Customer Guidance for Reported Zero-day Vulnerabilities in Microsoft Exchange Server – Microsoft Security Response Center
https://msrc-blog.microsoft.com/2022/09/29/customer-guidance-for-reported-zero-day-vulnerabilities-in-microsoft-exchange-server/
GitHub - HavocFramework/Havoc: The Havoc Framework
https://github.com/HavocFramework/Havoc
ZDI-CAN-18333 aka ProxyNotShell— the story of the claimed zero day in Microsoft Exchange | by Kevin Beaumont | Sep, 2022 | DoublePulsar
https://doublepulsar.com/proxynotshell-the-story-of-the-claimed-zero-day-in-microsoft-exchange-5c63d963a9e9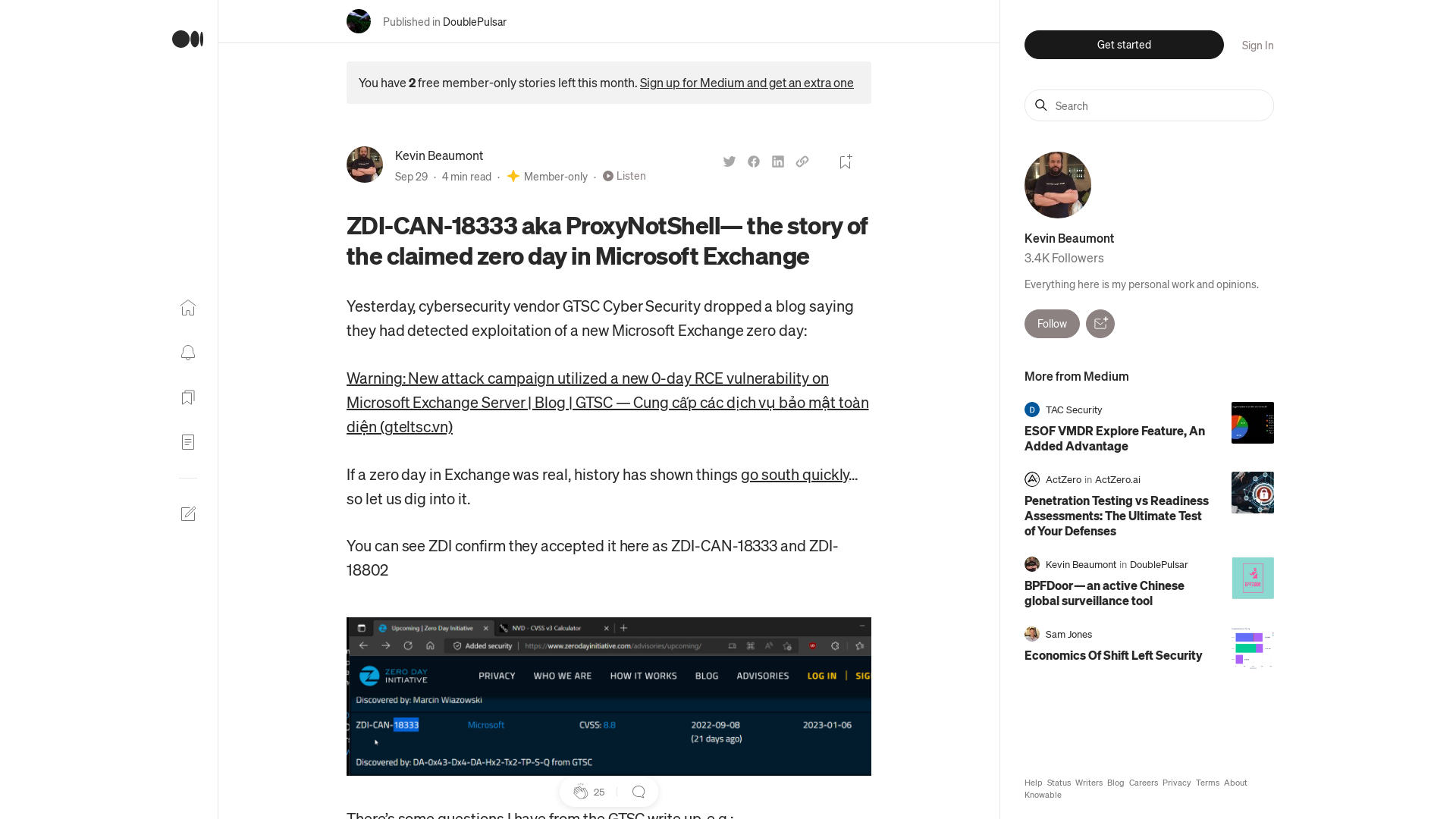
Cảnh báo chiến dịch tấn công sử dụng lỗ hổng ZERO DAY trên Microsoft Exchange Server | Blog | GTSC - Cung cấp các dịch vụ bảo mật toàn diện
