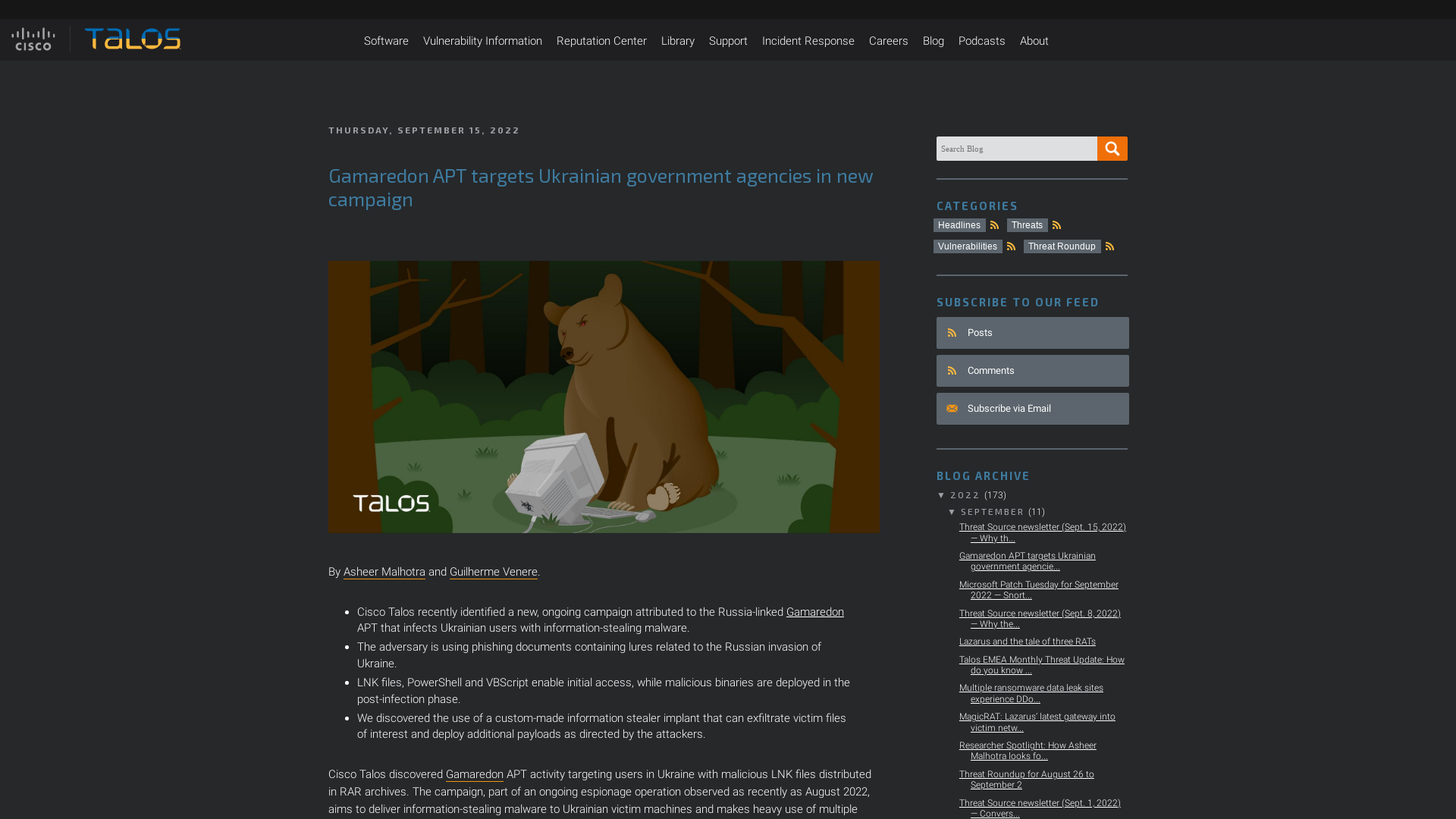
Uber Comms on Twitter: "We are currently responding to a cybersecurity incident. We are in touch with law enforcement and will post additional updates here as they become available." / Twitter
https://twitter.com/Uber_Comms/status/1570584747071639552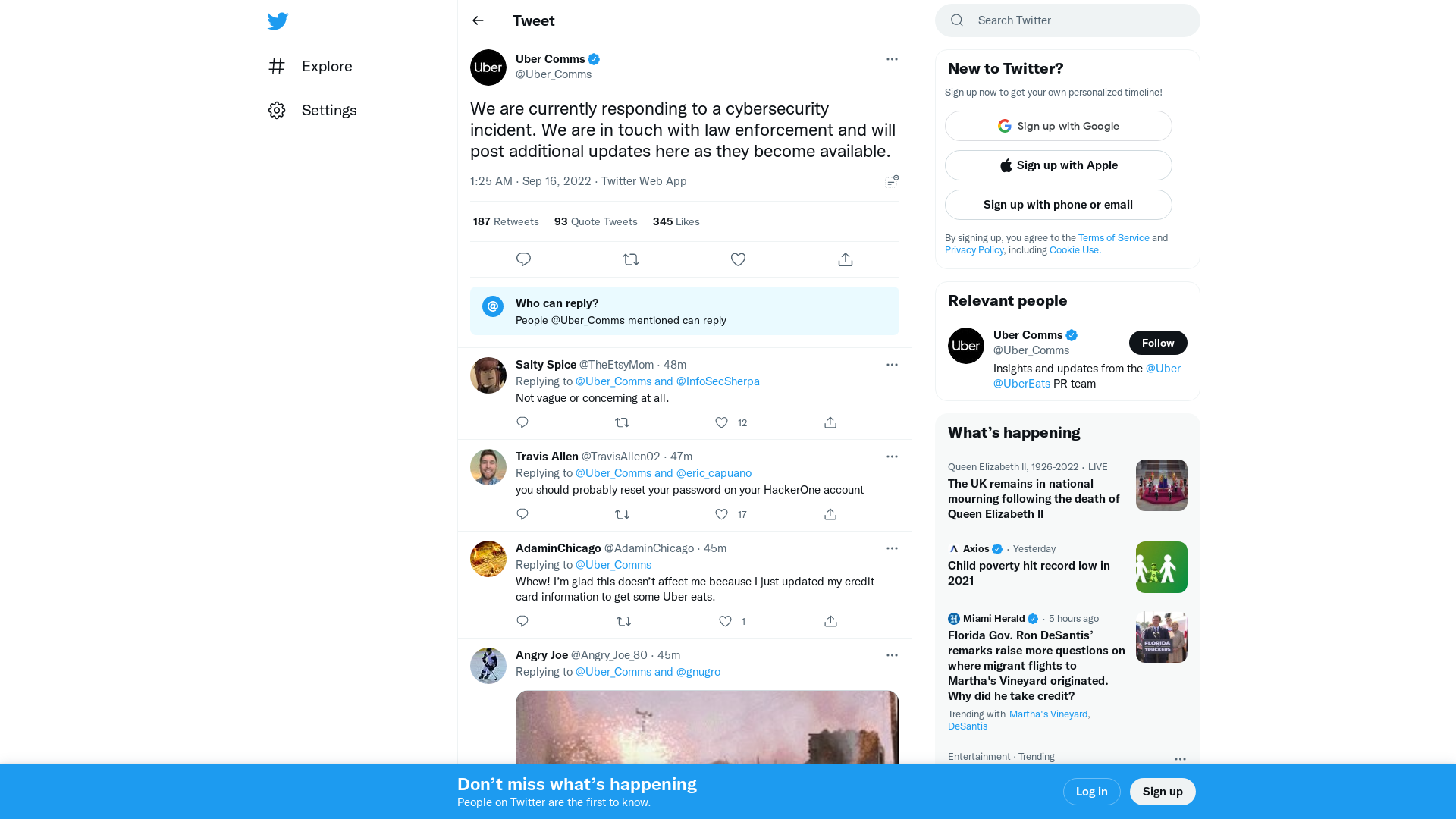
Corben Leo on Twitter: "Apparently there was an internal network share that contained powershell scripts... "One of the powershell scripts contained the username and password for a admin user in Thycotic (PAM) Using this i was able to extract secrets for all services, DA, DUO, Onelogin, AWS, GSuite" https://t.co/FhszpxxUEW" / Twitter
https://twitter.com/hacker_/status/1570582547415068672
Uber Investigating Breach of Its Computer Systems - The New York Times
