Breaking Bitbucket: Pre Auth Remote Command Execution (CVE-2022-36804) – Assetnote
https://blog.assetnote.io/2022/09/14/rce-in-bitbucket-server/
Exploiting Web3’s Hidden Attack Surface: Universal XSS on Netlify’s Next.js Library | Sam Curry
https://samcurry.net/universal-xss-on-netlifys-next-js-library
Out Of Band Update: Cobalt Strike 4.7.1 | Cobalt Strike
https://www.cobaltstrike.com/blog/out-of-band-update-cobalt-strike-4-7-1/
Analysis Report on Lazarus Group's Rootkit Attack Using BYOVD - ASEC BLOG
https://asec.ahnlab.com/en/38993/
Analysis-Report-on-Lazarus-Groups-Rootkit-Attack-Using-BYOVD_Sep-22-2022.pdf
https://asec.ahnlab.com/wp-content/uploads/2022/09/Analysis-Report-on-Lazarus-Groups-Rootkit-Attack-Using-BYOVD_Sep-22-2022.pdf
Making HTTP header injection critical via response queue poisoning | PortSwigger Research
https://portswigger.net/research/making-http-header-injection-critical-via-response-queue-poisoning
Inside Russia’s Vast Surveillance State: ‘They Are Watching’ - The New York Times
https://www.nytimes.com/interactive/2022/09/22/technology/russia-putin-surveillance-spying.html