https://www.gteltsc.vn/blog/canh-bao-chien-dich-tan-cong-su-dung-lo-hong-zero-day-tren-microsoft-exchange-server-12714.html
Warning: New attack campaign utilized a new 0-day RCE vulnerability on Microsoft Exchange Server | Blog | GTSC - Cung cấp các dịch vụ bảo mật toàn diện
https://gteltsc.vn/blog/warning-new-attack-campaign-utilized-a-new-0day-rce-vulnerability-on-microsoft-exchange-server-12715.html
WARNING: New Unpatched Microsoft Exchange Zero-Day Under Active Exploitation
https://thehackernews.com/2022/09/warning-new-unpatched-microsoft.html
Bad VIB(E)s Part One: Investigating Novel Malware Persistence Within ESXi Hypervisors | Mandiant
https://www.mandiant.com/resources/blog/esxi-hypervisors-malware-persistence
Dismantling a Prolific Cybercriminal Empire: REvil Arrests and Reemergence
https://www.trellix.com/en-us/about/newsroom/stories/research/dismantling-a-prolific-cybercriminal-empire.html
Kevin Beaumont on Twitter: "Exercise - I'm going to live tweet how long it takes me to patch an enterprise Exchange Server 2016 to latest security update (not including ProxyNotShell, as no update out yet). This one was last patched a few months ago." / Twitter
https://twitter.com/GossiTheDog/status/1575865934429900801
MalwareBazaar | SHA256 b9a1328f3107582e58d4fef064f2d3998b658ccc513f9e98a513f5606400d9be (Quakbot)
