GitHub - elastic/protections-artifacts: Elastic Security detection content for Endpoint
https://github.com/elastic/protections-artifacts
On Detection: Tactical to Functional | by Jared Atkinson | Posts By SpecterOps Team Members
https://posts.specterops.io/on-detection-tactical-to-functional-37ddcd75234b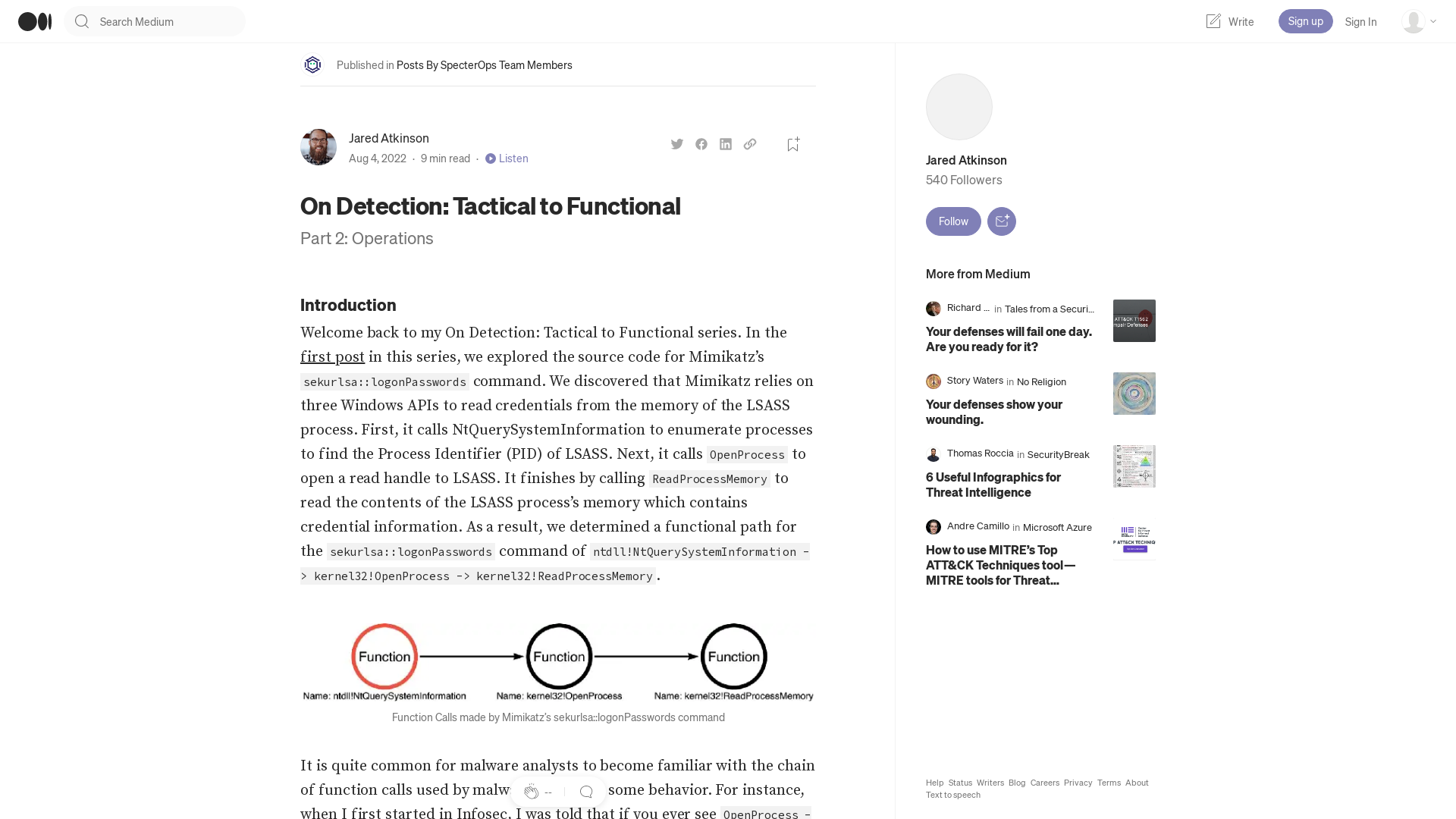
Likely Iranian Threat Actor Conducts Politically Motivated Disruptive Activity Against Albanian Government Organizations | Mandiant
https://www.mandiant.com/resources/likely-iranian-threat-actor-conducts-politically-motivated-disruptive-activity-against?1
Woody RAT: A new feature-rich malware spotted in the wild | Malwarebytes Labs