https://www.nytimes.com/2022/09/15/technology/uber-hacking-breach.html
Uber hacked, internal systems breached and vulnerability reports stolen
https://www.bleepingcomputer.com/news/security/uber-hacked-internal-systems-breached-and-vulnerability-reports-stolen/
Kevin Beaumont on Twitter: "Uber, what you need to know, the thread. 1) https://t.co/CXU75bqrZU" / Twitter
https://twitter.com/GossiTheDog/status/1570717994397073410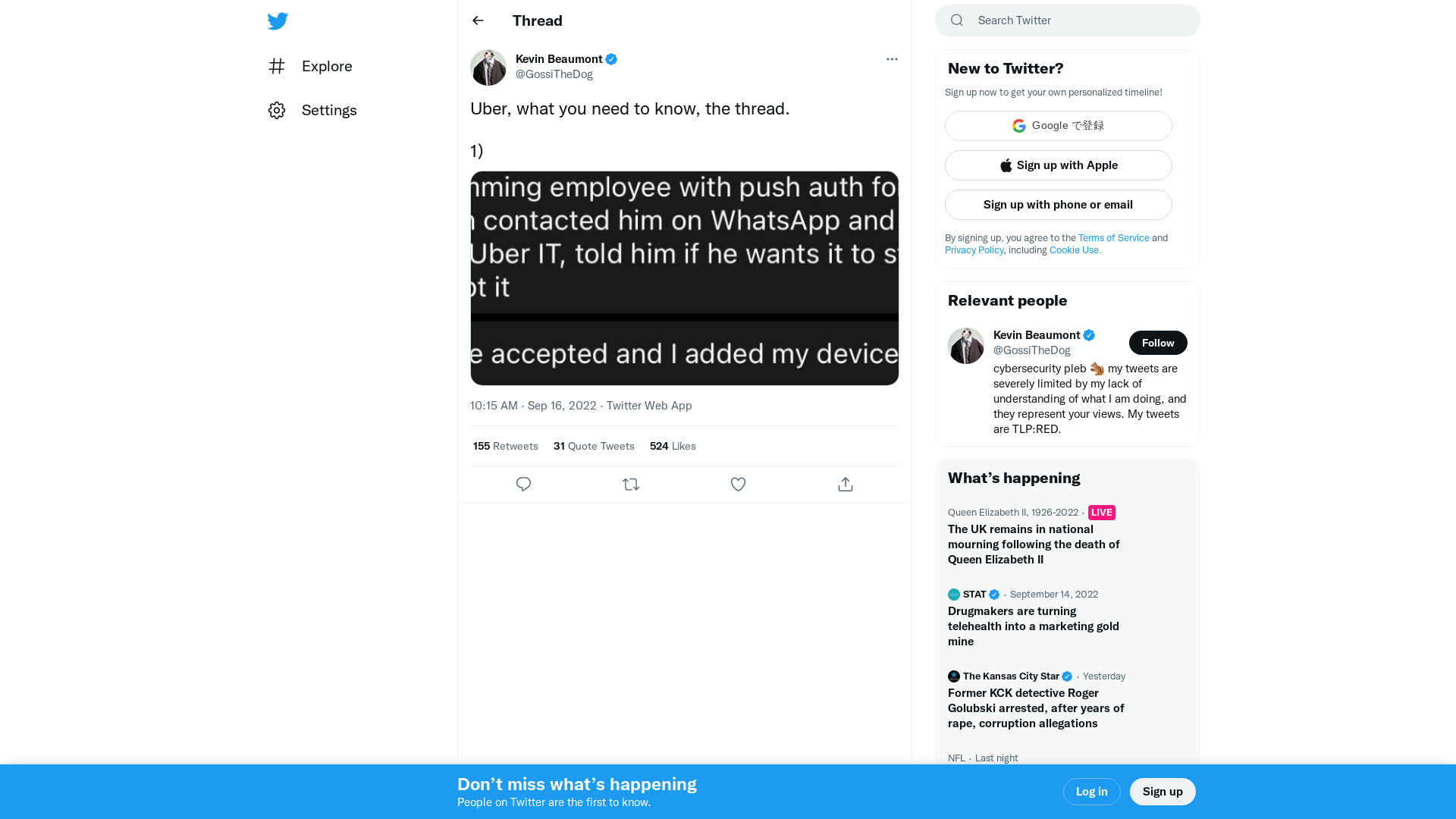
vx-underground on Twitter: "Update: A Threat Actor claims to have completely compromised Uber - they have posted screenshots of their AWS instance, HackerOne administration panel, and more. They are openly taunting and mocking @Uber. https://t.co/Q3PzzBLsQY" / Twitter
https://twitter.com/vxunderground/status/1570597582417821703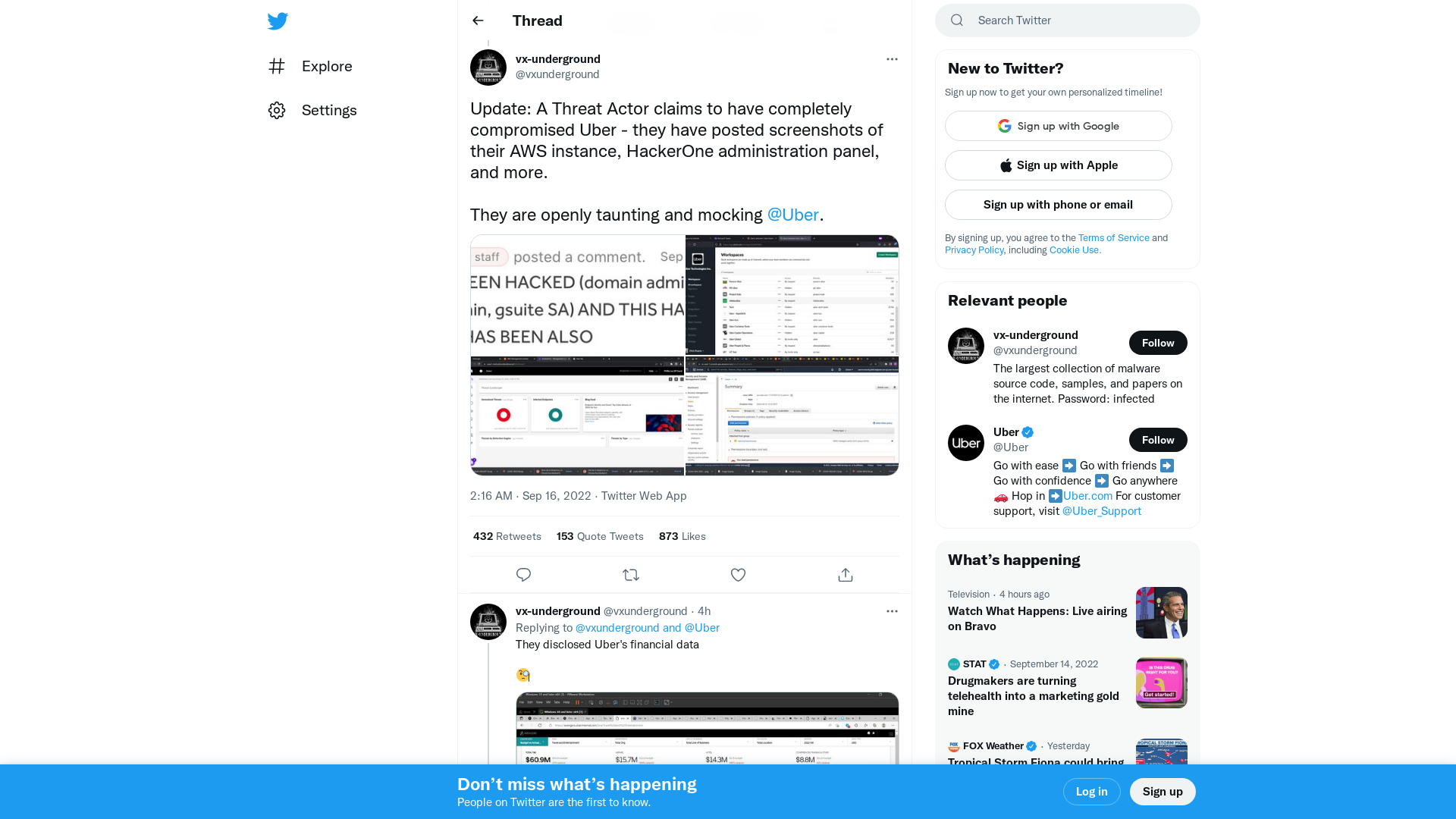
