Microsoft Teams stores auth tokens as cleartext in Windows, Linux, Macs
https://www.bleepingcomputer.com/news/security/microsoft-teams-stores-auth-tokens-as-cleartext-in-windows-linux-macs/
Attacking the Android kernel using the Qualcomm TrustZone | Tamir Zahavi-Brunner’s Blog
https://tamirzb.com/attacking-android-kernel-using-qualcomm-trustzone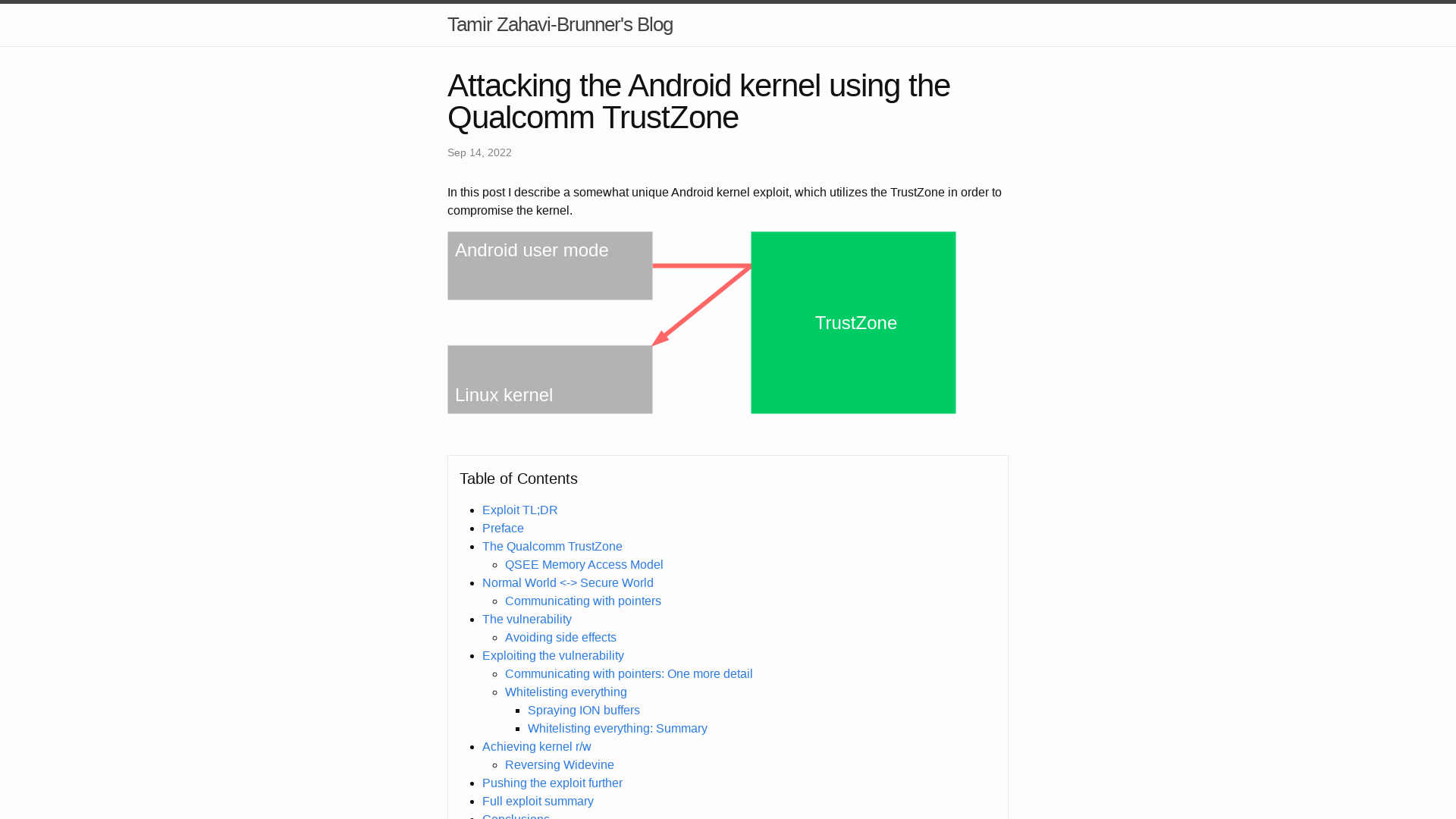
RED TEAM Operator: Malware Development Advanced - Vol.1
https://institute.sektor7.net/rto-maldev-adv1
New PsExec spinoff lets hackers bypass network security defenses
https://www.bleepingcomputer.com/news/security/new-psexec-spinoff-lets-hackers-bypass-network-security-defenses/
Introducing Bishop Fox Security Tool: CloudFox | Bishop Fox
https://bishopfox.com/blog/introducing-cloudfox
GitHub - BishopFox/cloudfox: Automating situational awareness for cloud penetration tests.