https://bazaar.abuse.ch/sample/b9a1328f3107582e58d4fef064f2d3998b658ccc513f9e98a513f5606400d9be/
MalwareBazaar | SHA256 af1692ced38f5fda305b35be66774822900a0b9617102db4b3da5f7c97f70e3e (Quakbot)
https://bazaar.abuse.ch/sample/af1692ced38f5fda305b35be66774822900a0b9617102db4b3da5f7c97f70e3e/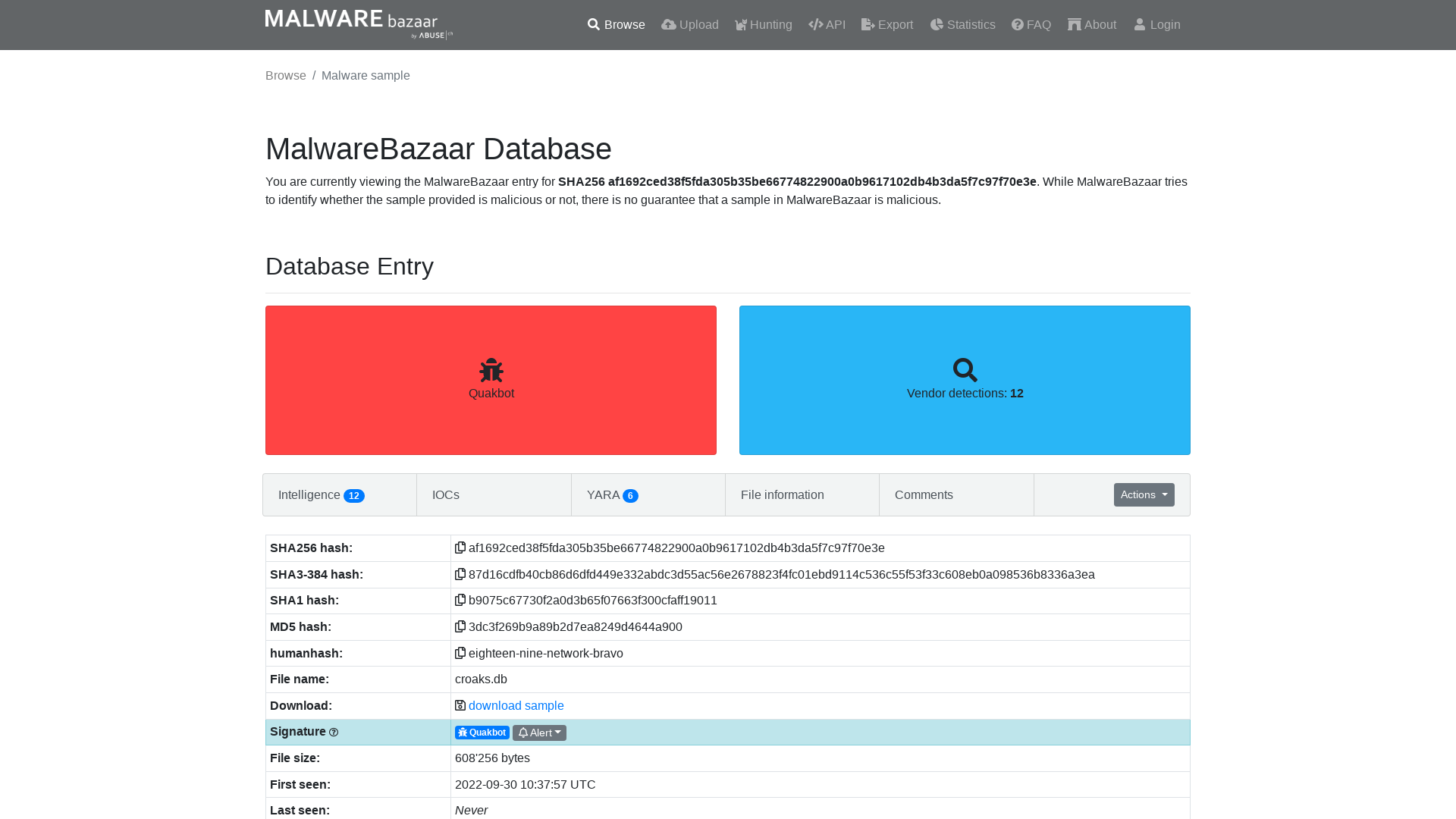
Suspected Post-Authentication Zero-Day Vulnerabilities in Microsoft Exchange Server | Rapid7 Blog
https://www.rapid7.com/blog/post/2022/09/29/suspected-post-authentication-zero-day-vulnerabilities-in-microsoft-exchange-server/
Qakbot/Qakbot_BB_30.09.2022.txt at main · pr0xylife/Qakbot · GitHub
https://github.com/pr0xylife/Qakbot/blob/main/Qakbot_BB_30.09.2022.txt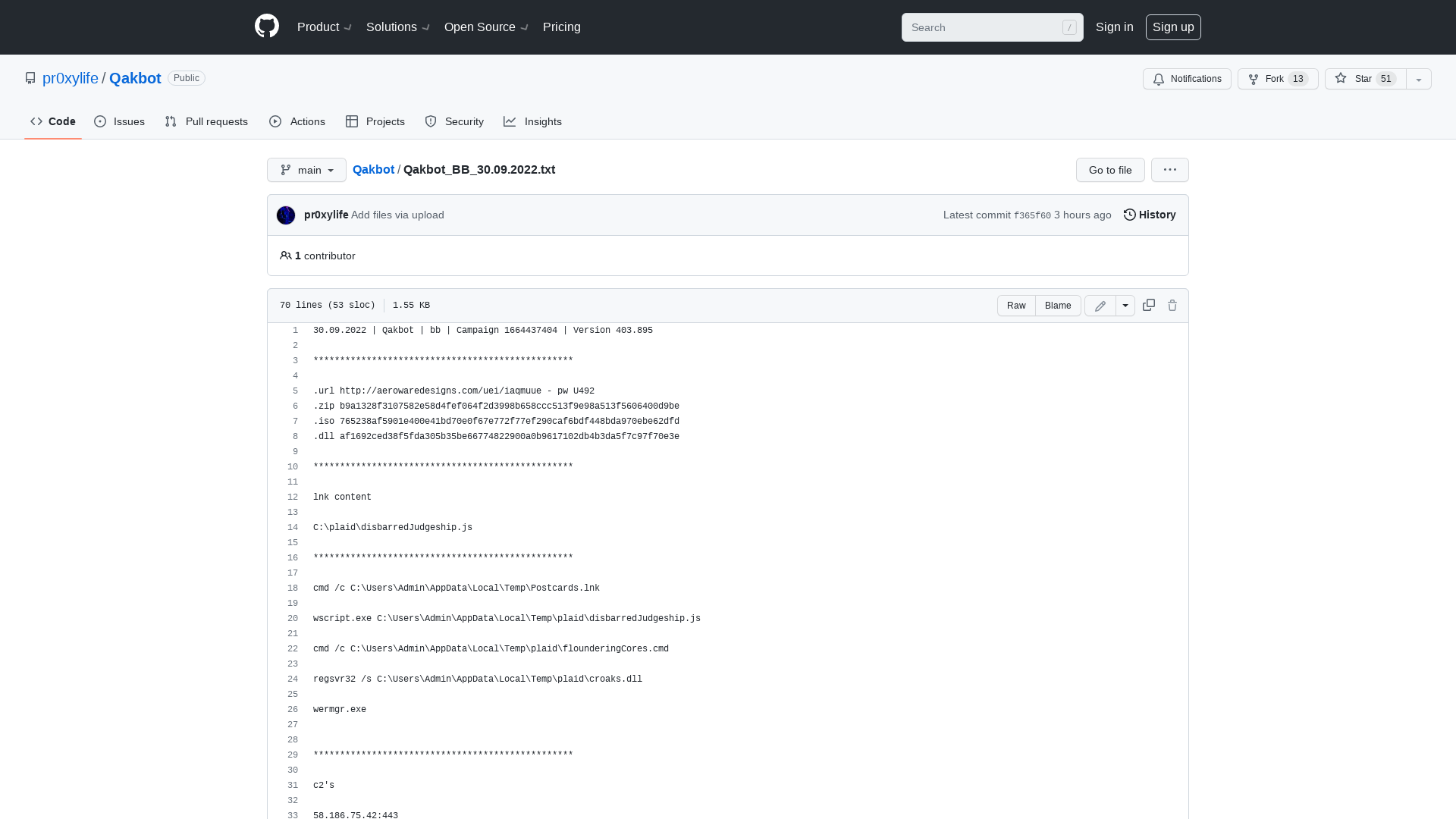