Sam Curry on Twitter: "Someone hacked an Uber employees HackerOne account and is commenting on all of the tickets. They likely have access to all of the Uber HackerOne reports. https://t.co/00j8V3kcoE" / Twitter
https://twitter.com/samwcyo/status/1570577801790783493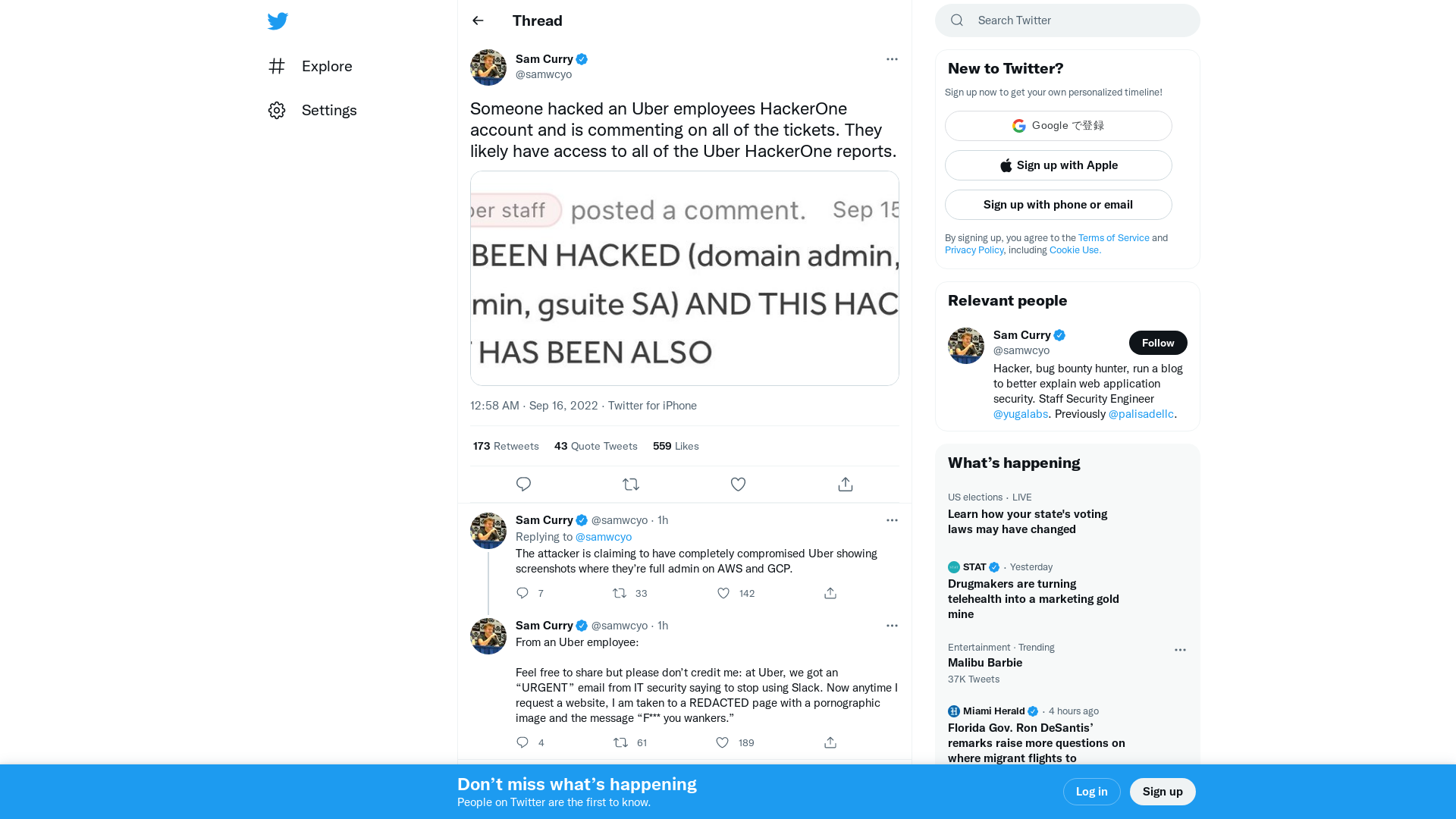
Uber Says It's Investigating a Potential Breach of Its Computer Systems
https://thehackernews.com/2022/09/uber-says-its-investigating-potential.html
_MG_ on Twitter: "Lots of screenshots going around about Uber but this one shows how wide the hack is. "Security Response Break Glass Service Account" password 🔥 https://t.co/pvz12cJrBY" / Twitter
https://twitter.com/_MG_/status/1570626240499032065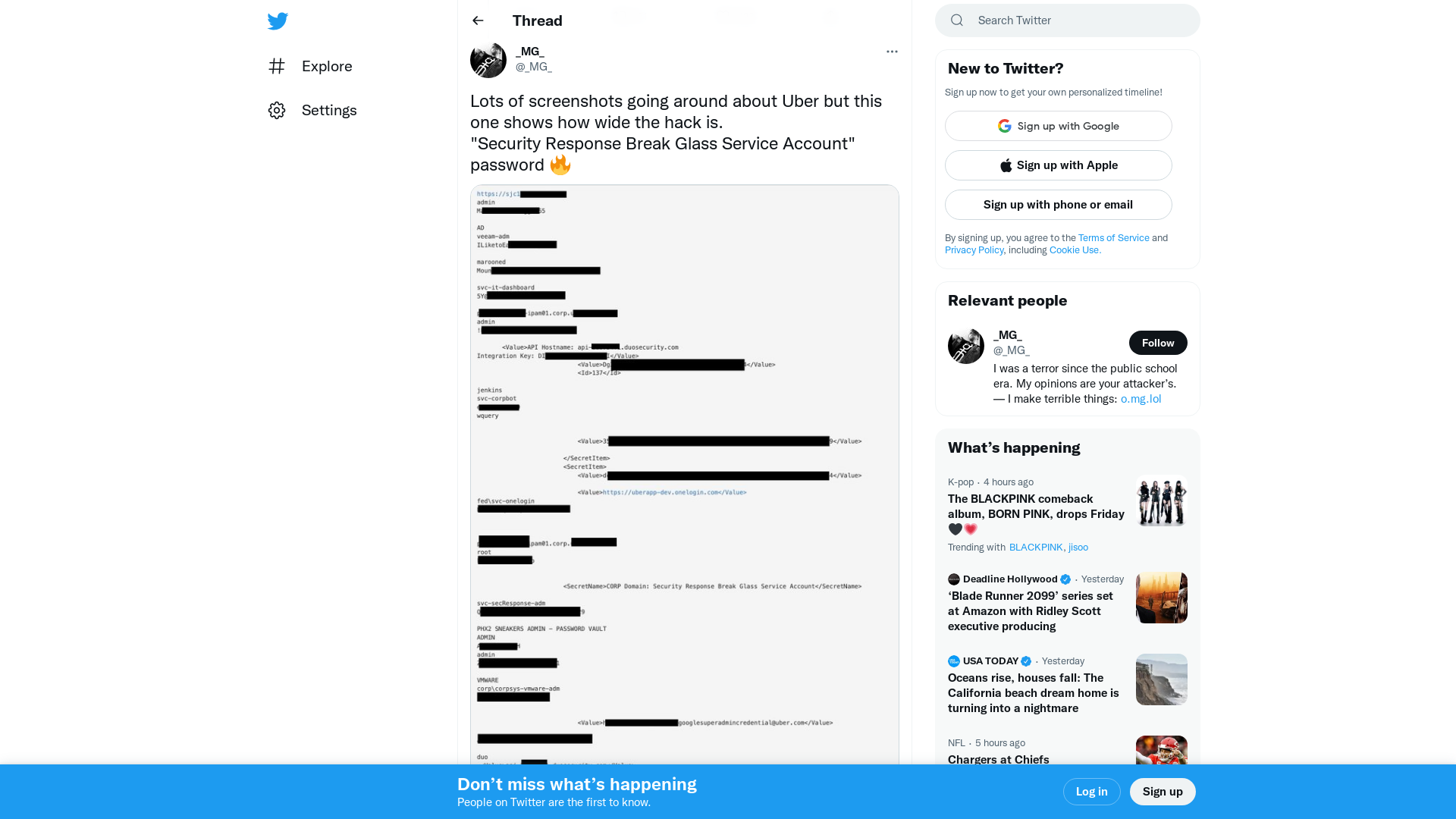
