Ransomware Actor Abuses Genshin Impact Anti-Cheat Driver to Kill Antivirus
https://www.trendmicro.com/en_us/research/22/h/ransomware-actor-abuses-genshin-impact-anti-cheat-driver-to-kill-antivirus.html
Notice of Recent Security Incident - The LastPass Blog
https://blog.lastpass.com/2022/08/notice-of-recent-security-incident/
The White House on Twitter: "Congresswoman Marjorie Taylor Greene had $183,504 in PPP loans forgiven. https://t.co/4FoCymt8TB" / Twitter
https://twitter.com/WhiteHouse/status/1562916200866267138
2290 - Xalan-J: integer truncation in XSLTC - project-zero
https://bugs.chromium.org/p/project-zero/issues/detail?id=2290
Ghidrathon: Snaking Ghidra with Python 3 Scripting | Mandiant
https://www.mandiant.com/resources/blog/ghidrathon-snaking-ghidra-python-3-scripting
Websites Can Identify If You’re Using iPhone’s New ‘Lockdown’ Mode
https://www.vice.com/en/article/epzpb4/websites-can-identify-if-youre-using-iphones-new-lockdown-mode
Jon Callas on Twitter: "I have a 🧵 about CISOs and CSOs and their fate. Get a cold drink or maybe a cuppa, as this is a long one. 1/32" / Twitter
https://twitter.com/joncallas/status/1562690112147709952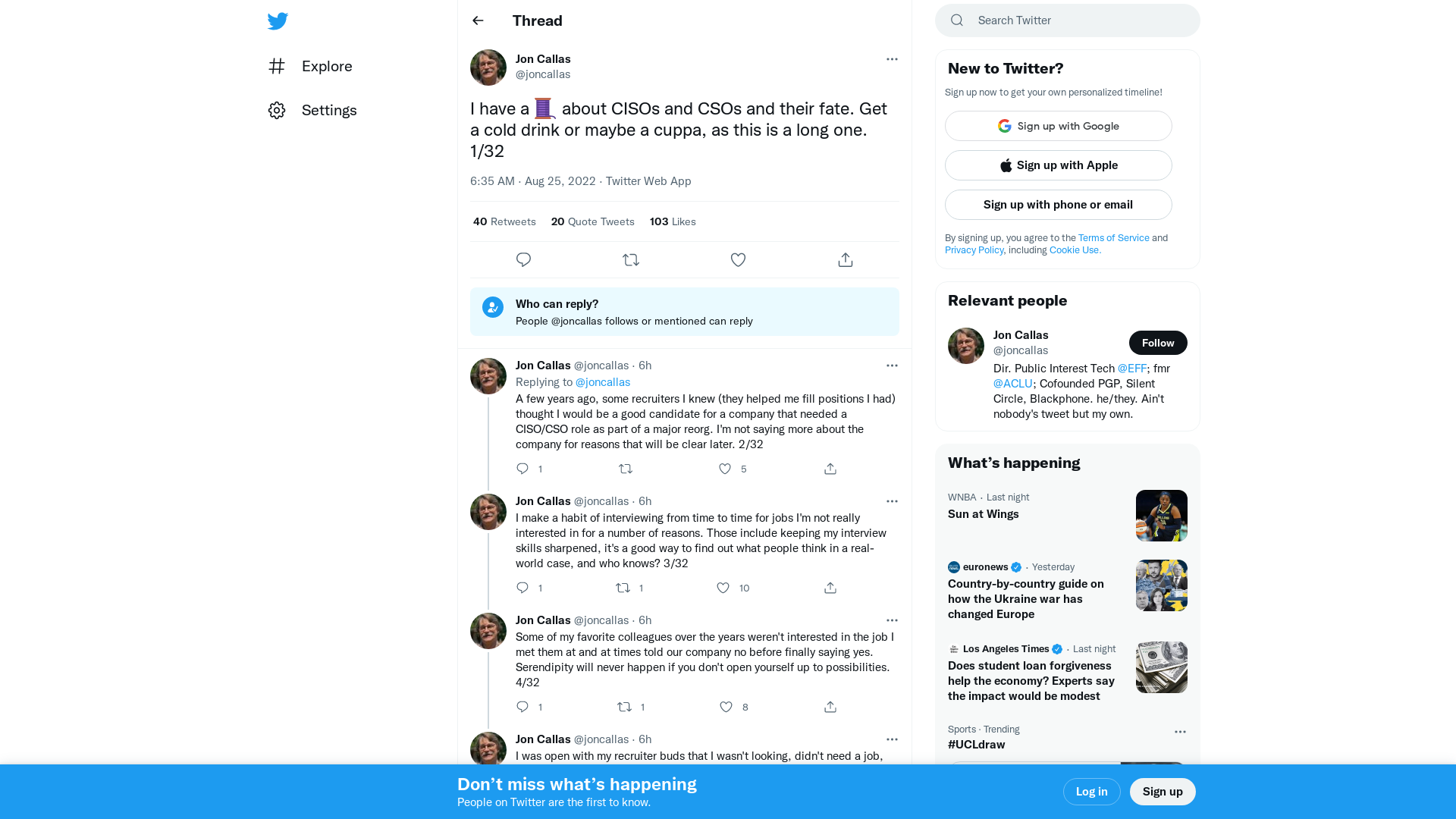

Linux Kernel Exploit (CVE-2022-32250) with mqueue | Theori
https://blog.theori.io/research/CVE-2022-32250-linux-kernel-lpe-2022/
2022_hitcon_settlers_of_netlink.pdf