https://blog.malwarebytes.com/threat-intelligence/2022/08/woody-rat-a-new-feature-rich-malware-spotted-in-the-wild/
Zellic on Twitter: "4/ The Slope Wallet for iOS and Android uses Sentry for event logging. Any interaction in the app would trigger an event log. Unfortunately, Slope didn't configure Sentry to scrub sensitive info. Thus, mnemonics were leaked to Sentry s/o to @sniko_ for this screenshot: https://t.co/Rs7pEvVGsJ" / Twitter
https://twitter.com/Zellic_io/status/1554936158114553856
Traffic Light Protocol (TLP)
https://www.first.org/tlp/
Introducing the Azure Threat Research Matrix - Microsoft Tech Community
https://techcommunity.microsoft.com/t5/security-compliance-and-identity/introducing-the-azure-threat-research-matrix/ba-p/3584976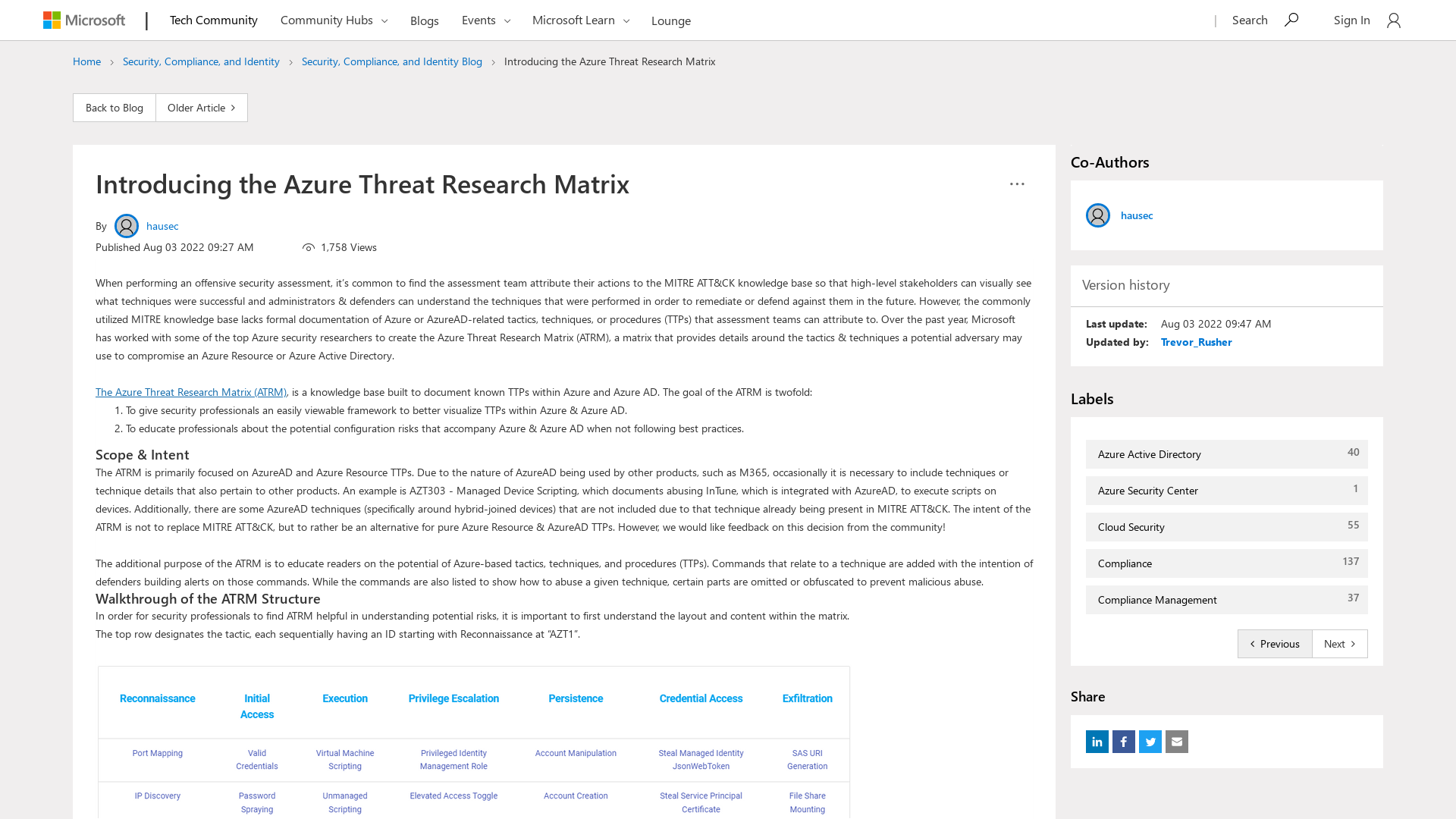