Hackers trojanize PuTTY SSH client to backdoor media company
https://www.bleepingcomputer.com/news/security/hackers-trojanize-putty-ssh-client-to-backdoor-media-company/
vx-underground on Twitter: "Free Uber DFIR report courtesy of @hacker_ https://t.co/RTsub1OjAE" / Twitter
https://twitter.com/vxunderground/status/1570605064003420160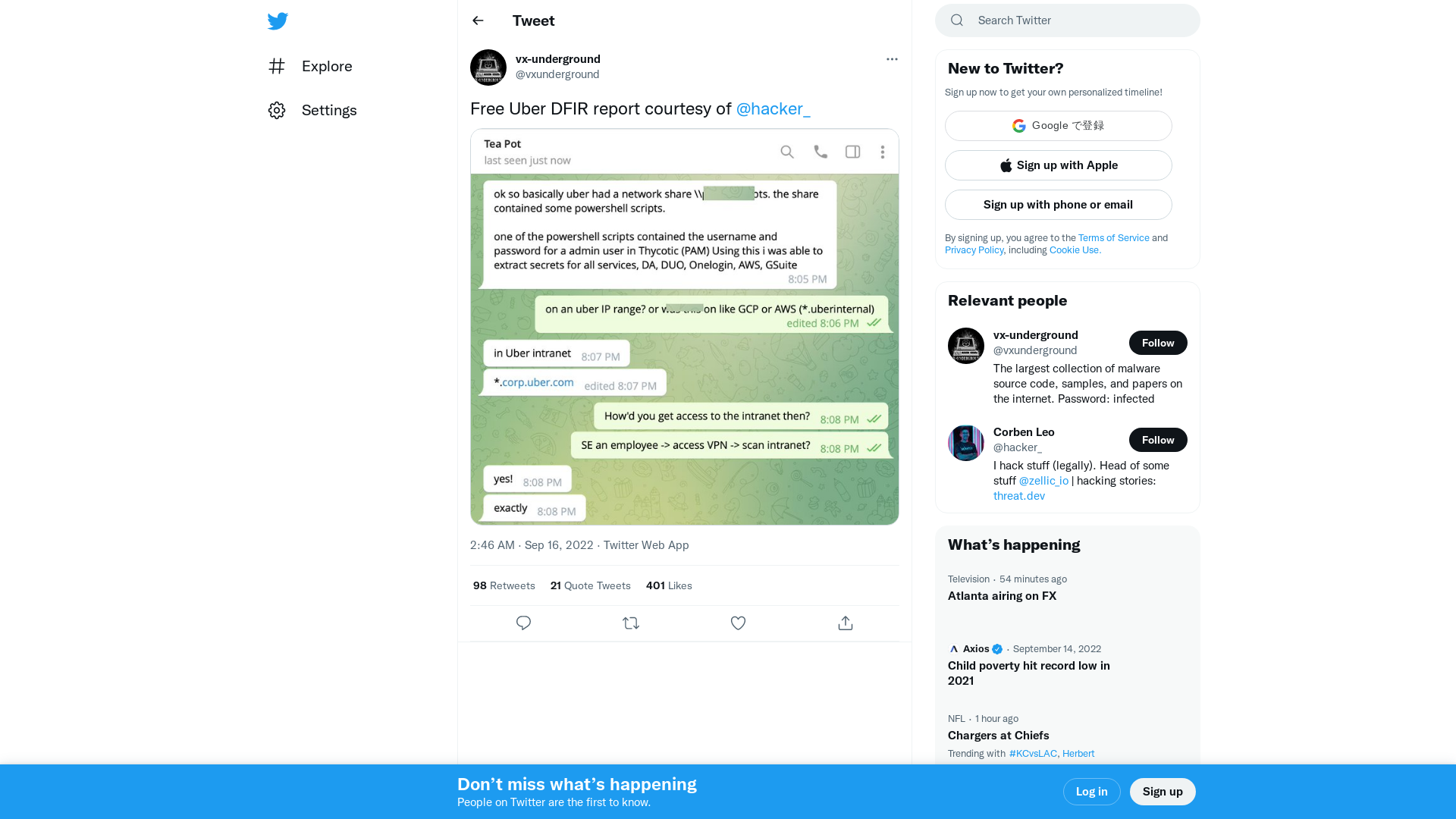
John Scott-Railton on Twitter: "Stop and watch this video. Whatever you thought about the governors' stunt... it turns out it was worse. https://t.co/GASpsChOzl" / Twitter
https://twitter.com/jsrailton/status/1570803548501446661
kate conger on Twitter: "Update from Uber: the company says there is no evidence that "sensitive user data" was accessed https://t.co/b1VNOy2QvQ" / Twitter
https://twitter.com/kateconger/status/1570829575013412864
