Attacking Firecracker: AWS' microVM Monitor Written in Rust - Blog | Grapl
http://www.graplsecurity.com/post/attacking-firecracker
Microsoft investigates Iranian attacks against the Albanian government - Microsoft Security Blog
https://www.microsoft.com/security/blog/2022/09/08/microsoft-investigates-iranian-attacks-against-the-albanian-government/
2306 - Windows: Credential Guard KerbIumGetNtlmSupplementalCredential Information Disclosure - project-zero
https://bugs.chromium.org/p/project-zero/issues/detail?id=2306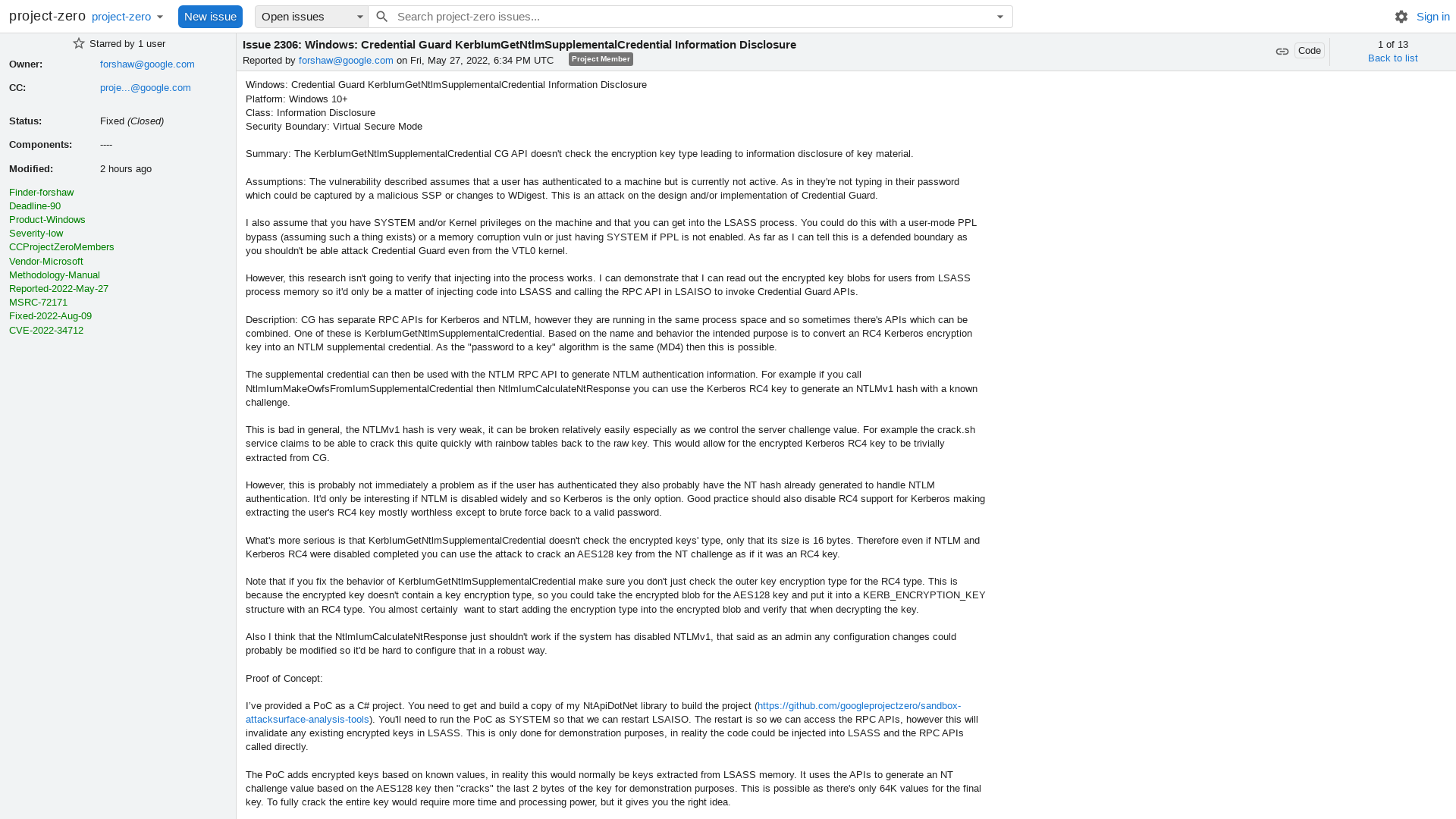
James Forshaw on Twitter: "I must say, https://t.co/hXzDGvrjSg is pretty impressive. 45 seconds for a NTLMv1 hash :) Of course if anyone can tell me what the password was I'd appreciate it, seems I've forgotten😂 https://t.co/EMp3ZnEw8B" / Twitter
