Cloudflare on Twitter: "Cloudflare launched nearly twelve years ago. Over that time, our set of services has become much more complicated. With that complexity we have developed policies around how we handle abuse of different features Cloudflare provides https://t.co/dxJw0yg6MA" / Twitter
https://twitter.com/Cloudflare/status/1564964203542315010
Cloudflare on Twitter: "Cloudflare launched nearly twelve years ago. Over that time, our set of services has become much more complicated. With that complexity we have developed policies around how we handle abuse of different features Cloudflare provides https://t.co/dxJw0yg6MA" / Twitter
https://twitter.com/cloudflare/status/1564964203542315010
BLACKHAT_USA2022 - Google ドライブ
https://drive.google.com/drive/mobile/folders/1KHx2rKUEdb53flGUN0mFHRdSdB5PUT4B?fbclid=IwAR1C2Fk3XDPU-ky-4B57ZmKtEKgjB6Yg-9m2c6MTxyJd779yPV7MCCHCvWo&fs=e&s=c
NCC Con Europe 2022 – Pwn2Own Austin Presentations – NCC Group Research
https://research.nccgroup.com/2022/08/30/ncc-con-europe-2022-pwn2own-austin-presentations/
GitHub - ps1337/reinschauer
https://github.com/ps1337/reinschauer
JPCERT/CCが確認したフィッシングサイトのURLを公開 - JPCERT/CC Eyes | JPCERTコーディネーションセンター公式ブログ
https://blogs.jpcert.or.jp/ja/2022/08/phishurl-list.html
Automating Azure Abuse Research — Part 2 | by Andy Robbins | Aug, 2022 | Posts By SpecterOps Team Members
https://posts.specterops.io/automating-azure-abuse-research-part-2-3e5bbe7a20c0
GitHub - p0dalirius/MSSQL-Analysis-Coerce: A technique to coerce a Windows SQL Server to authenticate on an arbitrary machine.
https://github.com/p0dalirius/MSSQL-Analysis-Coerce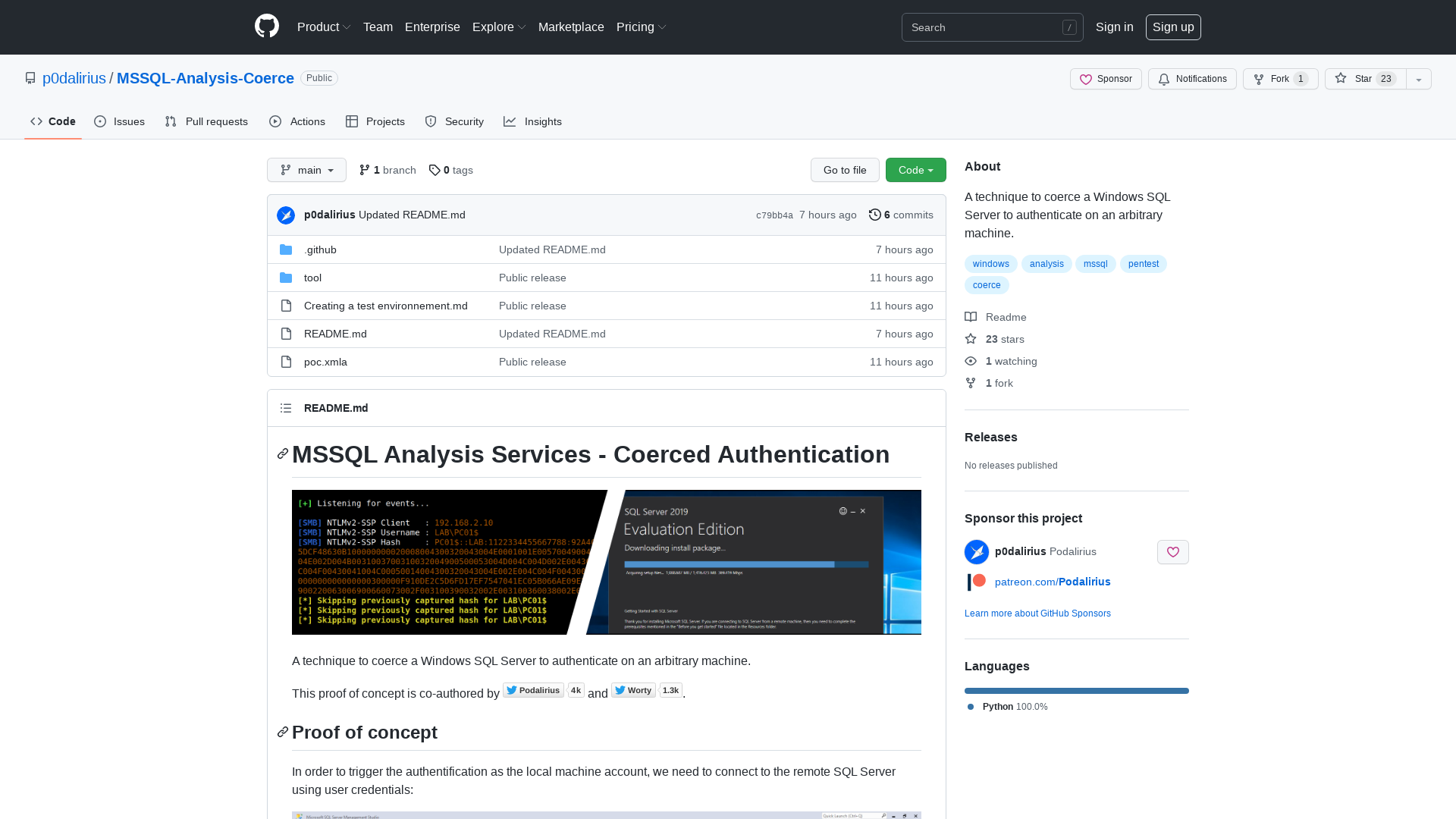