Flight of the Bumblebee: Email Lures and File Sharing Services Lead to Malware
https://unit42.paloaltonetworks.com/bumblebee-malware-projector-libra/
"Windows Kernel Debugging, Internals, and Exploitation" Pre-Class Survey - Beta
https://docs.google.com/forms/d/e/1FAIpQLScojZa4zQmlAO5365EYp8gGcd7npMtk9YyxVh7MG1jrUp7mNQ/viewform
Omer Benjakob on Twitter: "SCOOP We got our hands on screen shots of an early prototype of Pegasus, called Syaphan and intended for use by the Israeli police These photos are the closest we’ve gotten to seeing real working Pegasus system THREAD @JoshBreiner @haaretzcom https://t.co/73duo7QNEg https://t.co/Sk0CHD5gc1" / Twitter
https://twitter.com/omerbenj/status/1555198346293280770
Introducing BloodHound 4.2 — The Azure Refactor | by Andy Robbins | Aug, 2022 | Posts By SpecterOps Team Members
https://posts.specterops.io/1cff734938bd
MalwareBazaar | 193-149-176-134
https://bazaar.abuse.ch/browse/tag/193-149-176-134/
Meta’s Adversarial Threat Report, Second Quarter 2022 | Meta
https://about.fb.com/news/2022/08/metas-adversarial-threat-report-q2-2022/

InfoSec Handlers Diary Blog - SANS Internet Storm Center
https://i5c.us/d28914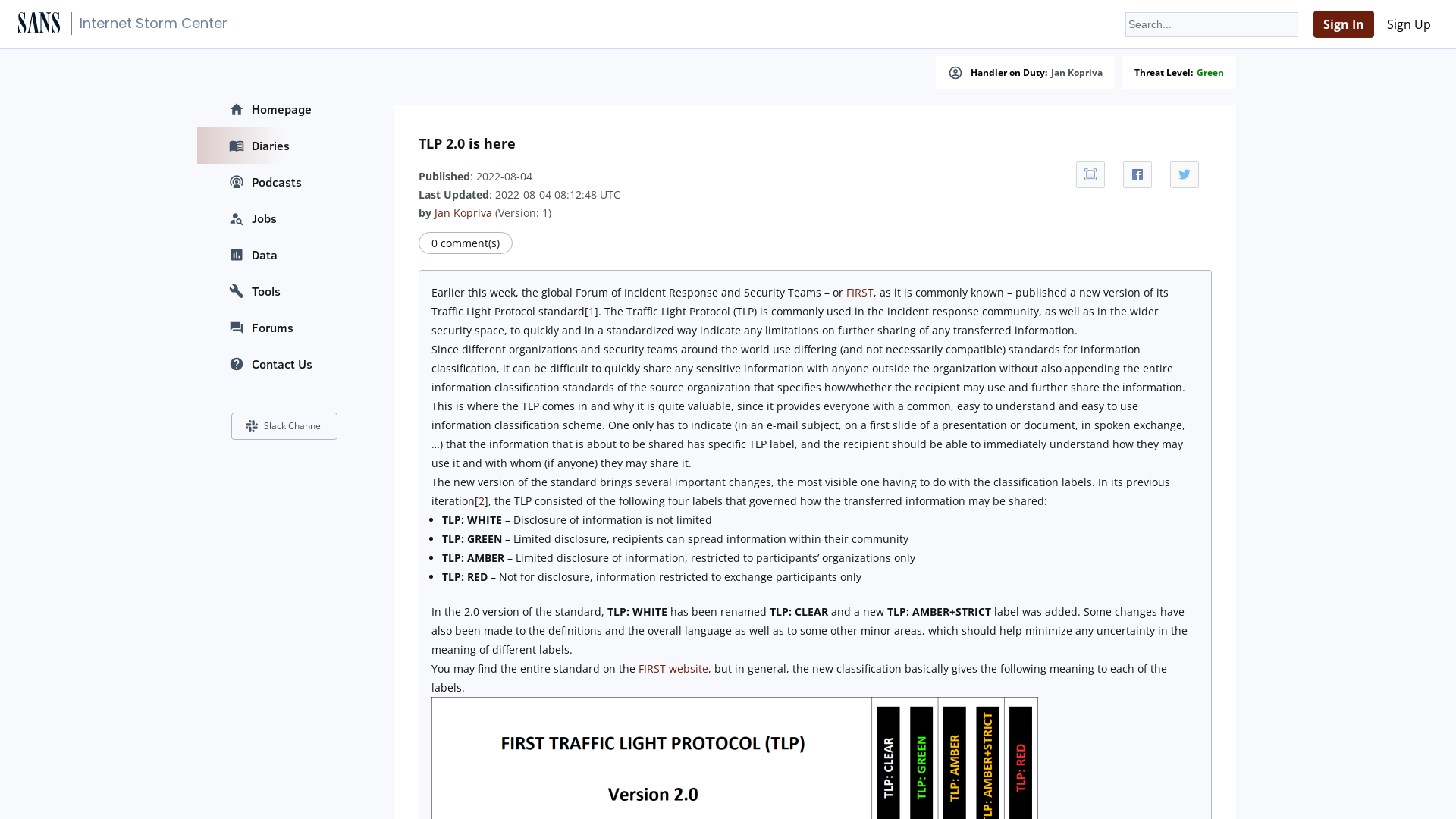
Cisco Business Routers Found Vulnerable to Critical Remote Hacking Flaws
https://thehackernews.com/2022/08/cisco-business-routers-found-vulnerable.html
Hackers Exploited Atlassian Confluence Bug to Deploy Ljl Backdoor for Espionage