https://twitter.com/tiraniddo/status/1535506402600357889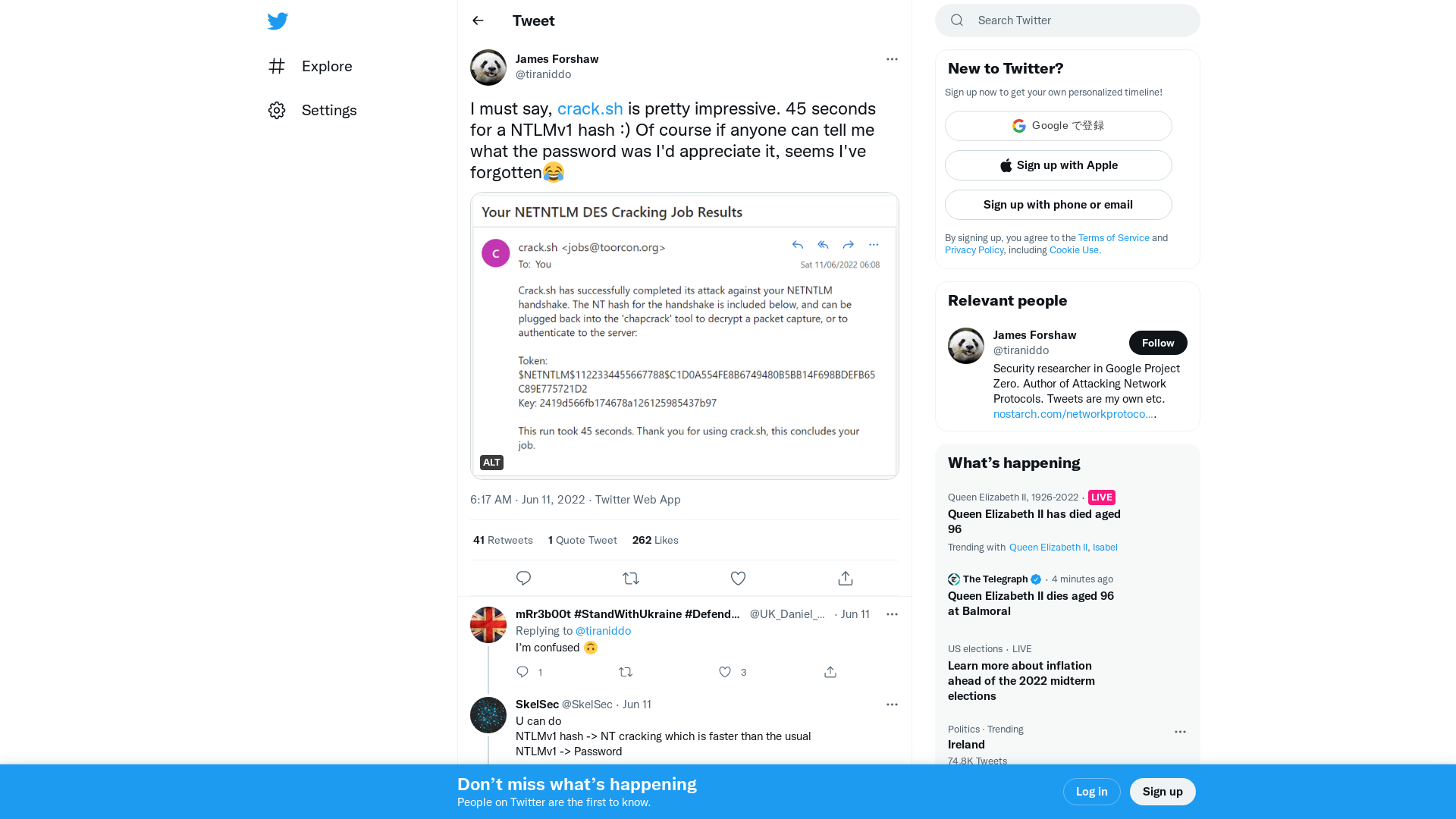
Whitney Merrill on Twitter: "Whoa @Patreon laid off their ENTIRE security team. Wouldn’t trust my data there. Also there’s some amazing talent to scoop up." / Twitter
https://twitter.com/wbm312/status/1567974063578185728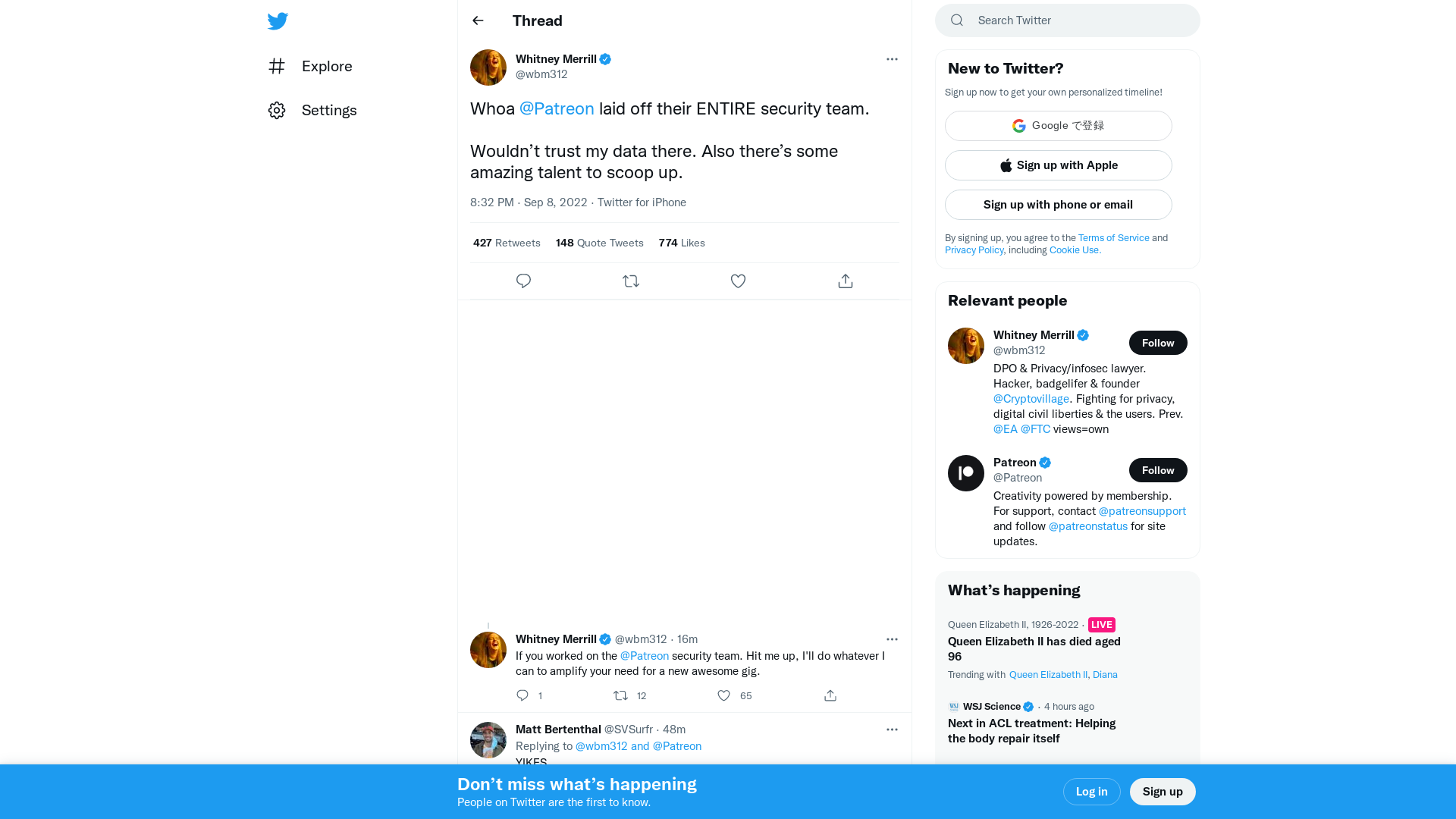
2313 - .NET: External Entity Injection during XML signature verification - project-zero
https://bugs.chromium.org/p/project-zero/issues/detail?id=2313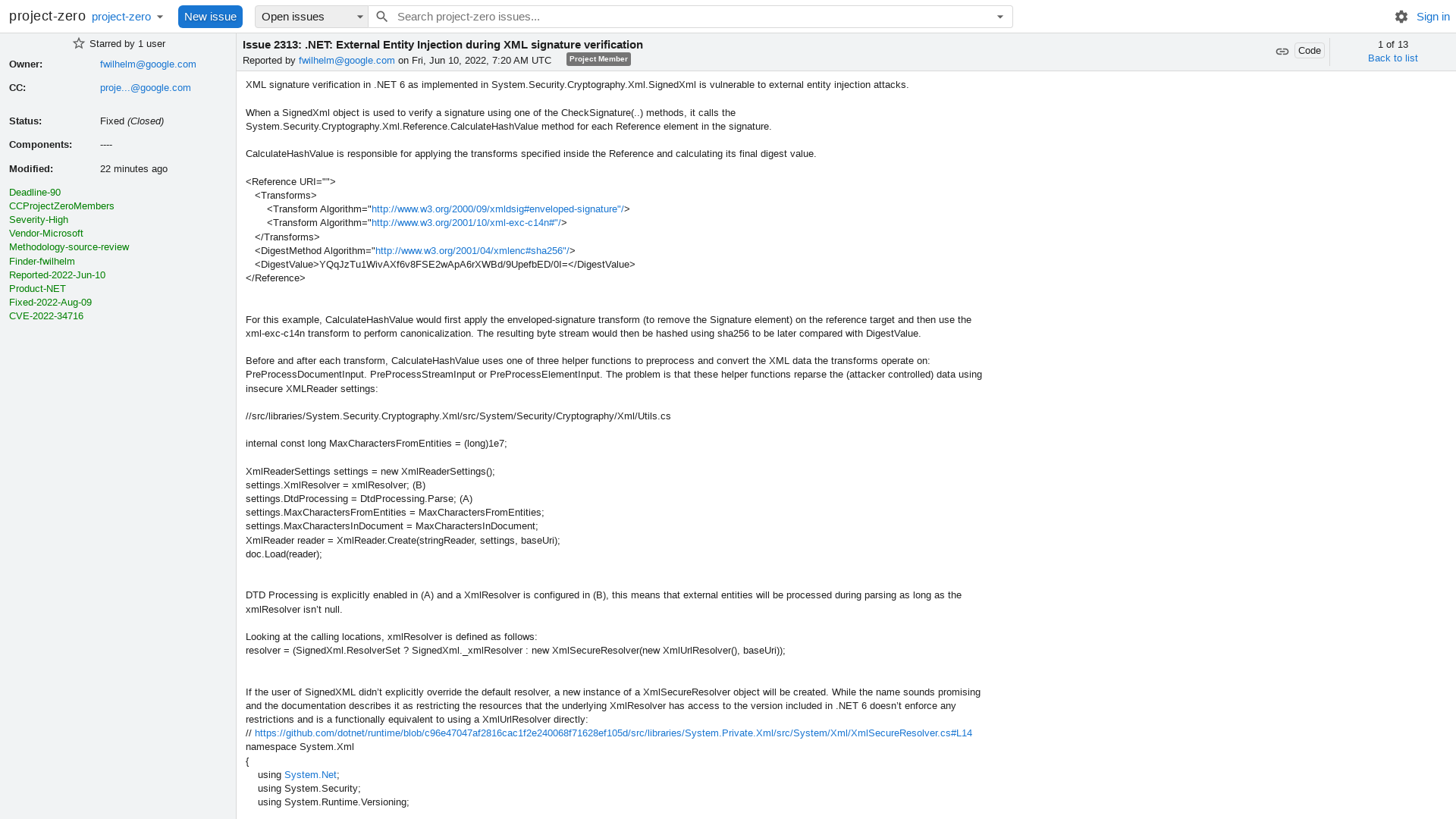
APT42: Crooked Charms, Cons, and Compromises | Mandiant
https://www.mandiant.com/resources/blog/apt42-charms-cons-compromises
Profiling DEV-0270: PHOSPHORUS’ ransomware operations - Microsoft Security Blog
https://www.microsoft.com/security/blog/2022/09/07/profiling-dev-0270-phosphorus-ransomware-operations/