Hackers hide malware in James Webb telescope images
https://www.bleepingcomputer.com/news/security/hackers-hide-malware-in-james-webb-telescope-images/
Announcing the Ninth Annual Flare-On Challenge | Mandiant
https://www.mandiant.com/resources/announcing-ninth-flareon-challenge
Semperis on Twitter: "#AzureAD admins, beware: #Cyberattackers can use SMTP matching to obtain privileged access via eligible role assignments. In this post by @SemperisTech Security Researchers Sapir Federovsky and Tomer Nahum, learn how- and how to stop them. https://t.co/Z2jDJZIoCk" / Twitter
https://twitter.com/SemperisTech/status/1564744534508060674
Digging into an NTLM Downgrade Attack - Praetorian
https://www.praetorian.com/blog/ntlmv1-vs-ntlmv2/
GitHub - dr4k0nia/Origami: Packer compressing .net assemblies, (ab)using the PE format for data storage
https://github.com/dr4k0nia/Origami
IcedID_08_31_2022.txt · GitHub
https://gist.github.com/myrtus0x0/c025d1e7feacc403cbb6923dd43b86a5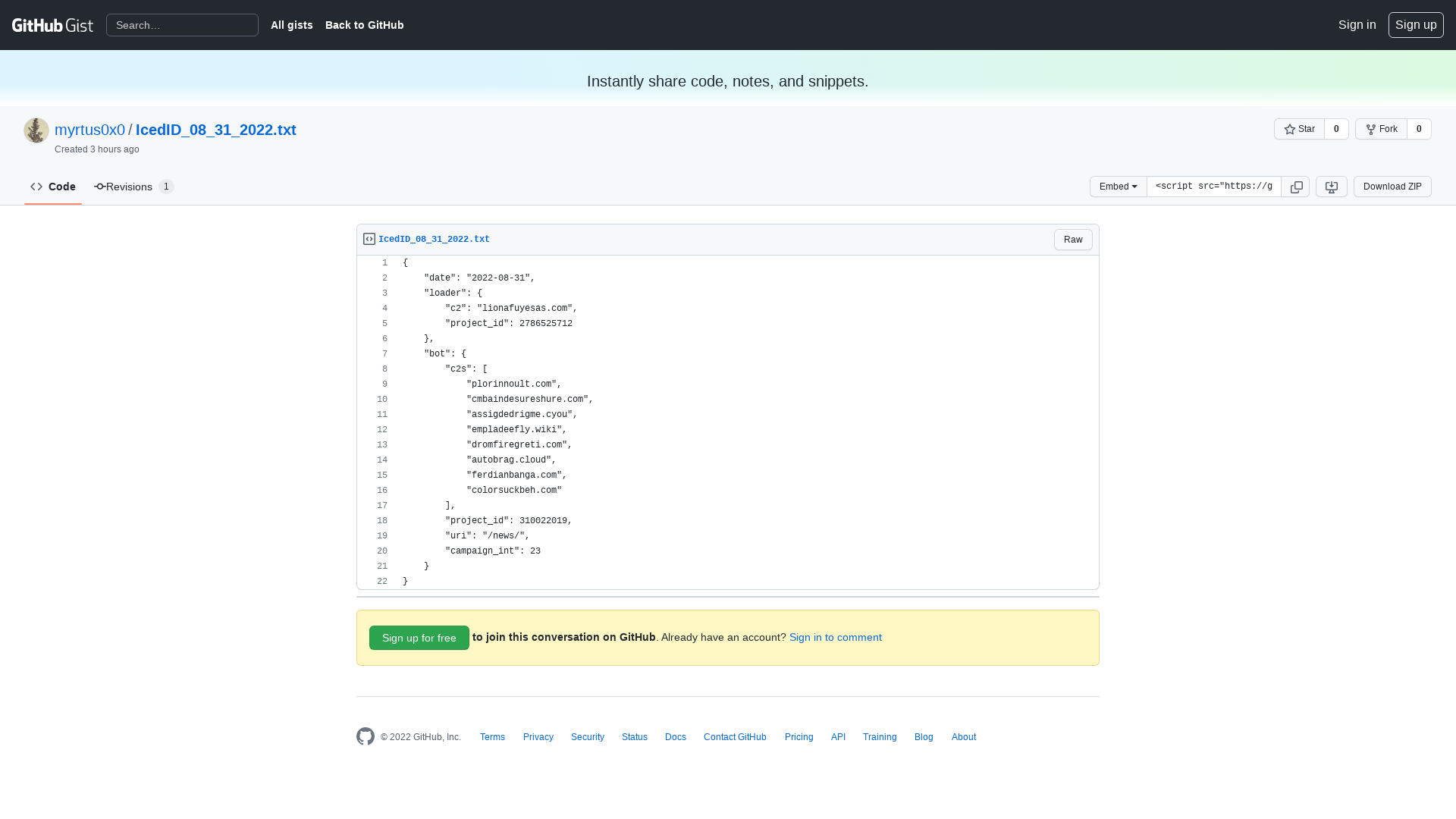
CVE-2022-26113: FortiClient Arbitrary File Write As SYSTEM - Rhino Security Labs
https://rhinosecuritylabs.com/research/cve-2022-26113-forticlient-arbitrary-file-write-as-system/
Dan Goodin on Twitter: "Behold the arrogance and nonchalance of this exec offering to pay me to write about his security snake oil product and then telling me to "take a chill pill" when he gets my response. In the past, I have redacted names when I posted emails like these on social media. Not anymore. https://t.co/irZQcphcNX" / Twitter
https://twitter.com/dangoodin001/status/1565009426376888320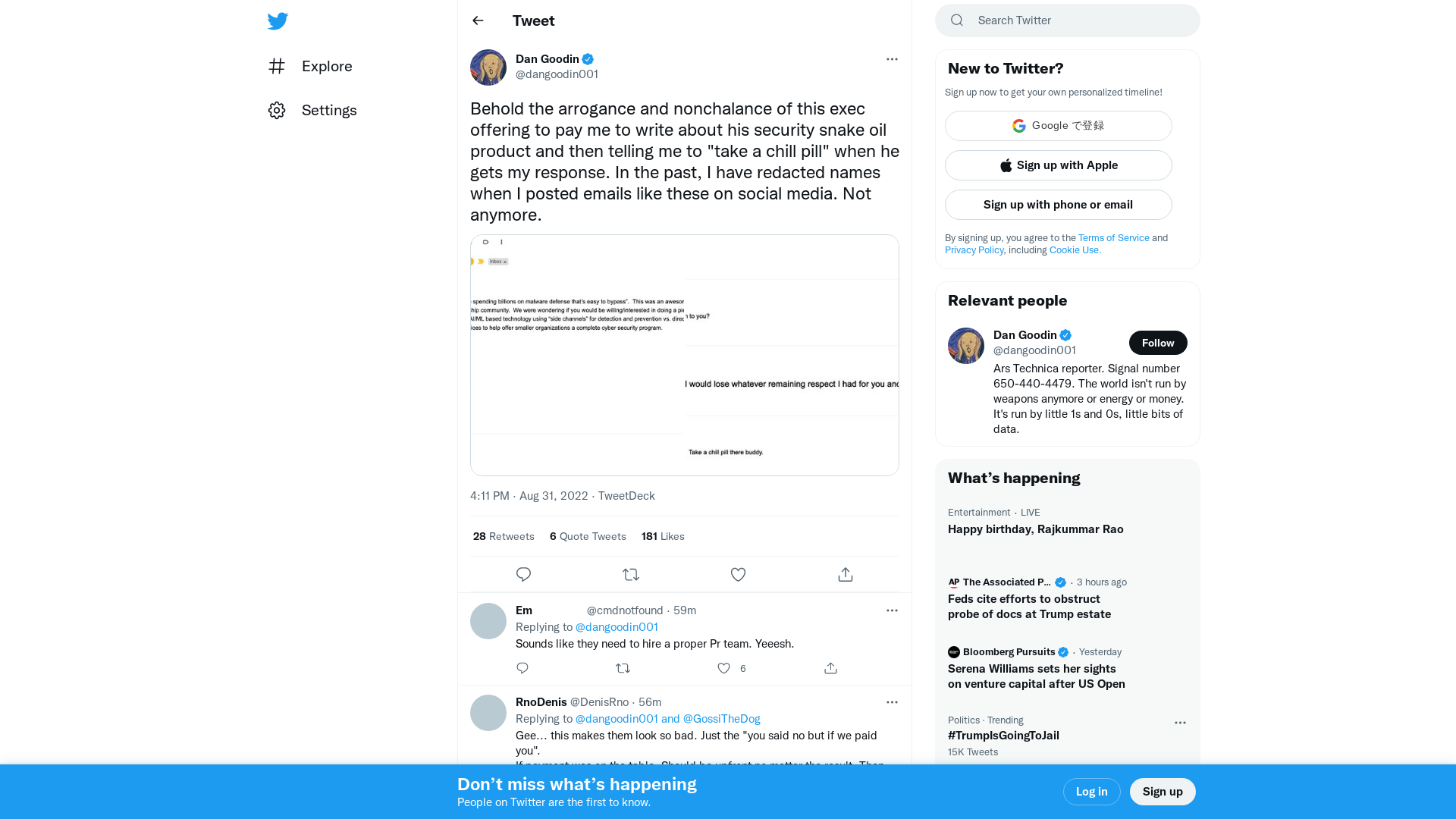