Worldwide Server-side Cache Poisoning on All Akamai Edge Nodes ($50K+ Bounty Earned) | by Jacopo Tediosi | Sep, 2022 | Medium
https://medium.com/@jacopotediosi/worldwide-server-side-cache-poisoning-on-all-akamai-edge-nodes-50k-bounty-earned-f97d80f3922b
Microsoft Confirms 2 New Exchange Zero-Day Flaws Being Used in the Wild
https://thehackernews.com/2022/09/microsoft-confirms-2-new-exchange-zero.html
Kevin Beaumont on Twitter: "Exercise - I'm going to live tweet how long it takes me to patch an enterprise Exchange Server 2016 to latest security update (not including ProxyNotShell, as no update out yet). This one was last patched a few months ago." / Twitter
https://twitter.com/gossithedog/status/1575865934429900801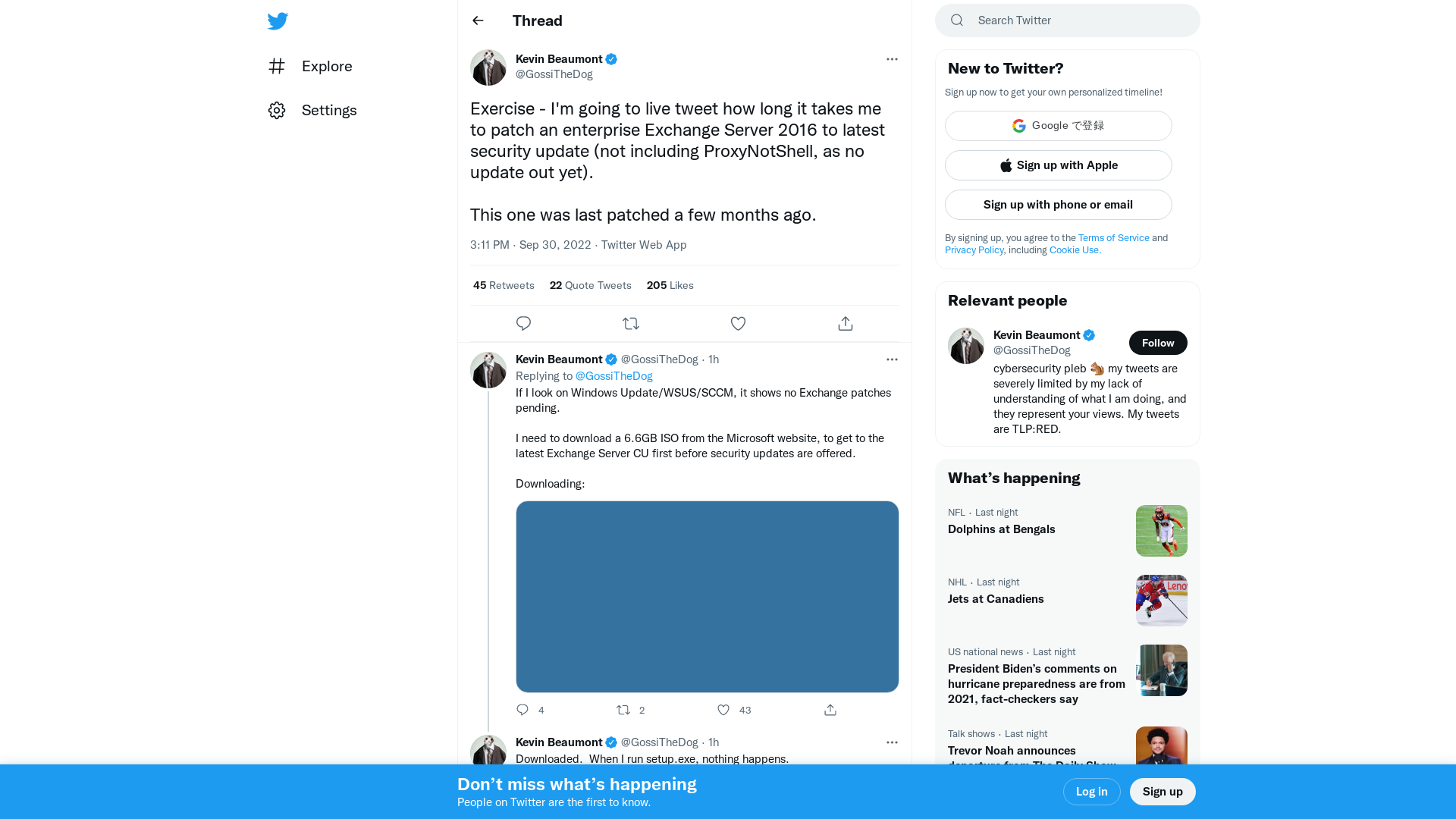
A glimpse into the shadowy realm of a Chinese APT: detailed analysis of a ShadowPad intrusion – NCC Group Research
https://research.nccgroup.com/2022/09/30/a-glimpse-into-the-shadowy-realm-of-a-chinese-apt-detailed-analysis-of-a-shadowpad-intrusion/
GitHub - Mr-Un1k0d3r/ATP-PowerShell-Scripts: Microsoft Signed PowerShell scripts
https://github.com/Mr-Un1k0d3r/ATP-PowerShell-Scripts
GreyNoise | Microsoft Exchange ProxyNotShell 0-Day Vulnerability
https://www.greynoise.io/blog/microsoft-exchange-proxynotshell-vulnerability
Protecting vSphere From Specialized Malware | VMware
https://core.vmware.com/vsphere-esxi-mandiant-malware-persistence