The seventh way to call a JavaScript function without parentheses | PortSwigger Research
https://portswigger.net/research/the-seventh-way-to-call-a-javascript-function-without-parentheses
Qakbot/Qakbot_BB_16.09.2022.txt at main · pr0xylife/Qakbot · GitHub
https://github.com/pr0xylife/Qakbot/blob/main/Qakbot_BB_16.09.2022.txt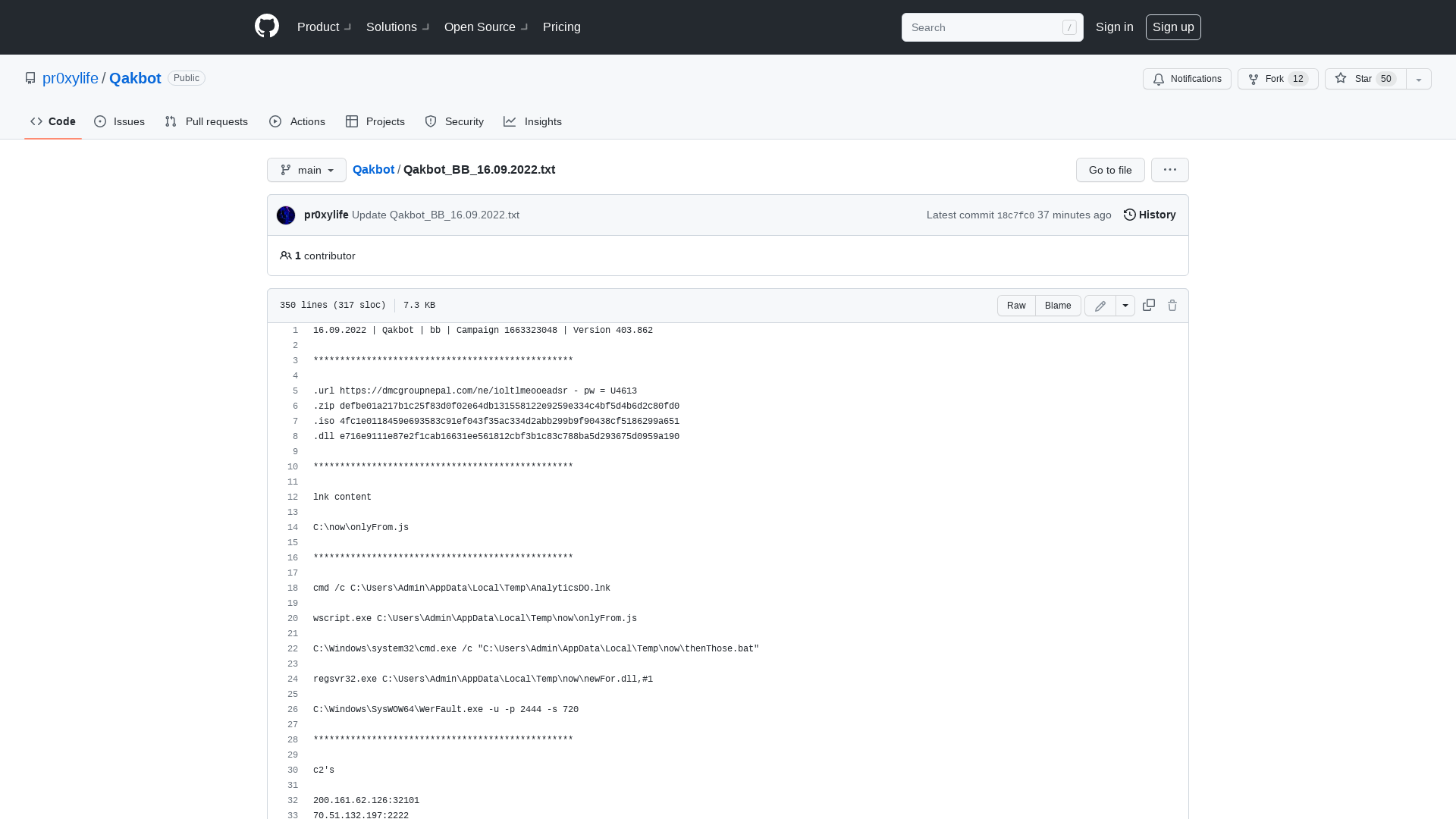
Shodan Account
https://trends.shodan.io/search?query=%22watermark%3A+666666%22#facet/overview
Using Hackability to uncover a Chrome infoleak | PortSwigger Research
https://portswigger.net/research/using-hackability-to-uncover-a-chrome-infoleak
vx-underground on Twitter: "@Uber UPDATE: More Uber information data disclosed: vSphere, Google workplace data, and more AWS data. https://t.co/aTSBBuyust" / Twitter