https://github.com/BishopFox/cloudfox
Caching the Un-cacheables - Abusing URL Parser Confusions (Web Cache Poisoning Technique) | Harel Security Research
https://nokline.github.io/bugbounty/2022/09/02/Glassdoor-Cache-Poisoning.html
Zero-day in WPGateway Wordpress plugin actively exploited in attacks
https://www.bleepingcomputer.com/news/security/zero-day-in-wpgateway-wordpress-plugin-actively-exploited-in-attacks/
Twilio lays off 11% of its staff as it aims for profitability in 2023 | TechCrunch
https://techcrunch.com/2022/09/14/twilio-lays-off-11-of-its-staff-as-it-aims-for-profitability-in-2023/
Treasury Sanctions IRGC-Affiliated Cyber Actors for Roles in Ransomware Activity | U.S. Department of the Treasury
https://home.treasury.gov/news/press-releases/jy0948
SparklingGoblin APT Hackers Using New Linux Variant of SideWalk Backdoor
https://thehackernews.com/2022/09/sparklinggoblin-apt-hackers-using-new.html
CVE-2022-37969 - Security Update Guide - Microsoft - Windows Common Log File System Driver Elevation of Privilege Vulnerability
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-37969
CSA_IRGC.PDF
https://media.defense.gov/2022/Sep/14/2003076379/-1/-1/0/CSA_IRGC.PDF
Dissecting%20PlugX%20to%20Extract%20Its%20Crown%20Jewels.pdf