GitHub - jsa2/caOptics: CA Optics - Azure AD Conditional Access gap analyzer
https://github.com/jsa2/caOptics#ca-optics---azure-ad-conditional-access-gap-analyzer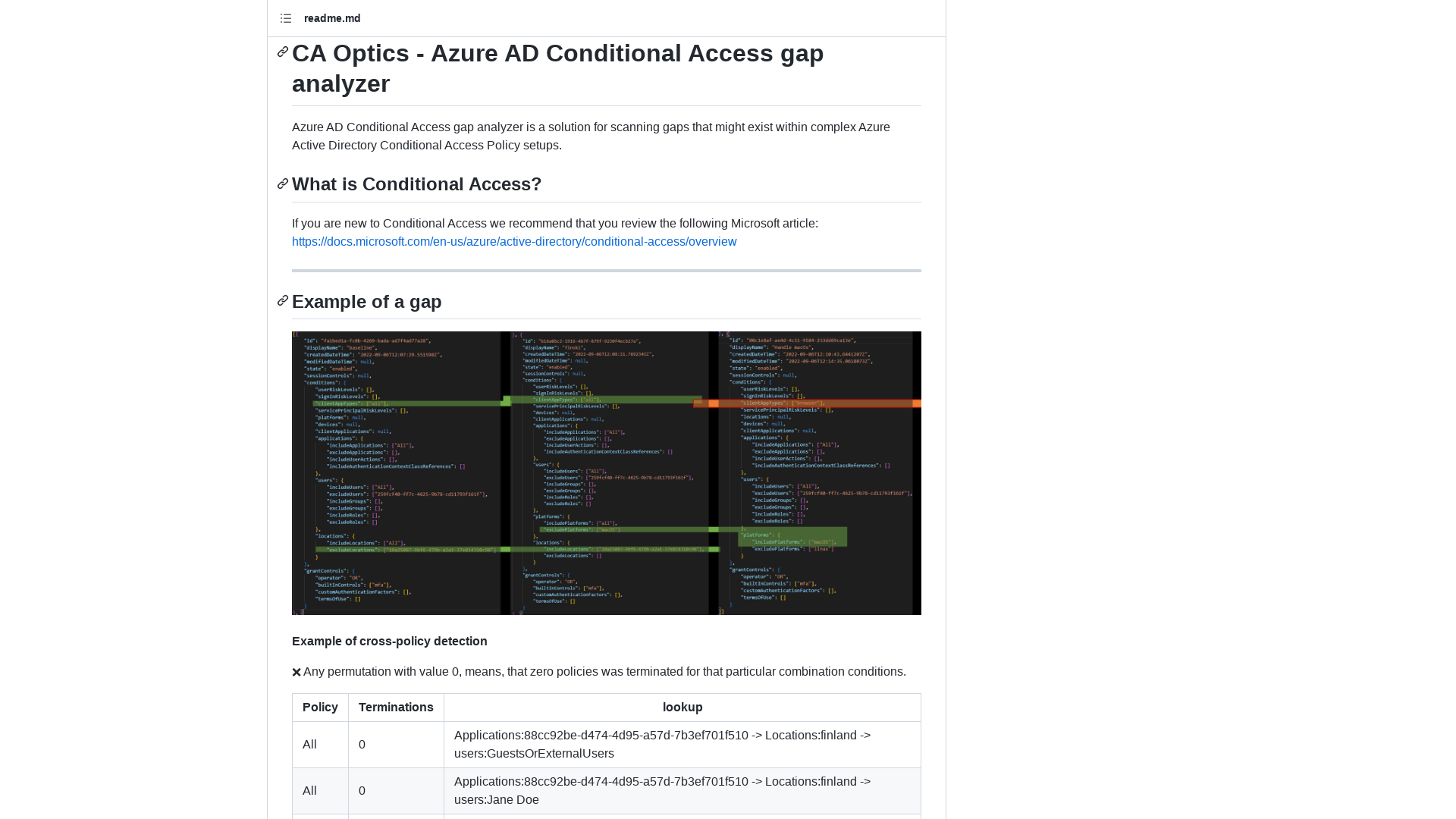
Kevin Beaumont on Twitter: "Starting a new thread for two Exchange zero days being exploited in the wild. Calling it ProxyNotShell for details explained within, aka CVE-2022-41040 and CVE-2022-41082. #ProxyNotShell https://t.co/Mzjm1qXtEA" / Twitter
https://twitter.com/GossiTheDog/status/1575762721353916417
Hybrid + Identity Cyber Range
https://www.purplecloud.network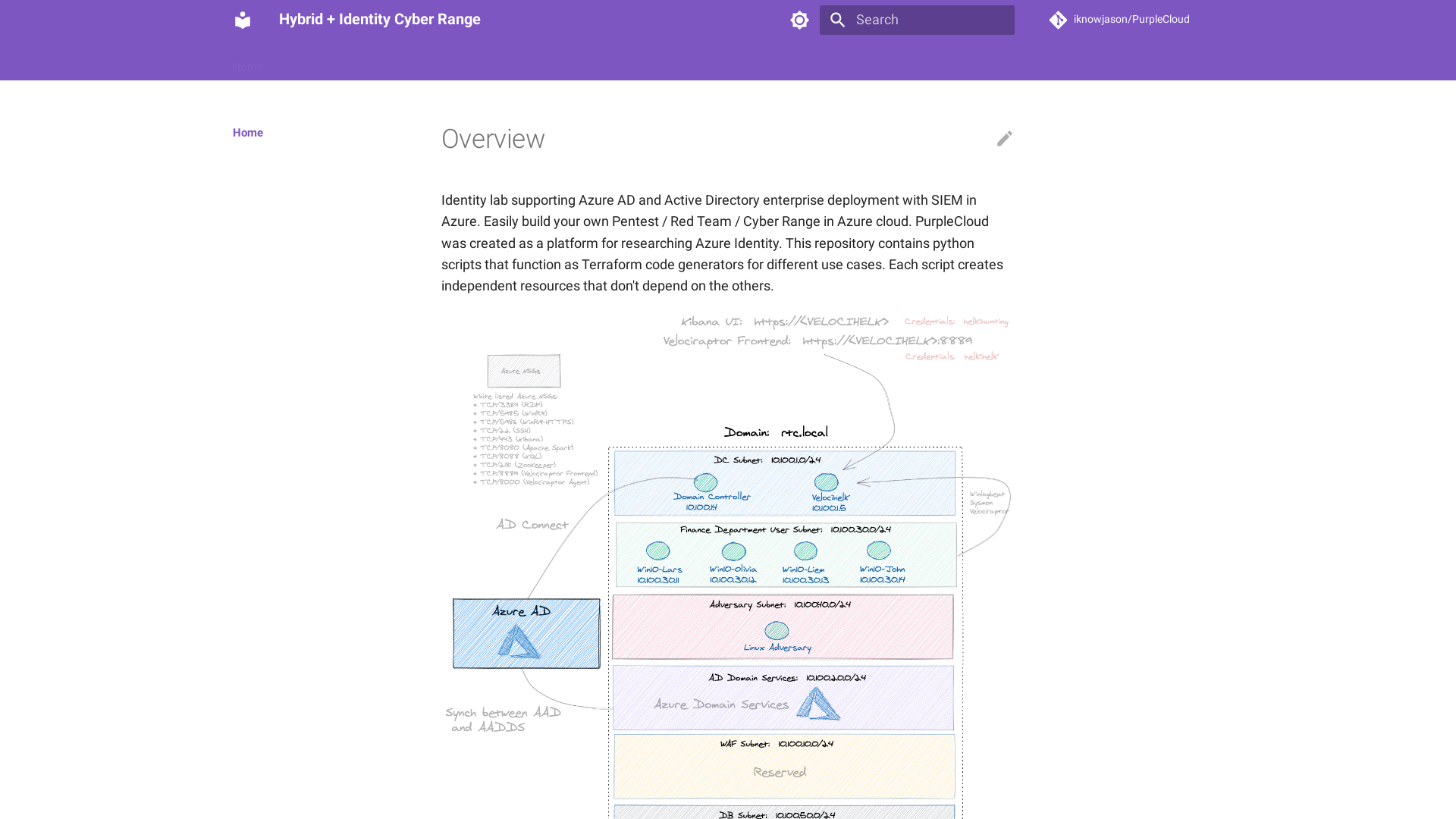
Germany arrests hacker for stealing €4 million via phishing attacks