https://twitter.com/vxunderground/status/1570611979169202179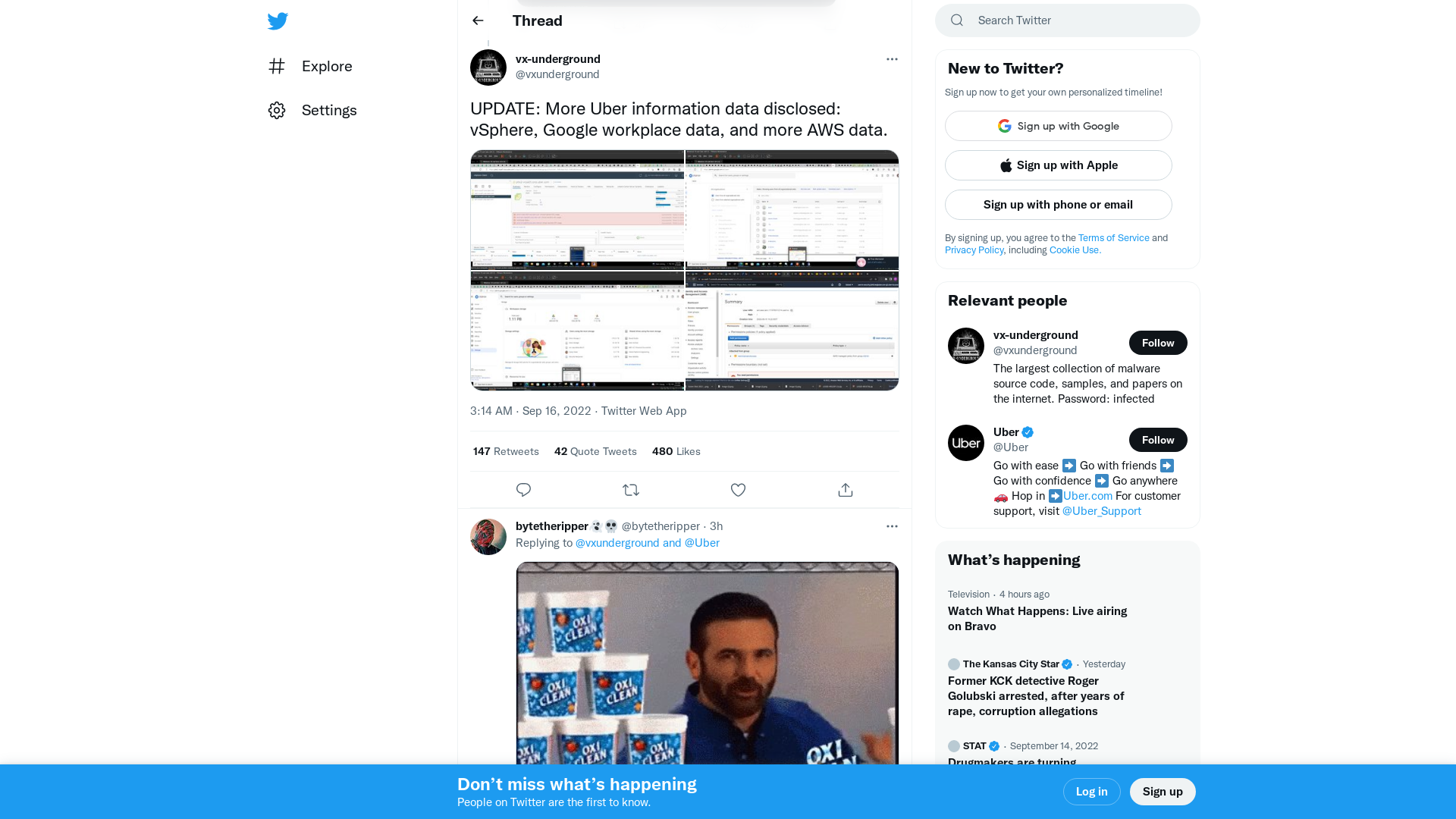
Uber Comms on Twitter: "https://t.co/BwzpviHxmR" / Twitter
https://twitter.com/Uber_Comms/status/1570829232246509569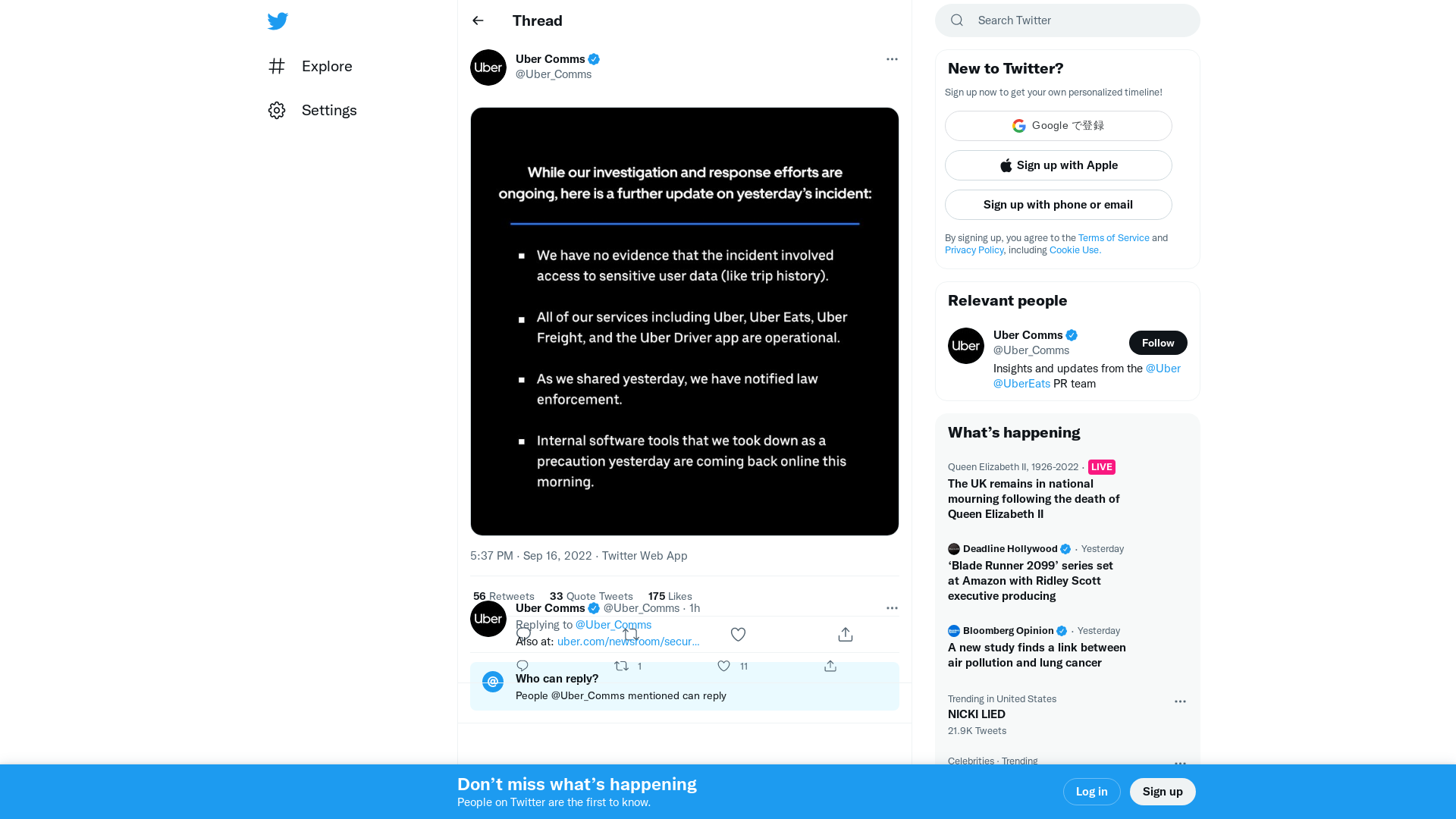
Hackers Targeting WebLogic Servers and Docker APIs for Mining Cryptocurrencies
https://thehackernews.com/2022/09/hackers-targeting-weblogic-servers-and.html
Uber cloud systems seemingly hijacked in 'security incident’ • The Register
https://www.theregister.com/2022/09/16/uber_security_incident/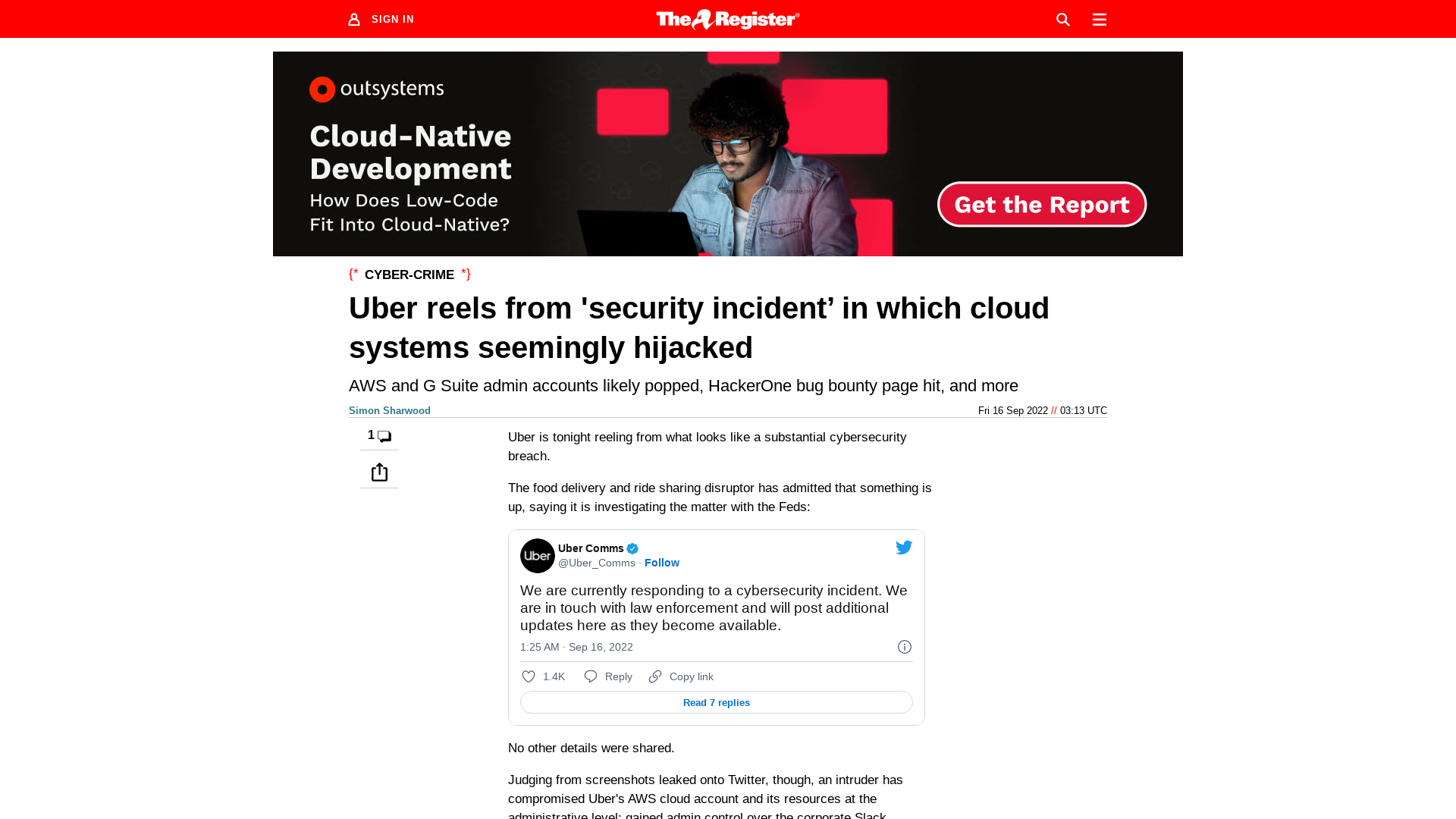
Widespread prototype pollution gadgets | PortSwigger Research
https://portswigger.net/research/widespread-prototype-pollution-gadgets
Bypassing Firefox's HTML Sanitizer API | PortSwigger Research
https://portswigger.net/research/bypassing-firefoxs-html-sanitizer-api