GitHub - olafhartong/MDE-AuditCheck: MDE relies on some of the Audit settings to be enabled
https://github.com/olafhartong/MDE-AuditCheck
MalwareBazaar | SHA256 e785dc7389084a775373d02a861bab1e75582570363cd6773ef2b986a0a1857a (IcedID)
https://bazaar.abuse.ch/sample/e785dc7389084a775373d02a861bab1e75582570363cd6773ef2b986a0a1857a/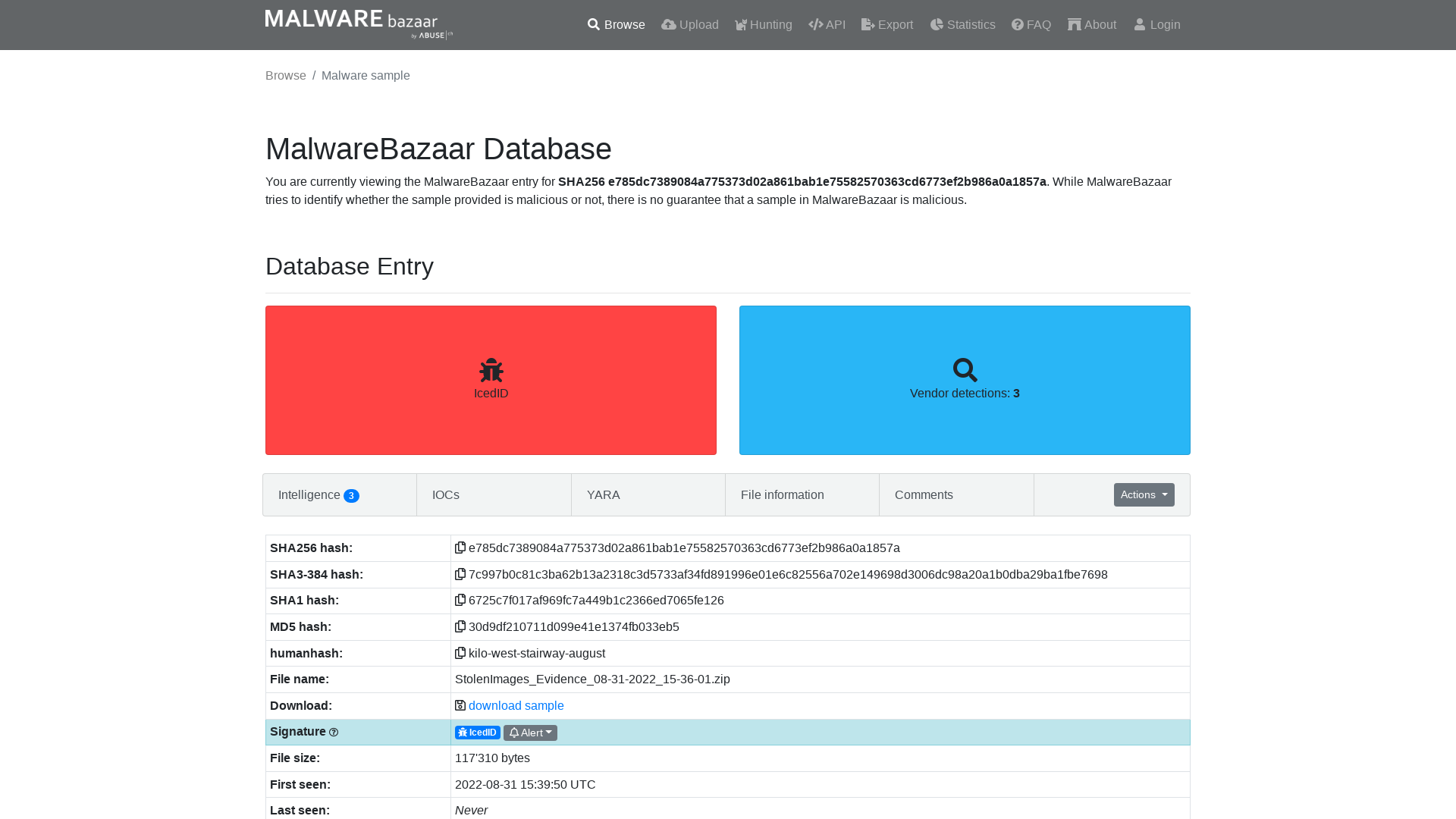
pwn.college
https://dojo.pwn.college/cse466/challenges/asm
Ekoparty | Hacking everything on Twitter: "Meet the Keynote speakers! ⚡ @ryanaraine is a cybersecurity strategist and career journalist with more than 20 years as a cybersecurity leader and practitioner. Don't miss his talk at #EKO2022, from November 2 to 4 at @CEC_BsAs! SAVE YOUR SEAT NOW 👉 https://t.co/hLkmlAfI4s https://t.co/wl8flN4iKt" / Twitter