https://secjoes-reports.s3.eu-central-1.amazonaws.com/Dissecting+PlugX+to+Extract+Its+Crown+Jewels.pdf
Job Application for Security Analyst at Tall Poppy
https://boards.greenhouse.io/tallpoppy/jobs/5297808003
You never walk alone: The SideWalk backdoor gets a Linux variant | WeLiveSecurity
https://www.welivesecurity.com/2022/09/14/you-never-walk-alone-sidewalk-backdoor-linux-variant/
Over 280,000 WordPress Sites Attacked Using WPGateway Plugin Zero-Day Vulnerability
https://thehackernews.com/2022/09/over-280000-wordpress-sites-attacked.html
Iranian Islamic Revolutionary Guard Corps-Affiliated Cyber Actors Exploiting Vulnerabilities for Data Extortion and Disk Encryption for Ransom Operations | CISA
https://www.cisa.gov/uscert/ncas/alerts/aa22-257a
Malware Analysis Series (MAS) – Article 5 – Exploit Reversing
https://exploitreversing.com/2022/09/14/malware-analysis-series-mas-article-5/
Firebombs and Shootings: The Rise of IRL Harassment and Violence as a Service
https://www.vice.com/en/article/3advxj/firebombings-shootings-as-a-service-telegram
Ronan Farrow on Twitter: "“They didn’t care how much it would cost them.” People around Twitter whistleblower Peiter “Mudge” Zatko are being inundated by offers from secret clients paying for dirt on him, as he testifies on the Hill about an alleged security crisis at Twitter. NEW: https://t.co/wnaPSIrFiZ" / Twitter