Diagrams, charts, and other sample slides - Google スライド
https://bit.ly/3BE4zbj
URLhaus | http://194.38.23.170/new1.plg
https://urlhaus.abuse.ch/url/2308917/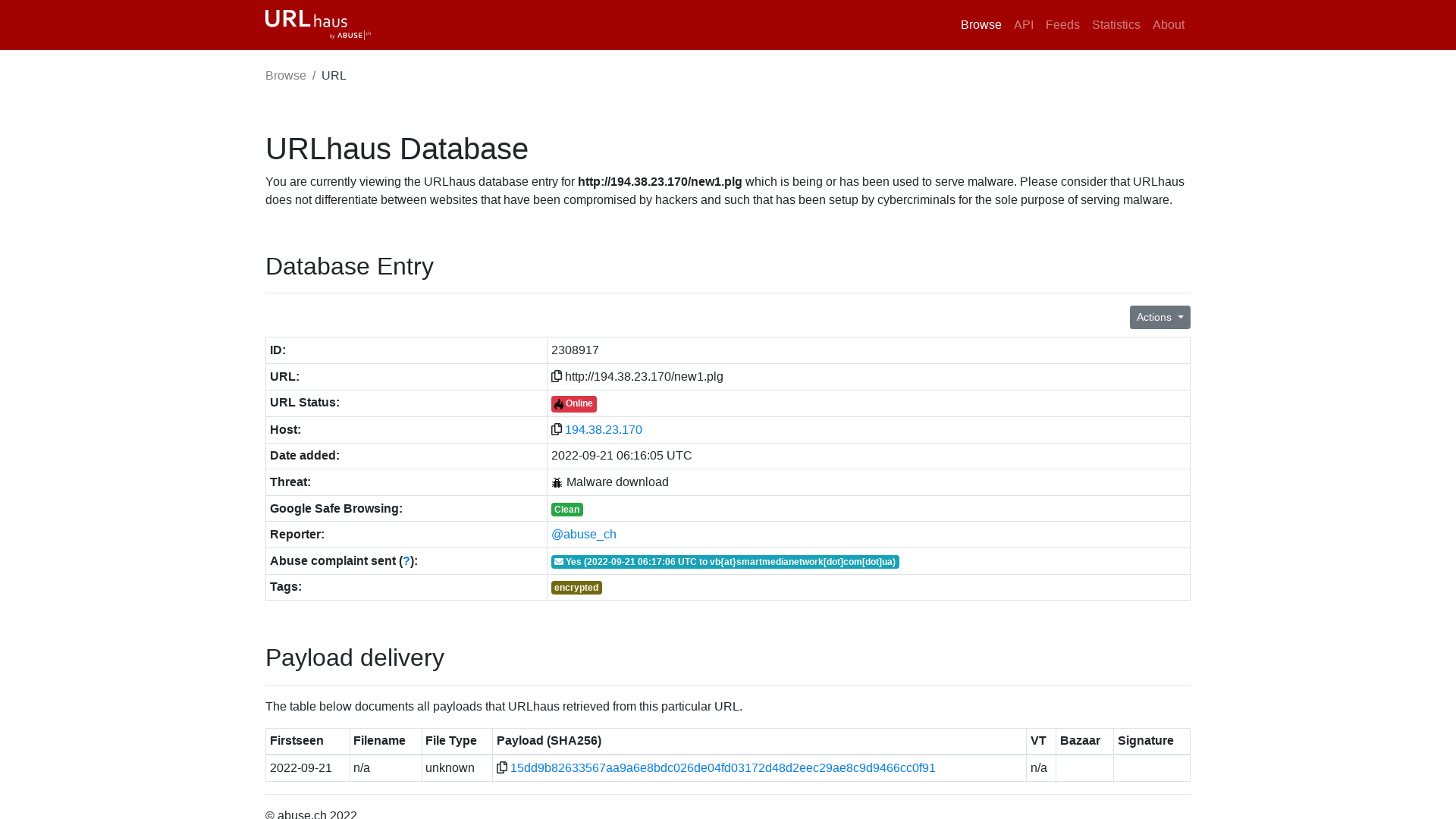
Malicious OAuth applications used to compromise email servers and spread spam - Microsoft Security Blog
https://www.microsoft.com/security/blog/2022/09/22/malicious-oauth-applications-used-to-compromise-email-servers-and-spread-spam/
Qakbot/Qakbot_BB_22.09.2022.txt at main · pr0xylife/Qakbot · GitHub
https://github.com/pr0xylife/Qakbot/blob/main/Qakbot_BB_22.09.2022.txt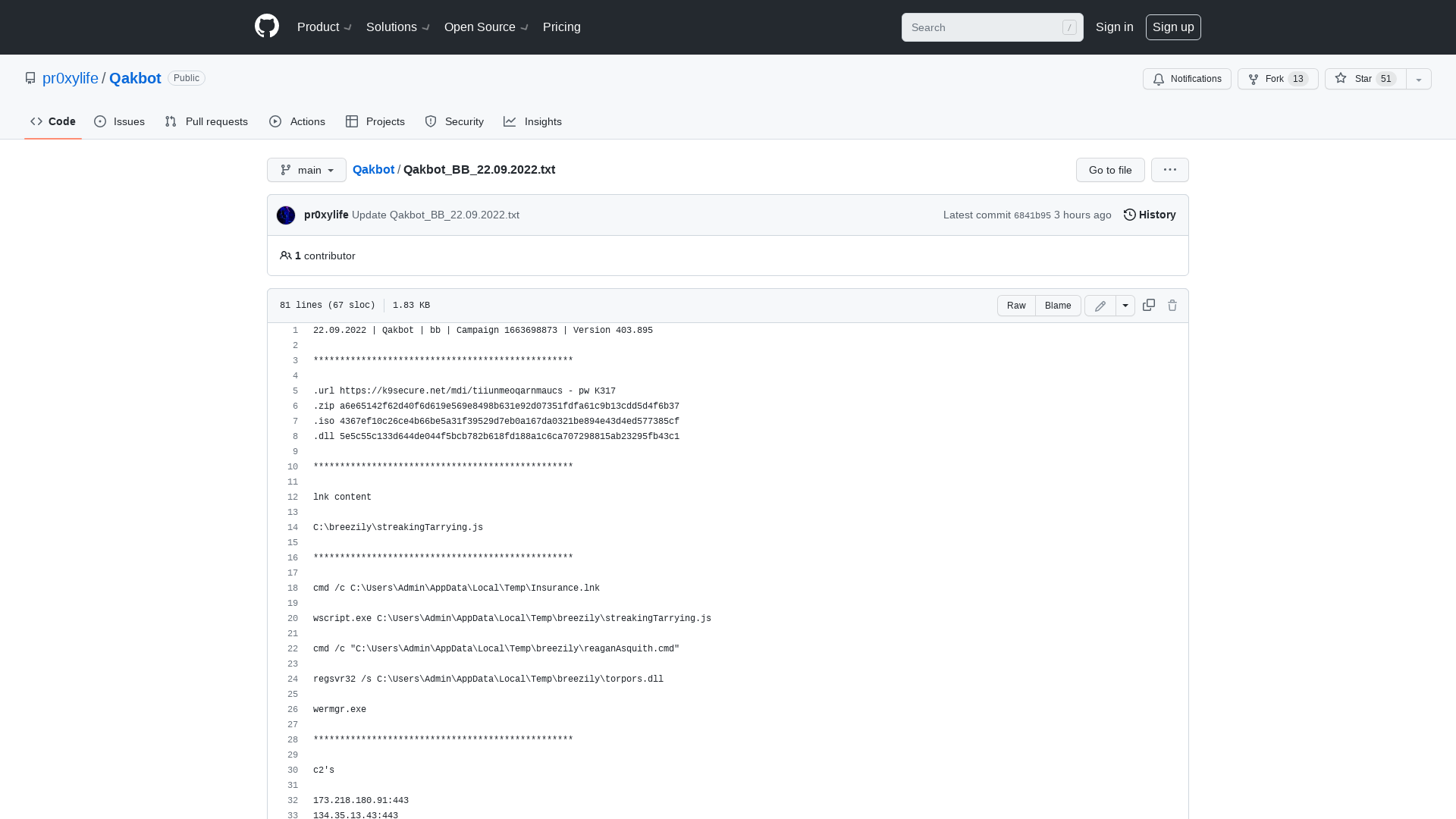
Raspberry Robin’s Roshtyak: A Little Lesson in Trickery - Avast Threat Labs
https://decoded.avast.io/janvojtesek/raspberry-robins-roshtyak-a-little-lesson-in-trickery/
Bypassing FileBlockExecutable in Sysmon 14.0: A Lesson In Analyzing Assumptions
https://www.huntandhackett.com/blog/bypassing-sysmon
LockBit ransomware builder leaked online by “angry developer”
https://www.bleepingcomputer.com/news/security/lockbit-ransomware-builder-leaked-online-by-angry-developer-/