https://thehackernews.com/2022/08/hackers-exploited-atlassian-confluence.html
pl0x_plox_chiken_p0x on Twitter: "@stephenlacy Hi Stephen, I'm sorry to rain on your parade, but what you've uncovered in GH is a bb effort. I've discovered a problematic behavior in GH and was exploiting it for bounty (affected companies were contacted responsibly). This is why I only exfiltrated the env variables." / Twitter
https://twitter.com/pl0xp/status/1554754171240341504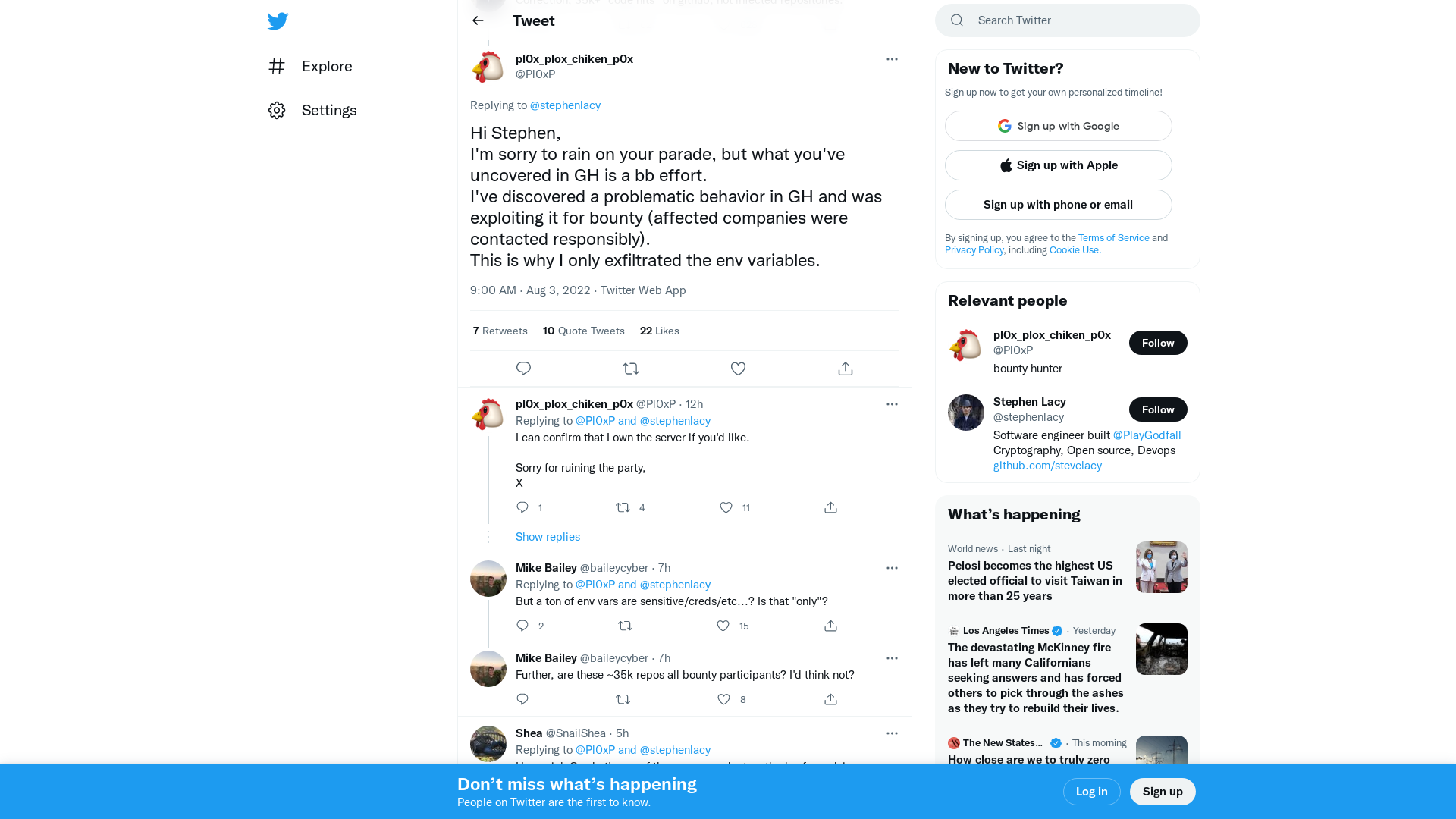
Pro-PRC “HaiEnergy” Information Operations Campaign Leverages Infrastructure from Public Relations Firm to Disseminate Content on Inauthentic News Sites | Mandiant
https://www.mandiant.com/resources/pro-prc-information-operations-campaign-haienergy