https://research.nccgroup.com/wp-content/uploads/2022/08/2022_hitcon_settlers_of_netlink.pdf
Roasting 0ktapus: The phishing campaign going after Okta identity credentials
https://blog.group-ib.com/0ktapus
GitHub - mandiant/Ghidrathon: The FLARE team's open-source extension to add Python 3 scripting to Ghidra.
https://github.com/mandiant/Ghidrathon
Kimsuky’s GoldDragon cluster and its C2 operations | Securelist
https://securelist.com/kimsukys-golddragon-cluster-and-its-c2-operations/107258/
James on Twitter: "Some fresh (compile time Wed Aug 24 15:25:49 2022) #icedid in a password'd zip: https://t.co/eZcmnjedE4 the aptly named: doc-shellcode.rtf 🤷 loader c2: http://dullthingpur[.]com/ cc @Myrtus0x0 @InQuest" / Twitter
https://twitter.com/James_inthe_box/status/1562801036066115584![James on Twitter: "Some fresh (compile time Wed Aug 24 15:25:49 2022) #icedid in a password'd zip: https://t.co/eZcmnjedE4 the aptly named: doc-shellcode.rtf 🤷 loader c2: http://dullthingpur[.]com/ cc @Myrtus0x0 @InQuest" / Twitter](/image/screenshot/443430e649dcae9c51e744d0a7b56654.png)
MagicWeb: NOBELIUM’s post-compromise trick to authenticate as anyone - Microsoft Security Blog
https://www.microsoft.com/security/blog/2022/08/24/magicweb-nobeliums-post-compromise-trick-to-authenticate-as-anyone/
doc-shellcode.rtf (MD5: 5645C167C55B0DA31625C2FD59279829) - Interactive analysis - ANY.RUN