MalwareBazaar | SHA256 3a00998d6a6c0d3db7d06cca0be5ae39b9c1884dda9f4dc4190bf0debc18da3d
https://bazaar.abuse.ch/sample/3a00998d6a6c0d3db7d06cca0be5ae39b9c1884dda9f4dc4190bf0debc18da3d/
Unpatched 15-year old Python bug allows code execution in 350k projects
https://www.bleepingcomputer.com/news/security/unpatched-15-year-old-python-bug-allows-code-execution-in-350k-projects/
The Mystery of Metador | An Unattributed Threat Hiding in Telcos, ISPs, and Universities - SentinelOne
https://www.sentinelone.com/labs/the-mystery-of-metador-an-unattributed-threat-hiding-in-telcos-isps-and-universities/
Exploiting Web3’s Hidden Attack Surface: Universal XSS on Netlify’s Next.js Library | Sam Curry
https://samcurry.net/universal-xss-on-netlifys-next-js-library/
Noberus Ransomware: Darkside and BlackMatter Successor Continues to Evolve its Tactics | Broadcom Software Blogs
https://symantec-enterprise-blogs.security.com/blogs/threat-intelligence/noberus-blackcat-ransomware-ttps
Researchers Disclose Critical Vulnerability in Oracle Cloud Infrastructure