CyberGrants | CISA
http://cisa.gov/CyberGrants
Bill Demirkapi on Twitter: "The scope of this attack demonstrates another problem with centralizing authentication. It can often be a single point of failure that can give attackers a wide variety of access, as we've seen in this example. USE PHISHING RESISTANT MFA!! Stop making it easy for attackers. 12/N" / Twitter
https://twitter.com/billdemirkapi/status/1570608023831478274
Get root on macOS 12.3.1: proof-of-concepts for Linus Henze’s CoreTrust and DriverKit bugs (CVE-2022-26766, CVE-2022-26763) | Worth Doing Badly
https://worthdoingbadly.com/coretrust/
Corben Leo on Twitter: "Uber was hacked. The hacker social engineered an employee -> logged into the VPN and scanned their intranet. 👇" / Twitter
https://twitter.com/hacker_/status/1570582202697809920
Kevin Roose on Twitter: "Update: a person claiming responsibility for the Uber hack tells the NYT that he is 18, got in through social engineering an employee’s password, and hacked the company because it had weak security. https://t.co/h3k7H9lpSo https://t.co/TZ8aDrNyQQ" / Twitter
https://twitter.com/kevinroose/status/1570604737317441539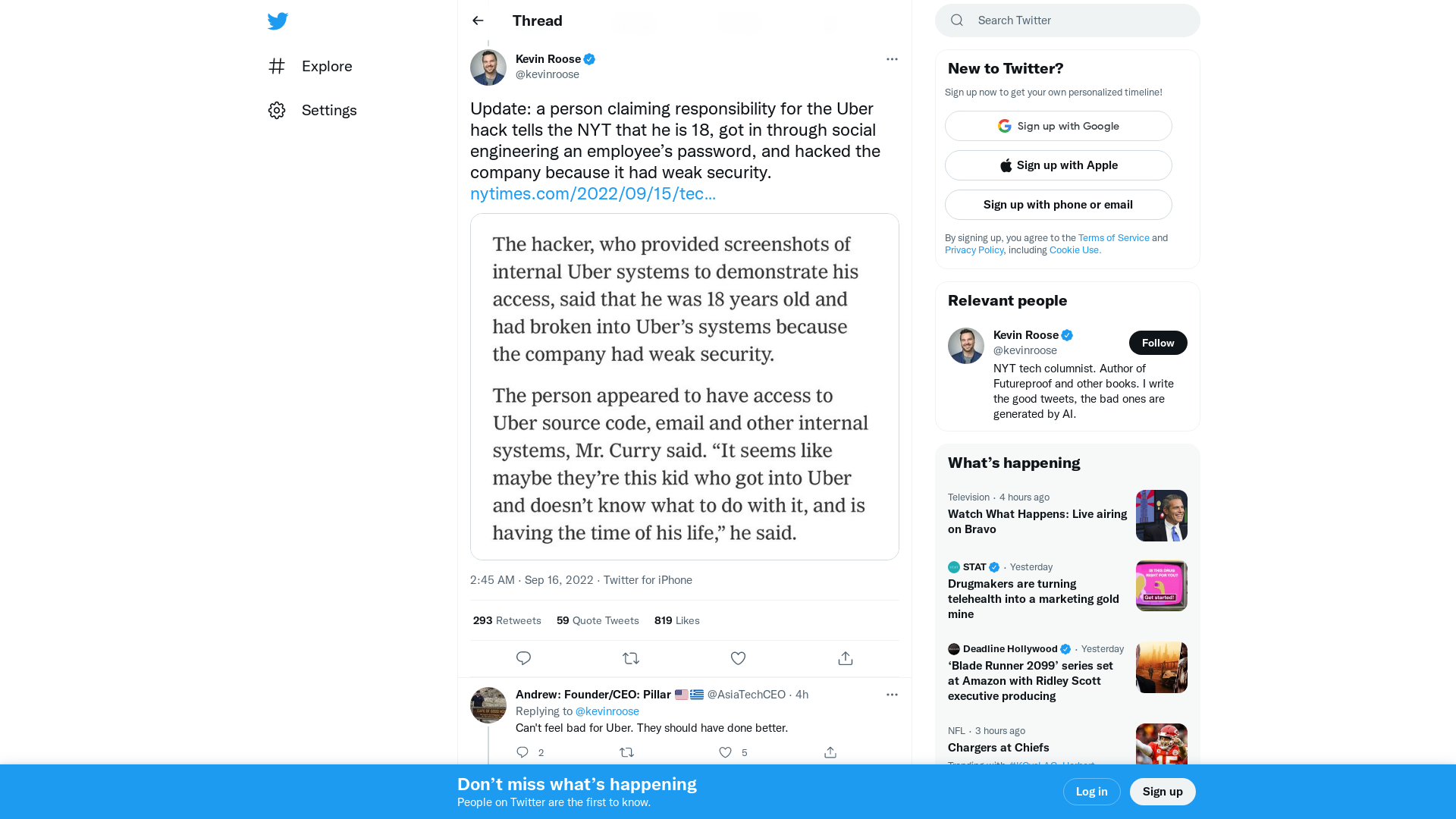
CVE-2022-34718 - Security Update Guide - Microsoft - Windows TCP/IP Remote Code Execution Vulnerability
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-34718
Cisco Talos Intelligence Group - Comprehensive Threat Intelligence: Gamaredon APT targets Ukrainian government agencies in new campaign
https://blog.talosintelligence.com/2022/09/gamaredon-apt-targets-ukrainian-agencies.html