https://www.bleepingcomputer.com/news/security/germany-arrests-hacker-for-stealing-4-million-via-phishing-attacks/
GreyNoise Trends
https://viz.greynoise.io/tag/exchange-proxynotshell-vuln-check?days=3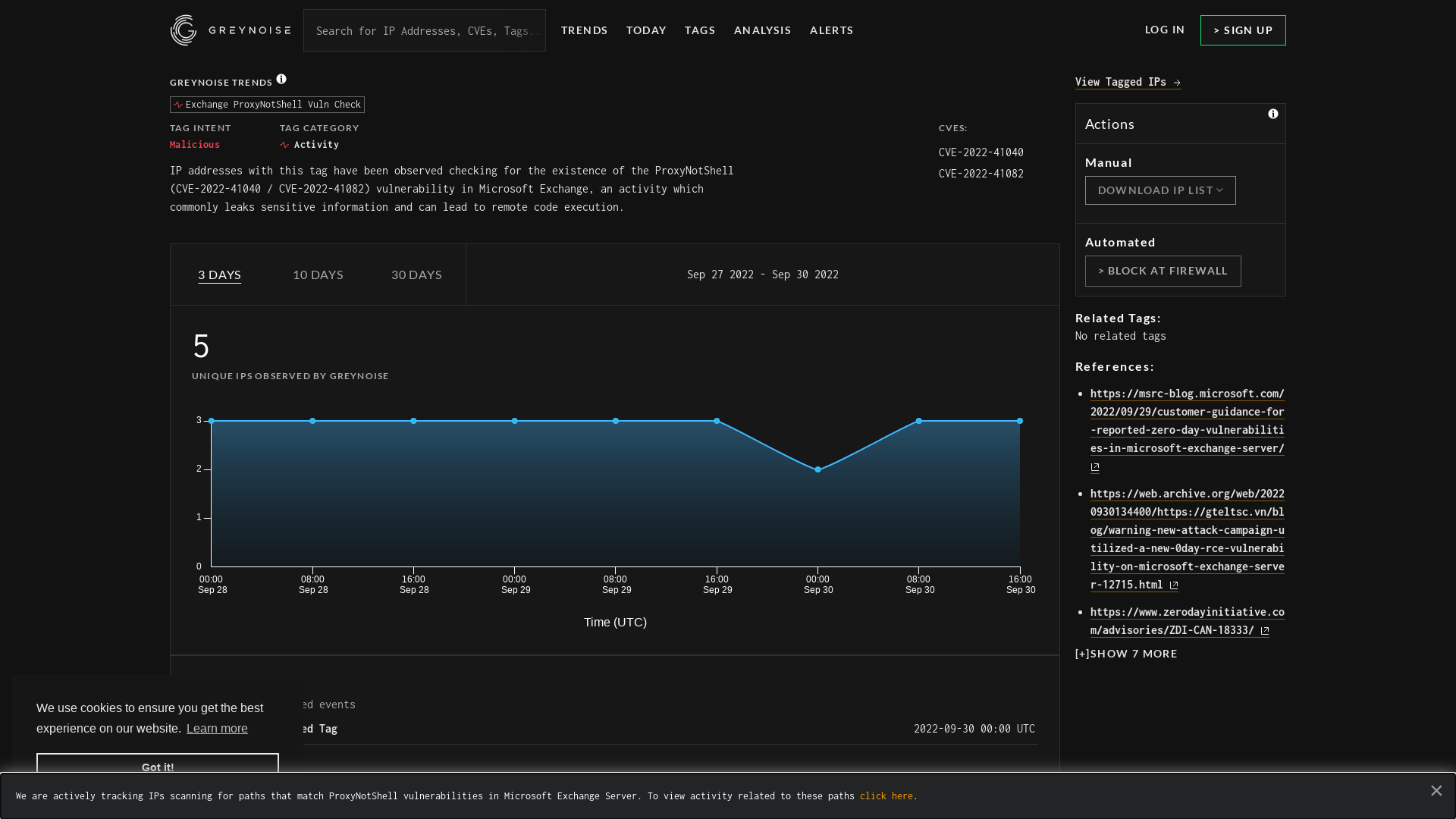
Microsoft: Two New 0-Day Flaws in Exchange Server – Krebs on Security
https://krebsonsecurity.com/2022/09/microsoft-two-new-0-day-flaws-in-exchange-server/
Exploitation of Microsoft Exchange Servers seen in the wild – PwnDefend
https://www.pwndefend.com/2022/09/30/exploitation-of-microsoft-exchange-servers-seen-in-the-wild/
Microsoft confirms new Exchange zero-days are used in attacks
https://www.bleepingcomputer.com/news/microsoft/microsoft-confirms-new-exchange-zero-days-are-used-in-attacks/