GitHub - tyranid/blackhat-usa-2022-demos: Demos for the Blackhat USA 2022 talk "Taking Kerberos to the Next Level"
https://github.com/tyranid/blackhat-usa-2022-demos
Discord Desktop - Remote Code Execution | Electrovolt Blog
https://blog.electrovolt.io/posts/discord-rce/
A New Jailbreak for John Deere Tractors Rides the Right-to-Repair Wave | WIRED
https://www.wired.com/story/john-deere-tractor-jailbreak-defcon-2022/
CVE-2022-30216 - Authentication coercion of the Windows “Server” service
https://www.akamai.com/blog/security/authentication-coercion-windows-server-service
akamai-security-research/cve-2022-30216 at main · akamai/akamai-security-research · GitHub
https://github.com/akamai/akamai-security-research/tree/main/cve-2022-30216
How I Hacked my Car :: Programming With Style
https://programmingwithstyle.com/posts/howihackedmycar/
How I Hacked my Car Guides: Creating Custom Firmware :: Programming With Style
https://programmingwithstyle.com/posts/howihackedmycarguidescreatingcustomfirmware/
GitHub - sneakid/DC30-PhineasTalk: Slides for the talk we presented as UniPi at DefCon's Red Team Village
https://github.com/sneakid/DC30-PhineasTalk
How I Hacked my Car Part 3: Making Software :: Programming With Style
https://programmingwithstyle.com/posts/howihackedmycarpart3/
How I Hacked my Car Part 2: Making a Backdoor :: Programming With Style
https://programmingwithstyle.com/posts/howihackedmycarpart2/
Matt Suiche @ BlackHat/DEFCON on Twitter: "Yo @defcon what’s up with the masks seriously? I remember when hackers all about freedom and stuff, not we became hyper conformists that normalized obeying to rules? 🤡 Even CDC said it’s fine. #DEFCON30" / Twitter
https://twitter.com/msuiche/status/1558500581165084672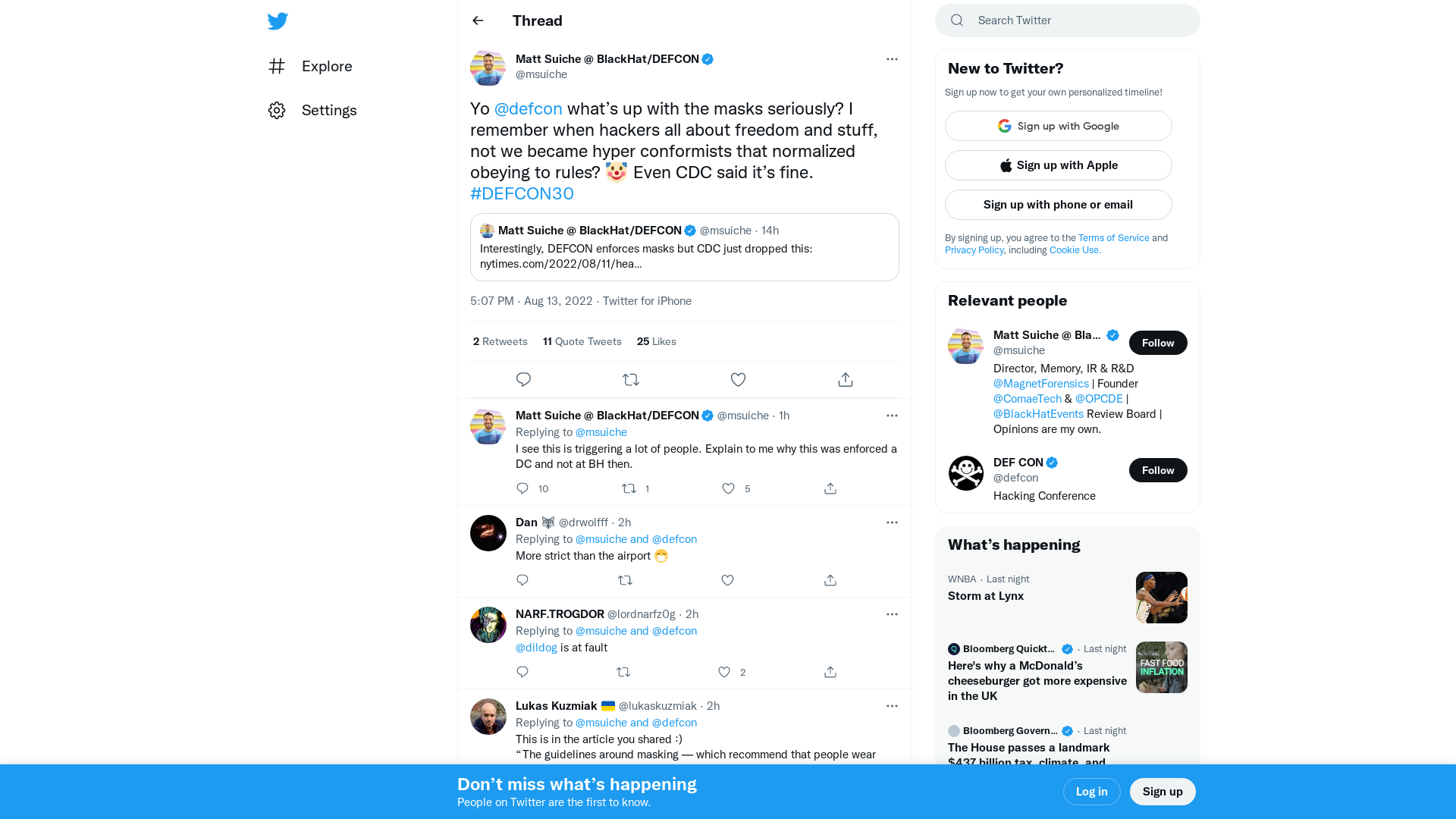
.NET Malware Analysis (Fake winlogon.exe) / Almog Ohayon - YouTube
https://youtu.be/4DJsNCX3okQ
Sebastiaan Provost @DEFCON 30 & Bsides LV on Twitter: "They are popping up everywhere lol @jonathandata0 https://t.co/h8wwceiOS6" / Twitter
https://twitter.com/Stekkz/status/1558255484427272192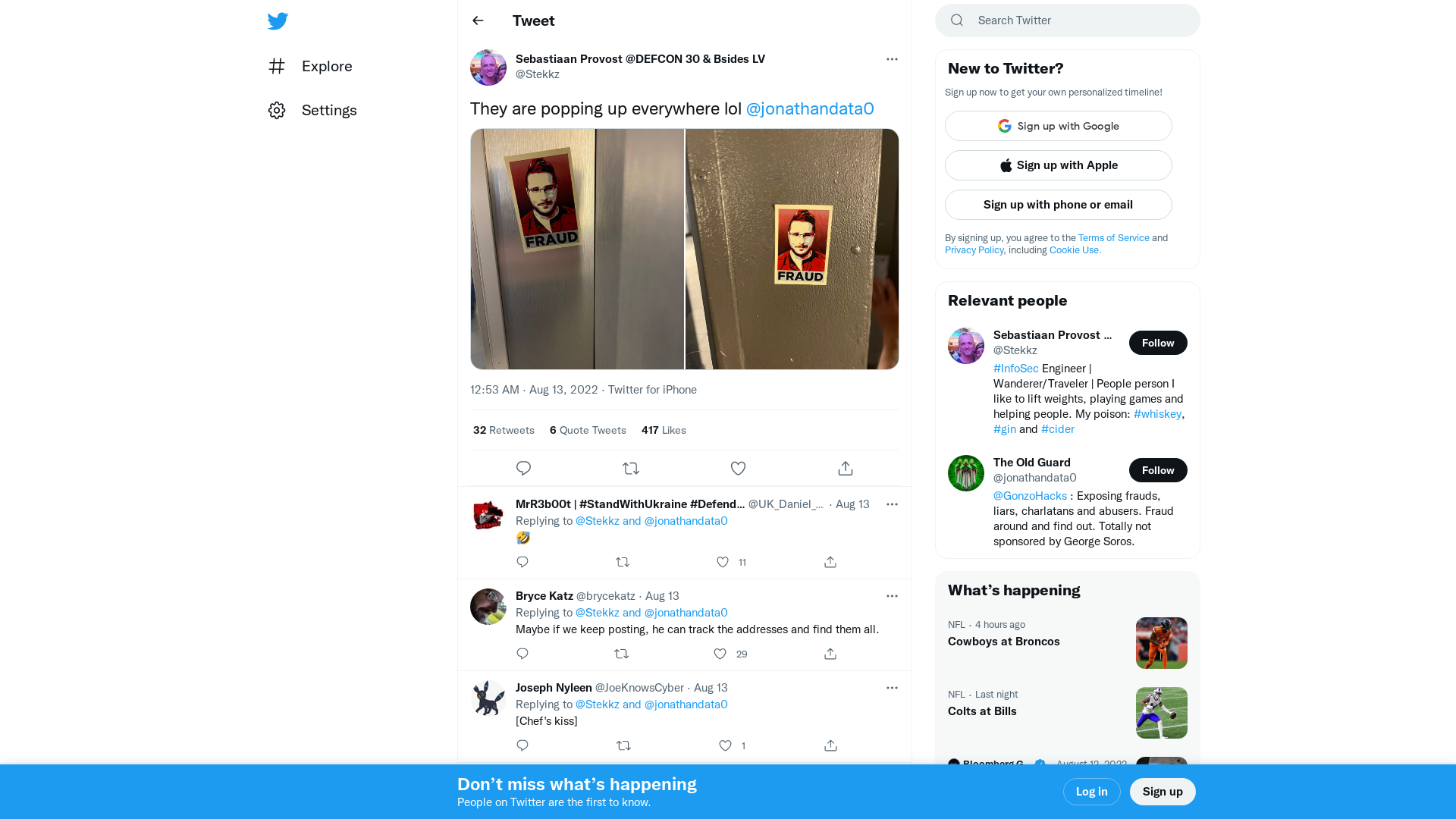
