-tools-and-the-hph.pdf
Rikhard Husu on Twitter: "Finnish prime minister Sanna Marin was asked about a potential off-ramp for Russia to end the war in Ukraine. Her reply: https://t.co/VblWxkMuFc" / Twitter
https://twitter.com/RikhardHusu/status/1578308226709590017
BlackByte Ransomware Abuses Vulnerable Windows Driver to Disable Security Solutions
https://thehackernews.com/2022/10/blackbyte-ransomware-abuses-vulnerable.html
ARM64 support for SyscallDumper · daem0nc0re/AtomicSyscall@a21c88c · GitHub
https://github.com/daem0nc0re/AtomicSyscall/commit/a21c88c53a0d117d60ee17a0eae717e7680b7db2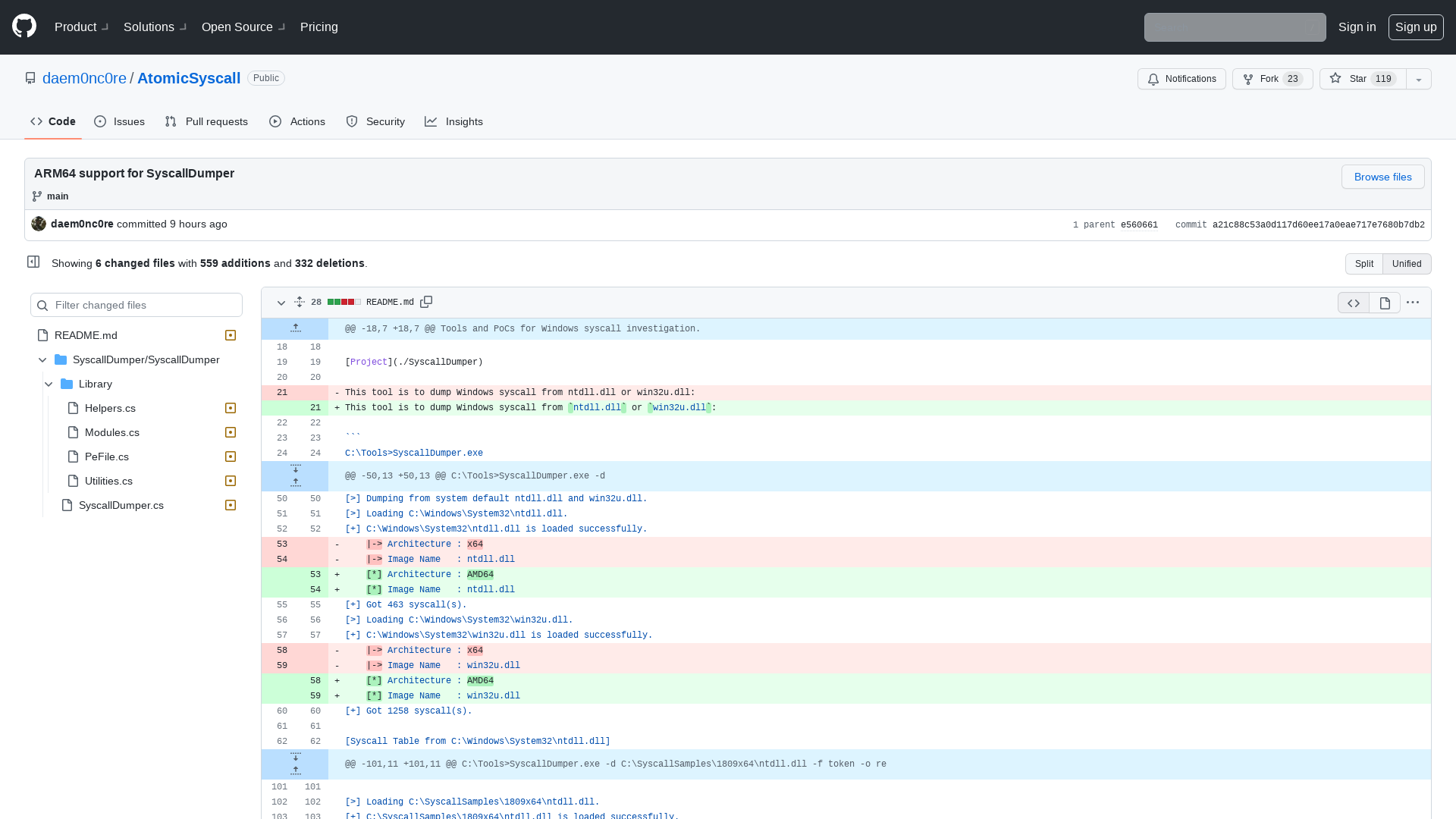
GitHub - jamf/aftermath: Aftermath is a free macOS IR framework
https://github.com/jamf/aftermath
Melting the DNS Iceberg: Taking over your infrastructure Kaminsky style