https://twitter.com/ronanfarrow/status/1569731738347216897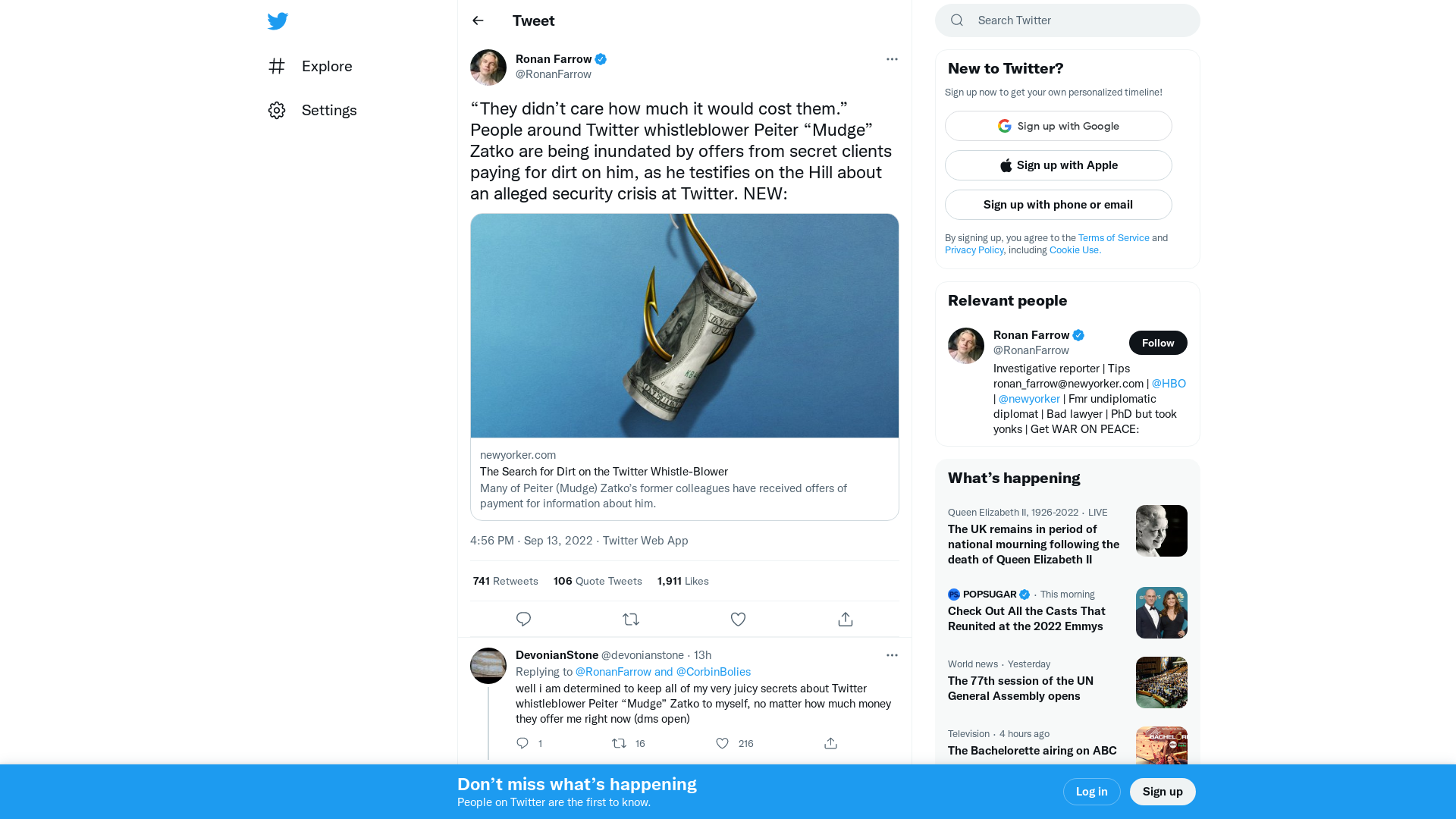
Death of Queen Elizabeth II exploited to steal Microsoft credentials
https://www.bleepingcomputer.com/news/security/death-of-queen-elizabeth-ii-exploited-to-steal-microsoft-credentials/
Here’s the Goatse Image Hackers Sent on the Seesaw Parent-Teacher Messaging App at Schools Around the Country
https://www.vice.com/en/article/3adpqn/seesaw-hacked-porn-images
GitHub - Accenture/Codecepticon
https://github.com/Accenture/Codecepticon
[48] Malware Lab - Shellcode Injection Unpacking and Extraction - YouTube
https://www.youtube.com/watch?v=07D0GbbPSi4![[48] Malware Lab - Shellcode Injection Unpacking and Extraction - YouTube](/image/screenshot/fb77bb9d946fe303a7dddab6392e9cdd.png)
Dan Hill on Twitter: "Mudge in front of Congress in 1998 vs 2022 https://t.co/ykVp1t6lmh" / Twitter
https://twitter.com/duncanyoudaho/status/1569800108568637441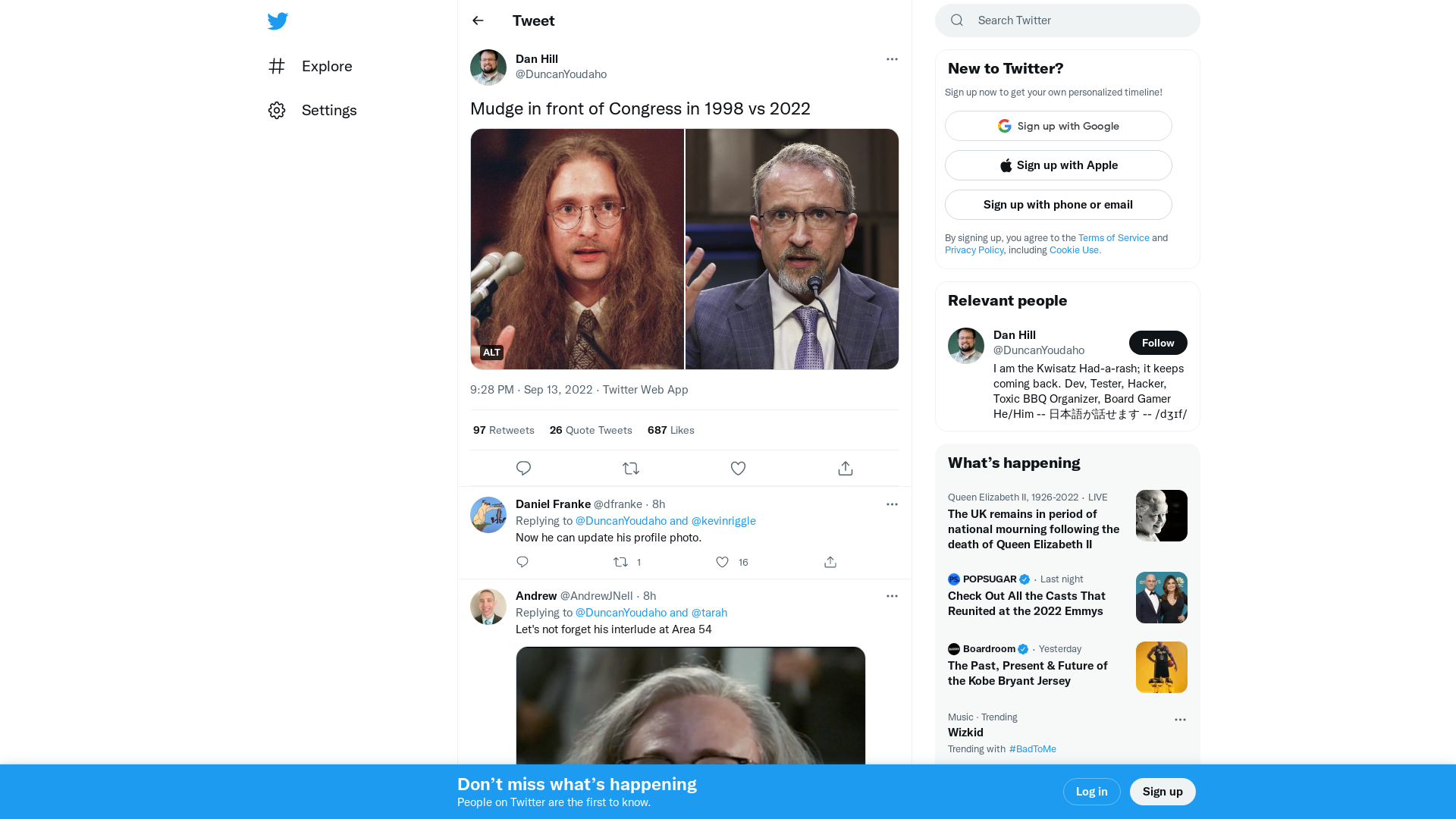
Three Iranian Nationals Charged with Engaging in Computer Intrusions and Ransomware-Style Extortion Against U.S. Critical Infrastructure Providers | OPA | Department of Justice