https://thehackernews.com/2022/09/researchers-disclose-critical.html
Rewards plus: Fake mobile banking rewards apps lure users to install info-stealing RAT on Android devices - Microsoft Security Blog
https://www.microsoft.com/security/blog/2022/09/21/rewards-plus-fake-mobile-banking-rewards-apps-lure-users-to-install-info-stealing-rat-on-android-devices/
How we Abused Repository Webhooks to Access Internal CI Systems at Scale - Cider Security Site
https://www.cidersecurity.io/blog/research/how-we-abused-repository-webhooks-to-access-internal-ci-systems-at-scale/
Giving JuicyPotato a second chance: JuicyPotatoNG – Decoder's Blog
https://decoder.cloud/2022/09/21/giving-juicypotato-a-second-chance-juicypotatong
A technical analysis of the leaked LockBit 3.0 builder – CYBER GEEKS
https://cybergeeks.tech/a-technical-analysis-of-the-leaked-lockbit-3-0-builder/
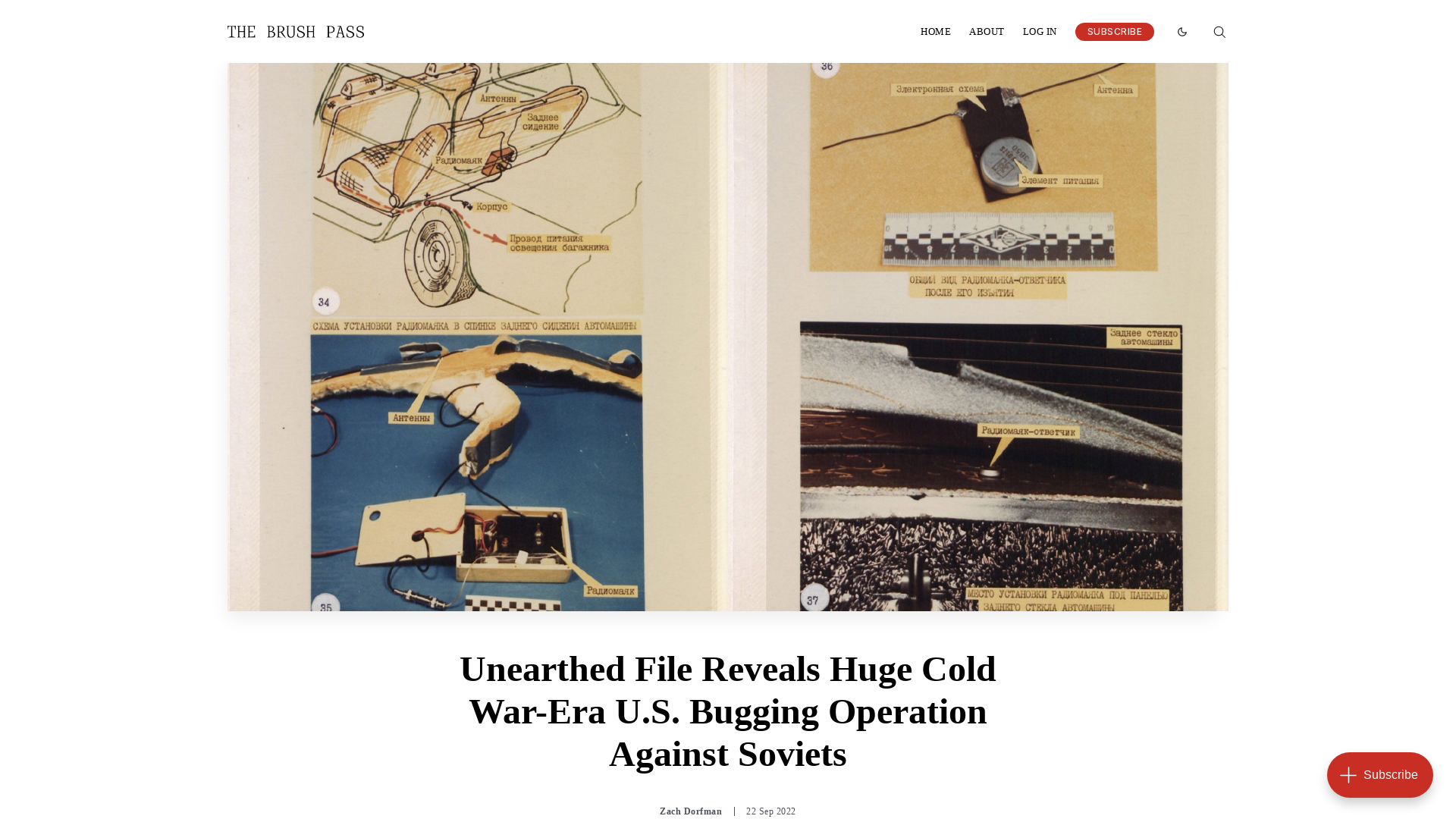
Unearthed File Reveals Huge Cold War-Era U.S. Bugging Operation Against Soviets
https://thebrushpass.projectbrazen.com/coldwarbuggingsovietunion/