https://twitter.com/ekoparty/status/1564719004421349376
Last Week in Security (LWiS) - 2022-08-30 | Bad Sector Labs Blog
https://blog.badsectorlabs.com/last-week-in-security-lwis-2022-08-30.html
Walmart Sells Fake 30TB Hard Drive That’s Actually Two Small SD Cards in a Trench Coat
https://www.vice.com/en/article/akek8e/walmart-30tb-ssd-hard-drive-scam-sd-cards
Kevin Beaumont on Twitter: "Montonegro is indeed ransomware." / Twitter
https://twitter.com/gossithedog/status/1564644686828130305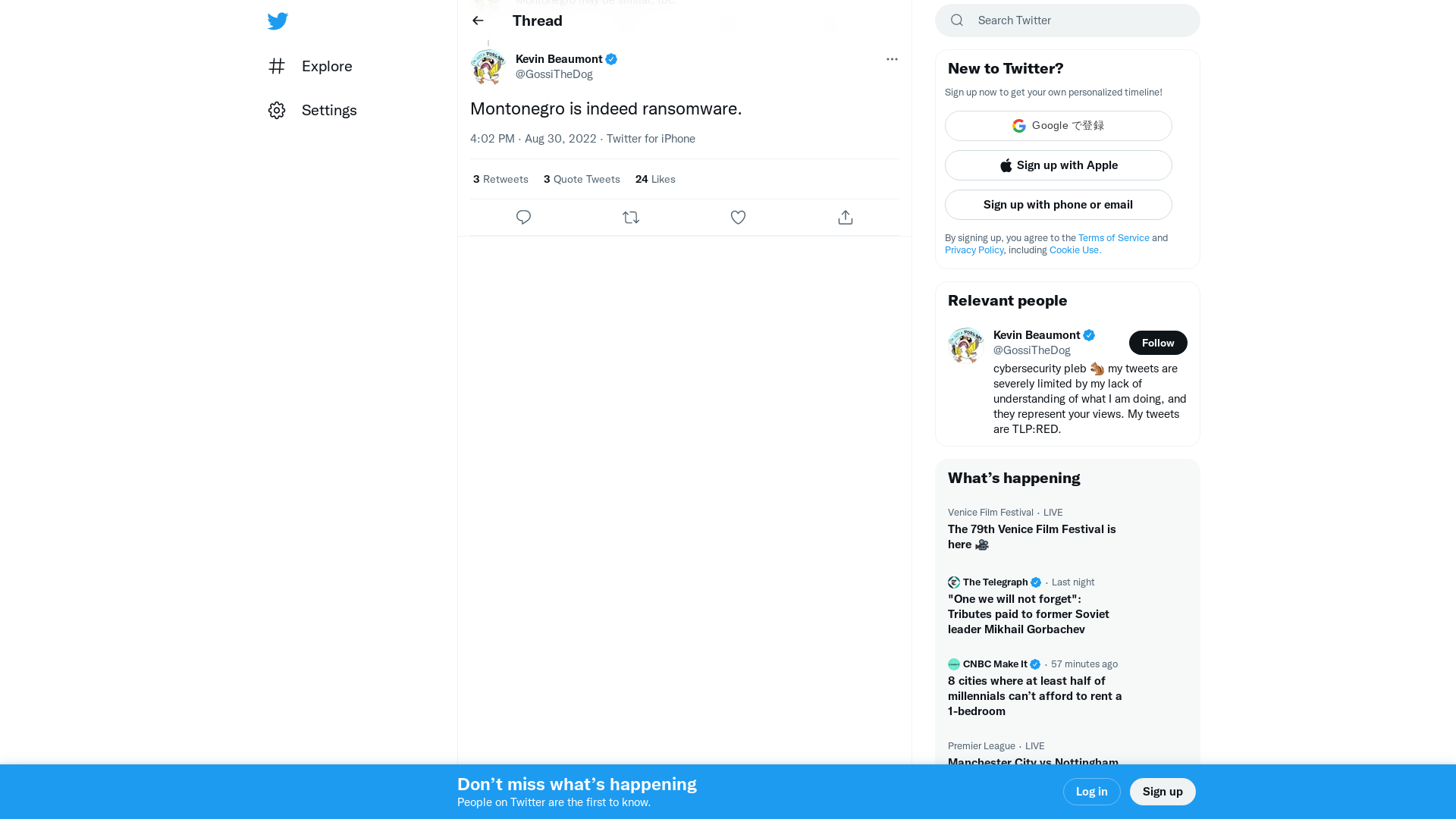
Google Online Security Blog: Announcing Google’s Open Source Software Vulnerability Rewards Program
https://security.googleblog.com/2023/08/Announcing-Googles-Open-Source-Software-Vulnerability-Rewards-Program%20.html
Google Launches New Open Source Bug Bounty to Tackle Supply Chain Attacks