https://www.justice.gov/opa/pr/three-iranian-nationals-charged-engaging-computer-intrusions-and-ransomware-style-extortion
Mark Malone on Twitter: "Patreon are shutting their Dublin offices and sacking 80 workerss A public blogpost stated those sacked would get an email in ten minutes letting them know. Patreon calls sacking workers a seperation It's 'European HQ' only opened in 2019, subsidised by the IDA with usual PR. https://t.co/Efh6xY3Pby" / Twitter
https://twitter.com/soundmigration/status/1569933839434235904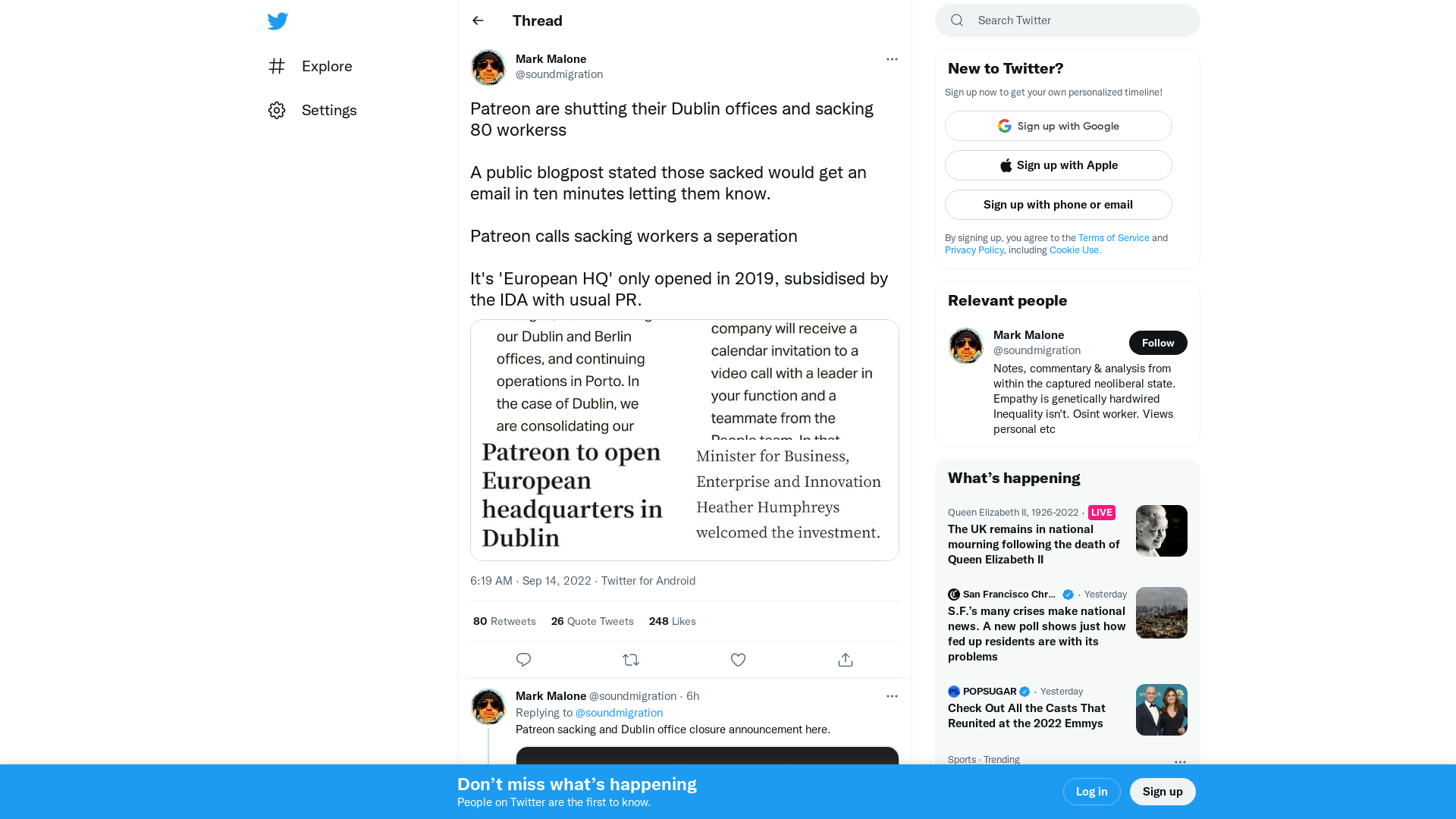
Hackers now use ‘sock puppets’ for more realistic phishing attacks
https://www.bleepingcomputer.com/news/security/hackers-now-use-sock-puppets-for-more-realistic-phishing-attacks/
Iranian Cyber Actors Exploit Known Vulnerabilities to Extort U.S. Critical Infrastructure Organizations, Other Victims > National Security Agency/Central Security Service > Press Release View
https://www.nsa.gov/Press-Room/Press-Releases-Statements/Press-Release-View/Article/3157562/iranian-cyber-actors-exploit-known-vulnerabilities-to-extort-us-critical-infras/
GitHub - b23r0/Heroinn: A cross platform C2/post-exploitation framework.
https://github.com/b23r0/Heroinn