Ransomware gang's Cobalt Strike servers DDoSed with anti-Russia messages
https://www.bleepingcomputer.com/news/security/ransomware-gangs-cobalt-strike-servers-ddosed-with-anti-russia-messages/
GIFShell attack creates reverse shell using Microsoft Teams GIFs
https://www.bleepingcomputer.com/news/security/gifshell-attack-creates-reverse-shell-using-microsoft-teams-gifs/
Initial access broker repurposing techniques in targeted attacks against Ukraine
https://blog.google/threat-analysis-group/initial-access-broker-repurposing-techniques-in-targeted-attacks-against-ukraine/
GitHub - CodeXTF2/cobaltstrike-headless: Aggressorscript that turns the headless aggressor client into a (mostly) functional cobalt strike client.
https://github.com/CodeXTF2/cobaltstrike-headless
GitHub - HavocFramework/Modules: Modules used by the Havoc Framework
https://github.com/HavocFramework/Modules
Google Online Security Blog: Fuzzing beyond memory corruption: Finding broader classes of vulnerabilities automatically
https://security.googleblog.com/2022/09/fuzzing-beyond-memory-corruption.html
On Detection: Tactical to Function | by Jared Atkinson | Sep, 2022 | Posts By SpecterOps Team Members
https://posts.specterops.io/on-detection-tactical-to-function-810c14798f63
GitHub - thinkst/canarytokens-docker: Docker configuration to quickly setup your own Canarytokens.
https://github.com/thinkst/canarytokens-docker
Microsoft Warns of Ransomware Attacks by Iranian Phosphorus Hacker Group
https://thehackernews.com/2022/09/microsoft-warns-of-ransomware-attacks.html
The Curious Case of “Monti” Ransomware: A Real-World Doppelganger
https://blogs.blackberry.com/en/2022/09/the-curious-case-of-monti-ransomware-a-real-world-doppelganger
Queen Elizabeth II has died - BBC News
https://bbc.in/3ewsh18
HADNAGY v. MOSS, 2:22-cv-03060 – CourtListener.com
https://www.courtlistener.com/docket/64866230/hadnagy-v-moss/
Cisco Releases Security Patches for New Vulnerabilities Impacting Multiple Products
https://thehackernews.com/2022/09/cisco-releases-security-patches-for-new.html
North Korean Lazarus Hackers Targeting Energy Providers Around the World
https://thehackernews.com/2022/09/north-korean-lazarus-hackers-targeting.html
Cybersecurity Alert Priority Matrix | by Josh Lemon | Medium
https://blog.joshlemon.com.au/cybersecurity-alert-priority-matrix-92a20fe8d955
SOC Core Skills w/ John Strand - Antisyphon
https://www.antisyphontraining.com/soc-core-skills-w-john-strand/
Albanian cyber war - by the grugq - The Info Op
https://grugq.substack.com/p/albanian-cyber-war