https://app.any.run/tasks/3a8a9a7a-2c6c-4033-a129-612e0f6735c6#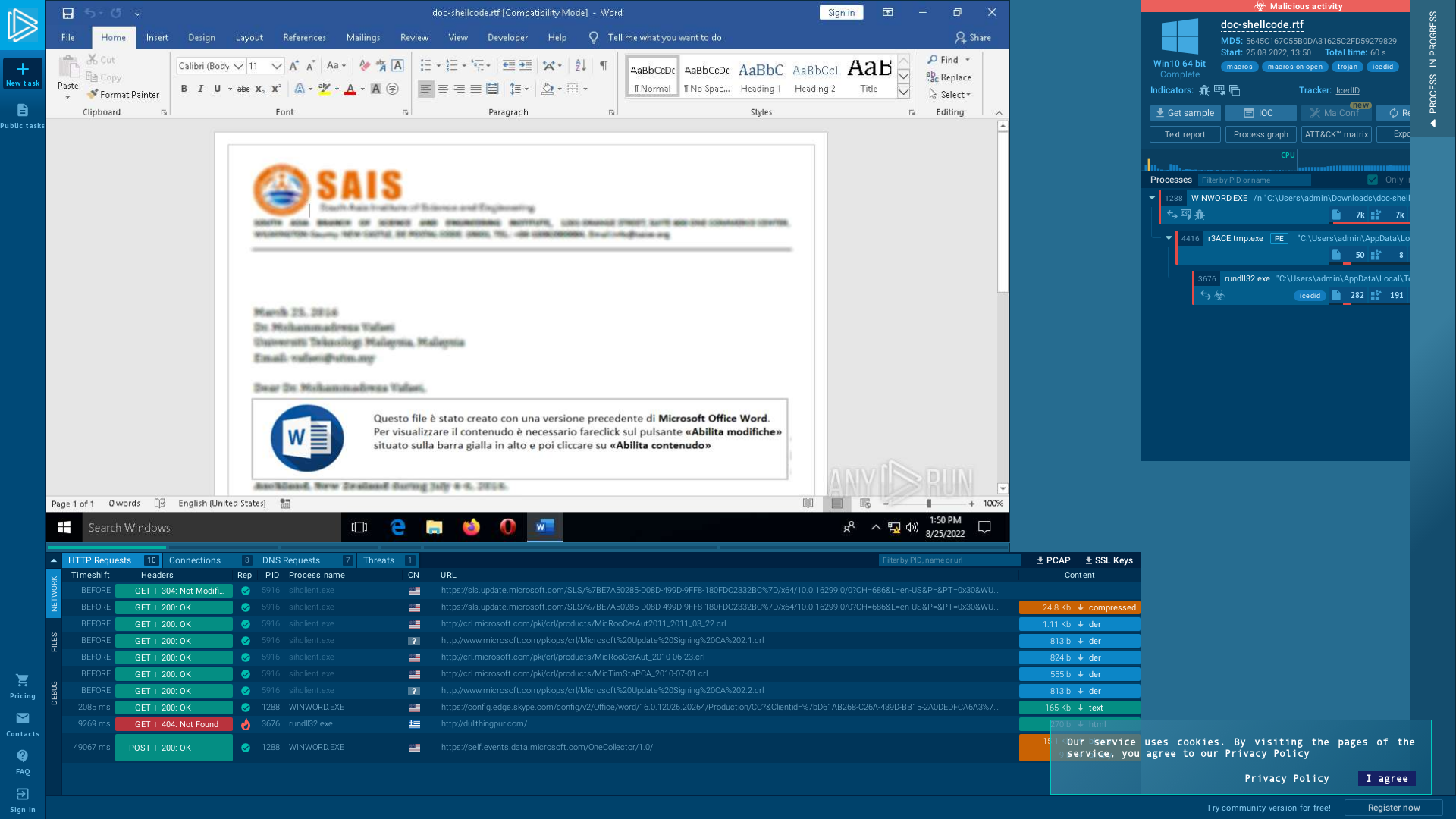
ScienceInsider on Twitter: "BREAKING: White House issues new policy that will require, by 2026, all federally-funded research results to be freely available to public without delay, ending longstanding ability of journals to paywall results for up to 1 year. Coverage coming on @ScienceInsider. https://t.co/HijntoZFDN" / Twitter
https://twitter.com/ScienceInsider/status/1562826693366415360
2-byte DoS in freebsd-telnetd / netbsd-telnetd / netkit-telnetd / inetutils-telnetd / telnetd in Kerberos Version 5 Applications - Binary Golf Grand Prix 3 - IT Security Research by Pierre
https://pierrekim.github.io/blog/2022-08-24-2-byte-dos-freebsd-netbsd-telnetd-netkit-telnetd-inetutils-telnetd-kerberos-telnetd.html
PyPI Repository Warns Python Project Maintainers About Ongoing Phishing Attacks
https://thehackernews.com/2022/08/pypi-repository-warns-python-project.html
Microsoft Uncovers New Post-Compromise Malware Used by Nobelium Hackers
https://thehackernews.com/2022/08/microsoft-uncovers-new-post-compromise.html
Detecting Scatter Swine: Insights into a relentless phishing campaign | Okta Security
https://sec.okta.com/scatterswine
More hackers adopt Sliver toolkit as a Cobalt Strike alternative
https://www.bleepingcomputer.com/news/security/more-hackers-adopt-sliver-toolkit-as-a-cobalt-strike-alternative/