https://sec-consult.com/blog/detail/melting-the-dns-iceberg-taking-over-your-infrastructure-kaminsky-style/
Catalin Cimpanu on Twitter: "The NSA, CISA, and the FBI have published a joint advisory on Thursday with a list of the top 20 vulnerabilities exploited by Chinese state-sponsored threat groups. Presser: https://t.co/GMUnDlBSFJ PDF: https://t.co/ROjLfJJay6 https://t.co/K6qPSILDZX" / Twitter
https://twitter.com/campuscodi/status/1578109267961212928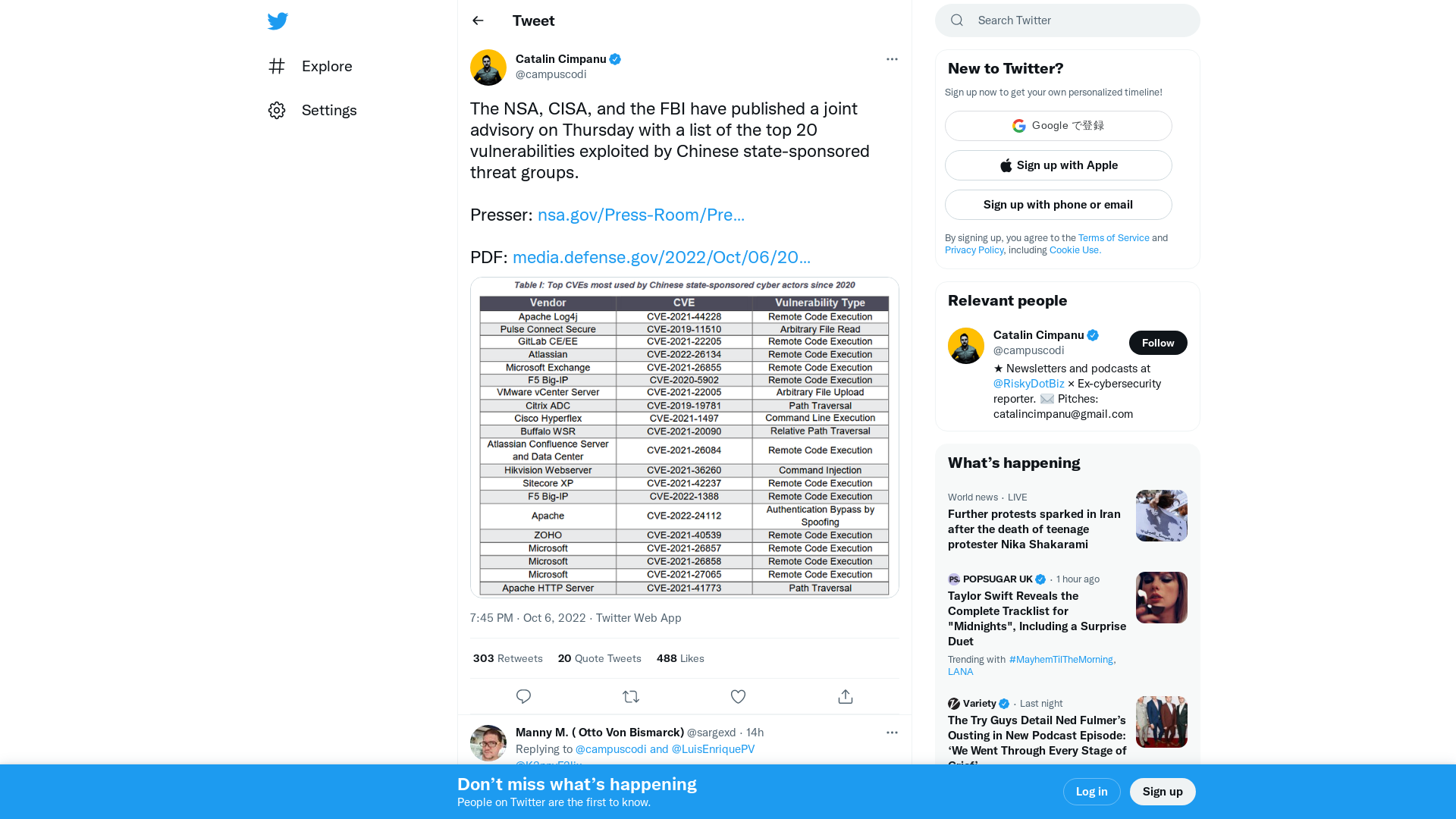
DEF CON 30 - Melvin Langvik - Taking a Dump In The Cloud (TeamFiltration) - YouTube
https://youtu.be/GpZTQHLKelg
Putin confronted by insider over Ukraine war, U.S. intelligence finds - The Washington Post
https://www.washingtonpost.com/national-security/2022/10/07/putin-inner-circle-dissent/