Introducing Threatest, A Go Framework For End-to-end Testing Of Threat Detection Rules | Datadog Security Labs
https://securitylabs.datadoghq.com/articles/threatest-end-to-end-testing-threat-detection/
Eugene Lim - You Have One New Appwntment - Hacking Proprietary iCalendar Properties.pdf
https://media.defcon.org/DEF%20CON%2030/DEF%20CON%2030%20presentations/Eugene%20Lim%20-%20You%20Have%20One%20New%20Appwntment%20-%20Hacking%20Proprietary%20iCalendar%20Properties.pdf
Eugene Lim - You Have One New Appwntment - Hacking Proprietary iCalendar Properties whitepaper.pdf
https://media.defcon.org/DEF%20CON%2030/DEF%20CON%2030%20presentations/Eugene%20Lim%20-%20You%20Have%20One%20New%20Appwntment%20-%20Hacking%20Proprietary%20iCalendar%20Properties%20whitepaper.pdf
Over 9,000 VNC servers exposed online without a password
https://www.bleepingcomputer.com/news/security/over-9-000-vnc-servers-exposed-online-without-a-password/
. on Twitter: "@TSA @LASairport alleged shooting at Vegas airport turns out to just be a “loud noise” according to @LVMPD. Who is going to be held accountable for allowing hundreds of unchecked passengers through “security?” Seems like they did the opposite of their job description here. https://t.co/nFYHVSJ65O" / Twitter
https://twitter.com/niklasfarraday/status/1558789798470356992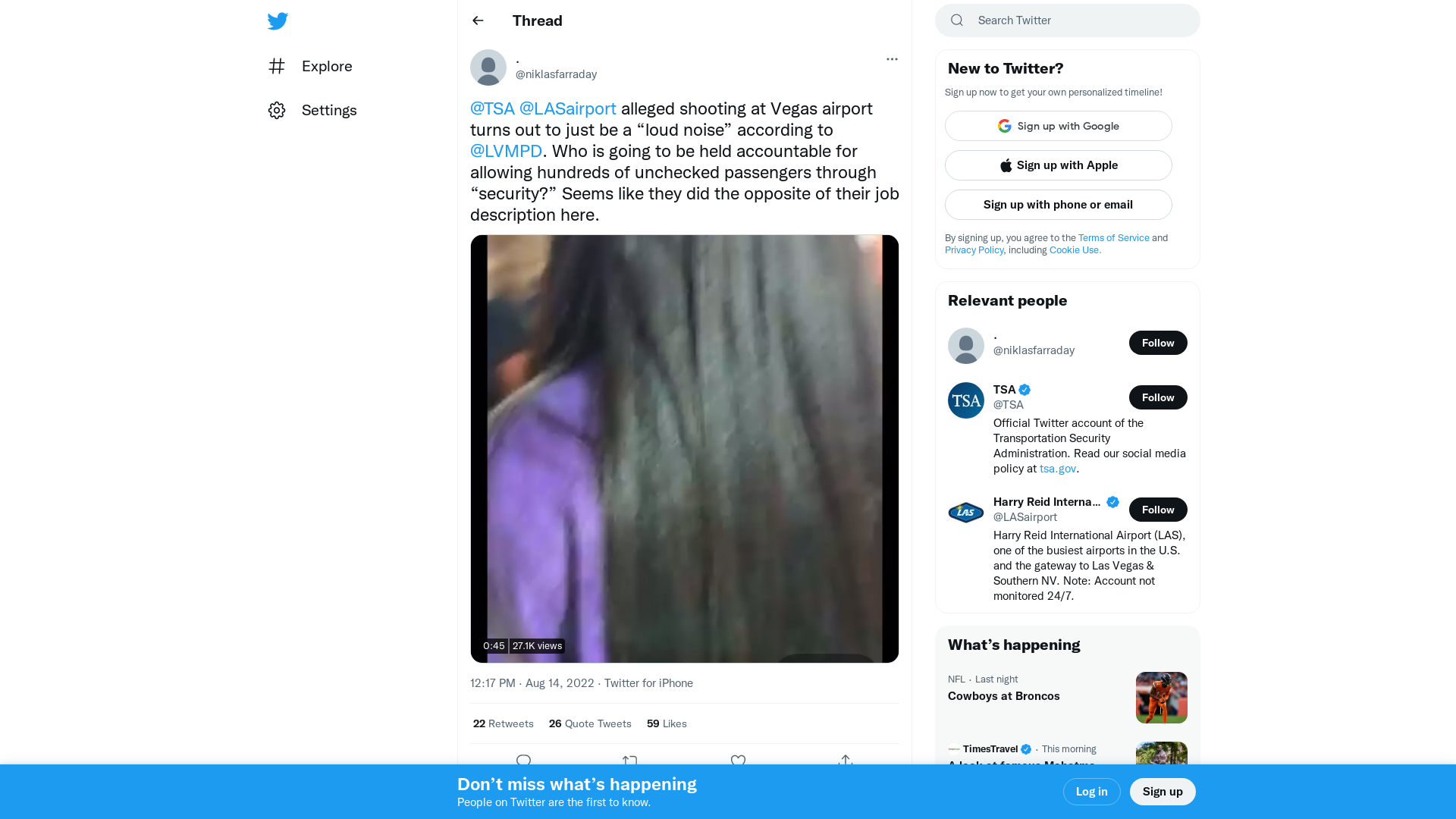
Digital Corpora Downloads: corpora/scenarios/magnet/
https://downloads.digitalcorpora.org/corpora/scenarios/magnet/
GitHub - h4wkst3r/Blackhat-USA-2022-Materials: Presentation materials for my Black Hat USA 2022 Briefing and Arsenal talks
https://github.com/h4wkst3r/Blackhat-USA-2022-Materials
XMPP Stanza Smuggling or How I Hacked Zoom - Black Hat USA 2022 | Briefings Schedule
https://www.blackhat.com/us-22/briefings/schedule/index.html#xmpp-stanza-smuggling-or-how-i-hacked-zoom-26618
Iron Tiger Compromises Chat Application Mimi, Targets Windows, Mac, and Linux Users
https://www.trendmicro.com/en_us/research/22/h/irontiger-compromises-chat-app-Mimi-targets-windows-mac-linux-users.html