https://thehackernews.com/2022/08/google-launches-new-open-source-bug.html
Hackers Hide Malware in Stunning Images Taken by James Webb Space Telescope
https://thehackernews.com/2022/08/hackers-hide-malware-in-stunning-images.html
IcedID/icedID_31.08.2022.txt at main · pr0xylife/IcedID · GitHub
https://github.com/pr0xylife/IcedID/blob/main/icedID_31.08.2022.txt
Kyle Cheney on Twitter: "NEWS: DOJ's new filing includes. photo of the classified documents found at Mar-a-Lago on Aug. 8. https://t.co/nm567c96bi https://t.co/0U2hoSogxQ" / Twitter
https://twitter.com/kyledcheney/status/1564817161528692737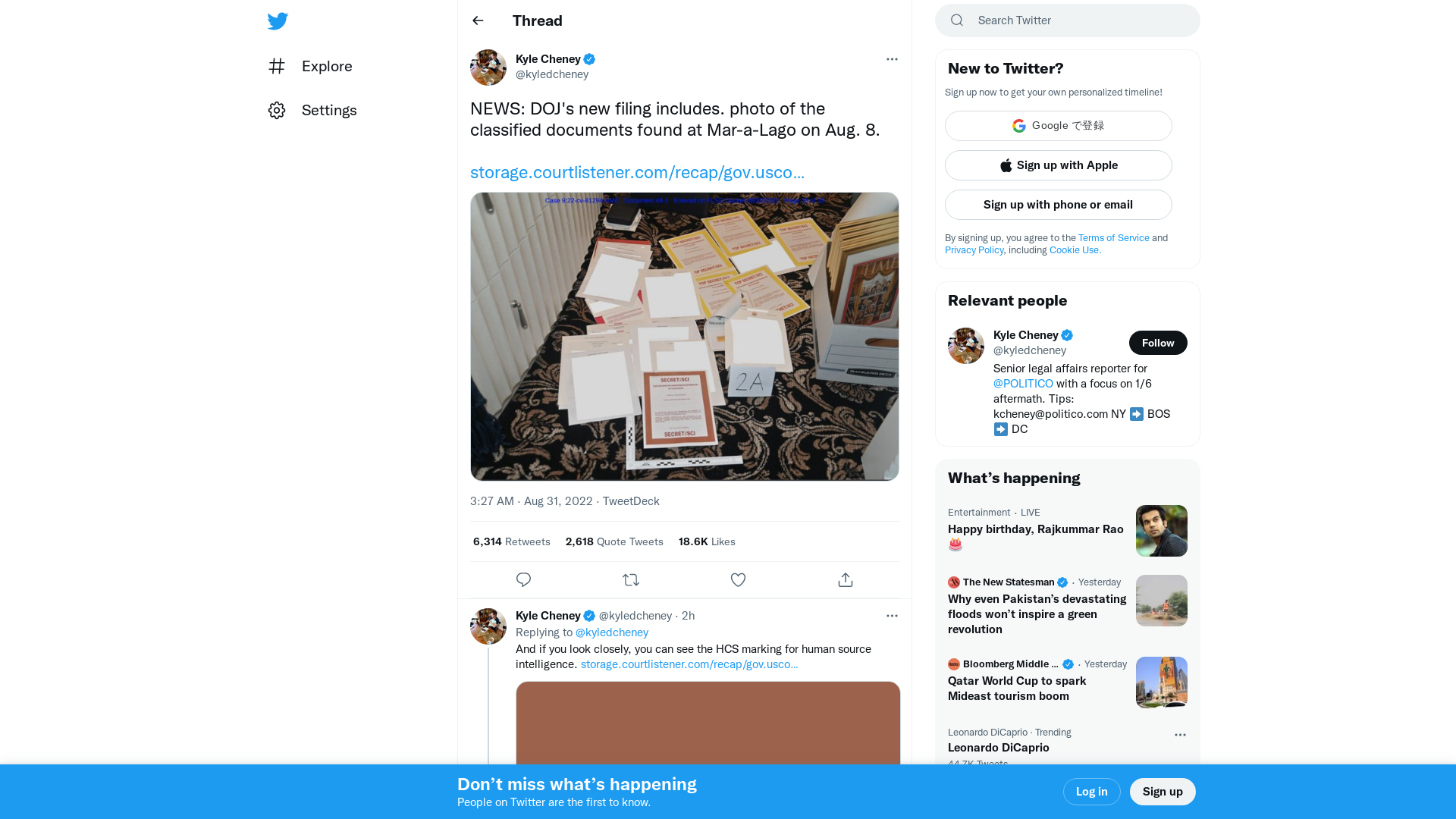
Chinese Hackers Used ScanBox Framework in Recent Cyber Espionage Attacks
https://thehackernews.com/2022/08/chinese-hackers-used-scanbox-framework.html